
Security specialists recommend creating robust, intricate passwords to safeguard our online accounts and information from clever cyber offenders. And “intricate” usually indicates employing lowercase and uppercase characters, digits, and even special characters. However, complexity alone can still expose your password to decryption if it lacks sufficient characters, as stated in research conducted by security company Hive Systems.
In this piece, we examine the duration it would require for hackers to decrypt various types of passwords and what steps you can take to enhance their security.
The duration needed to decrypt a password
In their Hive Systems 2024 Password Table report, Hive determined that a sophisticated, eight-character password containing digits, symbols, and both upper and lower case letters will take seven years to decrypt — assuming an attacker had a state-of-the-art 12 x RTX 4090 graphics card.
Comparatively, a five-character password composed solely of upper and lower case letters could be decrypted in two minutes. Additionally, Hive mentions that a four-character password containing only lower case letters can be cracked instantly, whereas a five-character password featuring both upper and lower case letters can be decrypted in three seconds.
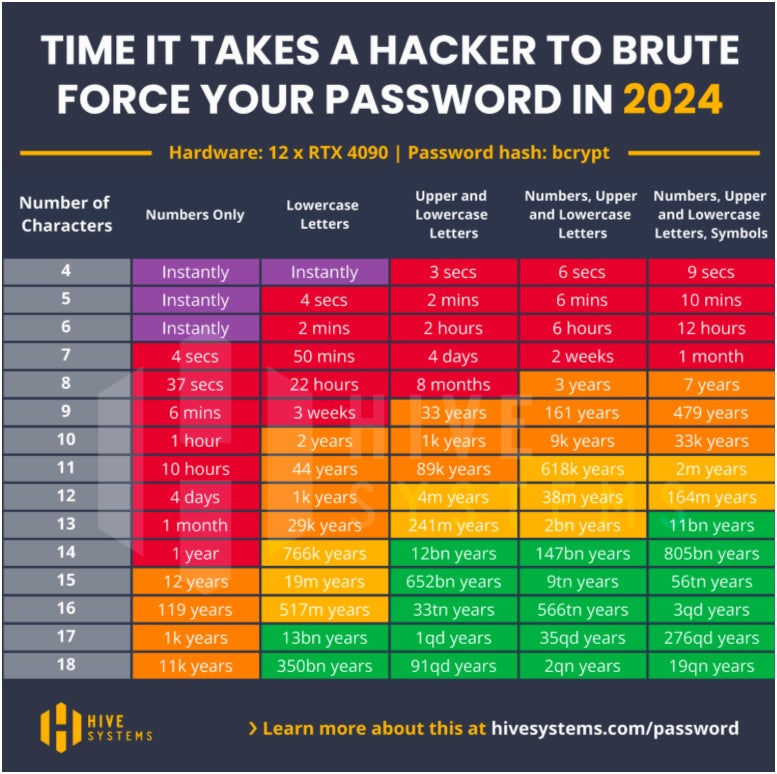
From my perspective, this highlights the imperative nature of adhering to best practices for passwords, like utilizing a blend of characters, symbols, and digits, whenever feasible. This is especially crucial due to the noticeable contrast in the potential decryption times based on the passwords’ complexity.
On a positive note, even simpler passwords with greater character counts are less prone to rapid decryption, per Hive’s findings. For instance, a numbers-only, 10-character password would require one hour to decrypt. Extending that password’s length to 18 characters would extend the decryption time to 11,000 years.
Regarding words versus digits, Hive’s statistics suggest that passphrases outshine traditional passwords. An 18-character password consisting solely of digits would necessitate 11,000 years to decrypt, whereas one with the same length but using lower case letters would demand 350 billion years for decryption. This demonstrates why passphrases, employing a lengthy sequence of genuine yet random words, can offer superior security compared to a short yet intricate password.
Hive’s report outlines that passphrases incorporating a mix of 18 upper and lower case letters, digits, and symbols pose the greatest challenge to brute force decryption.
Which instruments do hackers use to decrypt your passwords?
A hacker striving to rapidly decrypt sophisticated yet brief passwords would necessitate the most recent and advanced graphics processing technology. The more robust the graphics processing unit, the speedier it can undertake activities such as cryptocurrency mining and password decryption.
These GPUs enable hackers to launch brute-force attacks and leverage password-cracking software to speculate your passwords and other credentials. Brute-force attacks involve employing GPUs and machine-driven trial and error to pinpoint the ideal combination of characters, digits, and symbols to ultimately decrypt a user’s password.
For instance, one of today’s top GPUs is Nvidia’s GeForce RTX 4090, starting at $1,599. Nonetheless, even less potent and more affordable GPUs can crack passwords of modest length and complexity in a relatively brief time frame.
Hackers lacking cutting-edge graphics processing power on their systems can conveniently resort to cloud computing, as per Hive. By renting computing and graphics hardware via Amazon AWS and other cloud service providers, a cyber criminal can tap into multiple virtual instances of a potent GPU to execute password decryption at a reasonably low cost.
Furthermore, the advancements in AI have furnished hackers with an additional decryption tool that operates more swiftly and effectively. An April 2023 study by Home Security Heroes scrutinizing 15,600,000 common passwords unveiled that utilizing AI, hackers could decrypt 81% of them in under a month, 71% in less than a day, 65% in less than an hour, and 51% in under a minute.
SEE: Securing Linux Policy (TechRepublic Premium)
Techniques to shield yourself and your company from password hacking
With advancements in graphics and AI technology, passwords now take significantly less time to crack compared to just a couple of years ago. For instance, a seven-character password comprising letters, numbers, and symbols would have taken seven minutes to crack in 2020 but can now be cracked in just four seconds in 2023. In light of these technological developments, what strategies can you and your organization employ to enhance the security of your password-protected accounts and data? Below are some suggestions.
Consider employing a passphrase in place of a standard password
A passphrase typically consists of a lengthy series of random words. Passphrases are often more resilient than passwords and are generally easier to recall. For example, you could use something like “Sunset-cola-Mouse!” or “GatePen2BoxerRose”.
When opting for a passphrase, keep the following points in mind:
- Ensure it is a minimum of 10-15 characters or more.
- Avoid using common expressions or song lyrics.
- Select a passphrase that holds personal significance to you.
- Incorporate numbers and symbols into your passphrase.
For a more comprehensive guide, visit our What is a Passphrase? resource here.
Utilize a blend of digits, special characters, capitals, and small letters simultaneously
According to the findings of the Hive Systems report, the complexity of a password significantly affects its overall strength. By complexity, it means the inclusion of uppercase and lowercase letters, symbols, and numbers within passwords.
While incorporating one type of character enhances password security, combining all these elements delivers the most robust protection.
Implement a password organizer
As it is practically impossible to create and memorize multiple intricate and lengthy passwords on your own, a password organizer is indispensable. By utilizing a password organizer for personal use or within your enterprise, you can generate, store, and apply strong passwords for various websites and online accounts.
Recommended password managers
1Password

