Sophos Managed Detection and Response (MDR) thwarts and monitors actions from likely Iranian state actor called “MuddyWater”

Observations made by Sophos MDR reveal a recent campaign employing targeted phishing tactics to lure victims into downloading a valid remote machine management tool for credential dumping. We hold a fair degree of certainty that this operation, codenamed STAC 1171, is linked to an Iranian threat group commonly known as MuddyWater or TA450.
The initial incident identified was in early November, where Sophos endpoint behavior regulations intercepted credential dumping aimed at an Israeli organization. Upon investigation, we noticed indicators and tactics consistent with reports from Proofpoint about TA450. The attacker gained access through a phishing email instructing recipients to access a shared document located at hxxps[://]ws[.]onehub[.]com/files/ and download a file named ‘New Program ICC LTD.zip’.
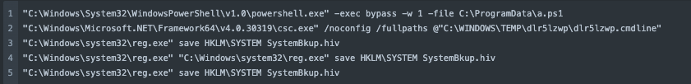
The ‘New Program ICC LTD.zip’ archive enclosed an installer file for the legitimate remote monitoring and management (RMM) platform called Atera. The installation utilized a trial account linked to an email address suspected to be compromised. Once the Atera Agent was installed, the threat actors executed a PowerShell script (named a.ps1) using Atera’s remote run commands to extract credentials and generate a backup of the SYSTEM registry hive. This credential extraction activity got intercepted and blocked by Sophos behavior norms:
“cmdline”: “C:WINDOWSsystem32reg.exe” save HKLMSYSTEM SystemBkup.hiv”
Subsequent post-compromise activities in Atera included:
- Multiple commands for domain enumeration;
- Establishment of an SSH tunnel towards 51.16.209[.]105;
- Utilization of an obfuscated PowerShell command to download the Level RMM tool (at hxxps[:]//downloads.level.io/install_windows.exe).
Telemetry data has also indicated similar behavior in another Sophos client in the US who is not using MDR services. Sophos X-Ops team will be vigilant in monitoring these activities and providing updates on this threat campaign.


