
ESET Research
ESET researchers uncovered a newly discovered loophole in Telegram for Android that enables the transmission of malignant files disguised as videos
22 Jul 2024
•
,
6 min. read

ESET researchers came across a zero-day loophole affecting Telegram for Android, which surfaced for sale at an undisclosed value in a post on an underground forum dated June 6th, 2024. By exploiting the loophole dubbed EvilVideo, cybercriminals could distribute malignant Android payloads through Telegram channels, groups, and chats, concealing them as multimedia files.
An instance of the loophole was identified, enabling further examination and subsequent reporting to Telegram on June 26th, 2024. On July 11th, Telegram issued an update rectifying the vulnerability in versions 10.14.5 and onwards.
An illustration and explanation of the EvilVideo vulnerability can be observed in Figure 1.
Figure 1. Explanation of the EvilVideo vulnerability
Key highlights from the blogpost:
- On June 26th, 2024, an advertisement for a zero-day loophole targeting Telegram for Android was discovered on an underground forum.
- The vulnerability exploited, named EvilVideo, was promptly reported to Telegram; a patch addressing it was released on July 11th, 2024.
- EvilVideo enables cyber assailants to send malevolent payloads masquerading as video files on unpatched Telegram for Android.
- The loophole is solely effective on Android Telegram versions 10.14.4 and previous iterations.
Exploration
We chanced upon the loophole being advertized for sale on an underground forum: refer to Figure 2.
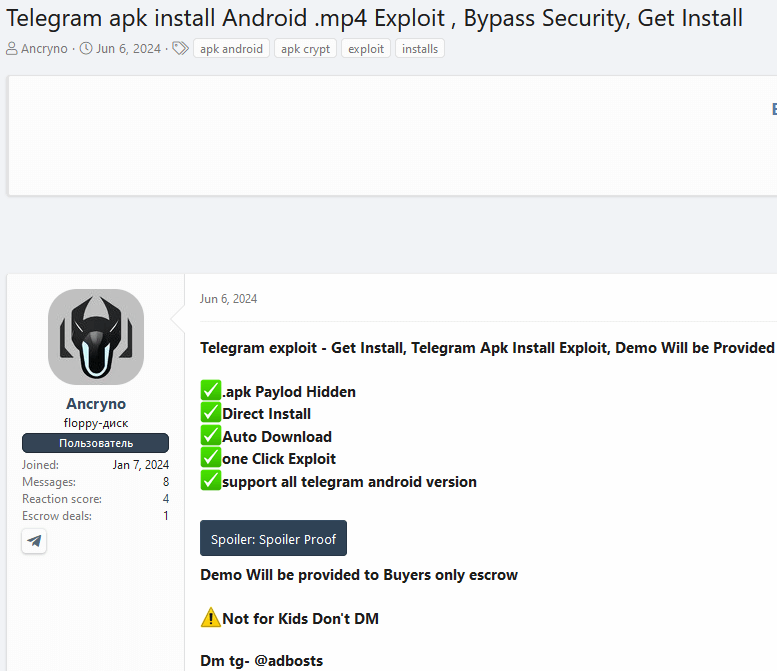
The seller showcased screenshots and a video demonstrating the loophole in a public Telegram channel within the post. Identification of the specific channel allowed us to access the active loophole, enabling us to obtain the payload for testing.
Examination
Our evaluation of the loophole unveiled its functionality on Telegram versions 10.14.4 and preceding versions. It is presumed that the distinct payload was likely crafted leveraging the Telegram API, offering developers the capability to programmatically upload specially designed multimedia files to Telegram chats or channels.
