Review on Driving School Training: The nucleus operators in Sophos Intercept X Advanced by MarcusA

Functioning in ‘kernel-space’ – the most privileged tier of an operating system, with direct reach to memory, hardware, resource administration, and storage – is significantly crucial for security applications. This grants them the capability to observe ‘user-space’ – the non-privileged setting where applications operate – and guard against malicious software executing in that setting, even when it tries to escape detection. However, kernel access also allows security products to combat more deceitful threats within the kernel itself. For instance, some threat actors employ BYOVD (Bring Your Own Vulnerable Driver) maneuvers, or endeavor to have their own malicious drivers cryptographically validated, to infiltrate kernel-space and exploit that elevated access level.
Nevertheless, from a security perspective, functioning in kernel-space comes with its own hazards. A misstep in this environment – like an erroneous update to a kernel driver – can result in downtime. If the concerned driver triggers at boot time, during the initial load of the operating system, it can lead to prolonged repercussions, possibly necessitating affected hosts to initiate in a recovery mode to address the issue and facilitate the machines to boot normally.
Sophos’ Intercept X Advanced product incorporates five nucleus operators as of the release 2024.2. All operators undergo thorough testing* with relevant flags activated and deactivated, and are dispatched with new flags deactivated. (Sophos Intercept X and Sophos Central leverage feature flags to gradually allow new functionalities. Feature flags are introduced through Sophos Central. Newly introduced features are typically ‘guarded’ by feature flags – turned off unless the flag is activated – to introduce the feature gradually and potentially adjust it before broader activation.)
In this piece, for the sake of transparency, we shall delve into what those operators are, their functions, startup instances, signing details, and inputs. We shall also probe into some of the protective measures we implement around these operators to minimize the disruption risk (such as phased rollouts, as mentioned earlier; an instance of this will be provided later in the piece), and the choices available to customers in terms of configuring them. It’s also noteworthy that Intercept X Advanced and all its constituents, including the nucleus operators, have been integrated into an external bug bounty initiative since December 14, 2017; we invite scrutiny through external bug bounty submissions, and we foster a cooperative atmosphere with the research community.
* ‘Testing’ entails a variety of internal evaluations, incorporating tools and verifiers provided by Microsoft
The ensuing table offers a summarized view of the five nucleus operators that are part of Intercept X Advanced release 2024.2.
| Operator | Version | Classification | Launch Type | Validated By Microsoft? | Signature | Overview |
| SophosEL.sys | 3.2.0.1150 | Central Driver | Early-Launch Boot Activation | Affirmative | ELAMP* | Sophos ELAM operator: equipped to inhibit execution of malicious boot activation drivers |
| SophosED.sys | 3.3.0.1727 | Data System Operator | Boot Activation | Affirmative | WHCP+ | The primary Sophos anti-malware operator |
| Sntp.sys | 1.15.1121 | Network Filtering Operator | System Initiation | Affirmative | WHCP+ | Sophos Network Threat Protection operator |
| Hmpalert.sys | 3.9.4.990 | Data System Operator | System Initiation | Affirmative | WHCP+ | Sophos HitmanPro.Alert operator |
| SophosZtnaTap.sys | 9.24.6.3 | Network Filtering Operator | As Requested | Affirmative | WHCP+ | Sophos Zero Trust Network Access (ZTNA) Tap operator |
Table 1: An overview of the nucleus operators in Intercept X Advanced2024.2
* Microsoft Windows Early Launch Anti-malware Publisher
+ Microsoft Windows Hardware Compatibility Publisher
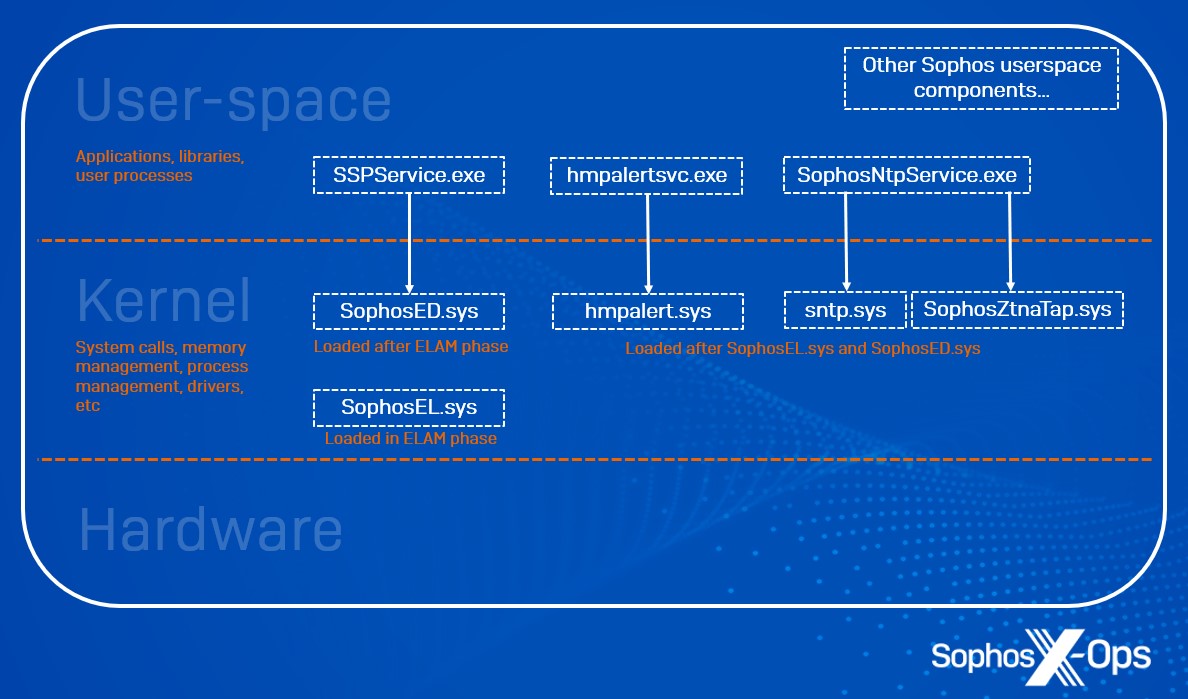
