An expert in security working at the National Labor Relations Board (NLRB) is asserting that personnel from the Department of Government Efficiency (DOGE) under Elon Musk moved significant amounts of confidential information from the agency’s case records in early March. This was done using temporary accounts set up to leave minimal traces of network activity. The whistleblower from NLRB mentioned that the substantial data transfers occurred simultaneously with multiple unsuccessful login attempts originating from a Russian IP address trying to utilize valid credentials for a newly established DOGE user account.

A letter sent to the Senate Select Committee on Intelligence, enclosed with Berulis’s whistleblower statement.
The accusations were detailed in a letter dated April 14 addressed to the Senate Select Committee on Intelligence, signed by Daniel J. Berulis, a security expert at NLRB aged 38.
NPR, the first to cover Berulis’s whistleblower statement, indicated that NLRB is a small independent federal agency responsible for investigating and settling complaints related to unfair labor practices. It holds a vast amount of potentially sensitive data, ranging from confidential details about employees seeking to establish unions to confidential business data.
The complaint describes a specific timeframe starting from March 3, during which DOGE officials allegedly insisted on the formation of highly powerful “tenant admin” accounts within NLRB systems. These accounts were to be excluded from network logging processes which typically record every action conducted by them.
Berulis pointed out that the new DOGE accounts possessed unrestricted permissions to view, copy, and modify data stored in NLRB databases. They also had the ability to manipulate log visibility, postpone retention, redirect logs elsewhere, or even delete them entirely — superior user privileges that neither Berulis nor his superior held.
According to Berulis, on March 3, a black SUV accompanied by law enforcement personnel arrived at his workplace — the NLRB headquarters in Southeast Washington, D.C. The DOGE representatives did not engage with Berulis or other IT staff at NLRB but directly met with the agency’s leadership.
“Following that encounter, our temporary chief information officer instructed us to deviate from standard procedure regarding DOGE account creation, with a mandate not to generate logs or records related to the accounts set up for DOGE employees requiring the highest level of access,” Berulis wrote regarding the instructions given after the meeting.
“While we have predefined roles that have been extensively utilized by auditors in the past, these roles do not grant permission to make modifications or access subsystems without proper authorization,” he further elaborated. “The recommendation to employ these accounts was non-negotiable.”
Berulis observed that one of the DOGE accounts created an obscured virtual environment termed a “container” on March 3. This container is utilized to create and execute programs or scripts without disclosing its operations to the external network. Berulis flagged this container because none of his colleagues acknowledged using containers within the NLRB network.
Additionally, Berulis noticed a significant surge in outbound traffic from the agency early the following morning, estimated between 3 a.m. and 4 a.m. EST on Tuesday, March 4. After several days of investigation with his peers, Berulis concluded that one of the new accounts had transferred approximately 10 gigabytes of data from NLRB’s NxGen case management system.
Revealingly, Berulis and his colleagues lacked the requisite network access rights to examine the specific files affected or moved, and their destinations remained unknown. Nevertheless, he underscored that the NxGen database contains private details on unions, ongoing legal disputes, and corporate confidential information.
“I’m unable to ascertain whether the data transferred totaled only 10GB or if it was compressed and consolidated beforehand,” informed Berulis to the senators. “This leaves the potential for more data exfiltration. Nonetheless, such a sharp increase is highly atypical as data rarely leaves NLRB’s databases directly.”
Moreover, Berulis and the team grew increasingly concerned upon discovering almost twenty unsuccessful login tries from a Russian IP address (83.149.30,186) providing accurate credentials for a DOGE employee account that had been established just moments earlier. Unfortunately, all these attempts were thwarted due to the existing protocol blocking logins from non-U.S. locations.
“The parties attempting to log in were leveraging one of the freshly generated accounts utilized in other DOGE-associated activities and it seemed they possessed the right username and password, as the authentication process solely halted them due to our foreign logins prohibition activating,” penned Berulis. “There were more than 20 such attempts, and the most concerning aspect is that a significant number was made within a 15-minute span post account creation by DOGE engineers.”
