
Perimeter 81 in BriefOur score: 3.9 out of 5 stars
|

Perimeter 81 is a cloud-native network security tool crafted to enhance security within corporate networks. The platform moves beyond traditional VPNs and firewalls, featuring a global presence with 50+ locations worldwide and a diverse array of security functionalities. Notable components include a zero-trust framework, advanced malware shielding, and device posture verification.
For more insights on Perimeter 81 as a network security solution, keep on reading.
Perimeter 81 Plans and Pricing
Perimeter 81 presents four payment options: Essentials, Premium, Premium Plus, and Enterprise.
Here is a brief comparison of their attributes and costs:
| Plans | Essentials | Premium | Premium Plus | Enterprise |
|---|---|---|---|---|
| Cost | $8 per user per month. | $12 per user per month. | $16 per user per month. | Contact for a quote. |
| Users | Minimum 10 users. | Minimum 10 users. | Minimum 20 users. | Minimum 50 users. |
| Unrestricted network tunnels | Yes | Yes | Yes | Yes |
| Split tunneling | Yes | Yes | Yes | Yes |
| No | Yes | Yes | Yes | |
| Retention of Logs | 14 days. | 30 days. | 30 days. | 60 days. |
| Exclusive chat and email assistance | Only available during official hours. | Response prioritized. | Response prioritized. | 24/7 |
The pricing model of Perimeter 81 resembles that of some of its rivals, such as NordLayer. For instance, the yearly charge in the Premium and Premium Plus brackets amounts to $12/user/month and $16/user/month correspondingly. In contrast, the Core and Premium tiers in NordLayer are priced at $11/user/month and $14/user/month respectively.
When compared directly with Twingate, whose highest rate for annual billing is $10/user/month, Perimeter 81 appears more costly.
While there is no trial period offered, I applaud Perimeter 81 for providing a 30-day refund guarantee for all their plans. Additionally, I admire the option for potential buyers to request a demonstration session for a 15-minute virtual tour of the VPN.
SEE: Free VPN vs Paid VPN: Which One Is Right for You? (TechRepublic)
Is Perimeter 81 safeguarded?
Indeed, I have found Perimeter 81 to be a secure and sound VPN software solution. Perimeter 81 offers numerous advanced security elements that position it as a secure VPN solution for various businesses. By employing multi-factor authentication (MFA), the tool requires personnel to navigate through a complex sign-in process before accessing a company’s assets.
As an enterprise tool, I acknowledge the presence of unified sign-on in Perimeter 81, which can be seamlessly integrated with enterprise services like Azure, Google Suite, LDAP, or OKTA to facilitate secure access for remote staff. However, it’s worth noting that SSO is not included in the Essentials package — this should be considered when evaluating their subscription options.
The platform also utilizes AES-256 encryption with IPsec or WireGuard protocols and supports security features like split tunneling, web filtering, a firewall, and an Always-On VPN feature. Another significant security component is Automatic Wi-Fi protection, which prevents employees from connecting to corporate assets if their connection is compromised.
SEE: 10 Ways a Zero Trust Architecture Protects Against Ransomware (TechRepublic)
One concern I have regarding the safety of Perimeter 81 relates to their data retention policy. While the provider retains IP log data for up to 60 days before deletion, they claim that only the workspace administrator can access this data.
Prominent attributes of Perimeter 81
Below are some standout features of Perimeter 81 that caught my attention.
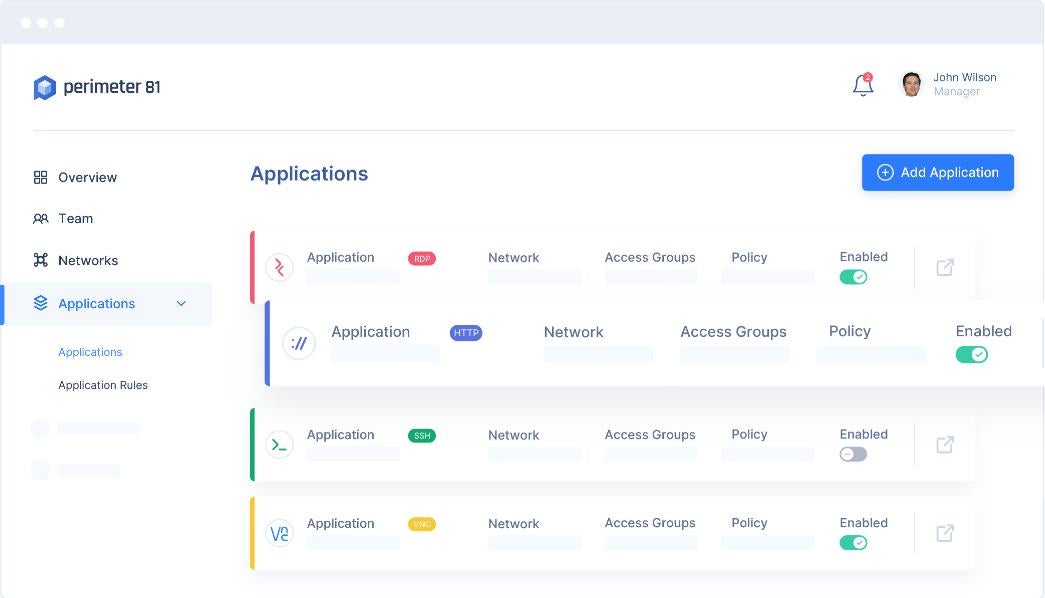
Agentless software access
One standout feature of Perimeter 81 is its Agentless Zero Trust Network Access. This functionality allows limited access to company networks for employees or third-party contractors. It permits specific employees to access a particular application through their browser, rather than granting access to the entire corporate network. This feature assists administrators in monitoring employee and third-party contractor access to corporate networks, tracking where and how access is granted.