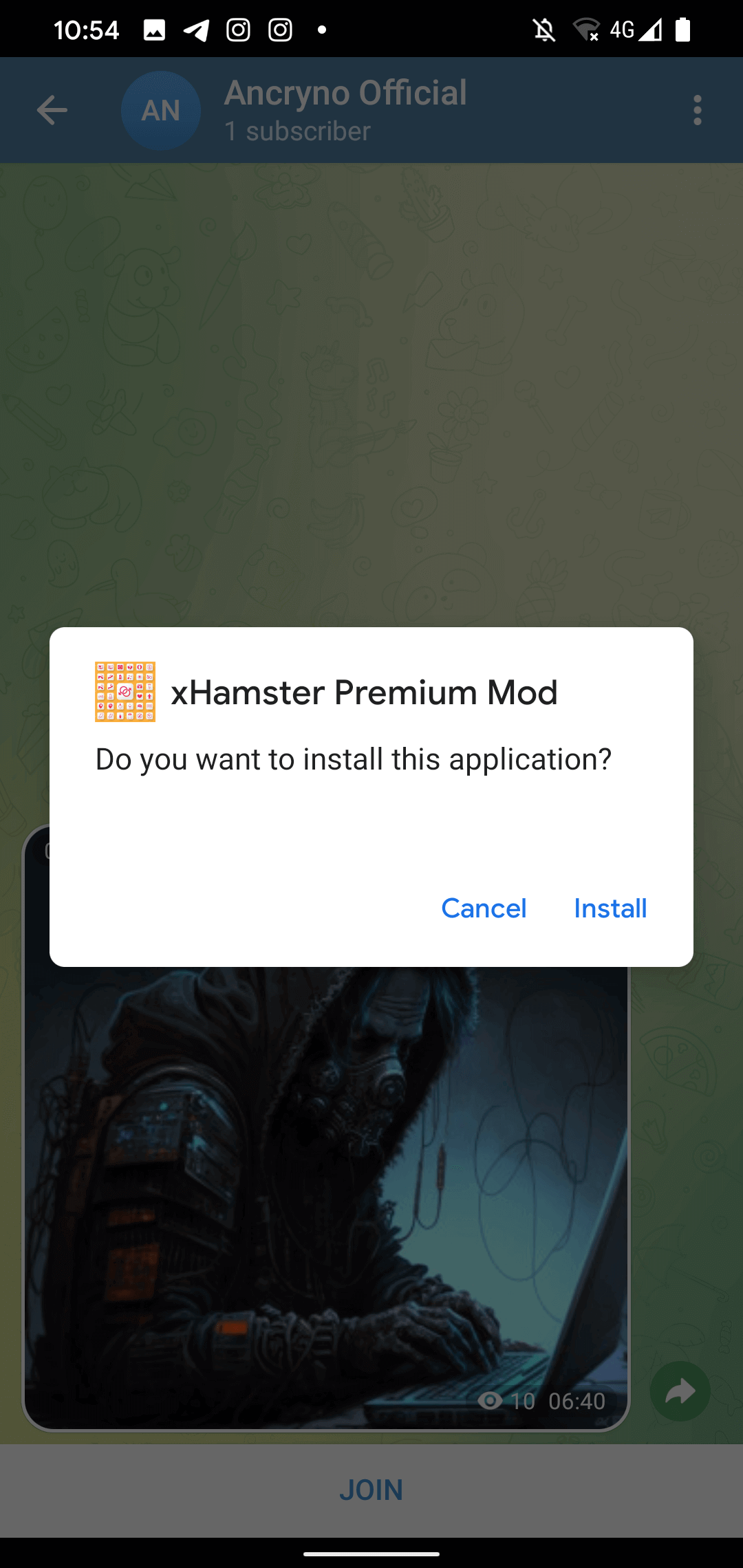
The loophole hinges on the threat actor creating a payload that exhibits an Android application as a multimedia preview rather than a binary attachment. Once shared within a chat, the malignant payload manifests as a 30-second video (Figure 3).
