Qilin partners target MSP ScreenConnect admin through spear-phishing, impacting downstream clients

In the final days of January 2025, an administrator of a Managed Service Provider (MSP) received a meticulously crafted phishing email claiming to be an authentication notification for their ScreenConnect Remote Monitoring and Management (RMM) tool. This email enabled Qilin ransomware actors to obtain the administrator’s login credentials, leading to ransomware assaults on the MSP’s clientele.
The threat Intelligence unit at Sophos MDR highly suspects that this occurrence can be linked to a ransomware partner known as STAC4365. This attack employed comparable infrastructure, domain naming conventions, tactics, tools, and methodologies to those utilized in preceding phishing campaigns discovered by Sophos MDR threat intelligence dating back to late 2022. These endeavors featured phishing websites created with the evilginx open-source man-in-the-middle attack framework to gather credentials and session cookies and evade multi-factor authentication (MFA).
In this particular instance, similar to other incidents related to this threat group, the perpetrators deployed fictitious ScreenConnect domains to function as intermediaries for the genuine ScreenConnect login operation. Upon clicking the login link in the email to inspect the authentication, the administrator was redirected to a deceitful phishing site, cloud.screenconnect[.]com.ms, posing as the authentic ScreenConnect login page. By submitting their credentials on the fake ScreenConnect platform, the attackers were able to intercept these inputs. Sophos suspects that the bogus ScreenConnect site relayed the inputs to the real ScreenConnect platform to validate the credentials and capture the time-sensitive one-time password (TOTP) sent by ScreenConnect to the administrator via email.
After intercepting the MFA inputs, the attacker successfully accessed the legitimate ScreenConnect Cloud portal using the administrator’s super admin account. This clearance allowed them to carry out various actions within this ScreenConnect instance and facilitated the execution of the Qilin attack.
Overview: Qilin
Qilin is a Ransomware-as-a-Service program operational since 2022, previously recognized as “Agenda.” The Qilin collective recruits associates on Russian-language cybercrime forums. According to Microsoft Threat Intelligence, new additions to these associates this year include a North Korean state entity designated by Microsoft as “Moonstone Sleet.”
