The Sophos X-Ops Incident Response unit has been investigating the strategies of a ransomware faction known as Mad Liberator. This is a relatively recent threat actor, first appearing in mid-July 2024. In this piece, we will delve into specific methods utilized by the group, involving the widely-used remote-control application Anydesk. We will outline the intriguing social manipulation techniques employed by the group and offer guidance on how to reduce your vulnerability to becoming a target, and for investigators, how to identify potential activity by this faction.
Before we delve into the details, it is important to acknowledge that Anydesk is legitimate software that the attackers are exploiting in this context. Although the attackers are misusing this application in the ways we will illustrate below, it is likely that any remote access tool could serve their intentions. Furthermore, it is important to mention at the outset that SophosLabs has a detection mechanism in place, known as Troj/FakeUpd-K, for the specified binary.
Who is Mad Liberator?
The actions observed by the Sophos X-Ops team thus far indicate that Mad Liberator concentrates on data exfiltration; in our own observations, we have not yet encountered any incidents of data encryption attributed to Mad Liberator. However, information on watchguard.com implies that the group occasionally employs encryption and also engages in double extortion (stealing data and then encrypting the victim’s systems with a threat of releasing the stolen data if the victim does not pay for decryption).
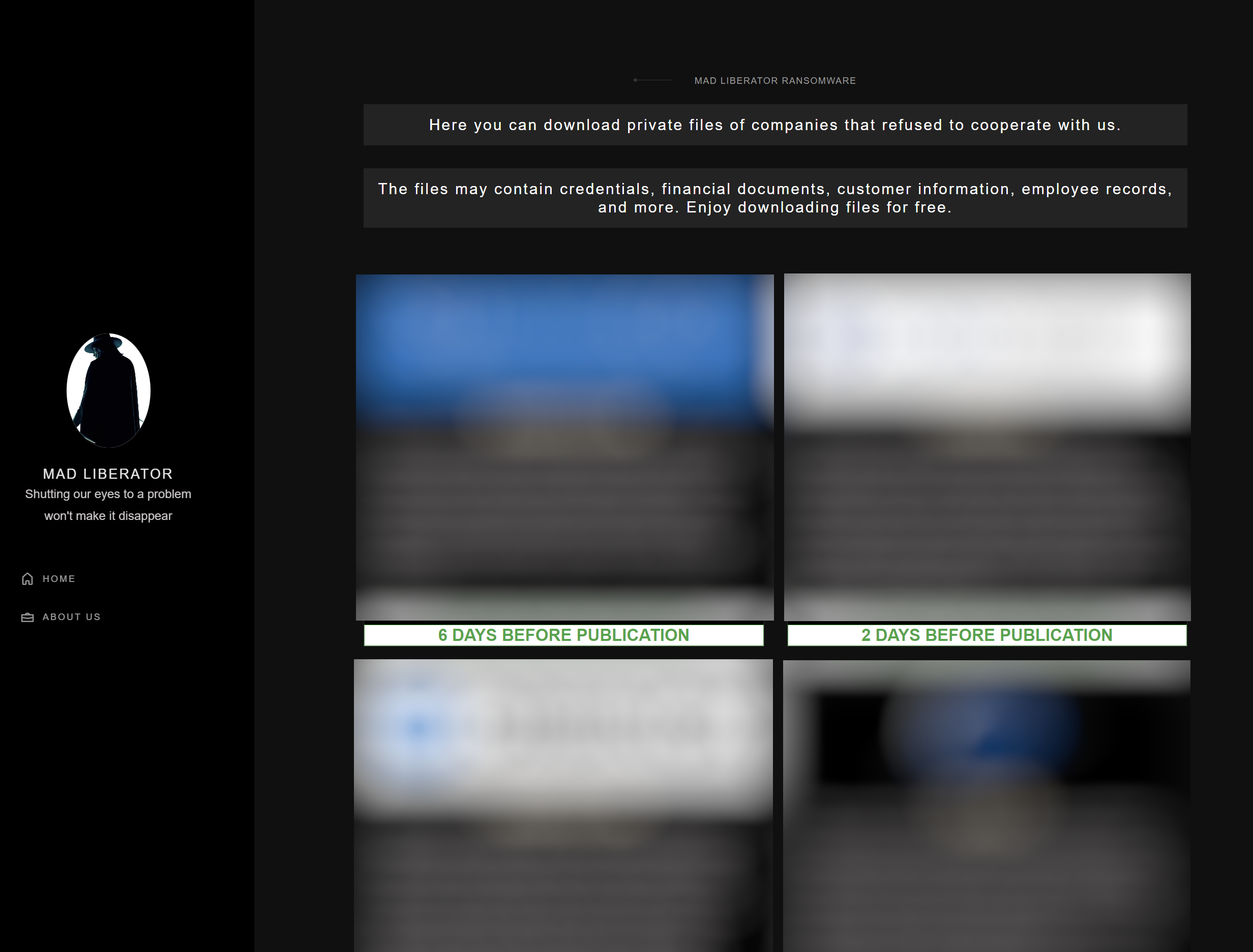
In line with the behavior of threat actors involved in data exfiltration, Mad Liberator maintains a leak site where they disclose victim information, aiming to exert additional pressure on victims for payment. The site claims that files can be downloaded “for free.”
Figure 1: The disclosure site of Mad Liberator
Interestingly, Mad Liberator employs social manipulation tactics to gain access to environments, targeting victims who use remote control tools installed on endpoints and servers. Notably, Anydesk is commonly employed by IT teams to manage their environments, especially when dealing with remote users or devices.
Operation of the attack
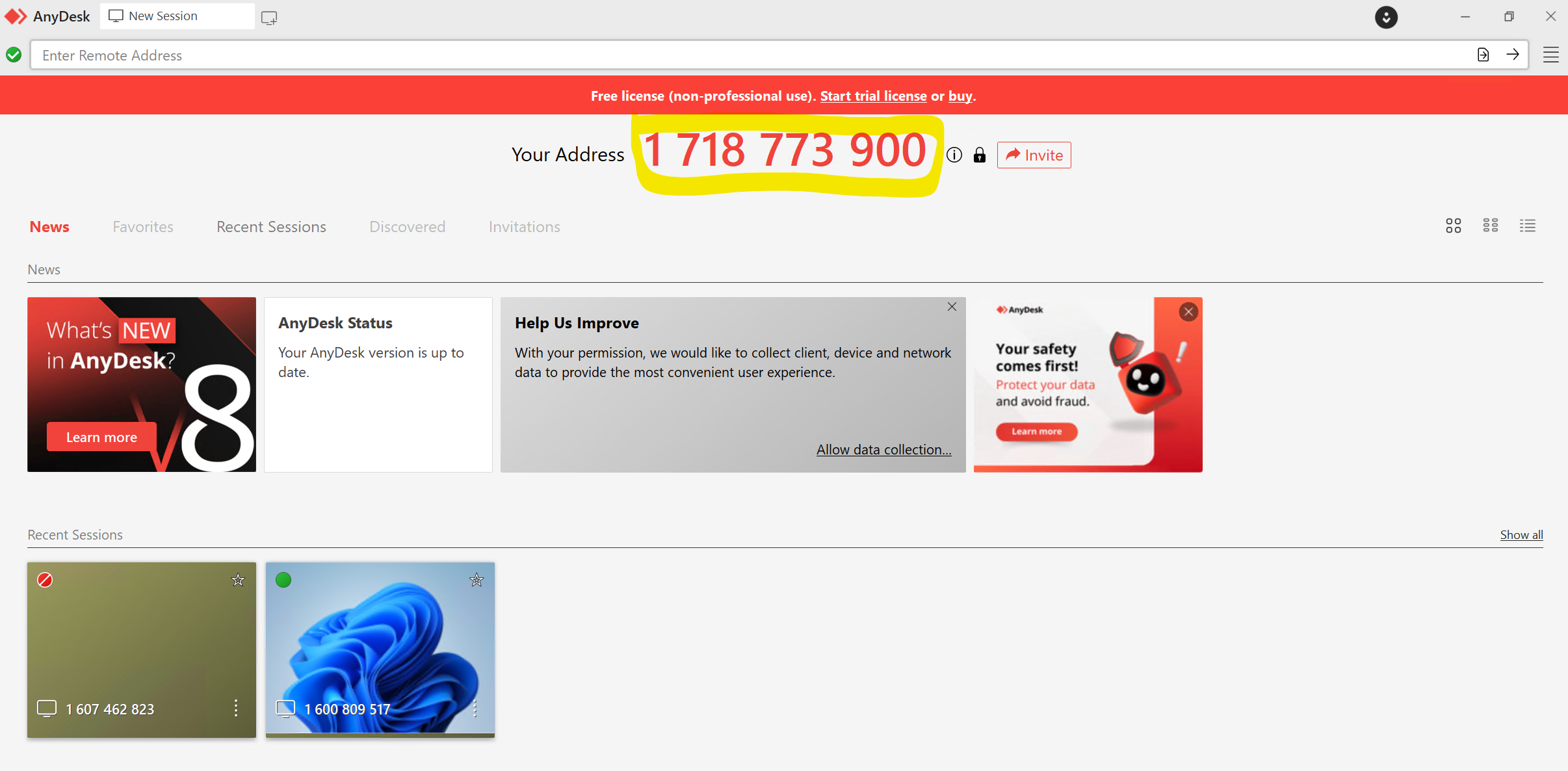
