The current excitement surrounding cryptocurrency trading and the substantial amounts of digital riches accumulated (and squandered) in crypto markets serve as a compelling temptation for certain aspiring investors. However, the intricacy of cryptocurrency and decentralized finance (DeFi) schemes derived from it have also crafted an environment where wrongdoers can ensnare victims, utilizing this intricacy to cloak fake apps, malicious contracts, and other ploys that deceive victims into believing they are on the path to wealth while coaxing them into relinquishing more and more currency.
A particular type of scheme that we have previously highlighted, dubbed CryptoRom, involves potential targets being engaged on mobile dating apps, drawn into conversing with someone masquerading as a romantic companion, and gradually brought into a fabricated cryptocurrency investment setup supported by bogus trading apps and websites. Interestingly, while we were delving into that scheme, another case nearly fell into my lap: via a Twitter direct message prompting me to partake in “liquidity mining research.”
This encounter spurred an inquiry that uncovered multiple deceitful operations revolving around “liquidity mining,” a variant of cryptocurrency-driven decentralized finance (DeFi) which, even in its authentic form, is an enormously intricate pursuit. The mechanisms of legitimate liquidity mining offer a convenient facade for traditional swindles reworked for the era of cryptocurrency.
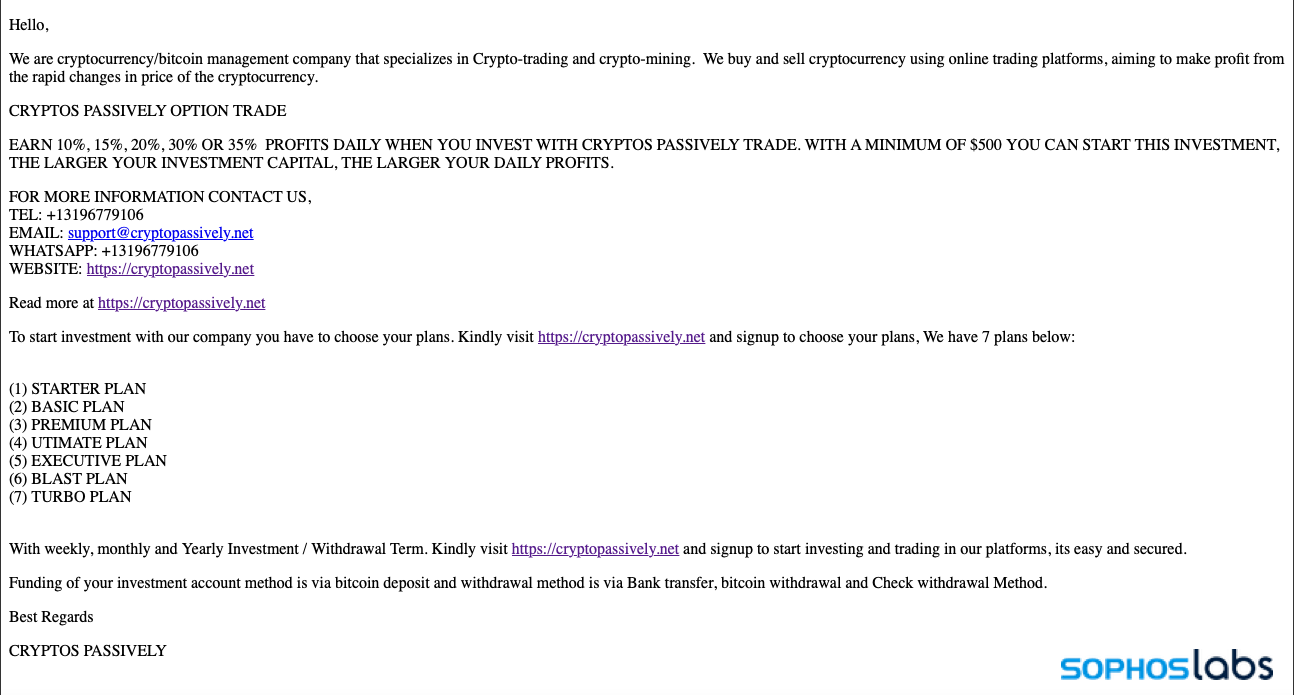
Perpetrators have exploited the intricacies of the genuine practice to disguise a range of scams, enticing victims with the allure of exceptional investment returns. We identified numerous of these rings, predominantly operating out of China, employing a mix of fraudulent blockchain contracts, websites, and applications to drain victims’ crypto wallets while deceiving them into thinking they were generating daily profits. Similar to the other crypto frauds we monitor, these have transitioned from being region-centric in Asia to a worldwide occurrence. During our investigation of one scam, the Washington Post documented a victim’s encounter with another liquidity mining scam that closely mirrored the setup of the CryptoRom swindles we have previously discussed.