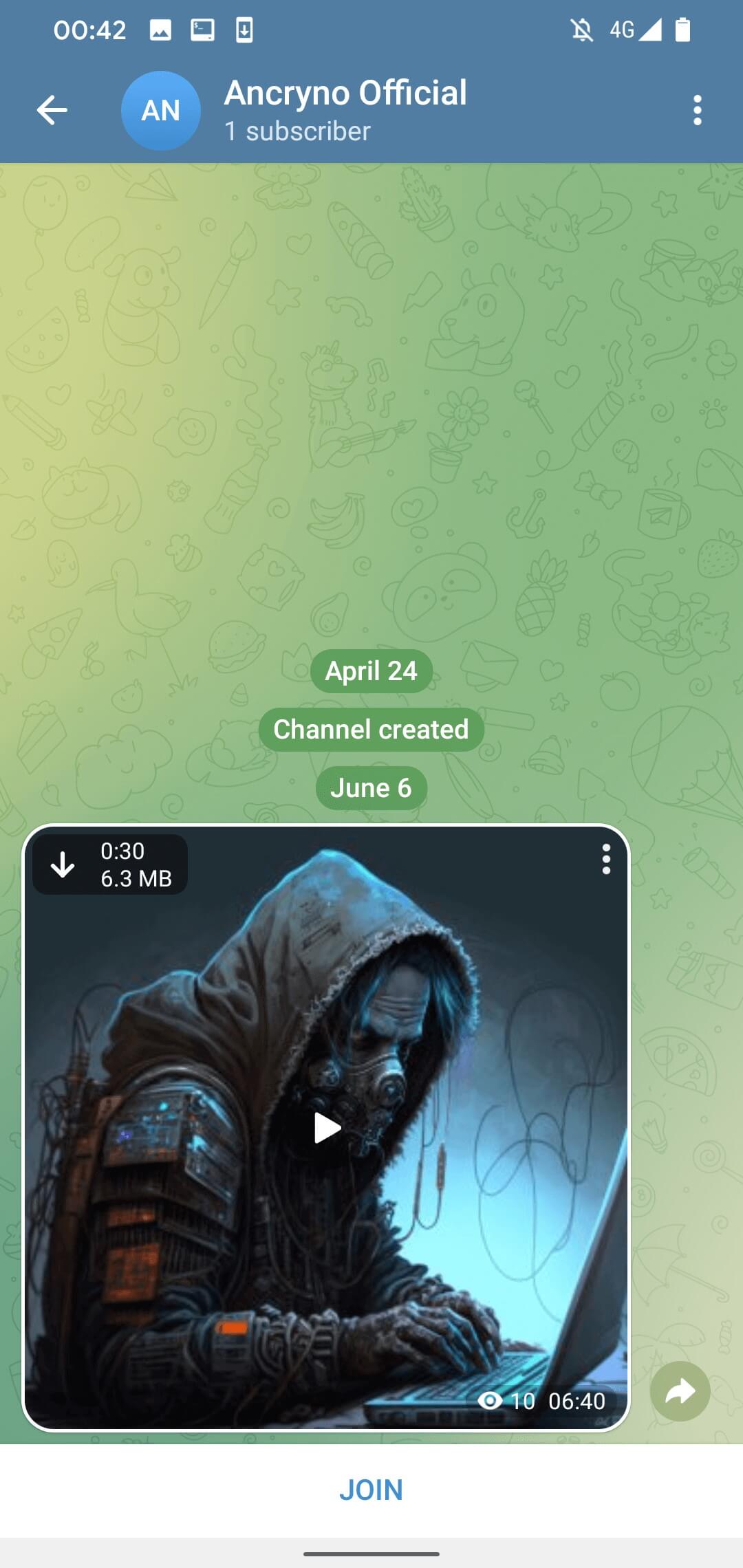
Ordinarily, multimedia files received via Telegram are configured to autodownload. Consequently, users with this setting enabled will automatically download the malevolent payload upon accessing the conversation where it was disseminated. Manual disabling of this option is feasible – in which case, the payload can still be downloaded by tapping the download option in the top left corner of the purported video, as depicted in Figure 3.