To exert pressure on victims being extorted, Qilin ransomware directs them to a data-leak platform hosted on Tor. By May 2024, this pressure tactic expanded to the public internet when operatives linked to Qilin ransomware launched a data-leak portal named “WikiLeaksV2.” This initiative was hosted on an IP address provided by a Russian Internet service firm with prior associations to command-and-control (C2) activities, malware hosting, and phishing schemes. The platform remains operational and its URL was included in the ransom notes from this incident.
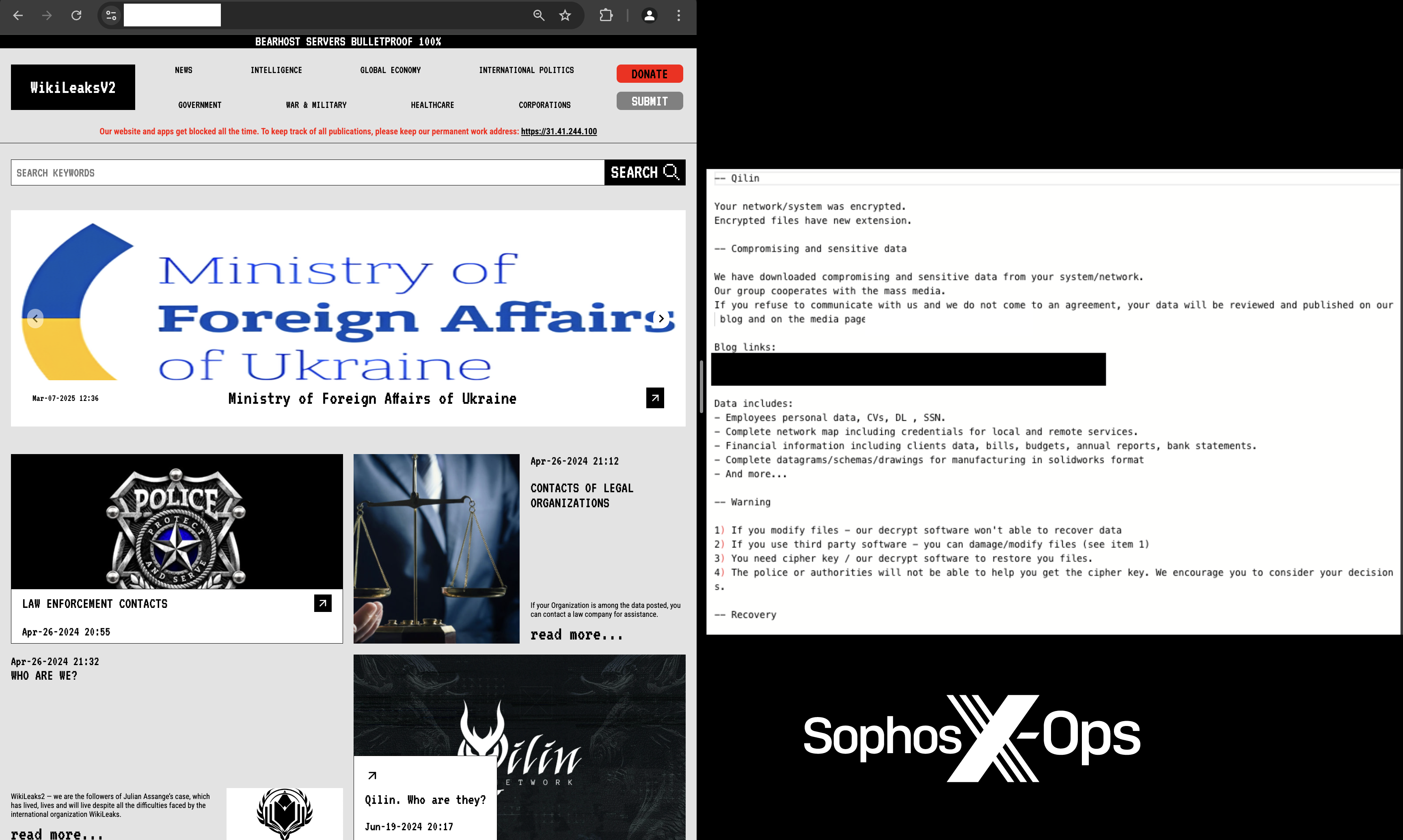
Figure 2: The Qilin data-leak site hosted on Tor presents a QR code and linkage to the WikiLeaksV2 page
Insight: STAC4365
STAC4365 is affiliated with a series of activities and identifiers common among a cluster of phishing sites since November 2022. These sites shared resemblances such as URL structure and domain composition, concentrating on mimicking authentic ScreenConnect URLs.

| Domain | Initial Activity |
| account.microsoftonline.com[.]ec | February 2025 |
| cloud.screenconnect.com[.]ms | January 2025 |
| cloud.screenconnect[.]is | November 2024 |
| cloud.screenconnect.com[.]so | October 2024 |
| cloud.screenconnect.com[.]bo | July 2024 |
| cloud.screenconnect.com[.]cm | July 2024 |
| cloud.screenconnect.com[.]am | April 2024 |
| cloud.screenconnect.com[.]ly | February 2024 |
| cloud.screenconect[.]com[.]mx | January 2024 |
| cloud.screenconnect[.]co[.]za | January 2024 |
| cloud.screenconnect[.]uk[.]com | January 2024 |
| cloud.screenconnect[.]de[.]com | November 2023 |
| cloud.screenconnect.com[.]se | October 2023 |
| cloud.screenconnect.jpn[.]com | October 2023 |
| cloud.screenconnect.com[.]ng | June 2023 |
| cloud.screenconnect.com[.]ph | May 2023 |
| cloud.screenconnect.com[.]vc | May 2023 |
| cloud.screenconnect[.]cl | April 2023 |
| cloud.screenconnect[.]gr[.]com | April 2023 |
| cloud.screenconect[.]eu | January 2023 |
| cloud.screenconnect[.]co[.]com | January 2023 |
| cloud.screenconnect[.]us[.]com | January 2023 |
| cloud.iscreenconnect[.]com | December 2022 |
| cloud.screenconnect[.]app | November 2022 |
Illustration 4: A compilation of domains resembling STAC4365’s behavior pattern
For the setup of these deceptive websites, STAC4365 utilizes evilginx, a freely available adversary-in-the-center assault platform used for seizing credentials and session cookies via phishing techniques and performing as an MFA intermediary.