Understanding Liquidity Mining
Genuine liquidity mining serves to facilitate decentralized finance (DeFi) networks in automatically executing digital currency transactions. DeFi is an emerging financial technology that utilizes a blockchain-based distributed ledger akin to that utilized by cryptocurrencies to mediate trades between various crypto forms—governed by trading protocols integrated into the ledger itself.
Traditional cryptocurrency exchanges function as “market makers” for transactions from their reserves. Platforms like Coinbase often incentivize prominent investors (with reduced trading fees and other perks) to allocate portions of their holdings to ensure the exchange possesses adequate quantities of widely traded crypto pairs to handle trades efficiently. For instance, for someone looking to convert Ethereum to a stablecoin like Tether (USDT), the exchange must maintain sufficient USDT reserves to execute the trade and complete the transaction. The same principle applies in reverse.
DeFi exchanges handle trades differently—executed by a built-in protocol within their networks known as Automated Market Makers (AMMs). Smart contracts embedded in the DeFi network must swiftly determine the relative values of the traded currencies and carry out the transaction. Given the absence of a centralized crypto pool for these decentralized exchanges to draw from for completing transactions, they rely on crowd-contributed cryptocurrency capital to form a liquidity pool.
To establish the liquidity pool—usually handling trades between a single crypto pair—investors commit equal amounts of both cryptos to the pool, locking them on the blockchain through the smart contract. In return for supplying crypto to the pool, contributors receive rewards based on a portion of the DeFi protocol’s transaction fees. The “mining” aspect refers to liquidity pool tokens (LP tokens)—representations of the investor’s share in the liquidity pool.
The LP tokens essentially function as another cryptocurrency, pegged to the percentage of the pool they represent.
Holding the tokens typically comes with benefits: a share of trading fees and additional rewards. However, there is also the risk of losses—for instance, if the crypto pool’s value plunges, the tokens’ value may drop below the initial investment. As long as the individuals behind the tokens do not abscond with the pool’s assets, investors have a means to exit the scenario.
Regrettably, several pitfalls can arise if the individuals managing the liquidity pool are unethical—or blatantly criminal. DeFi exchanges lack regulation, and the sole assurance of legitimacy lies in the smart contract code integrated into the DeFi network’s (usually Ethereum-based) blockchain. If the tokens get revoked—or if there never was a pool supporting them in the first place—all guarantees are void. This scenario presents ample opportunities for digital Ponzi schemes, counterfeit tokens, and outright theft.
Constructing a Repository of Fabrications
For individuals intrigued by cryptocurrency, numerous unethical and criminal “liquidity mining” schemes exist out there. Similar to the CryptoRom networks we monitor, they utilize various social media and messaging platforms to target potential victims (in addition to spam emails). In certain instances, they also deploy counterfeit mobile apps and websites that imitate or forge connections to more recognized entities in blockchain-based trading.
In our observation, the sales presentations have not emphasized the sentimental aspect greatly—despite indulging, in specific examples, in crafted profiles featuring youthful females to bolster an affective enticement.