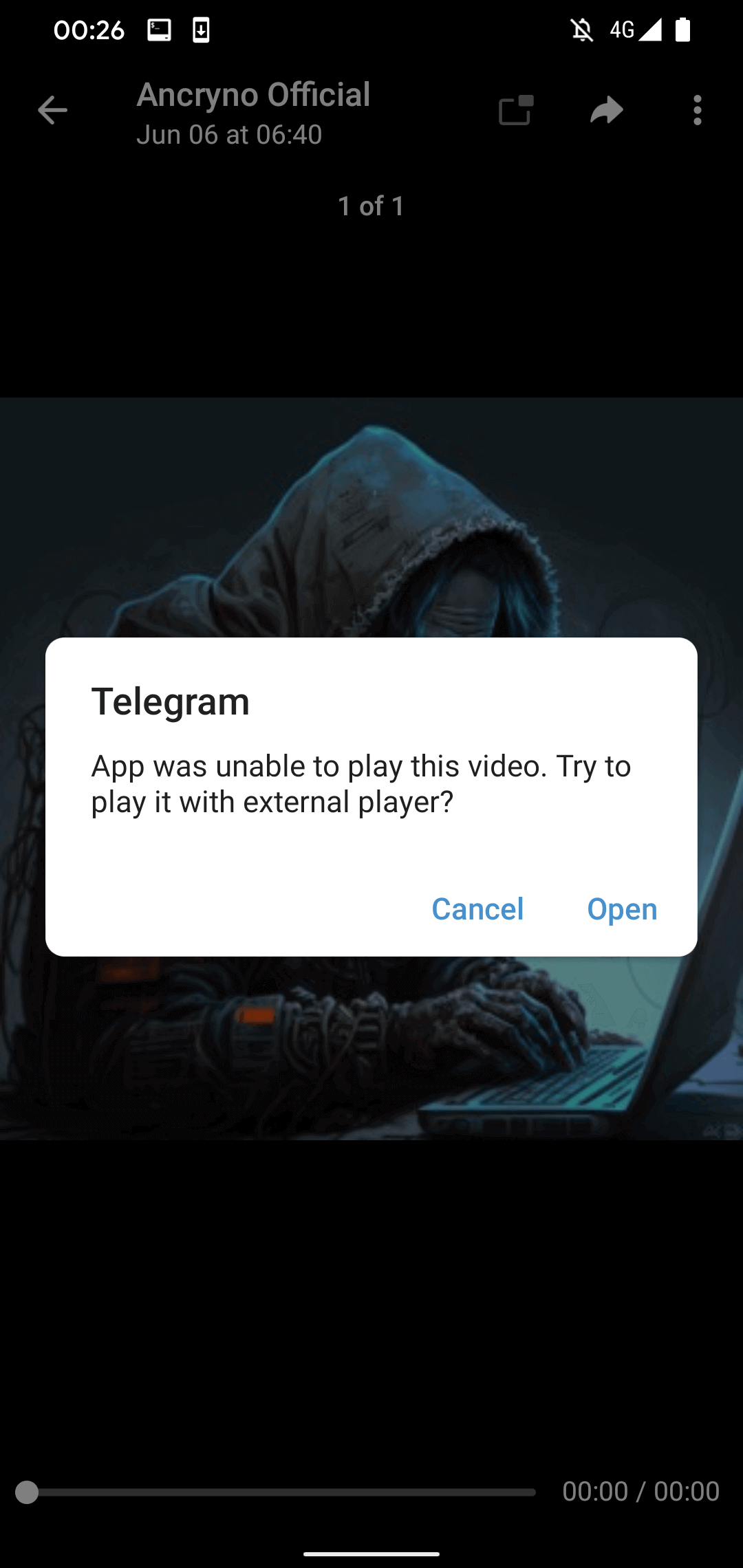
Upon attempting to playback the “video,” Telegram exhibits a notification indicating its inability to play it and suggests using an external player (refer to Figure 4). This notification, present in the source code of the authentic Telegram for Android application, is not manipulated or introduced by the malicious payload.
