Cybersecurity analysts have revealed that the LightSpy surveillance software believed to be targeting Apple iOS users is actually an unrecorded macOS variant of the malware.
This discovery was made by both Huntress Labs and ThreatFabric, who independently examined the elements linked with the malware framework that is likely capable of infecting various platforms including Android, iOS, Windows, macOS, Linux, and routers from NETGEAR, Linksys, and ASUS.
“Utilizing two publicly accessible exploits (CVE-2018-4233, CVE-2018-4404), the threat actor group deployed implants for macOS,” mentioned ThreatFabric in a report released last week. “Part of the CVE-2018-4404 exploit is possibly adopted from the Metasploit framework, and macOS version 10 was the target using these exploits.”
Initially reported in 2020, LightSpy has been linked to a potential connection with an Android surveillance tool known as DragonEgg, as revealed by subsequent reports from Lookout and a Dutch mobile security company.
Earlier in April, BlackBerry publicized what was described as a “resurrected” cyber espionage campaign aimed at users in South Asia to distribute an iOS edition of LightSpy. However, it has now been identified as a more refined version for macOS that utilizes a system based on plugins to gather various types of data.
“It’s important to note that while this specimen was recently uploaded to VirusTotal from India, it’s not a very strong indication of an active campaign or regional targeting,” stated Huntress researchers Stuart Ashenbrenner and Alden Schmidt.
“It’s a contributing factor, but one should approach it with caution without substantial evidence or insight into delivery mechanisms.”
ThreatFabric’s analysis suggests that the macOS version has been operational in the wild since at least January 2024, but limited to approximately 20 devices, mostly test devices.
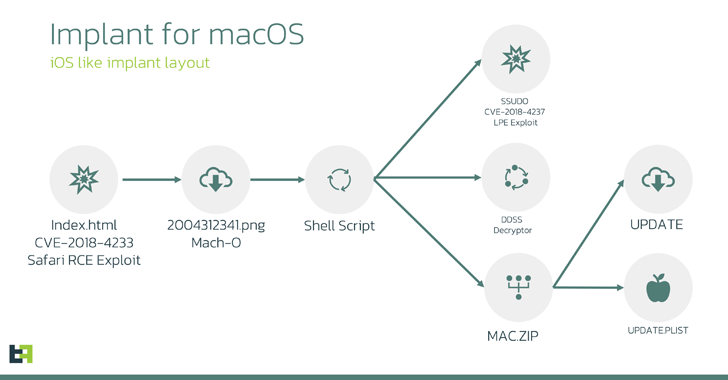
The attack sequence starts with the exploitation of CVE-2018-4233, a vulnerability in Safari WebKit, through malicious HTML pages to initiate code execution, paving the way for the distribution of a 64-bit MachO binary that poses as a PNG image file.
The binary is primarily created to extract and initiate a shell script which in turn retrieves three additional payloads: A privilege escalation exploit, an encryption/decryption tool, and a ZIP archive.
The script proceeds to unpack the ZIP archive contents – update and update.plist – and allocates root privileges to both. The information property list (plist) file is utilized to establish persistence for the other file so that it is executed after each system reboot.
The “update” file (also known as macircloader) functions as a loader for the LightSpy Core element, enabling the latter to connect with a command-and-control (C2) server, fetch commands, and download plugins.
The macOS version supports 10 different plugins to capture audio from the microphone, take pictures, record screen actions, collect and erase files, run shell commands, obtain lists of installed applications and active processes, and extract data from web browsers (Safari and Google Chrome) and iCloud Keychain.
Furthermore, two additional plugins enable the retrieval of information on other devices connected to the same network as the target, the histories of Wi-Fi networks connected by the device, and the specifics of nearby Wi-Fi networks.
“The Core functions as a command dispatcher, and additional plugins enhance the capabilities,” as stated by ThreatFabric. “Both the Core and plugins can be updated interactively by a command from C2.”
The cybersecurity company identified a configuration flaw that allowed access to the C2 panel, including a remote management platform containing victim information and associated data.
“Irrespective of the targeted platform, the threat actor has a comprehensive surveillance arsenal.”group dedicated to intercepting victim communications, such as messenger dialogues and recorded voices,” as per the company’s statement. “A specialized plugin for macOS was specifically crafted for detecting networks, with the goal of identifying devices near the target.”
This development emerges amidst the targeting of Android devices with notorious banking trojans like BankBot and SpyNote in assaults directed at users of mobile banking apps in Uzbekistan and Brazil, as well as by posing as a Mexican telecom service provider to infect users in Latin America and the Caribbean.
Simultaneously, a report from Access Now and the Citizen Lab uncovered proof of Pegasus spyware attacks aimed at seven Russian and Belarusian-speaking opposition activists and independent media outlets in Latvia, Lithuania, and Poland.
“The utilization of Pegasus spyware to target journalists and activists who speak Russian and Belarusian dates back to at least 2020, with more attacks occurring after Russia’s full-scale invasion of Ukraine in February 2022,” stated the Access Now report, which also mentioned “a lone operator of Pegasus spyware might be behind the targeting of at least three victims, and potentially all five.”














