
A latest study from Mandiant, a division of Google Cloud, unveils that a financially driven threat actor known as UNC5537 collected and removed data from approximately 165 organizations’ Snowflake customer instances. Snowflake is a cloud-based data platform utilized for storing and processing large quantities of data.
The cybercriminal managed to obtain these data by activating credentials that were previously stolen by infostealer malware or acquired from other hackers.
As stated by Mandiant, the threat actor UNC5537 markets victim data on cybercrime forums and pressures many of the victims for payment. Once the data is sold, any cybercriminal could purchase this information for various purposes like cyber espionage, competitive intelligence, or more profit-driven fraud.
Methods used to target Snowflake users for this data theft and extortion
A joint declaration provided by Snowflake, Mandiant, and cybersecurity firm CrowdStrike suggests there is no proof indicating that the fraudulent activity was due to a vulnerability, misconfiguration, or breach of Snowflake’s platform. There is also no indication that the activity stemmed from compromised credentials of current or former Snowflake employees.
Instead, evidence points to the attackers acquiring credentials from numerous infostealer malware operations that infected systems not owned by Snowflake. The threat actor then accessed the compromised accounts, allowing the extraction of a substantial amount of customer data from the respective Snowflake customer instances.
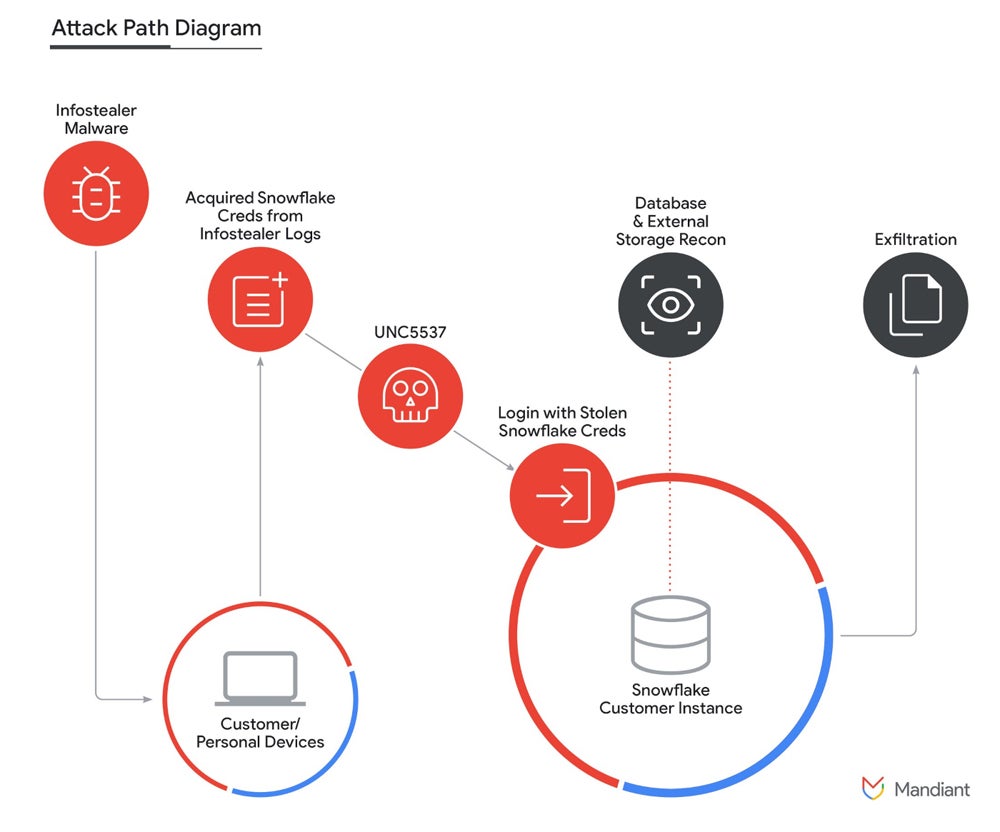
Mandiant researchers revealed that most of the credentials utilized by UNC5537 were sourced from past infostealer malware; some of these credentials trace back to November 2020 but were still effective. Various infostealer malware families contributed to the theft of credentials — the most prominent ones being Vidar, Risepro, Redline, Racoon Stealer, Lumma, and Metastealer.
