The latest initiative aimed at Docker ecosystems with an innovative evasion maneuver

Recent cyberattack focuses on Docker ecosystems through undisclosed methods to covertly mine digital currency, as per security researchers.
Researchers from Darktrace and Cado Security have identified a cyberattack that aims at Docker ecosystems utilizing an innovative method to mine digital currency.
The cyberattack directs itself towards Docker ecosystems to introduce a deceitful node linked to Teneo, a decentralized infrastructure network. Teneo enables users to receive incentives (Teneo Points) by operating Community Nodes that extract public data from social platforms such as Facebook, X, Reddit, and TikTok. These points are convertible to $TENEO tokens. The malware covertly makes profits from social media bandwidth through this process.
The cyber campaign commences with a request to initiate a container from Docker Hub, specifically the kazutod/tene:ten image.
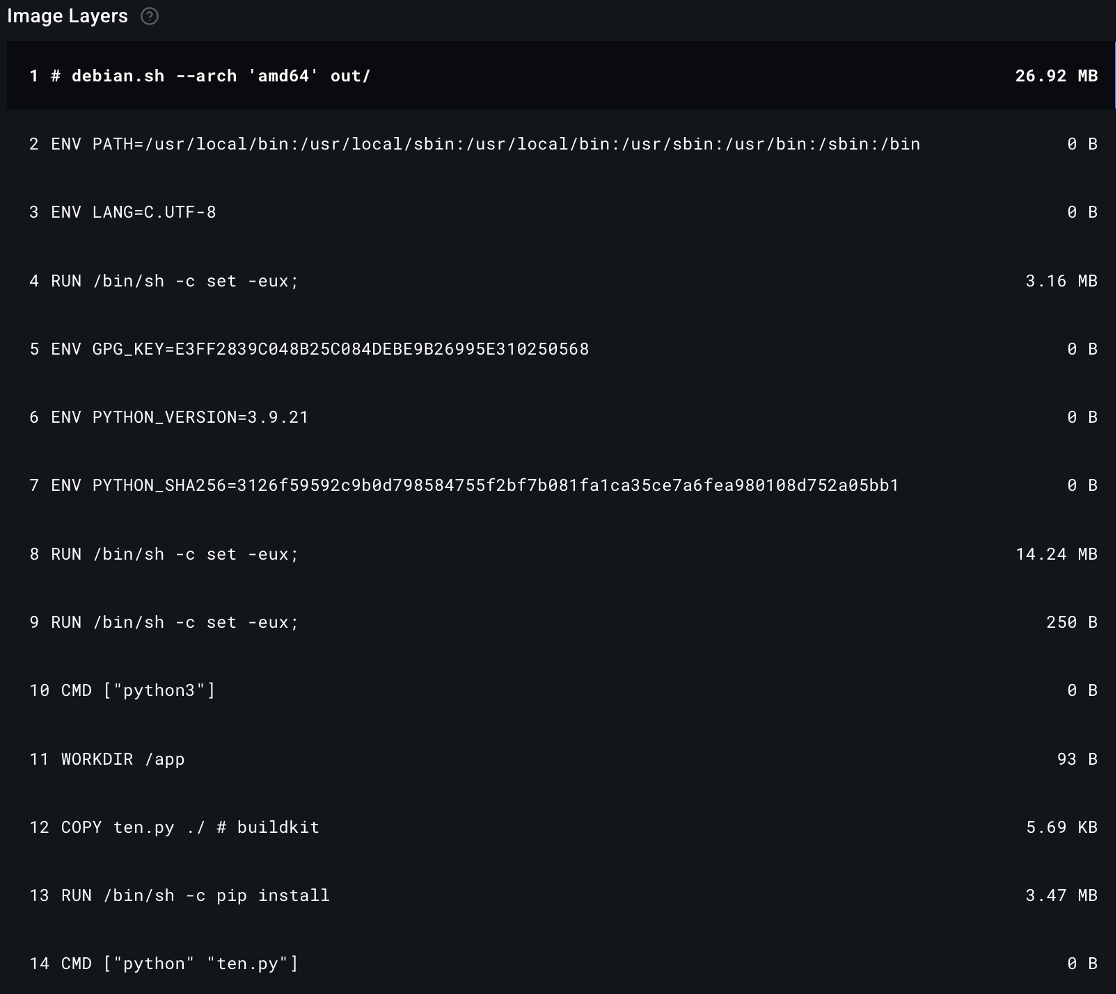
To examine the malicious Docker image kazutod/tene:ten, experts employed Docker tools to extract and conserve it as a tar archive for simplified examination.

Subsequent to unarchiving the tar file, analysts observed that the image is structured in the OCI format, where data is arranged in layers. Each layer is preserved as a tar file with linked JSON metadata, rather than a conventional file system.
“The Docker image employs the OCI format, which differs from a typical file system. Rather than having a fixed collection of files, the image comprises layers. Hence, when utilizing the file command on the sha256 directory, each layer is displayed as a tar file, alongside a JSON metadata file.” highlights the report issued by DarkTrace. “As the detailed layers are dispensable for evaluation, a single command can be employed to dearchive all of them into a unified directory, simulating the container file system structure:”
The analysts dissected the ten.py script embedded in the malicious Docker image and disclosed that it is deeply concealed through multiple layers of base64 encoding, zlib compression, and string reversal. The script deciphers and executes a payload iteratively, each time revitalizing another encoded string for decoding, necessitating 63 repetitions before the actual detrimental code is unveiled. The analysts emphasized that even with the intricate obfuscation process, the decoding procedure was readily automated, indicating that the effort was likely aimed at discouraging casual analysis rather than impeding experts significantly.
The harmful script connects to teneo[.]pro, however, instead of scraping, the malware transmits counterfeit keep-alive signals to acquire “Teneo Points” based on activity levels. This approach facilitates the evasion of common detection methods for XMRig-associated cryptojacking assaults. The attacker’s DockerHub profile implies parallel exploitation of decentralized computational networks. Nevertheless, owing to the exclusive nature of private tokens like Teneo, the profitability of this strategy remains uncertain.
The attacker’s DockerHub profile exposes a trend of misuse, with their most recent container executing a Nexus network client to generate digital currency through distributed zero-knowledge computational tasks.
“Typically, traditional cryptojacking attacks leverage XMRig to directly extract digital currency, nonetheless since XMRig is highly noticeable, attackers are transitioning to alternative approaches for generating digital assets. Whether this is more lucrative remains uncertain. Presently, there is no straightforward method to gauge the revenues of the attackers owing to the more “restricted” attributes of the private tokens.” concludes the report “Mapping a user ID to a wallet address seems unfeasible, and public information about the tokens is scarce.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Docker)