SEE: How to Create an Effective Cybersecurity Awareness Program (TechRepublic Premium)
Domain Name System (DNS) Filtration
Another noteworthy component within Perimeter 81 is its DNS Filtration feature. This capability restricts user access to unauthorized websites that could jeopardize a company’s network infrastructure. It aids IT teams in determining which content or IP addresses should be whitelisted or blacklisted on employees’ devices.
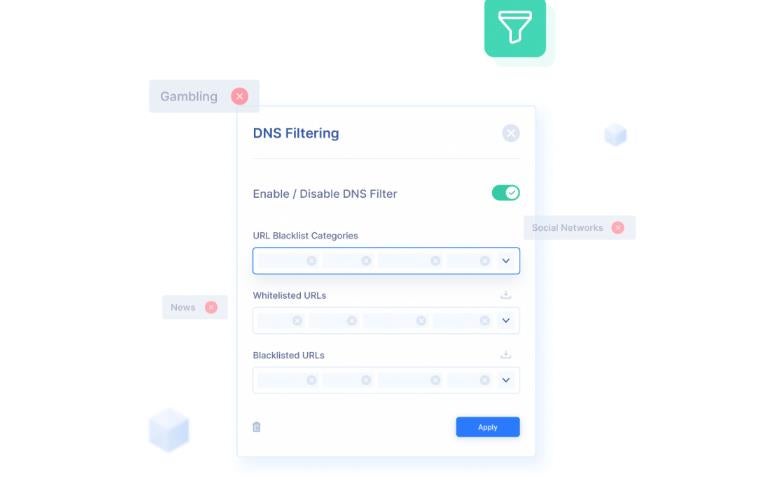
This could be particularly advantageous for businesses with hybrid workforces and fully remote employees.
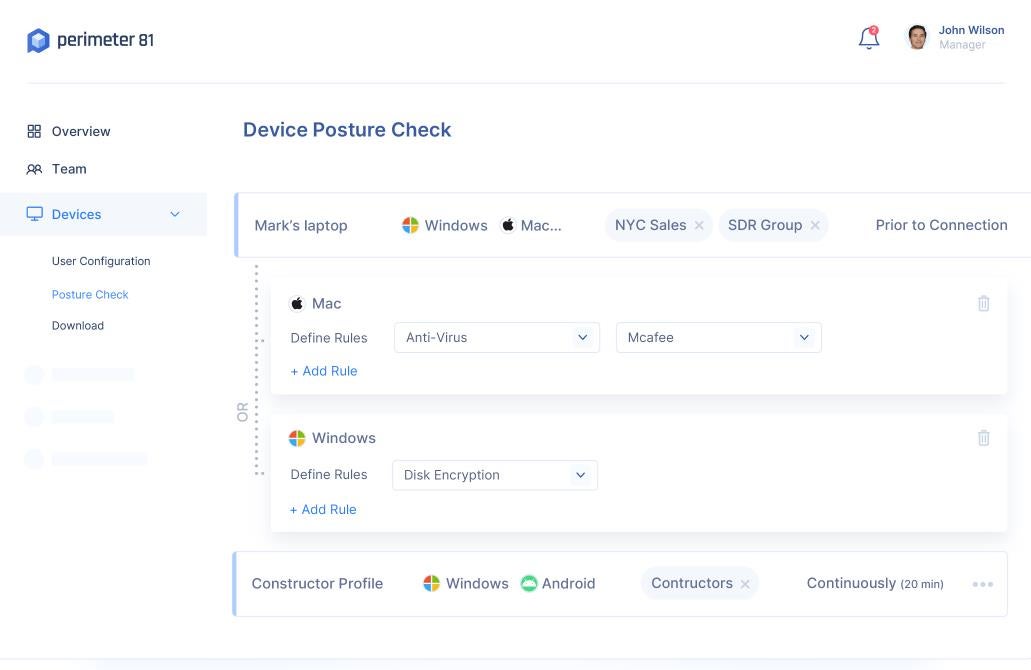
Device Security Status Review
For departments handling sensitive data routinely, a deep dive into Perimeter 81’s Device Posture Check (DPC) is advised. DPC guarantees that the company’s critical resources remain secure by only granting access to devices that align with specific security posture standards. The DPC norms set by Perimeter 81 cater to Android, iOS, Windows, MacOS, and Linux devices before.and whilst accessing the network, eliminate devices when there exists a contradiction between the user policy and device posture.
