The recent Patch Tuesday collection for June introduces Windows administrators smoothly to the summer period, as Microsoft delivered 49 patches across 7 product families. Windows, as per usual, accounts for the majority of patches with 34. The remaining patches pertain to Azure, 365 Apps for Enterprise, Dynamics 365, Office, Visual Studio, and SharePoint.
Currently, there are no known exploits for the addressed issues in the wild. Nevertheless, Microsoft has identified eleven vulnerabilities in Windows that are more susceptible to exploitation within the next 30 days. Among these, one is the only critical-severity issue for this month, which will be elaborated on in detail later. Six of the vulnerabilities this month can be detected by Sophos protection measures, and details on these are provided in a table below.
Aside from the patches, this release includes advisories for seven patches related to the Edge browser, one concerning GitHub, an intriguing item from MITRE affecting various internet components, and two from Adobe. While the advisories are not included in the CVE counts and visuals below, detailed information on each is available in an appendix at the end of this post. Furthermore, we will delve into the MITRE advisory below. As usual, three other appendices categorizing all of Microsoft’s patches by severity, predicted exploitability, and product family are provided at the end of this article.
Numerical Overview
- Total Microsoft CVEs: 49
- Total Edge / Chrome advisory issues covered in the update: 7
- Total non-Edge Microsoft advisory issues covered in update: 2
- Total Adobe issues covered in update: 2
- Publicly disclosed: 0*
- Exploited: 0
- Severity
- Critical: 1
- Important: 48
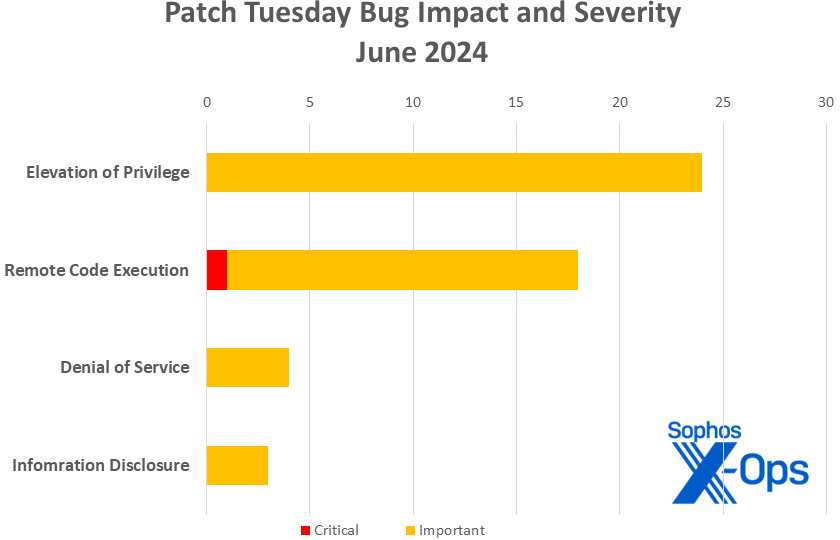
- Impact:
- Elevation of Privilege: 24
- Remote Code Execution: 18
- Denial of Service: 4
- Information Disclosure: 3
* One advisory-only CVE is publicly disclosed; details below
Figure 1: The June Patch Tuesday assortment is characterized by four distinct vulnerability categories
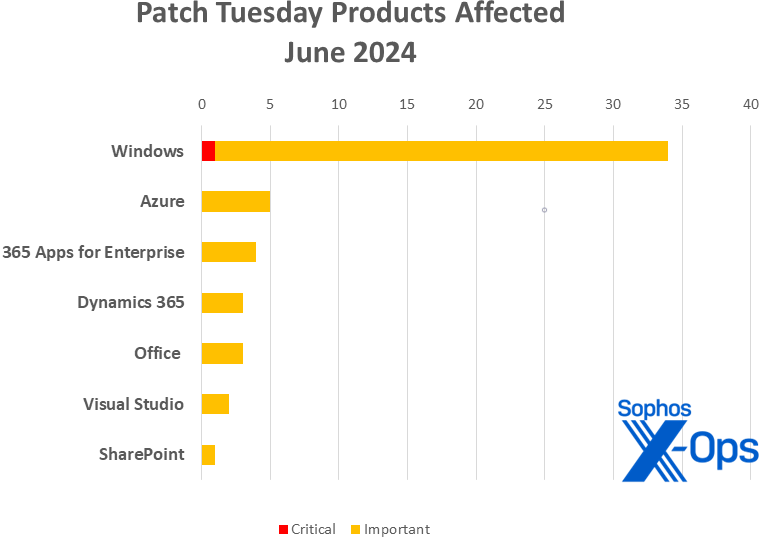
Product Overview
- Windows: 34
- Azure: 5
- 365 Apps for Enterprise: 4 (including one in conjunction with Office)
- Dynamics 365: 3
- Office: 3 (shared with 365 Apps for Enterprise)
- Visual Studio: 2
- SharePoint: 1
Figure 2: The majority of June’s patches are attributed to Windows, which also hosts the only Critical-level vulnerability
Prominent June Updates
In addition to the aforementioned issues, a few specific items warrant attention.