Figure 1: A conceptual representation of user-space/nucleus boundaries and where Intercept X Advanced components function
Functionality: SophosEL.sys acts as the Sophos Early Launch Anti-Malware (ELAM) operator.
Inputs: This operator receives one input – a blacklist of known malevolent operators which must be obstructed from executing as boot activation operators at system startup. This blacklist, situated in the registry key below, is set by Sophos user-space threat detection logic upon detecting a malevolent operator. At the subsequent boot cycle, SophosEL.sys ensures that this operator remains inactive.
| Input | Description | Safeguards |
| HKLMSYSTEMCurrentControlSetServicesSophos ELAMConfig | Blacklist of known malevolent operators | DACLs; Sophos Tamper Protected |
Customer choices: Customers have the option to set up remediation and permitted items in the Threat Protection policy from Sophos Central.
Additional precautions: Any Microsoft or Sophos-signed operator is immune to cleanup/blocking.
Functionality: SophosED.sys (Endpoint Defense) is a boot activation operator, initialized during ELAM processing and ahead of many other nucleus operators loading, Windows user-space being initialized, and the system drive getting mounted. It shoulders three primary responsibilities:
- Ensuring tamper protection for the Sophos setup and configuration
- Revealing system activity events> to Sophos client-space elements for safety and identification
- Documenting system activity events at a low level to the Sophos Event Logs for retrospective forensics and examination
Inputs: As SophosED.sys initiates before the file system becomes accessible, its complete setup is supplied via its service key. Please note that all the inputs listed below are within HKLMSYSTEMCurrentControlSetServicesSophos Endpoint Defense.
Filter driver elevations inputs
SophosED.sys enlists with Windows as a Mini-Filter driver at numerous elevations (a specific identifier that specifies a driver’s position on the ‘stack’ of drivers, with ‘lower’ drivers positioned closer to the hardware) allocated and endorsed by Microsoft.
| Input | Description | Safety |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseInstances | Multiple elevations allocated by Microsoft | DACLs; Sophos Tamper Protected |
Tamper Protection inputs
The configuration of Sophos Tamper Protection is a blend of customer strategies, Sophos feature indicators, and certified manifests embedded within the agent.
| Input | Description | Safety |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionConfig | Client strategy (On/Off, configuration passcode*) | DACLs; Sophos Tamper Protected |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionComponents
HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionServices |
Manifest of safeguarded keys, directories, services, etc. | Certified; authenticated by driver pre-loading |
* The configuration passcode is encrypted using PBKDF2-SHA512 and a cryptographic salt
System Activity Events inputs
The policy of Sophos Central Threat Protection sustains several configuration alternatives which user-space processes of Sophos inscribe to the SophosED.sys registry key for later use when loading the driver.
| Input | Description | Security |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseScanningConfig | Client policy (On/Off, exceptions, and numerous more) | DACLs; Sophos Tamper Protected |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEndpointFlags | Sophos feature flags (various) | DACLs; Sophos Tamper Protected |
Event Log inputs
| Input | Description | Security |
| HLKMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEventJournalConfig | Client policy (exceptions, disk limits) | DACLs; Sophos Tamper Protected |
| HLKMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEventJournalFeatures | When a subkey exists with a DWORD value Enabled =1, event journals are activated | DACLs; Sophos Tamper Protected |
Client choices: Customers can configure disk limits and handle exclusions in the Sophos Central Threat Protection policy.