Anydesk operates by assigning a unique ID, in this case, a ten-digit code, to each device it is installed on. Once the application is set up on a device, a user has the option to request access to a remote device for taking control by entering the ID, or to allow another user to take control of their device through a remote session.
Figure 2: A session on Anydesk featuring the prominently displayed ten-digit address
At present, it is unclear how, or if, the attacker specifically selects an Anydesk ID. Theoretically, they could cycle through potential addresses until a connection request is accepted; however, with up to 10 billion ten-digit numbers, this method seems rather inefficient. In an investigation carried out by the Incident Response team, no evidence was found of any prior contact between the Mad Liberator attacker and the victim before the victim received an unsolicited Anydesk connection request. The user wasn’t a well-known or publicly recognized staff member, and there was no obvious reason for them to be singled out.
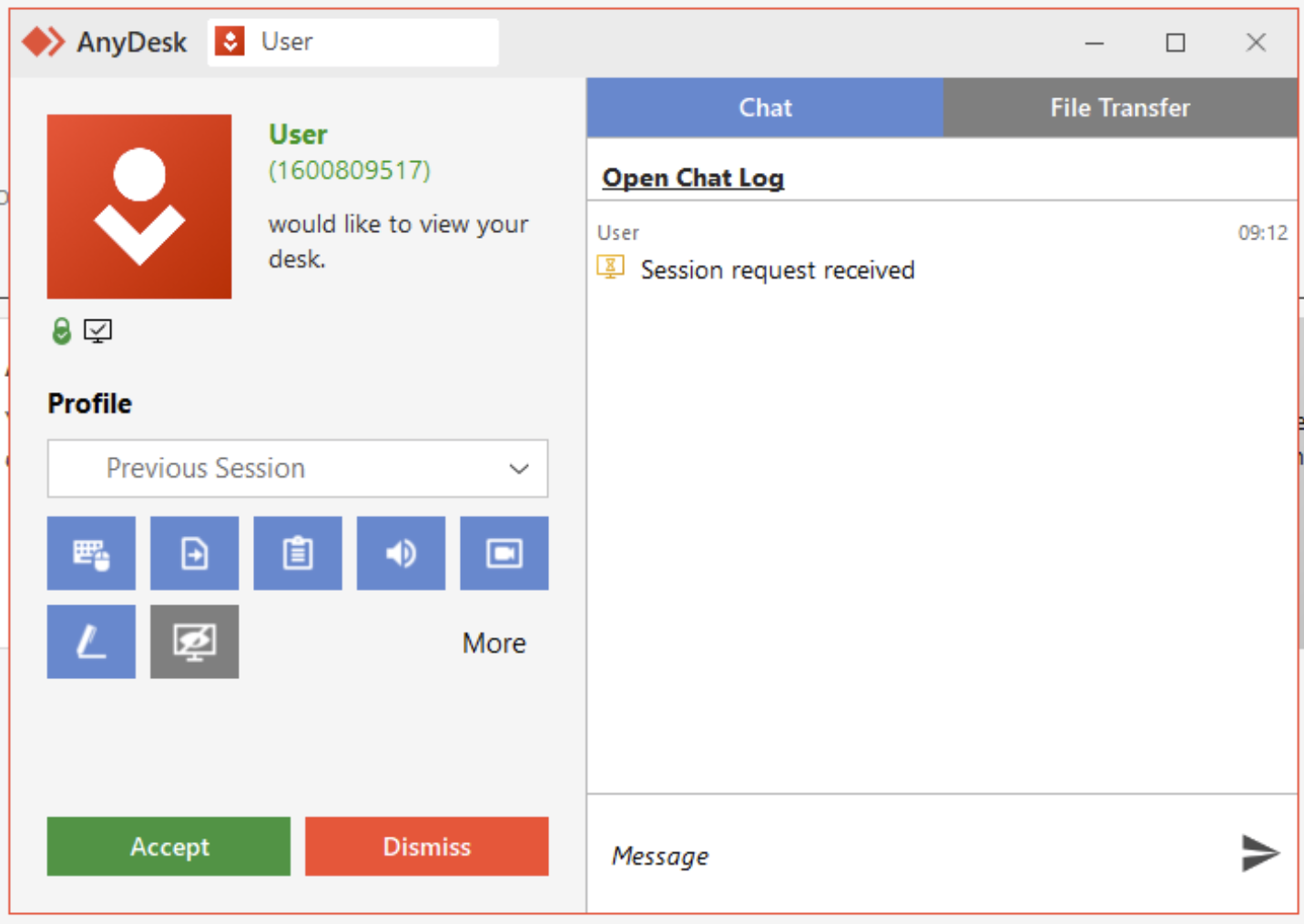
When an Anydesk connection request is received, the user will encounter the pop-up depicted in Figure 3. Prior to establishing the connection, the user will need to authorize it.