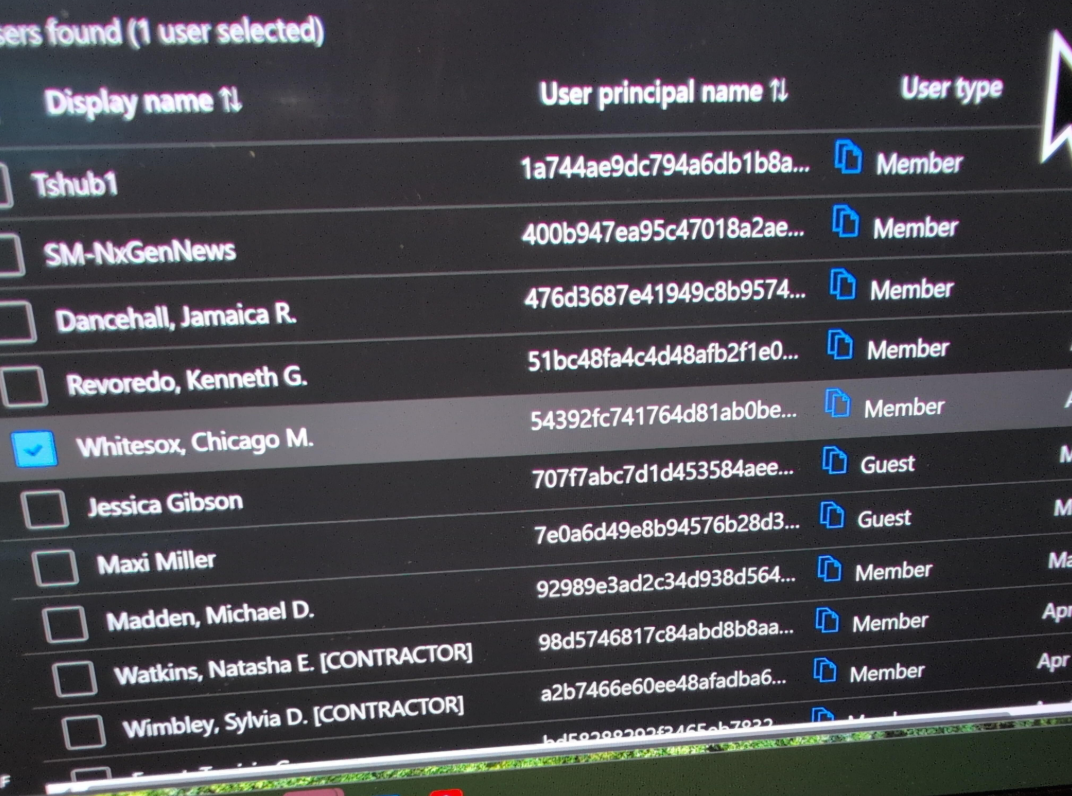
As per Berulis, the unconventional nomenclature of a certain Microsoft user account linked to the suspicious behavior implied it was generated and subsequently eradicated for DOGE requisites in NLRB’s cloud systems: “DogeSA_2d5c3e0446f9@nlrb.microsoft.com.” He also highlighted the presence of other fresh Microsoft cloud administrator accounts with unconventional usernames like “Whitesox, Chicago M.” and “Dancehall, Jamaica R.”
On March 5, Berulis recorded the absence of a significant section of logs for recently established network resources, with a network observer within Microsoft Azure set to an inactive mode, causing it to cease aggregating and storing data as required.
The discovery was made that an individual had downloaded three external code libraries from GitHub that were never utilised by NLRB or its subcontractors. A documentation file within one of the code packages outlined its purpose as rotating connections through a vast array of cloud IP addresses functioning as a proxy to produce an extensive range of IPs for web scraping and brute-force attempts. Brute-force attacks involve automated login trials that test numerous credential combinations.
Rapidly sequencing combinations.
The accusation claims that by the 17th of March, it was evident that the NLRB lacked the required resources or network connectivity to thoroughly investigate the peculiar activities from the DOGE accounts. By the 24th of March, the agency’s associate chief information officer had approved reporting the issue to US-CERT. Managed by the Cybersecurity and Infrastructure Security Agency (CISA) under the Department of Homeland Security, US-CERT delivers on-premises cyber incident response capabilities to federal and state entities.