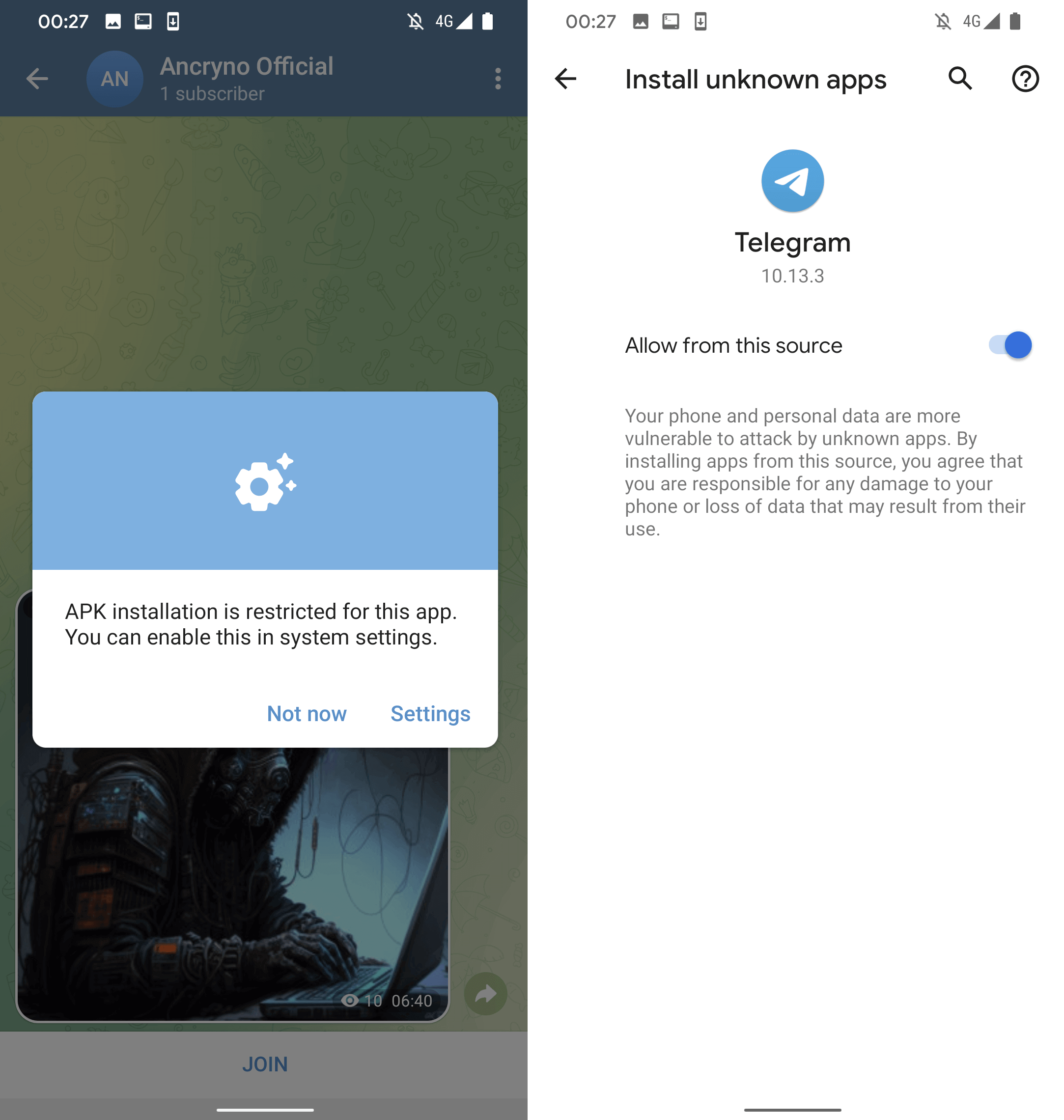
However, selecting the Open option in the displayed notification prompts the user to install a malicious application camouflaged as the aforementioned external player. As seen in Figure 5, before installation, Telegram requests permission to allow the installation of unknown applications.