Figure 3: A connection request from “User” via Anydesk; a detail that Anydesk administrators are familiar with but may be unknown to end users is that anyone can choose any username when configuring Anydesk, allowing an attacker to even use the name “Tech Support” or similar.
In the incident managed by our IR team, the victim knew that Anydesk was utilized by their company’s IT department. They therefore assumed that the incoming connection request was a routine occurrence of the IT department conducting maintenance, and thus clicked Accept.
After the connection was established, the attacker transmitted a binary to the victim’s device and ran it. In our investigations, this file was labeled as “Microsoft Windows Update,” with the following SHA256 hash:
f4b9207ab2ea98774819892f11b412cb63f4e7fb4008ca9f9a59abc2440056fe
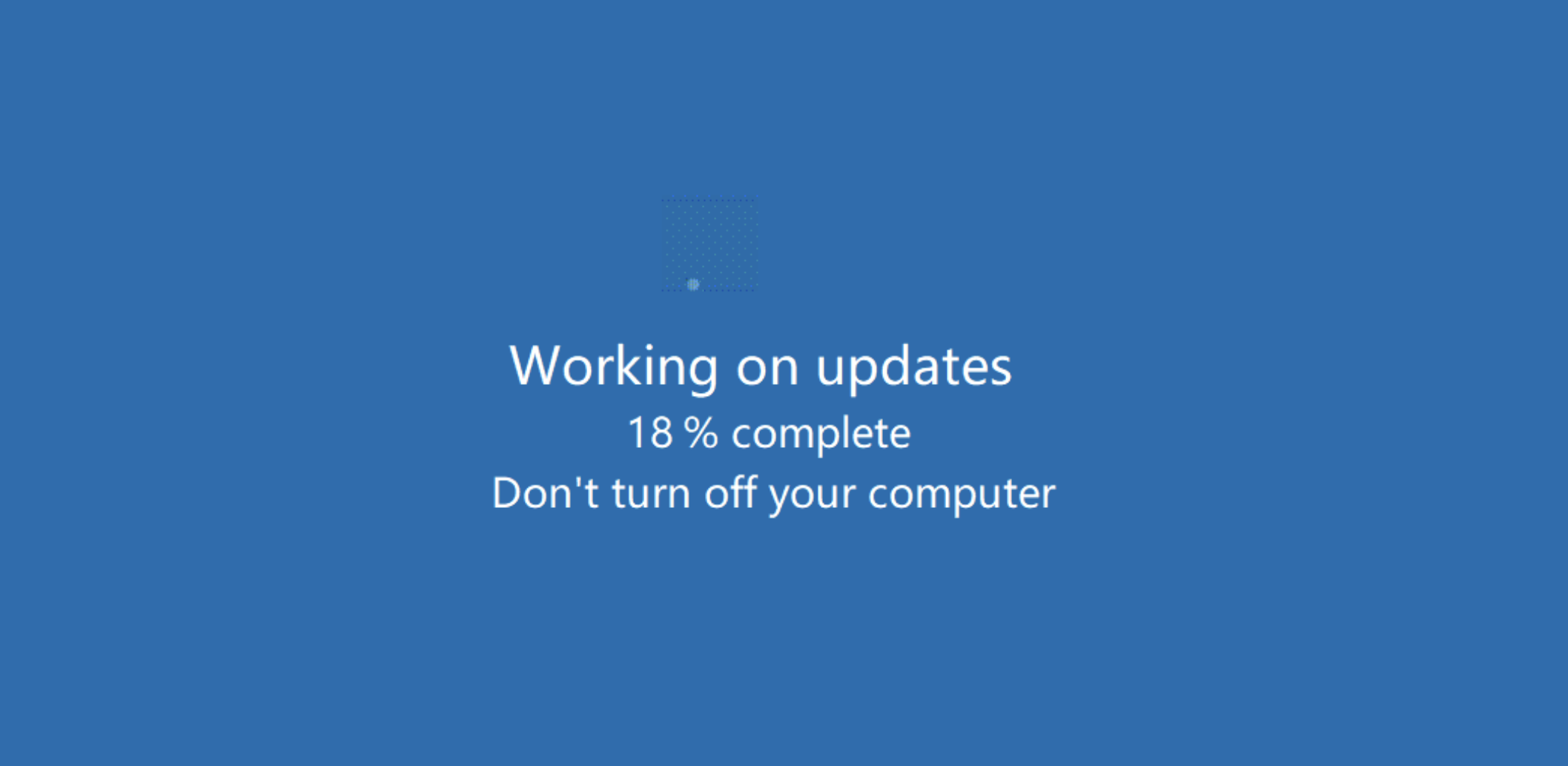
This binary constituted a straightforward program that displayed a splash screen mimicking a Windows Update interface. The screen featured animations, giving the impression that the system was undergoing an update, as illustrated in Figure 4.
Figure 4: A Windows Update interface that may not be what it seems!
The application did not engage in any other activities, making it less likely to be promptly identified as malicious by most anti-malware tools. (Sophos has produced detection [Troj/FakeUpd-K] for this specific binary and will stay vigilant for any changes in this regard.)
To prevent the discovery and interruption of the deception, the attacker took an additional measure at this juncture. By utilizing a functionality within Anydesk, the attacker disabled user input from the keyboard and mouse, to avoid the program being closed if the user inadvertently pressed the “Esc” key.
Due to the keyboard being inaccessible to the victim and the seemingly innocuous nature of the displayed screen, the user remained oblivious to the malicious activities happening in the background, making it challenging for them to detect or halt the actions, even if they were suspicious.
The attacker proceeded to gain entry to the victim’s OneDrive account linked to the device, as well as files stored on a central server accessible through a mapped network share. By utilizing the Anydesk FileTransfer feature, the attacker pilfered and removed these corporate files. Subsequently, the attacker employed Advanced IP Scanner to identify potential exploitable devices within the same network segment. (Ultimately, there was no lateral movement to other devices.)