As an illustration, consider the man-made profile utilized in the unsought offer I was sent.
The individual managing this Twitter account professed to be a young lady situated in the “United States”:
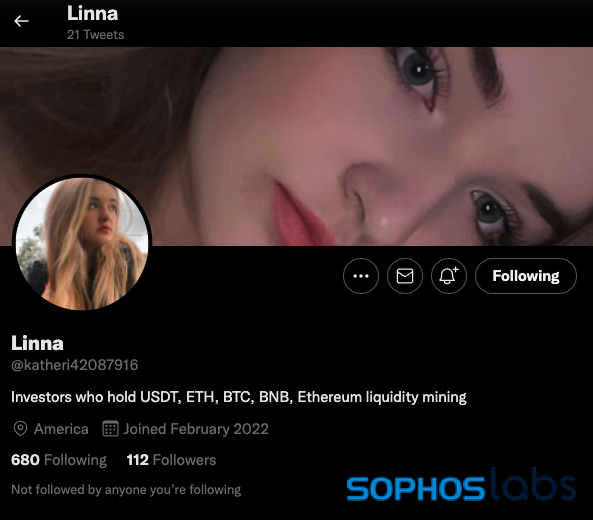
The profile had been arranged just a few weeks prior to the initial direct messages I was sent. The profile’s timeline is brimming with self-portraits and recordings of the woman, who, judging by the context of some photos and posts, appears to be located in Russia. The woman’s images are utilized on multiple Twitter accounts exhibiting indistinguishable content.
Further engagement with “Catherina” resulted in an offer to continue the discussion on WhatsApp or Telegram:
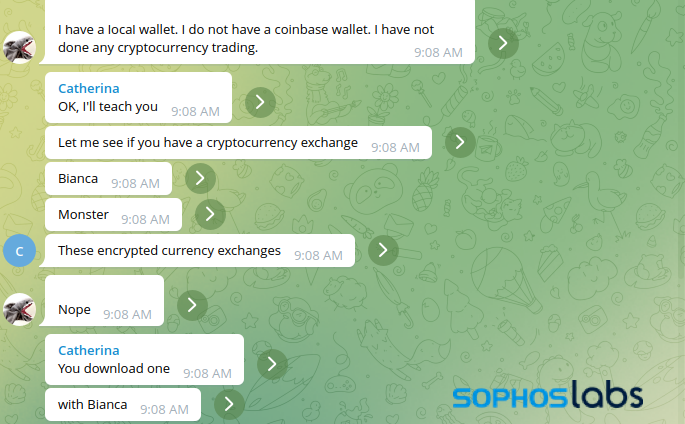
Throughout the discussion on Telegram, the con artist endeavored to instruct me on establishing a Coinbase wallet and depositing Tether (USDT), a “coin” supposedly upheld by securities that mirrors the value of the US dollar.
The screenshot from the Binance app store provided by the criminals exhibited traces of automated translation and displayed Chinese versions of the application. No hyperlink had been included, suggesting that this could be the authentic Binance app in this scenario.
The depiction of the CoinBase Wallet app (another legitimate application) from the Google Play store was in Turkish:
During our exchange, I persuaded “Catherine” to access a canary link—a URL attached to a server I had arranged. The logs revealed that the individual’s IP address was in Hong Kong.