The most recent iteration, Evilginx2, introduces a” javascriptRedirect” functionality that malevolent actors employ to strategically route traffic. STAC4365 utilizes awstrack[.]me in conjunction with JavaScript redirections to guarantee that only selective targets, accessing the phishing website via the designated profiling link, land on the page for gathering credentials—while those who access directly (like analysts) are steered to the authentic service interface, evading identification and scrutiny. This capability is conventional in other MFA phishing tools, as evidenced by Rockstar and FlowerStorm.
The STAC4365 Qilin offensive sequence
Initial entry
The phishing bait specifically aimed at the Managed Service Provider’s (MSP) admin account, flawlessly mimicking a ConnectWise ScreenConnect login notification:
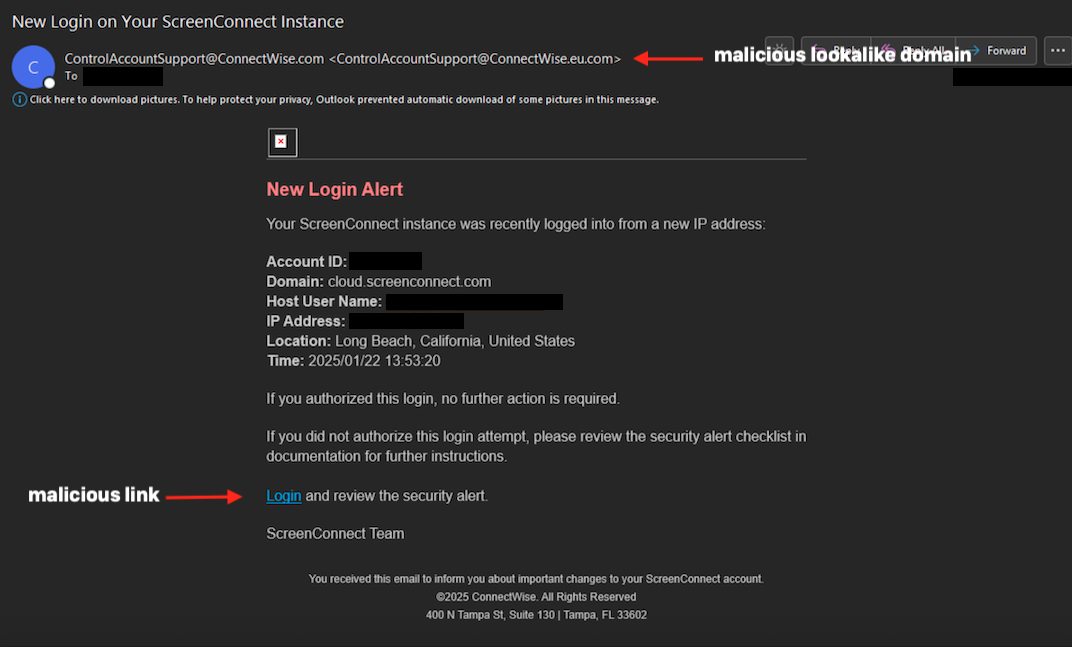
The targeted admin clicked on the “Log in and check the security alert” link, redirecting the victim’s browser to the phishing site through a harmful reroute utilizing Amazon Simple Email Service (SES):
hxxps[:]//b8dymnk3.r.us-east-1.awstrack[.]me/L0/https[:]%2F%2Fcloud.screenconnect[.]com.ms%2FsuKcHZYV/1/010001948f5ca748-c4d2fc4f-aa9e-40d4-afe9-bbe0036bc608-000000/mWU0NBS5qVoIVdXUd4HdKWrsBSI=410
The redirected link resolved to the URI of a domain mimicking ScreenConnect:
hxxps[:]//cloud.screenconnect[.]com.ms/suKcHZYV/1/010001948f5ca748-c4d2fc4f-aa9e-40d4-afe9-bbe0036bc608-000000/mWU0NBS5qVoIVdXUd4HdKWrsBSI=410
This URI was utilized for verifying the target; other accesses to the domain were directed to the legitimate cloud.screenconnect.com. The host at cloud.screenconnect[.]com.ms (186.2.163[.]10) was probably set up as a reversed proxy to the genuine ScreenConnect domain.
By using the captured credentials and the MFA code, the intruder logged into the target’s ScreenConnect subdomain via the ScreenConnect Control Panel and gained entry to the MSP’s remote management system.