After obtaining control of the pilfered files, the attacker executed another program that generated numerous ransom notes. Interestingly, these ransom notes were created in various locations on a shared network location mapped to the device, instead of on the victim’s device directly. These notes warned of data theft and provided instructions on ransom payment to prevent disclosure of the stolen files. (These tactics are likely familiar to readers of our study on current ransomware gang pressure tactics.)
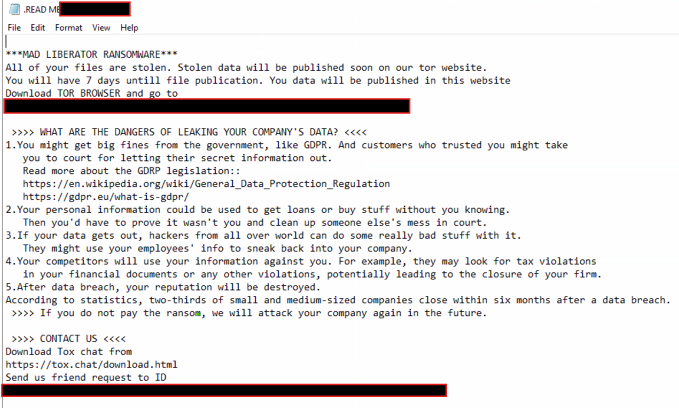 Figure 5: The ransom note sent to the victim; highlighting threats of reputational and regulatory harm, without specifying a ransom amount
Figure 5: The ransom note sent to the victim; highlighting threats of reputational and regulatory harm, without specifying a ransom amount
The deceptive Windows Update screen concealed the attacker’s actions on the victim’s screen. The attack persisted for nearly four hours, after which the attacker closed the fake update screen and terminated the Anydesk session, returning device control to the victim. Notably, the binary was manually triggered by the attacker; lacking any scheduled task or automation to execute it again post attacker exit, the file remained on the compromised system.
Key Learnings and Measures
This was a direct attack that hinged on the victim assuming the Anydesk request was routine. The investigation found no additional social engineering efforts by the attacker, such as email communication or phishing attempts. This incident underscores the importance of continuous staff training and the necessity for organizations to establish and communicate a clear policy on how IT departments will initiate and manage remote sessions.
Aside from user training, it is strongly recommended that administrators enforce Anydesk Access Control Lists to permit connections only from specific devices, significantly reducing the risk of such attacks. AnyDesk offers detailed guidance on implementing this along with additional security steps in the provided link:
Further guidance can be accessed here:
Procedural instructions for investigators follow at the article’s end.
Wrap-Up
Ransomware gangs emerge and fade, with Mad Liberator potentially becoming a major player or a temporary phenomenon. Nonetheless, the social engineering tactics used by the group in the above case are notable – though not unprecedented. Attackers will persist in developing and utilizing diverse tactics to exploit both human vulnerabilities and technical security defenses.
Balancing security and usability when deploying tools within an environment, especially ones enabling remote access by those responsible for critical system upkeep, can be challenging. Yet, it is always advised to review and adhere to vendor security recommendations when deploying network applications that facilitate remote device access. Failure to follow these recommendations should be documented in the risk management process for ongoing review or the implementation of alternative safeguards to align with the organization’s risk tolerance.