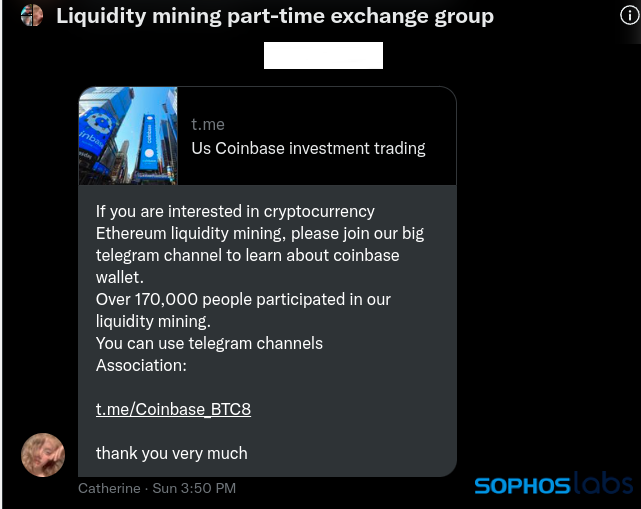
Eventually, “Catherine” directed me to a Telegram group named “US Coinbase Investment Trading” for further insight into joining the “pool.” The identical Telegram group was promoted in a Twitter direct message channel known as “Liquidity mining part-time exchange group”:
The Telegram group shares “updates” about substantial rewards being distributed, along with warnings to disregard any direct messages from other members of the forum due to fraud risks. In messages purportedly originating from a CoinBase representative (@Coinbase_CarlM), the fraudulent group instructs potential victims to follow a URL to register their wallets on the “official block”:
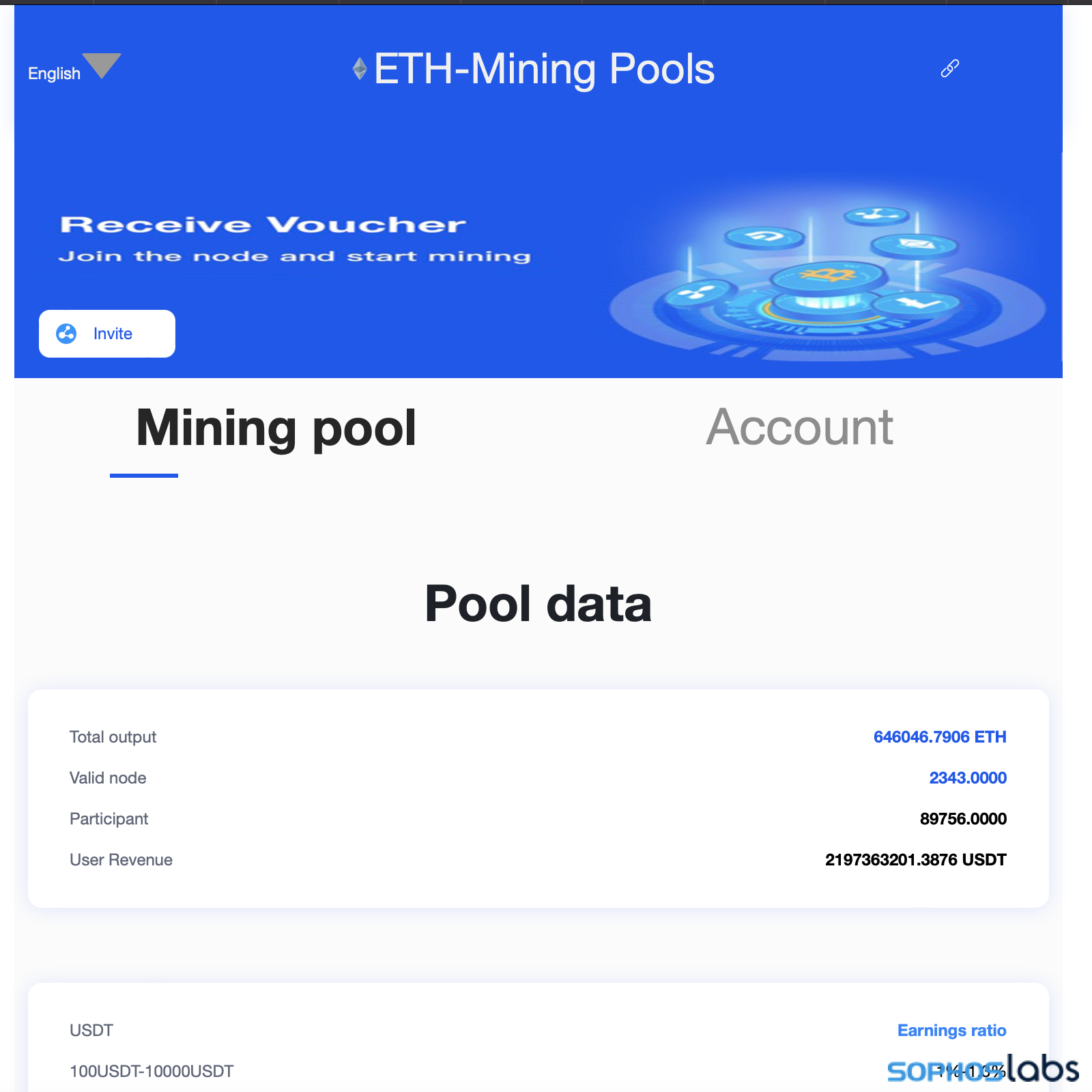
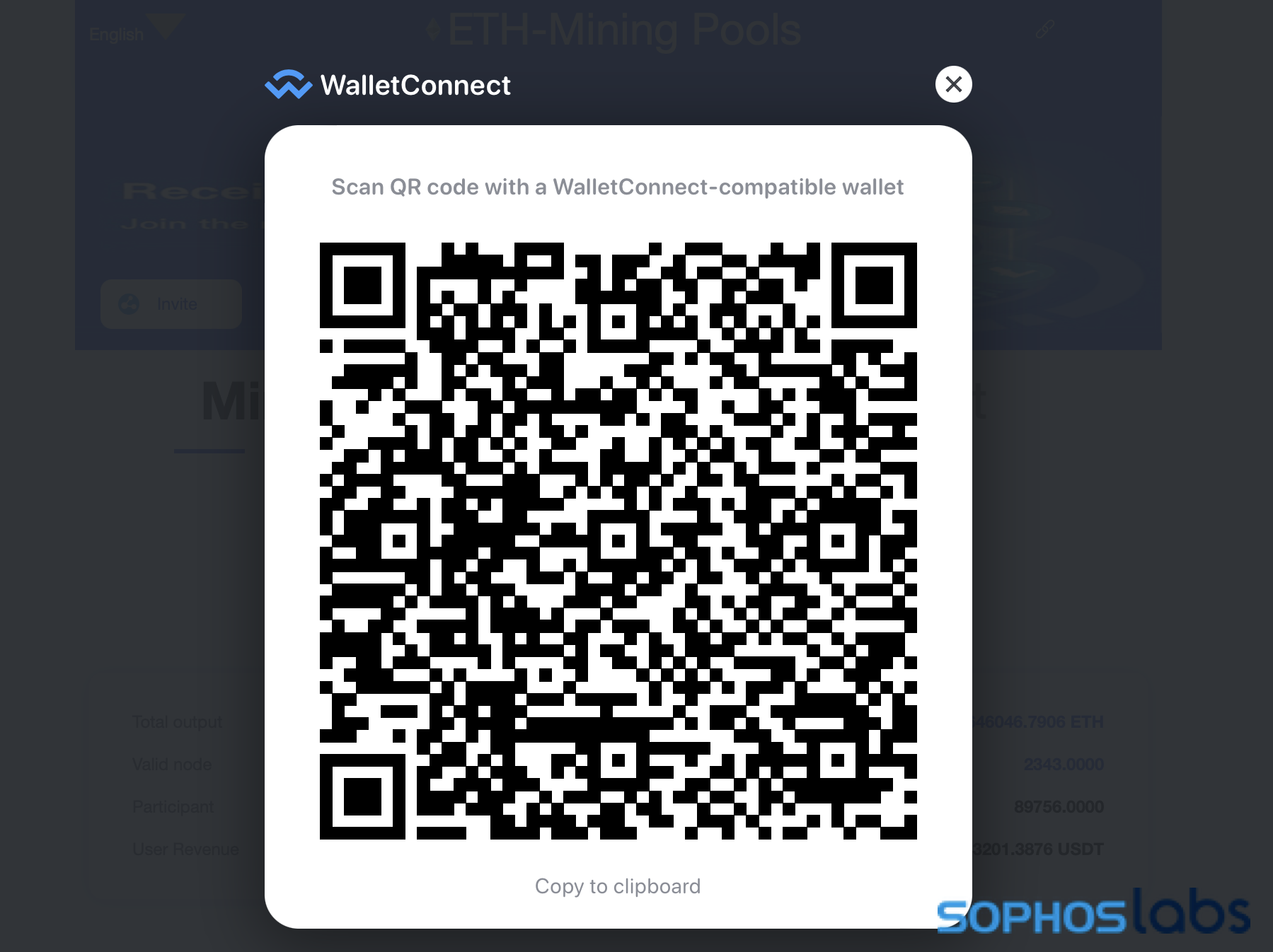
A mobile-optimized website, coinbase-udt[.]cc, is accessed via a link and displays a QR code with a link formatted specifically for crypto wallets that are compatible with the WalletConnect protocol. If the user has a browser wallet extension like MetaMask installed, they will be prompted automatically to establish a connection with their wallet.
The website claims to have produced more than 2 billion USDT (approximately equal to $2 billion US) in “user revenue,” with 2,300 “valid” wallet “nodes” available. Although hosted on Alibaba Cloud in the US, most of the content away from the main page is in Chinese.