However, Berulis mentioned that between the 3rd and 4th of April, he and the associate CIO were instructed to abandon the US-CERT reporting and investigation. They were directed not to proceed or create any official reports. It was at this juncture that Berulis opted to publicize his discoveries.
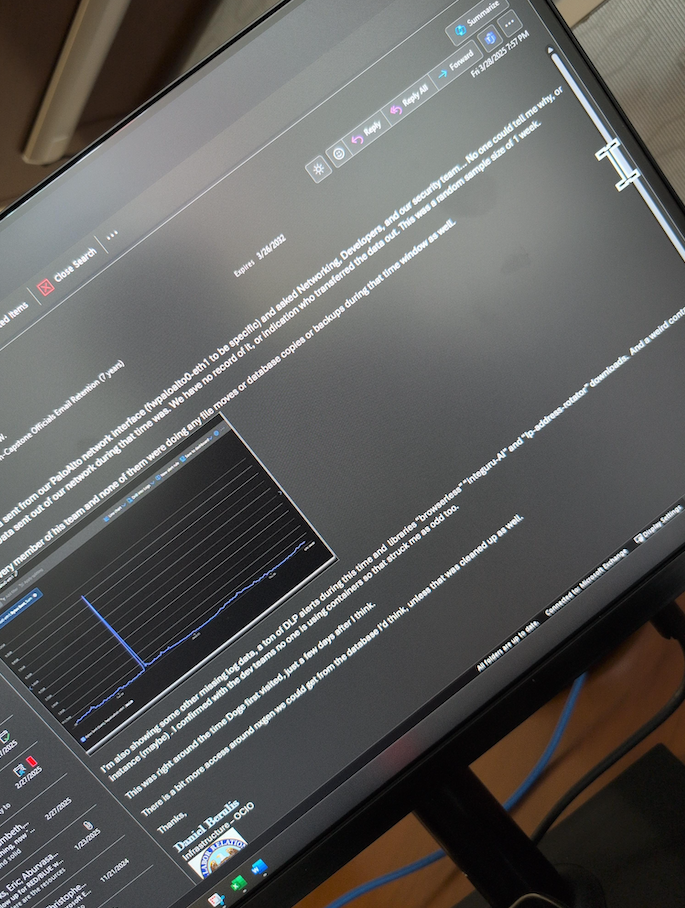
A March 28 email from Daniel Berulis to his colleagues, discussing the unexplained traffic surge earlier in the month and unauthorized alterations to user account security settings.
Tim Bearese, the interim press secretary of the NLRB, informed NPR that DOGE neither solicited nor obtained access to its systems. The agency conducted an investigation following Berulis’s alerts, concluding that no breach of agency systems had occurred. The NLRB did not address inquiries from KrebsOnSecurity.
Nonetheless, Berulis has disclosed several corroborating screenshots displaying internal email conversations within the agency regarding the suspicious account activities linked to the DOGE accounts. Additionally, he showed NLRB security notifications from Microsoft concerning network irregularities observed during the mentioned time intervals.
As highlighted by CNN in a recent report, the NLRB has been significantly impaired since President Trump dismissed three board members, rendering the agency without the quorum necessary for its operations.
“Despite its limitations, the agency had become a thorn in the side of some of the wealthiest and most influential individuals in the country — specifically Elon Musk, a key supporter of Trump both financially and potentially politically,” noted CNN.
Both Amazon and Musk’s SpaceX have filed lawsuits against the NLRB over complaints the agency lodged in conflicts related to workers’ rights and union organizing, contending that the legitimacy of the NLRB is unconstitutional. On the 5th of March, a U.S. appeals court unanimously rejected Musk’s claim that the NLRB’s structure violates the Constitution.
Berulis shared screenshots with KrebsOnSecurity indicating that on the day NPR published its article about his claims (April 14), the NLRB’s deputy CIO sent an email stating that administrative access had been revoked for all employee accounts. This meant that suddenly, none of the IT personnel at the agency could adequately perform their duties, according to Berulis.