Appendix: Investigating Mad Liberator
If investigating an incident where Anydesk may have been exploited by attackers, check for relevant event and connection data stored in the following files:
- C:ProgramDataAnyDeskconnection_trace.txt
- C:ProgramDataAnyDeskad_svc.trace
- C:Users%AppDataRoamingAnyDeskad.trace
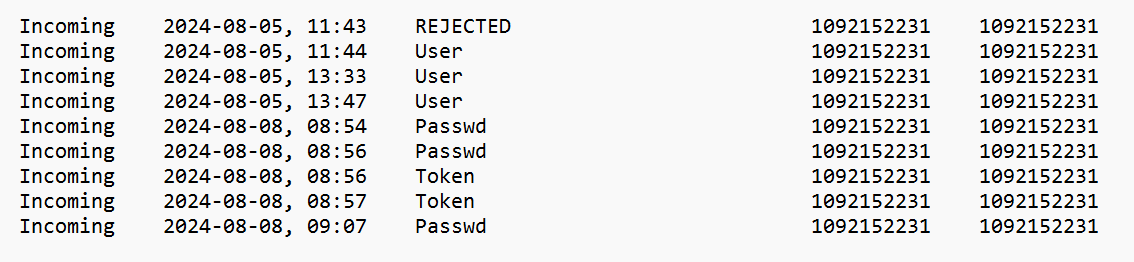
The connection_trace.txt file contains only recent connection Address IDs and may not be overly useful independently. Nevertheless, it aids in pinpointing the offending ID.
Figure
6: An examination of connection_trace.txt, providing details on the outcome of each event
In reference to each connection, there exist four potential states:
- DECLINED – the end-user turned down a connection request
- End user – the end-user endorsed a connection request
- Passcode – secret key input by the remote system to secure access
- Identifier – remote system has chosen the ‘Sign In Automatically’ preference
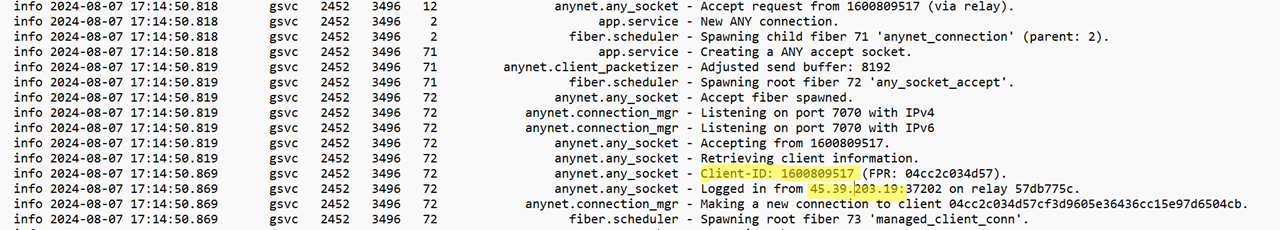
Both ad_svc.trace and ad.trace logs encompass a substantial amount of intricate information. These files are accessible for inspection using a text editor like Notepad and include connection data in addition to other occurrences. The ad_svc.trace file stores particulars about the primary IP addresses of remote connections.
Figure 7: An insight into ad_svc.trace; an uncertain connection stands out in the illustration
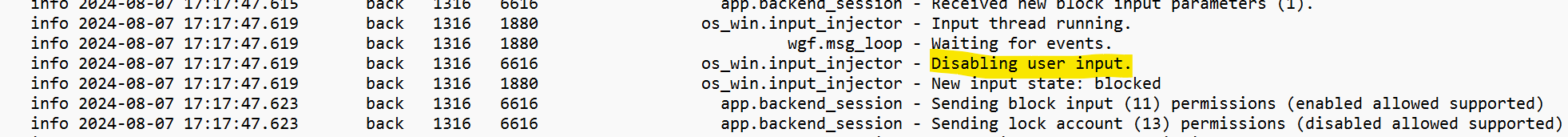
The ad.trace file logs events related to file transmissions, such as situations where user input is deactivated.
Figure 8: Deactivation of user input choices
Figure 9: Transcript of the file transfer instances
While the records will disclose the directory and the count of files transferred during data extrusion, regrettably, they will not specify the name of each file.