Upon linking a wallet, users are assured that they can invite others to earn additional rewards. However, to participate, users need to pay a “blockchain miner’s fee” to acquire a “blockchain certificate” that configures their wallet as a node. Despite the promise, once registered, scammers can withdraw the wallet contents at any time. Users are encouraged to deposit more funds to enhance returns, but they will eventually realize that they cannot withdraw their crypto assets or access any rewards they were promised.
An exploration of domain records revealed numerous similar domain names pointing to the same server:
Wwv[.]trxusdt.vip
eth-usdt[.]group
trxusdt[.]vip
coinbase-usdt[.]cc
ercusdt[.]vip
cyth-usdt[.]com
We have provided information about this particular scam to Coinbase and other relevant entities. However, this is only one of many liquidity mining scams in existence. We are actively gathering data on other scams, including several that leverage fake mobile applications on Android and iOS to create a convincing facade for their fraud.
Ensuring the safety of potential victims
The success of these scams has spawned imitators in the cryptocurrency fraud ecosystem, with each new iteration attempting to expand the pool of potential victims through varied tactics inspired by the CryptoRom/ sha zhu pan playbook.
The absence of safeguards, regulatory oversight, reliable cryptocurrency investment information, and international law enforcement collaboration to dismantle these schemes has provided a shield for well-executed scams. In a world where many rely on social media platforms, WhatsApp, and Telegram for information, scammers have capitalized on these channels to entice and retain victims until they have extracted as much money as possible, particularly targeting vulnerable individuals seeking companionship, wealth enhancement, and online relationships.
To mitigate the proliferation of fraud, educating users is crucial. People must be informed about the existence of these scams and educated on how to identify them. Cryptocurrency exchanges, wallet providers, and other stakeholders should take swift action to block domains and wallets associated with fraudulent activities.
Despite the potential for law enforcement intervention in some instances, dismantling or disrupting these international scams solely through legal means is highly improbable. Significant disruption would necessitate international cooperation, including collaboration with the jurisdictions where these criminal networks operate, such as China. Even if some scams are dismantled, new ones are likely to emerge, supported by extensive networks of web and app developers facilitating criminal entry into fraudulent schemes. Ultimately, enhanced defenses and education are the keys to putting an end to these scams.