CVE-2024-30080 – Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
Among the 11 CVEs identified as more prone to exploitation within 30 days of Patch Tuesday, this critical-severity RCE stands out as the sole critical-class concern for the month. It impacts both clients and servers with the Windows message-queuing service enabled. When active, an attacker could leverage a maliciously crafted MSMQ packet to initiate RCE on the server. (Sophos provides a detection method for this; details can be found in the table below Figure 3.)
CVE-2023-50868 – MITRE: CVE-2023-50868 NSEC3 closest encloser proof can deplete CPU resources
This specific CVE is advisory-only, raised by MITRE, and of industry-wide importance rather than solely affecting Microsoft. It highlights a publicly disclosed issue concerning DNSSEC and its method of proving the non-existence of a designated zone. For those unfamiliar with DNSSEC intricacies or puzzled by how an NSEC record can validate a negative, the DNS Institute offers a highly approachable narrative explaining the concept. The identified bug is a critical-severity denial-of-service flaw, currently not known to be exploited in the wild. Given its DNS implications, it deserves attention.
CVE-2024-37325 – Azure Science Virtual Machine (DSVM) Elevation of Privilege Vulnerability
While only one vulnerability is deemed critical in severity for this month (CVE-2024-30800, mentioned above), this Azure EoP demands consideration for those inclined to assess vulnerabilities based on CVSS scores. If utilizing a version of Linux/Ubuntu Data Science Virtual Machines (DSVM) preceding 24.05.24, this 9.8 CVSS-rated bug is noteworthy. It demands no privileges nor user interaction; a specially crafted request sent to the target machine is enough for the attacker to access authorized user credentials. Users impacted by this should refer to detailed information and take swift action.
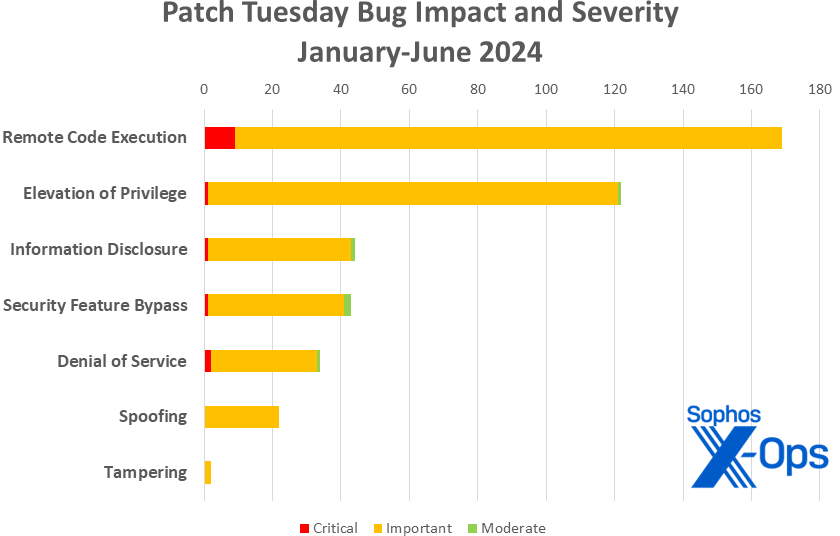
Figure 3: As we approach the latter half of the year 2024, Information Disclosure vulnerabilities slightly surpass Security Feature Bypass issues, with RCE maintaining its lead
Sophos Protection Measures
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-30080 | sid:2309700 | sid:2309700 |
| CVE-2024-30084 | Exp/2430084-A | Exp/2430084-A |
| CVE-2024-30087 | Exp/2430087-A | Exp/2430087-A |
| CVE-2024-30088 | Exp/2430088-A | Exp/2430088-A | Vulnerability ID: CVE-2024-30089 | Exploit ID: Exp/2430089-A | Exploit ID: Exp/2430089-A |
| Vulnerability ID: CVE-2024-35250 | Exploit ID: Exp/2435250-A | Exploit ID: Exp/2435250-A |
If you wish to expedite the installation of Microsoft’s updates before your system does it automatically, you have the option to manually download them from the Windows Update Catalog website. First, utilize the winver.exe utility to identify the Windows 10 or 11 build you are using. Afterward, obtain the Cumulative Update package specific to your system’s architecture and build number.