If Sophos Intercept X is installed, simplification of data collection can occur. The subsequent OSquery can be employed through Live Discover within the Sophos Central Dashboard:
SELECT
strftime('%Y-%m-%dT%H:%M:%S', substr(grep.line, instr(grep.line, 'info') + 5, 19)) AS Datetime,
grep.path,
CASE
WHEN grep.pattern = 'Logged in from' THEN 'Login'
WHEN grep.pattern = 'Preparing files' THEN 'File Transfer from this Host'
WHEN grep.pattern = 'Accepting from' THEN 'Accepted Connection Request'
WHEN grep.pattern = 'Incoming session request:' THEN 'Incoming Session Request'
WHEN grep.pattern = 'Remote OS:' THEN 'Remote OS'
WHEN grep.pattern = 'Disabling user input.' THEN 'Disable Mouse and Keyboard'
WHEN grep.pattern = 'Download started' THEN 'File Transfer to this Host'
WHEN grep.pattern = 'Received a sysinfo request.' THEN 'System Information Request'
WHEN grep.pattern = 'Authenticated with permanent token' THEN 'Authenticated with Token'
WHEN grep.pattern = 'Authenticated with correct passphrase' THEN 'Authenticated with Password'
WHEN grep.pattern = 'Profile was used:' THEN 'Profile Assigned'
END AS 'Operation',
grep.line as Data
FROM file
CROSS JOIN grep ON (grep.path = file.path)
WHERE
(
file.path LIKE 'C:ProgramDataAnyDeskad_svc.trace'
OR file.path LIKE 'C:Users%AppDataRoamingAnyDeskad.trace'
)
AND
(
--AnyDesk
grep.pattern = 'Logged in from'
OR grep.pattern = 'Preparing files'
OR grep.pattern = 'Accepting from'
OR grep.pattern = 'Incoming session request:'
OR grep.pattern = 'Remote OS:'
OR grep.pattern = 'Disabling user input.'
OR grep.pattern = 'Download started'
OR grep.pattern = 'Received a sysinfo request.'
OR grep.pattern = 'Authenticated with permanent token'
OR grep.pattern = 'Authenticated with correct passphrase'
OR grep.pattern = 'Profile was used:'
)
ORDER BY Datetime DESC
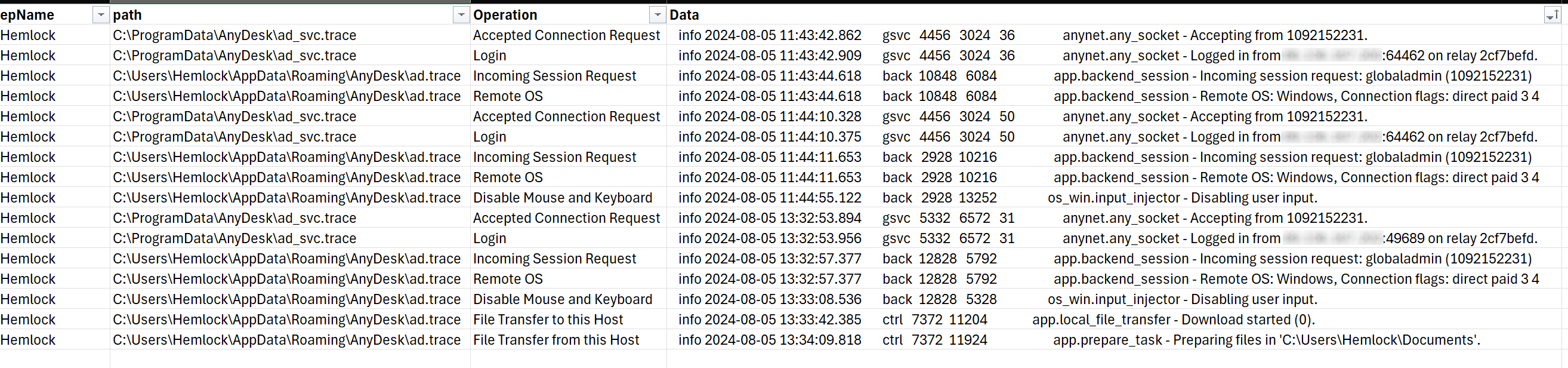
The query further assists in structuring the data into a coherent table, as depicted in Figure 10.
Figure 10: The results of the above OSquery, presented in a convenient tabular layout
Acknowledgments
Harshal Gosalia, Ollie Jones, and Andy French contributed to the completion of this study.