If you prefer a password manager with a polished user interface, I suggest 1Password. This tool features an intuitive and well-crafted desktop application that caters to both novices and experienced users, aiding in password organization.
Moreover, 1Password’s base subscription includes several additional security functionalities such as the Watchtower data breach scanner and secure password sharing and history features. It has also undergone independent audits by third-party firms to ensure compliance with its no-logs policy, guaranteeing user data privacy.
To delve deeper, peruse our comprehensive 1Password review.
Bitwarden

For those concerned with privacy, Bitwarden stands out as an open-source password manager that publicizes its source code for scrutiny. This level of transparency allows customers and stakeholders to assess Bitwarden’s code for vulnerabilities, a critical feature for a service that safeguards passwords. Additionally, Bitwarden provides one of the most generous free plans in the market, offering unlimited password storage across an endless array of devices for free users.
To find out more, explore our comprehensive Bitwarden review.
Keeper

If you require a password manager more tailored towards business needs, Keeper is worth considering. Their business package enables you to oversee your team’s credentials through features like the admin console, team management tools, and policy engine and enforcements. The enterprise plan offers additional team-oriented functions including AD and LDAP synchronization and SAML 2.0 authentication. I particularly appreciate Keeper’s folder and subfolder system, facilitating streamlined password management across teams and accounts.
To get more insights, visit our detailed Keeper review.
This article was originally published in August 2023. It was revised by Luis Millares in January 2025.