Appendix A: Impact and Severity of Vulnerabilities
Below is a categorized list of June patches based on impact and severity, with further sorting by CVE.
Privilege Elevation (24 CVEs)
| Severity: Important | |
| CVE-2024-29060 | Visual Studio Vulnerability Permitting Privilege Elevation |
| CVE-2024-30064 | Windows Kernel Privilege Elevation Vulnerability |
| CVE-2024-30066 | Winlogon Privilege Elevation Vulnerability |
| CVE-2024-30067 | WinLogon Privilege Elevation Vulnerability |
| CVE-2024-30068 | Windows Kernel Privilege Elevation Vulnerability |
| CVE-2024-30076 | Privilege Elevation Vulnerability in Windows Container Manager Service |
| CVE-2024-30082 | Win32k Privilege Elevation Vulnerability |
| CVE-2024-30084 | Windows Kernel-Mode Driver Privilege Elevation Vulnerability |
| CVE-2024-30085 | Windows Cloud Files Mini Filter Driver Privilege Elevation Vulnerability |
| CVE-2024-30086 | Windows Win32 Kernel Subsystem Privilege Elevation Vulnerability |
| CVE-2024-30087 | Win32k Privilege Elevation Vulnerability |
| CVE-2024-30088 | Windows Kernel Privilege Elevation Vulnerability |
| CVE-2024-30089 | Privilege Elevation Vulnerability in Microsoft Streaming Service |
| CVE-2024-30090 | Privilege Elevation Vulnerability in Microsoft Streaming Service |
| CVE-2024-30091 | Win32k Privilege Elevation Vulnerability |
| CVE-2024-30093 | Windows Storage Privilege Elevation Vulnerability |
| CVE-2024-30099 | Windows Kernel Privilege Elevation Vulnerability |
| CVE-2024-35248 | Privilege Elevation Vulnerability in Microsoft Dynamics Business Central |
| CVE-2024-35250 | Windows Kernel-Mode Driver Privilege Elevation Vulnerability |
| CVE-2024-35253 | Privilege Elevation Vulnerability in Microsoft Azure File Sync |
| CVE-2024-35254 | Privilege Elevation Vulnerability in Azure Monitor Agent |
| CVE-2024-35255 | Privilege Elevation Vulnerability in Azure Identity Libraries and Microsoft Authentication Library |
| CVE-2024-35265 | Windows Perception Service Privilege Elevation Vulnerability |
| CVE-2024-37325 | Privilege Elevation Vulnerability in Azure Science Virtual Machine (DSVM) |
Execution of Remote Code (18 CVEs)
| Severity: Critical | |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Vulnerability Permitting Remote Code Execution |
| Severity: Important | |
| CVE-2024-30052 | Visual Studio Vulnerability Permitting Remote Code Execution |
| CVE-2024-30062 | Remote Code Execution Vulnerability in Windows Standards-Based Storage Management Service |
| CVE-2024-30063 | Remote Code Execution Vulnerability in Windows Distributed File System (DFS) |
| CVE-2024-30072 | Remote Code Execution Vulnerability in Microsoft Event Trace Log File Parsing |
| CVE-2024-30074 | Remote Code Execution Vulnerability in Windows Link Layer Topology Discovery Protocol |
| CVE-2024-30075 | Remote Code Execution Vulnerability in Windows Link Layer Topology Discovery Protocol |
| CVE-2024-30077 | Remote Code Execution Vulnerability in Windows OLE |
| CVE-2024-30078 | Remote Code Execution Vulnerability in Windows WiFi Driver |
| CVE-2024-30094 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| CVE-2024-30095 | Remote Code Execution Vulnerability in Windows Routing and Remote Access Service (RRAS) |
| CVE-2024-30097 | Remote Code Execution Vulnerability in Microsoft Speech Application Programming Interface (SAPI) |
| CVE-2024-30100 | Remote Code Execution Vulnerability in Microsoft SharePoint Server |
| CVE-2024-30101 | Remote Code Execution Vulnerability in Microsoft Office |