According to Mandiant and Snowflake, at least 79.7% of the accounts exploited by the threat actor had previous occurrences of credential exposure.
Mandiant also disclosed that the initial compromise by infostealer malware took place on contractor systems that were also used for personal activities, including gaming and downloading pirated software, which serves as a highly effective channel for spreading infostealers.
Means by which UNC5537 acquired the stolen credentials
Reportedly, the threat actor acquired credentials from various infostealer malware, nevertheless, UNC5537 also made use of credentials acquired from previous transactions.
Although Mandiant did not provide any further details, it is plausible to assume that these credentials were procured in one or more cybercriminal underground markets directly through so-called Initial Access Brokers, who are a class of hackers selling stolen corporate access to other fraudulent parties.
As outlined in Mandiant’s report, “the underground infostealer economy is also highly active, with extensive lists of stolen credentials available for free or sale both on and off the dark web.” Mandiant also stated that, in 2023, 10% of overall intrusions started with stolen credentials, marking it as the fourth most significant initial intrusion approach.
Initial access and data extraction methods in this Snowflake attack
In this assault campaign, the initial access to Snowflake customer instances often took place through the native user interface accessible via the web (Snowflake SnowSight) or through the command-line interface tool provided by Snowflake (SnowSQL). Additionally, an attacker-developed tool known as “rapeflake” and identified as FROSTBITE by Mandiant has been utilized for conducting reconnaissance on Snowflake instances.
FROSTBITE exists in at least two variants: one utilizing .NET for interaction with the Snowflake .NET driver, and another version using Java to communicate with the Snowflake JDBC driver. This tool enables the attackers to carry out SQL operations like user listing, current roles, IP addresses, session IDs, and organizational names.
A publicly available tool for database management, DBeaver Ultimate, has also been harnessed by the threat actor to execute queries on the Snowflake instances.
With SQL queries, the threat actor managed to extract information from databases. Once valuable data was identified, it was compressed using the “COPY INTO” command in GZIP format to lessen the data size for extraction.
The attacker primarily employed Mullvad and Private Internet Access VPN services to reach the victims’ Snowflake instances. Moreover, a Moldovan VPS provider called ALEXHOST SRL was used for data exfiltration. The threat actor stored victim data on diverse international VPS providers and the cloud storage service provider MEGA.
Which companies are susceptible?
An assault initiative appears to be directed towards Snowflake users who rely solely on single-factor authentication. Those utilizing multifactor authentication are immune to this offensive move and were not singled out.
Furthermore, the affected Snowflake client instances lacked authorization restrictions to exclusively permit connections from trusted sources.
Guidance from Snowflake on safeguarding your enterprise against this digital security threat
Snowflake has publicized guidance on identifying and halting unauthorized user entry.
The corporation shared a catalogue of almost 300 dubious IP addresses utilized by the malicious actor and offered a query to pinpoint activities from the suspect IPs. They also presented a query for recognizing the utilization of the “rapeflake” and “DBeaver Ultimate” utilities. Any user account yielding findings from these queries should be promptly deactivated.
Snowflake strongly recommends enhancing security measures:
- Enforce MFA for users.
- Establish network policies at both account and user levels for esteemed users/service accounts.
- Inspect account settings to restrain data exports from Snowflake accounts.
- Monitor Snowflake accounts for unauthorized elevation of privileges or configuration alterations and probe such incidents.
It is highly encouraged to keep all software and operating systems current and patched to deter potential compromise due to a prevalent vulnerability that may result in credential exposure.
Implement security solutions on all endpoints to halt infostealer infiltration.
It is also recommended to boost knowledge on computer security and educate personnel on detecting and reporting dubious digital security occurrences.
Disclaimer: I am affiliated with Trend Micro, however, the opinions articulated in this article are personal.




