Frauds
Your modest phone number holds more worth than you might imagine. Here is how it might end up in the wrong hands – along with ways to safeguard it from swindlers.
15 Jul 2024
•
,
7 min. read

What could potentially be one of the simplest methods to deceive someone of their funds – under a veil of anonymity, naturally?
Could it involve appropriating their credit card particulars, perhaps by utilizing digital skimming or breaching a database carrying sensitive personal details? Despite being effective, these practices might demand substantial resources and a degree of technical finesse.
How about extracting payment information through counterfeit websites? This approach could indeed fit the bill, but mimicking legitimate websites (and email addresses for “word of mouth” propagation) may not be everyone’s cup of tea. Chances are also high that discerning individuals with a knack for security will detect such schemes promptly or nullify them with security measures.
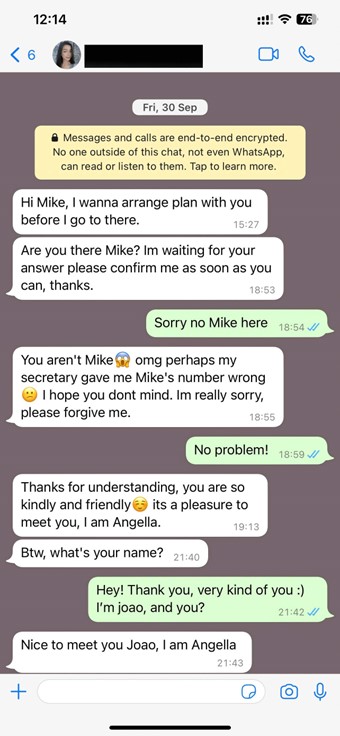
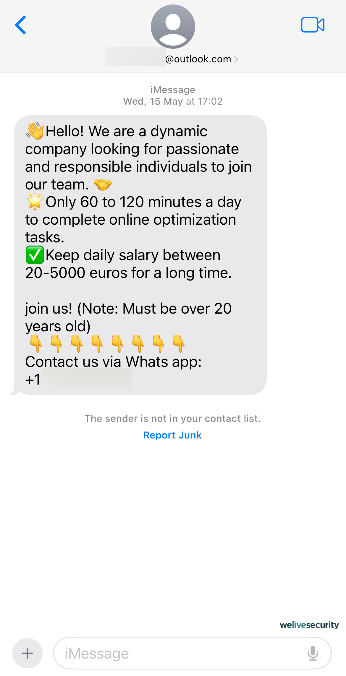
Instead, malevolent agents are opting for significantly expandable operations bankrolled on intricate social manipulation strategies that incur minimal expenses. Through voice phishing (termed vishing) and message scams (known as smishing), these setups have evolved into a scam call-center industry valued in the billions.
To kick off, these stratagems may not mandate specialized or technical expertise. Additionally, an individual (often a target of human trafficking) can simultaneously entrap multiple unsuspecting victims in diverse forms of deceit. These typically encompass pig butchering, cryptocurrency schemes, romance scams, and tech support fraud, each weaving a convincing narrative and exploiting some of our intrinsic human traits.
Hey, anyone out there listening?
Visualize receiving a call from your bank stating that your account has been compromised, and for safeguarding your funds, you are required to divulge sensitive information. The urgency in the voice of the bank’s purported “employee” might be sufficient to prompt you to disclose your private details. The catch is, this individual might not be affiliated with your bank – or they could merely be a fabricated persona, yet sounding entirely genuine.
This scenario is not infrequent, with cautionary anecdotes from recent years aplenty. In 2019, a CEO fell victim to a swindle, forfeiting nearly US$250,000 due to a convincing voice deepfake impersonating their parent company’s head honcho. Similarly, in 2024, a financial professional was duped via a deepfake video call, resulting in a US$25 million loss for their organization.
AI, the facilitator
With contemporary AI-driven voice replication and translation capabilities, vishing and smishing have become streamlined. Undoubtedly, ESET Global Cybersecurity Advisor Jake Moore showcased how effortlessly anyone can craft a compelling deepfake of another person – even someone familiar to you. Seeing and hearing are no longer unimpeachable.
AI is diminishing the entry barrier for budding adversaries, functioning as a versatile instrument to amass data, automate monotonous tasks, and extend their global influence. Consequently, leveraging artificial intelligence-generated voices and text for phishing will likely become more prevalent.
In this context, a recent study by Enea highlighted a 1,265% surge in phishing scams subsequent to ChatGPT’s unveiling in November 2022, emphasizing the potential of extensive language models in fueling such nefarious maneuvers.
What’s your title, what’s your digits?
As corroborated by Consumer Reports’ 2022 research, people are growing more cautious about privacy than previously. Roughly 75% of the survey’s participants expressed a certain level of apprehension regarding the privacy of their web-sourced data, which could encompass phone numbers, considered a valuable asset for authentication and marketing.
But now that we have surpassed the era of the Yellow Pages, how does this interplay between phone numbers and advertising function?
Consider thisExemplary case: A baseball enthusiast added tickets to a specialized app’s cart but failed to finalize the transaction. Shortly after exiting the app, he was contacted by phone with an offer for a discounted rate on the tickets. This left him puzzled as he had not consciously shared his phone number with the app. So, how did they obtain his number?