At this stage, the malevolent application in question has already been downloaded under the guise of a video file, albeit with the .apk extension. It is intriguing to note that the vulnerability results in the shared file appearing as a video – the legitimate malevolent application was not altered to mimic a multimedia file, indicating potential exploitation during the upload process. The installation prompt for the malicious application is depicted in Figure 6.
Regrettably, duplicating the loophole was unachievable, with our inspection being solely limited to the sample provided by the vendor.
Telegram Web and Desktop
Despite the payload’s exclusive focus on Telegram for Android, we sought to ascertain its performance across other Telegram platforms. Testing was conducted on both the Telegram Web client and Telegram Desktop client for Windows – predictably, the loophole proved ineffective on both.
Upon attempting to view the “video” on Telegram Web, an error message redirected users to use the desktop app instead (refer to Figure 7). Manual download of the attached file disclosed its name and extension as Teating.mp4. Albeit the file being an Android executable binary (APK), Telegram’s misinterpretation of it as an MP4 file impeded the loophole’s operation: for successful execution, the attachment necessitated the .apk extension.
Similar circumstances transpired with the Telegram Desktop client for Windows: the downloaded file was labeled Teating.apk.mp4, reinstating it as an APK binary file with an appended .mp4 extension. The implication is that even if a perpetrator engineered aA Windows executable can be utilized in place of the Android APK file, and it will still be considered a multimedia data type, rendering the exploit ineffective.

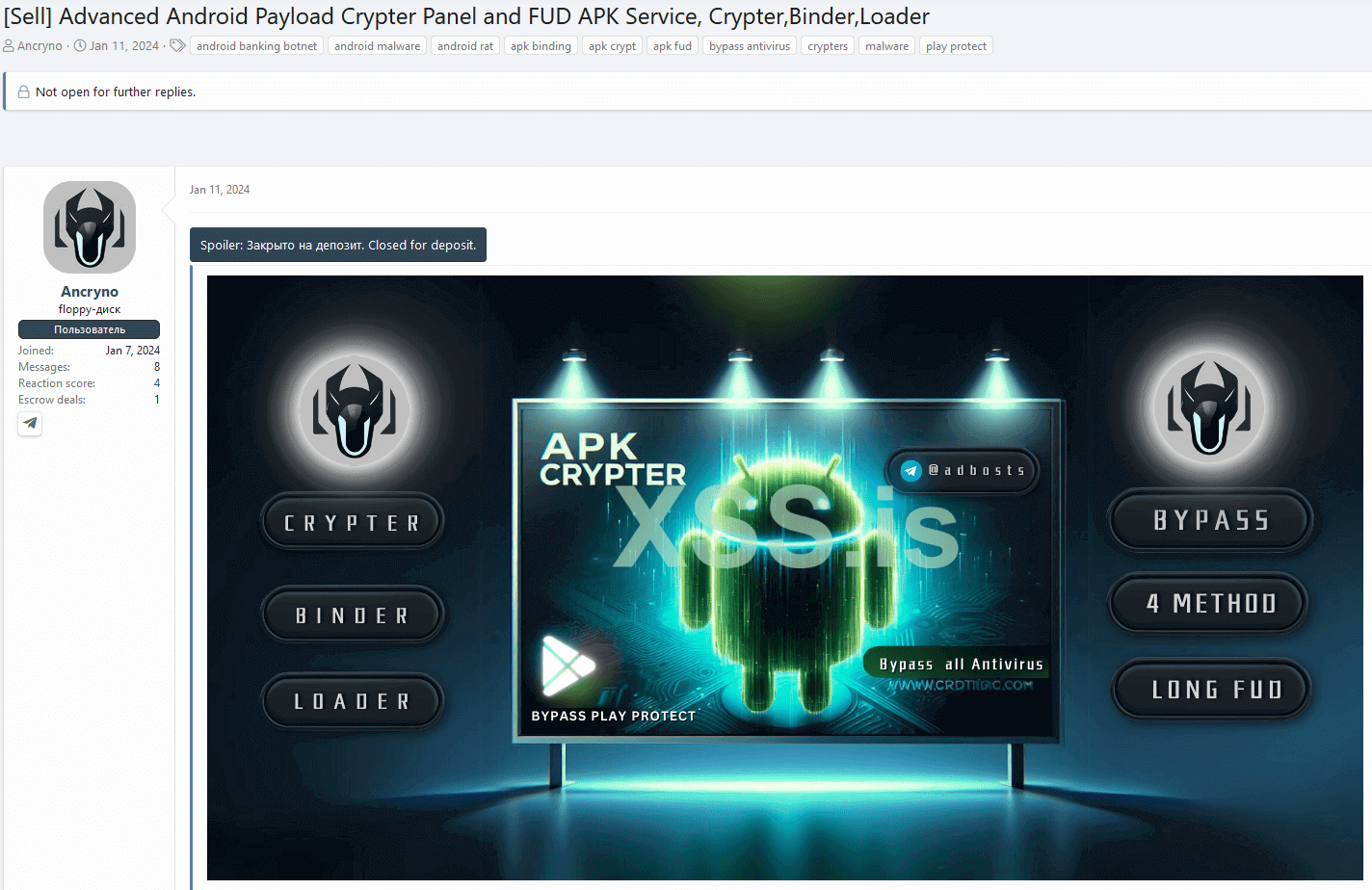
Threat actor
Although details about the malicious actor are limited, we were able to identify another suspicious service offered by them, which was linked to the Telegram handle shared in their forum post. Alongside the exploit, they were also promoting an Android cryptor-as-a-service on the underground forum, claiming it to be completely undetectable (FUD) since January 11th, 2024. The forum post is illustrated in Figure 8.