Maintenance, Command and Oversight
Shortly after successfully logging into the ScreenConnect environment as the super admin account, the attacker introduced a new ScreenConnect instance utilizing a file labeled ‘ru.msi,’ which deployed a hacker-operated ScreenConnect instance across several of the MSP’s serviced customers.

Revelation, access of credentials, and lateral progression
The infected ScreenConnect platform was employed across various client settings to conduct network discovery, revelation of users, and resetting of multiple user account passwords. The aggressors also utilized the ScreenConnect platform to access various legitimate utilities for gathering further local credentials and executing distant directives, along with employing Windows tools like:
- PsExec
- exe (NetExec from GitHub)
- WinRM
- ScreenConnect platform
In addition, the offenders retrieved a file named “veeam.exe,” an executable designed to exploit CVE-2023-27532, a flaw in the Veeam Cloud Backup service that permits an unauthenticated user to request unencrypted credentials from the local Veeam configuration database. The filename, path, and SHA256 digest of this file match one documented in a 2023 cyber intrusion reported by Huntress, which also utilized ScreenConnect but did not lead to ransomware deployment.
Gathering
Subsequent to the revelation and lateral advancement stages, the attacker initiated dual extortion tactics by leveraging the manipulated accounts to recover files from multiple customer environments using WinRAR.

Data Removal
Post data retrieval using WinRAR, the offenders transferred the .rar archives to easyupload.io through an Incognito tab on Google Chrome.
Avoidance of Detection and Outcome
Throughout the breach, the offenders employed various techniques to evade detection and conceal their actions. When accessing EasyUpload on Google Chrome, they utilized the Incognito mode to obscure forensic traces. They also eliminated utilities post usage, such as WinRAR.
Through the malicious ScreenConnect platform, the offender ensured identification and targeting of backups at varied customer sites to impede service restoration and enhance the likelihood of ransom compliance. Moreover, they altered diverse boot settings to ensure the targeted devices booted into Safe Mode with networking.
Eventually, they exploited the compromised accounts to deploy Qilin ransomware across several client environments.
Upon analyzing the ransomware binary retrieved by the MDR team, SophosLabs identified the following features:
- Disable and halt Volume Shadow Copy Service (VSS) service
- Enable symbolic links
- Enumerate hosts
- Erase shadow copies
- Erase Windows Event Logs
- Change wallpaper to ransomware message
- Delete itself after execution
While the same ransomware binary affected multiple client environments, each client had a distinct 32-character password associated with ransomware execution.
Observe the unique endings of the obscured passwords in the snapshot below:
Furthermore, the ransomware’s readme files contained unique chat IDs for each client, indicating that the threat actor was aware of targeting multiple organizations and clients.

Suggestions for protectors
Managed service providers heavily depend on external applications and services to carry out their operational duties for client organizations. Ransomware perpetrators focus on these services for the same reason—they have become an increasingly popular pathway for subsequent attacks on MSP clients. Hence, it is crucial for MSPs and companies of all sizes that make use of these services to comprehend the risk elements involved and implement measures to reduce them.
Adversaries with legitimate administrative privileges and access can be hard to thwart, especially when it comes to data exfiltration. However, there are actions organizations can take to hinder the initial compromise of critical credentials and obstruct the operation of ransomware.
The breach in this scenario originated from well-targeted phishing and the interception of an MFA TOTP. The attackers utilized a replica domain and a skillfully crafted email to lure the victim into clicking the link. Defenders should integrate evaluations into organizational phishing education to aid users in identifying replica and other dubious domains. Additionally, ensure that your email solution either pinpoints or prevents incoming messages that do not pass a Domain-based Message Authentication, Reporting and Conformance (DMARC) verification.
The phishing incident in this case involved an AITM phishing kit to pass on credentials and a TOTP to procure a valid session. Whenever feasible, organizations should restrict access to corporate applications and third-party services to identified managed devices through conditional admission, and transition to phishing-resistant authentication services (such as those based on FIDO 2).
In this assault, the perpetrator configured systems to reboot in safe mode to circumvent endpoint security measures. Businesses should deploy resistance against safe boot restarts without endpoint protection. Sophos clients can achieve this by activating proactive attack upgrades in Sophos Central through Endpoint and Server Threat Protection policies.
Signs of intrusion for STAC4365 and Qilin are detailed on the Sophos GitHub page here.