The explanation lies in tracking. Certain tracking mechanisms can gather specific details from a webpage; hence, after entering their phone number into a form, a tracker could identify and retain it for the purpose of creating what is commonly referred to as personalized content and experiences. There exists a whole business model known as “data brokering”, and the regrettable truth is that data doesn’t necessarily need to be breached to become public.
Monitoring, data vendors, and disclosures
Data vendors amass your personal data from publicly accessible resources (official licenses/registrations), commercial channels (collaborative partners such as credit card issuers or retailers), as well as by monitoring your online engagements (interactions on social media, ad clicks, etc.), before vending this data to third parties.
However, you might be inquisitive about how scammers manage to procure other individuals’ phone numbers?
Essentially, the more companies, sites, and apps you entrust with your personal data, the more comprehensive your personal “marketing profile” becomes. Consequently, this heightens your vulnerability to data leaks, as data vendors themselves may also experience security breaches. A data vendor might also trade your details with others, potentially including malign agents.
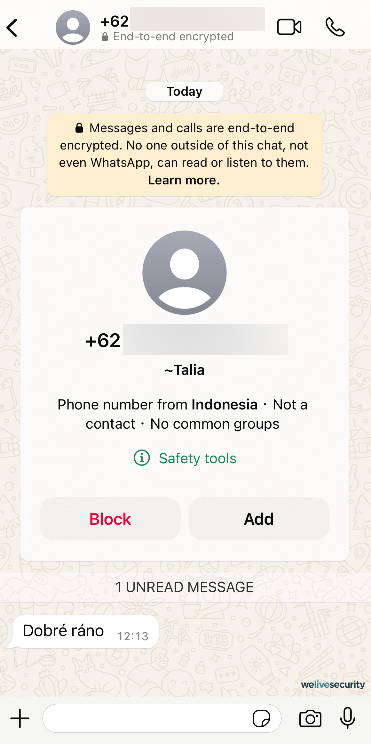
Yet, data vendors, or breaches affecting them, are not the sole sources of phone numbers for fraudsters. Here are some alternative methods through which criminals can access your phone number:
- Publicly available sources: Social networking sites or online job platforms may exhibit your phone number as a mode of connection. In instances where your privacy settings are not properly configured or you are oblivious to the repercussions of disclosing your phone number on your social media profile, your number could be accessible to anyone, including an automated web scraper.
- Compromised accounts: Various online services mandate your phone number for identification purposes, order placement, or as an authentication factor. In cases where your accounts are penetrated due to feeble passwords or if one of your online providers undergoes a data breach, your number could easily leak as well.
- Automated callers: Automated calling systems dial random numbers, and the moment you pick up the call, you may be pursued by a scam. Occasionally, these automated callers ring to verify that the number is actively used, enabling its inclusion in a list of targets.
- Postal mail: Review your recent deliveries – these typically display your address on the package/letter, but occasionally, they might also present your email or phone number. Suppose someone pilfered one of your deliveries or perused through your discarded items? Given that data breaches generally comprise similar details, this could be extremely hazardous, laying grounds for further exploitation.
To cite a vast breach that involved phone numbers, AT&T recently disclosed that millions of consumers’ call and text message logs from the latter half of 2022 were exposed in a monumental data breach. Nearly all the firm’s clientele and individuals utilizing the cellular network have had their phone numbers, call durations, and quantity of call interactions laid bare. While call and message contents purportedly were not part of the breached data, customer names and numbers can still be effortlessly correlated, as outlined by CNN.
Reportedly, a third-party cloud platform is to blame, having been infiltrated by a malicious actor. Incidentally, this very platform has hosted several instances of extensive leaks linked to it in recent times.
Securing your phone number
So, how can you safeguard yourself and your number? Here are a few suggestions:
- Stay cautious of phishing. Refrain from responding to unsolicited messages/calls from international numbers, avoid clicking on random links in your emails/messages, and remember to maintain composure and think before reacting to an ostensibly urgent scenario, as that’s how they ensnare you.
- Inquire with your service provider about their SIM security protocols. They may offer options for card locks to combat SIM swapping, for instance, or supplementary account security layers to thwart scams like call forwarding.
- Fortify your accounts with two-factor authentication, preferably employing dedicated security keys, applications, or biometrics instead of SMS-based verification. The latter can be intercepted by malicious actors with relative ease. Implement this for service provider accounts too.
- Exercise caution prior to divulging your phone number to a website. While having it as an additional recovery choice for your diverse applications may be beneficial, other alternatives like secondary emails/authenticators could potentially offer more secure options.
- For online transactions, contemplate utilizing a prepaid SIM card or a VoIP service in place of your regular number.
- Utilize a mobile security solution with call screening capabilities, and ensure that third-party cookies in your web navigator are blocked, exploring other privacy-enhancing tools and technologies.
In a society increasingly reliant on digital record-keeping, it’s unlikely that your number won’t be retained by some third party. As illustrated by the AT&T incident, depending solely on your carrier’s security measures can be problematic. However, this doesn’t signify that you must remain in a state of perpetual paranoia.
On the contrary, it underscores the necessity of adhering to proper cyber hygiene and staying informed about your online data. Vigilance still remains crucial, particularly when contemplating the implications of this emerging, AI-dominated underworld.