| CVE-2024-30102 | Remote Code Execution Vulnerability in Microsoft Office |
| CVE-2024-30103 | Remote Code Execution Vulnerability in Microsoft Outlook |
| CVE-2024-30104 | Remote Code Execution Vulnerability in Microsoft Office |
| CVE-2024-35249 | Remote Code Execution Vulnerability in Microsoft Dynamics Business Central |
Service Denial (4 CVEs)
| Severity: Important | |
| CVE-2024-30065 | Denial of Service Vulnerability in Windows Themes |
| CVE-2024-30070 | Denial of Service Vulnerability in DHCP Server Service |
| CVE-2024-30083 | Denial of Service Vulnerability in Windows Standards-Based Storage Management Service |
| CVE-2024-35252 | Denial of Service Vulnerability in Azure Storage Movement Client Library |
Information Exposure (3 CVEs)
| Severity: Important | ||
| CVE-2024-30069 | Information Exposure Vulnerability in Windows Remote Access Connection Manager | |
| CVE-2024-30096 | Information Exposure Vulnerability in Windows Cryptographic Services | |
| CVE-2024-35263 | CVE-2024-35260 | 365 Apps for Enterprise Service Elevation of Privilege Vulnerability |
| CVE-2024-35261 | 365 Apps for Enterprise Information Disclosure Vulnerability | |
| CVE-2024-35262 | 365 Apps for Enterprise Remote Code Execution Vulnerability | |
| CVE-2024-35263 | 365 Apps for Enterprise Denial of Service Vulnerability | |
D365 (3 Vulnerabilities)
| Significant seriousness | |
| CVE-2024-35248 | Microsoft Dynamics Business Center Vulnerability for Elevation Of Privilege |
| CVE-2024-35249 | Microsoft Dynamics Business Center Vulnerability for Remote Code Execution |
| CVE-2024-35263 | Microsoft Dynamics 365 (On-Premises) Vulnerability for Information Disclosure |
Office (3 Vulnerabilities)
| Significant seriousness | |
| CVE-2024-30101 | Microsoft Office Vulnerability for Remote Code Execution |
| CVE-2024-30103 | Microsoft Outlook Vulnerability for Remote Code Execution |
| CVE-2024-30104 | Microsoft Office Vulnerability for Remote Code Execution |
Visual Studio (2 Vulnerabilities)
| Significant seriousness | |
| CVE-2024-29060 | Visual Studio Vulnerability for Elevation of Privilege |
| CVE-2024-30052 | Visual Studio Vulnerability for Remote Code Execution |
SharePoint (1 Vulnerability)
| Significant seriousness | |
| CVE-2024-30100 | Microsoft SharePoint Server Vulnerability for Remote Code Execution |
Appendix D: Alerts and Other Products
This is a compilation of alerts and details on other pertinent CVEs in the June Microsoft update, classified by product.
Related to Edge / Chromium (7 Vulnerabilities)
| CVE-2024-5493 | Chromium: CVE-2024-5493 Heap buffer overflow in WebRTC |
| CVE-2024-5494 | Chromium: CVE-2024-5494 Use after free in Dawn |
| CVE-2024-5495 | Chromium: CVE-2024-5495 Use after free in Dawn |
| CVE-2024-5496 | Chromium: CVE-2024-5496 Use after free in Media Session |
| CVE-2024-5497 | Chromium: CVE-2024-5497 Out of bounds memory access in Keyboard Inputs |
| CVE-2024-5498 | Chromium: CVE-2024-5498 Use after free in Presentation API |
| CVE-2024-5499 | Chromium: CVE-2024-5499 Out of bounds write in Streams API |
Related to GitHub (1 Vulnerability)
| CVE-2024-29187 | GitHub: CVE-2024-29187 WiX Burn-based bundles are vulnerable to binary hijack when run as SYSTEM |
Related to Visual Studio (non-Microsoft CVE issuer) (1 Vulnerability)
| CVE-2023-50868 | MITRE: CVE-2023-50868 NSEC3 closest encloser proof can exhaust CPU |
Related to Adobe (non-Microsoft release) (2 Vulnerabilities)
| APSB24-41 | CVE-2024-34112 | Improper Access Control (CWE-284) |
| APSB24-41 | CVE-2024-34113 | Weak Cryptography for Passwords (CWE-261) |