Vulnerability report
Following the discovery of the EvilVideo vulnerability on June 26th, 2024, we adhered to our coordinated disclosure procedure and reported it to Telegram. Initially, no response was received. Subsequently, we re-reported the vulnerability on July 4th, prompting Telegram to acknowledge the matter on the same day and confirm their team was investigating the issue. They subsequently addressed the problem by releasing version 10.14.5 on July 11th, notifying us via email.
The vulnerability impacted all versions of Telegram for Android up to 10.14.4 but has been resolved in version 10.14.5. Our verification confirmed that the chat preview now accurately identifies the shared file as an application (Figure 9) rather than a video.

Conclusion
A zero-day exploit targeting Telegram for Android was found for sale on an underground forum. The exploit allowed sending malicious payloads disguised as multimedia files via Telegram chat. Should a user attempt to play the fake video, they would be prompted to install an external application that actually delivers the malicious payload. Fortunately, after reporting the issue to Telegram, it was fixed as of July 11th, 2024.
For inquiries regarding our WeLiveSecurity publications, please contact us at threatintel@eset.comESET Research provides confidential APT intelligence reports and data feeds. For further information on this service, visit the ESET Threat Intelligence page.
Indicators of Compromise
A detailed list of Indicators of Compromise (IoCs) and samples are available in our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinityhackscharan. |
Administrator Beam Cable System |
2024‑07‑16 |
C&C server of EvilVideo payload. |
MITRE ATT&CK techniques
This table was constructed using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Exploitation for Initial Access |
The EvilVideo vulnerability can be abused by Android malware to achieve initial device access. |
|
|
Execution |
Exploitation for Client Execution |
The EvilVideo vulnerability tricks the victim into installing a malicious app that impersonates a multimedia file. |