Supplementary actions: If a driver utility is available (based on a mix of Client Policy plus Sophos flag), then processes in the user-space can configure varied parameters dynamically:
- A bit pattern of mitigations to apply per process
- Which events to activate or deactivate for each process
- The duration for which the driver should pause for a response from user-space (or whether it should be an asynchronous notification).
What it operates: Sntp.sys (Sophos Network Threat Protection) is a core driver that registers for different Windows Filtering Platform events to intercept and possibly alter network flow data. Depending on the features enabled by Sophos Central Threat Protection and Web Control policies, distinct filters and callouts are enlisted.
Inputs: Feature setup is transmitted to the driver from one or more of the subsequent user mode processes:
- SophosNtpService.exe
- SophosNetFilter.exe
- SophosIPS.exe
- SSPService.exe
User-space processes interact with the driver via the Windows Driver Framework, utilizing IOCTLs, Read, and Write. Communication to and from the driver is secured, only permitting connections from authorized and genuine Sophos processes.
Client choices: The filter driver intercepts network traffic by browser and non-browser processes based on the regulations specified in Sophos Central. The processing of the intercepted traffic is executed in user-space by SophosNetFilter.exe and SophosIPS.exe, which might forward modified data back to the driver (e.g., to exhibit a warning page for malicious content).
Supplementary actions: Clients can insert individual sites into their allow or block listing in Sophos Central.
What it operates: Hmpalert.sys ensures Sophos CryptoGuard, which recognizes and limits massive encryption of files by ransomware. It also configures the execution of exploit mitigations as processes are launched.
Inputs: Hmpalert.sys incorporates several inputs, encompassing various registry subkeys and IOCTLS.
| Input | Description | Security |
| HKLMSYSTEMCurrentControlSetServiceshmpalert | Software setup | DACLs; Sophos Tamper Protected |
| HKLM SYSTEMCurrentControlSetServiceshmpalertConfig | Client policy | DACLs; Sophos Tamper Protected |
| HKLM SYSTEMCurrentControlSetServicesSophos Endpoint DefenseEndpointFlags | Sophos feature flags (various) | DACLs; Sophos Tamper Protected |
Client options: Customers can enable/disable exploit mitigations and manage exclusions in the Sophos Central Threat Protection policy.
Supplementary actions: N/A
What it operates: SophosZtnaTap.sys is a custom-built OpenVPN TAP driver from Sophos. When the client deploys the Sophos Zero Trust Network Access (ZTNA) agent, the driver seizes DNS inquiries for managed applications and redirects the traffic for those applications to the relevant Sophos ZTNA gateways. ZTNA applications and gateways are configured through Sophos Central policies and preserved in the registry.
Inputs: Inputs into SophosZtnaTap.sys arrive via a registry subkey.
| Input | Description | Security |
| HKLMSOFTWARESophosManagementPolicyNetworkPerimeter | DACLs; Sophos Tamper Resistant |
Client choices: Consumers have the ability to oversee their ZTNA-secured applications and gateways from Sophos Central.
Further actions: Not applicable
Sophos CryptoGuard has shielded against extensive encryption on fixed drives for more than a decade. Intercept X version 2024.1.1 presented a new functionality, CryptoGuard ExFAT, which broadens this defense to ExFAT partitions (commonly found on detachable USB drives).
The development and testing of CryptoGuard ExFAT occured from September 2023 to March 2024. This feature was protected by the identifier ‘hmpa.cryptoguard-exfat.available.’
Sophos Engineering trialed the software internally with the identifier activated (our ‘Dogfood release’) commencing on March 22, 2024.
Intercept X version 2024.1.1 was distributed to Sophos, then to consumers utilizing our progressive software deployment process, between May 21, 2024 through June 6, 2024. At this point, the feature remained inactive for everyone except Sophos engineers.
The ‘hmpa.cryptoguard-exfat.available’ identifier was activated using our staged identifier enablement process, between June 10, 2024 through June 26, 2024.
Consumers have the option to choose a fixed software version (Endpoint Software Management: Fixed-tenure support, Long-term support). This locks the software and identifiers until the consumer selects an alternative software package. Consumers who opt for the ‘Sophos recommended’ alternative receive new software periodically. In addition to software deployments, they also receive gradual identifier activations for novel features in the software, as is customary with a typical software release. Sophos has refined this process to enhance stability and prevent the global activation of new events for all consumers.
Kernel drivers are crucial to the Intercept X Advanced product – and to sturdy Windows endpoint security, in general – but we also understand that operating in kernel-space carries inherent risks.
In this write-up, we have delved into the kernel drivers in Intercept X Advanced (as of release 2024.02), their functionalities, their signing, their inputs, the oversight consumers possess over their management, and the additional protective measures we have implemented – which include gradual, phased rollouts of new features, and exceptions to reduce the risk of disruptions.
While no protective measure can completely eliminate risk, we wanted to provide an in-depth overview of our drivers for the sake of transparency, and to elaborate on how we tackle the intricate challenge of safeguarding our consumers from threats in the most secure manner possible.