American food delivery enterprise PurFoods, known as Mom’s Meals, has recently disclosed a security breach that occurred from January 16, 2023, to February 22, 2023.
An official statement from the organization mentioned:
The cyber intrusion involved the encryption of specific files on our network.
Given the discovery of tools capable of unauthorized data extraction, there is a possibility that data might have been taken from one of our file servers.
PurFoods has reached out to individuals affected by this incident or those whose data was present in the encrypted files, presumed to be the data targeted by the attackers.
Exposure Details
The corporation did not disclose the exact number of individuals impacted by the breach, but a recent article on IT news portal The Register estimates it to be over 1.2 million people.
PurFoods identified the affected parties as:
Users of PurFoods who had received meal deliveries, along with some existing and former staff and freelance workers.
The compromised details included birth dates, state ID/driver’s license numbers, financial account data, medical records, Medicare/Medicaid IDs, health records, treatment info, diagnosis codes, meal specifics and costs, health insurance particulars, and patient IDs.
Social Security numbers were implicated for less than 1% of the individuals, mostly internal to PurFoods.
One can assume that the company did not acquire SSNs for customers as they normally would for employees, hence the internally tagged SSNs at risk.
Questions may arise as to why a food delivery enterprise would necessitate customers’ medical particulars, such as health and treatment data…
…this query was shared by many.
The company specializes in catering to individuals with specific dietary requirements, including those with diabetes, kidney issues, and other medical conditions requiring precise ingredient selection.
Therefore, Mom’s Meals requires medical info for some, if not all, customers, and this data was intermingled with various other personally identifiable pieces of information (PII) which may now be in the hands of cyber felons.
Recommendations
If you are among the million-plus impacted consumers:
- Consider replacing your payment card if it could have been compromised. Most banks issue new cards swiftly, rendering the old ones unusable to cybercriminals accessing or attempting to sell the details on illicit platforms.
- Monitor your statements vigilantly. It is advisable to regularly check your accounts for any irregular transactions, especially amidst the elevated risk of identity theft or fraudulent card use.
- Think about enacting a credit freeze. This additional security layer requires your authorization before any credit data can be released, making it tougher for fraudsters to utilize your identity for obtaining credit cards or loans. However, initiating a credit freeze involves submitting substantial PII, including a copy of your photo ID and SSN, to a credit bureau.
For corporations handling critical PII:
- Respond promptly upon detecting any network anomalies. In this breach, the hackers lurked within PurFoods’ network for over a month before their presence was identified during the file encryption stage, likely a ploy for extortion.
- Contemplate utilizing a Managed Detection and Response (MDR) service if self-monitoring is challenging. Robust threat detection tools not only prevent malware activation but also assist in pinpointing vulnerabilities like unsecured systems or outdated software, plus spotting suspicious activities indicative of an impending security breach.
skilled professionals available round the clock enhances the probability of detecting any warning signs before it becomes too late.
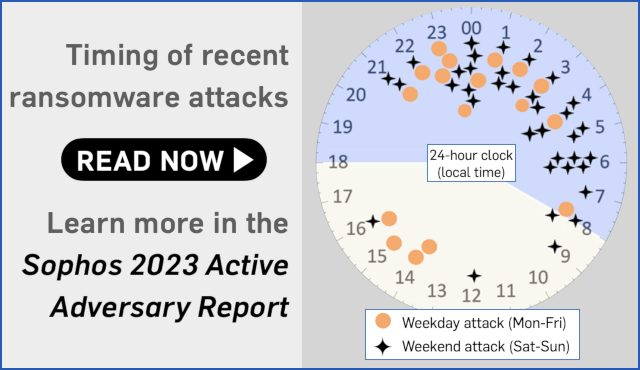
The latest Sophos Active Adversary report reveals that the median dwell time in ransomware assaults (the duration between cybercriminals infiltrating your network and successfully compromising all files at once) has decreased to just five days.
This indicates that if your company is targeted by ransomware perpetrators for their next extortion scheme, there is a likelihood of more than 50% that you will have less than a week to identify and thwart the intruders preparing for a catastrophic network breach.
Furthermore, the decisive ransomware strike by attackers is likely to occur at a highly inconvenient hour for your IT team, with the file encryption typically happening between 21:00 and 06:00 (9pm to 6am) in your local time zone.
In the wise words of Mr. Miyagi from the Karate Kid: The best approach to evade a blow is constant vigilance, promptly monitoring and taking action.
Short on time or expertise for managing cybersecurity incident response? Concerned about cybersecurity becoming a major distraction from your other tasks?
Discover more about Sophos Managed Detection and Response:
24/7 threat hunting, detection, and response ▶