Enhanced Malware Protection
Regarding traditional threat protection, the Advanced Malware Protection by Perimeter 81 proves to be a valuable asset. Employing a mix of signature-based identification, heuristics, and cutting-edge machine learning, it effectively detects and blocks malware as well as zero-day attacks. I particularly value its ability to empower administrators in effortlessly monitoring user exposure to harmful content through comprehensive reports.
VIEW: Guidance on Verifying Your VPN’s Proper Functioning (TechRepublic)
Which platforms, ID providers, and cloud solutions is Perimeter 81 compatible with?
From my investigation, Perimeter 81 is compatible with all the major operating systems and devices. In particular, it offers support for the following:
- Windows 10 onwards.
- macOS 11 onwards.
- Linux 7 onwards.
- iOS 15 onwards.
- Android 8.1 onwards.
In terms of well-known enterprise applications and cloud services, Perimeter One aligns with Amazon AWS, Google Cloud, and Microsoft Azure. Appreciatively, for identity providers and SAML 2.0 providers, I commend Perimeter 81 for its wide-ranging support. Currently, it is compatible with:
- Google.
- Auth0.
- Azure AD.
- ADFS.
- Rippling.
- Okta.
- OneLogin.
- JumpCloud.
- PingIdentity.
- PingFederate.
A quick note, the above compilation represents Identity Providers supported as of October 2024.
Perimeter 81 advantages
- The user interface is straightforward.
- Integrates seamlessly with numerous third-party solutions like Azure, Google Suite, LDAP, and OKTA.
- 50+ worldwide data centers.
- Provides unsegmented network access.
- Compatible with various platforms and operating systems.
- Offers a 30-day money-back guarantee.
Perimeter 81 disadvantages
- No free trial or free version available.
- Essential security features not included in certain plans.
- Retains IP logs for up to 60 days based on the plan.
Who can benefit from Perimeter 81?
I suggest Perimeter 81 for medium to large enterprises with staff requiring secure remote network access. Through my evaluation, Perimeter 81 may not suit smaller businesses unless they are open to investing in higher-tier plans to access its complete security offerings.
Alternatives to Perimeter 81
While Perimeter 81 can serve as a viable security solution for the majority of organizations, there are alternative options worth exploring if Perimeter 81 doesn’t align with your requirements. Below, I have scrutinized two alternatives which I consider to be suitable replacements.
NordLayer

NordLayer represents a secure remote access solution from Nord Security. The paid subscription of NordLayer enables the establishment of secure connections between remote devices and corporate networks. An advantage that NordLayer boasts over Perimeter 81 is the 24/7 live/email support available across all its plans. Perimeter 81 offers live support exclusively on higher-tier plans.
Twingate

If you are a small team or an individual on a budget looking for a quality network security alternative to Perimeter 81 offering a free plan, Twingate could be a solid choice. This tool, a cloud-based service, facilitates secure remote access to organizational networks. Pricing starts from $5/user/month for annual subscriptions. This is notably cheaper compared to Perimeter 81, which starts at $8 per month. Additionally, Twingate features a 14-day free trial across all its premium plans.
VIEW: Various VPN Categories & Optimal Usage Scenarios (TechRepublic)
Evaluative methodology
My assessment of Perimeter 81 is primarily based on user interface, integration capabilities, and security attributes. The bulk of the analysis involved gathering details from the Perimeter 81 website, where I assessed and compared their capabilities with other analogous services such as NordLayer and Twingate. Additionally, I delved into user reviews of the product from prominent review platforms to gain insights into user perspectives on the offering.
I assigned a rating to Perimeter 81 utilizing an internal algorithm, resulting in a 3.9 out of 5 stars rating. The evaluation was anchored on Perimeter 81’s standalone performance and in correlation with other contemporary VPN solutions.