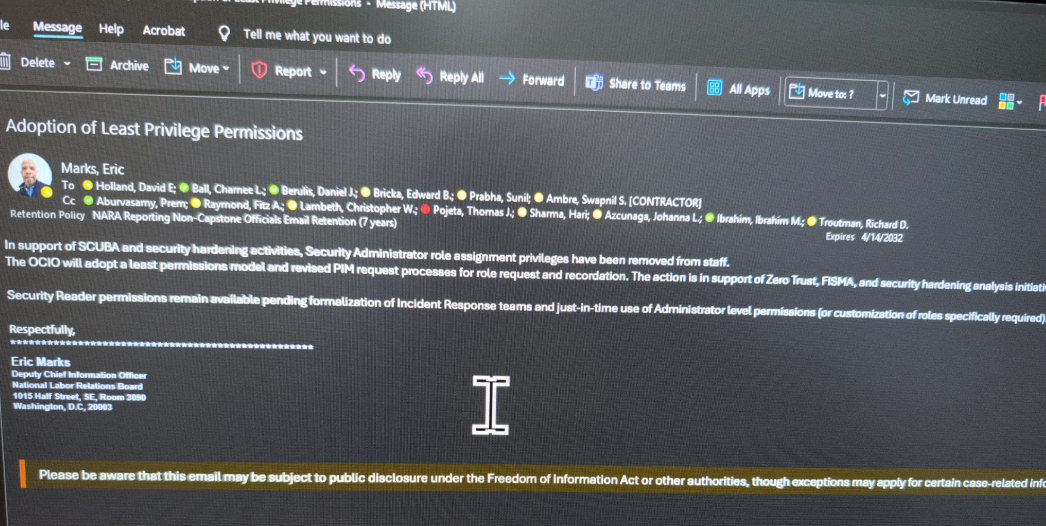
An email from Eric Marks, the NLRB’s associate chief information officer, notifying employees of the loss of security administrator privileges.
Berulis revealed a screenshot of a comprehensive email dated April 16 from NLRB director Lasharn Hamilton, stating that DOGE officials had requested a meeting. It reiterated the assertion that the agency had not had any previous “official” engagements with DOGE personnel. The message informed NLRB employees that two DOGE representatives would be on site part-time for several months.

An email from the NLRB Director Lasharn Hamilton on April 16, clarifying the agency’s previous lack of contact with DOGE personnel.
Berulis informed KrebsOnSecurity that he was in the process of initiating a support ticket with Microsoft to solicit further details about the DOGE accounts when his network admin privileges were curtailed. He now anticipates lawmakers to request Microsoft for more insights into the actual occurrences with the accounts.
“This would offer us a more comprehensive view,” he remarked. “Microsoft ought to possess a better perspective than us. That’s my current objective, at any rate.”
Berulis’s legal counsel informed legislators that on April 7, while Berulis and the legal team were drafting the whistleblower report, an individual affixed a menacing note to Mr. Berulis’s home door with pictures — obtained via drone — of him strolling in his neighborhood.
“The threatening note explicitly referred to this very disclosure he was preparing for you, as the appropriate governing body,” a preface by Berulis’s lawyer Andrew P. Bakaj stated. “While we are not certain about the perpetrator, we can only speculate that it involved someone with NLRB system access.”
Berulis mentioned that the responses from friends, colleagues, and the general public have been mostly supportive, and he stands by his decision to speak out.
“I didn’t anticipate the message on my door or the resistance from [agency] leaders,” he remarked. “Even if given a choice, I would still take the same action because there was no real alternative the first time around.”
Presently, Mr. Berulis is utilizing some allocated family leave from the NLRB, which he acknowledged was appropriate considering he had been stripped of the necessary tools to perform his duties at the agency.
“They took over full administrative control, locked everyone out, and mentioned that limited permissions would be granted on a necessity basis moving forward,” Berulis remarked on the handling by the DOGE employees. “We are practically unable to do anything, so essentially, we are being paid to count ceiling panels.”
Further reading: Berulis’s grievance (PDF).