Frauds
Don’t underestimate the significance of your simple phone number. Learn how it could end up in the wrong hands and ways to prevent it from falling into the grasp of scammers.
15 Jul 2024
•
,
7 min. read

What could be one of the simplest methods to deceive someone into revealing their finances – without revealing their identity?
Could it involve acquiring their credit card information through methods like digital skimming or hacking into databases of sensitive personal data? While effective, these techniques may demand resources and technical skills.
What about obtaining payment details through counterfeit websites? This tactic might work, but impersonating legitimate websites (and email addresses to “spread the word”) might not suit everyone. There’s also a high likelihood that such schemes will be detected early by those knowledgeable about security or blocked by security measures.
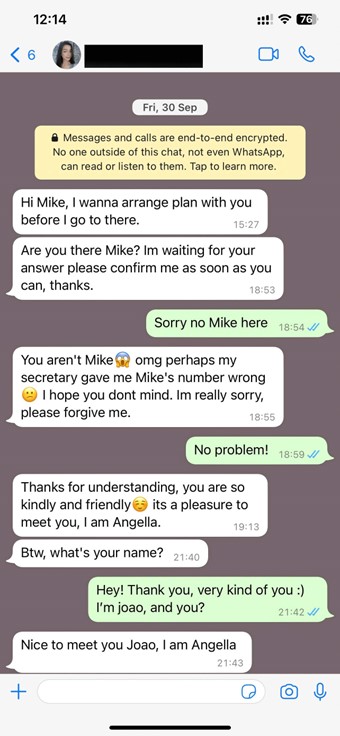
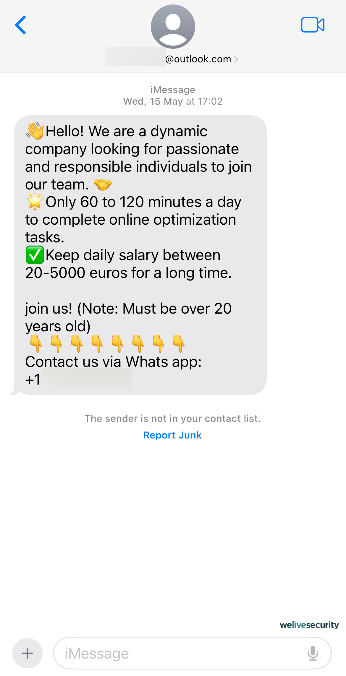
Instead, malicious actors are adopting highly scalable methods that rely on advanced social engineering strategies and require minimal expenses. Through voice phishing (also known as vishing) and message scams (smishing), these operations have evolved into a massive scam call-center industry worth billions of dollars.
Primarily, these tactics may not demand specialized skills or technical expertise. Additionally, a single individual (often a victim of human trafficking) can entangle multiple unsuspecting victims in various scams. These may include pig butchering, cryptocurrency frauds, romance deceptions, and tech support schemes, each weaving a captivating story and exploiting our vulnerable human aspects.
Hey there? Is this communication working?
Imagine receiving a call purportedly from your bank, claiming your account has been compromised and demanding you disclose your sensitive information to secure your funds. The urgency in the voice of the “bank employee” might convince you to share your details. However, this individual may not be affiliated with your bank – or they might not even exist. Their voice could be fabricated yet sound completely authentic.
Instances like this are not uncommon, with numerous cautionary tales from recent times. For instance, in 2019, a CEO fell victim to a nearly US$250,000 scam involving a convincing voice deepfake impersonating the chief of their parent company. Similarly, a financial worker was deceived via a deepfake video call in 2024, leading to a loss of US$25 million for their firm.
AI, the facilitator
Thanks to advanced AI voice replication and translation capabilities, vishing and smishing have become more accessible than ever. In fact, ESET Global Cybersecurity Advisor Jake Moore demonstrated how effortlessly anyone can create a convincing deepfake of another person – even someone familiar to them. Seeing and hearing no longer equate to believing.
AI is reducing the entry barrier for new adversaries, acting as a versatile tool to gather information, automate mundane tasks, and expand their global influence. Consequently, phishing using AI-generated audio and text will likely become more prevalent.
In this context, a recent report by Enea highlighted a 1,265% surge in phishing scams following the debut of ChatGPT in November 2022 and underscored the influence of large language models in bolstering such malevolent activities.
Who are you, what’s your contact?
According to Consumer Reports’ 2022 study, people are growing more cautious of their privacy compared to earlier. Around 75% of respondents in the survey expressed some level of concern about the privacy of their online-collected data, including phone numbers, which are crucial for identification and marketing purposes.
But now that the era of the Yellow Pages is long gone, how does this association between phone numbers and advertisements function?
Contemplate thisexemplary instance: a passionate baseball enthusiast inserted tickets into a specialized app’s cart but did not finalize the transaction. Shortly after closing the application, he was contacted by phone with an offer for a discounted price on the tickets. Naturally, he was puzzled as he did not recall furnishing his phone number to the app. How did the app acquire his number, then?
The solution lies in – through tracking. Certain trackers possess the ability to gather specific details from a webpage, hence, post entering your phone number on a form, a tracker might identify and retain it to develop what is frequently referred to as customized content and experience. There exists a complete business strategy known as “data brokering”, and the negative news is that a breach is not requisite for the data to become public.
Tracking, data intermediaries, and breaches
Data intermediaries gather your personal details from publicly accessible sources (government permits/registrations), commercial channels (business affiliates such as credit card issuers or stores) as well as by monitoring your online pursuits (engagements on social media, advertisement clicks, etc.), before vending your information to others.
However, you might be curious about how scammers manage to access other individuals’ phone numbers, right?
Naturally, the more corporations, websites, and applications you disclose your personal data to, the more comprehensive your personal “marketing profile” becomes. This, in turn, elevates your vulnerability to data breaches, since data intermediaries themselves might encounter security breaches. An intermediary could also sell your details to others, potentially involving malicious entities.
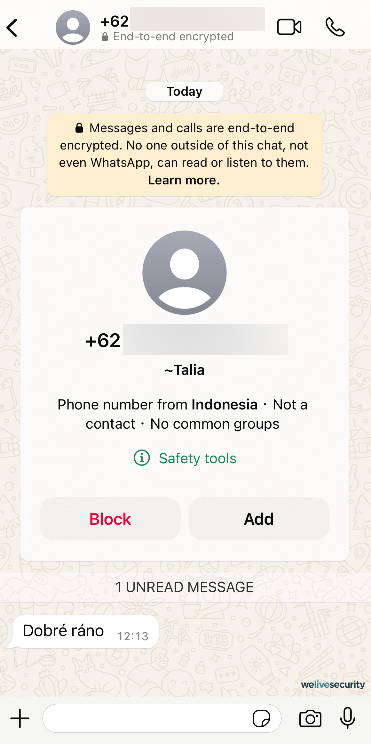
Nevertheless, data intermediaries, or breaches impacting them, are not the exclusive sources of phone numbers for scammers. Here are some alternative methods by which malefactors can access your phone number:
- Public references: Social media platforms or online job portals may display your phone number for networking purposes. In scenarios where your privacy settings are inadequately adjusted or you are oblivious to the consequences of disclosing your phone number in your social media profile, your number could be accessible to anyone, including an AI internet data collector.
- Pilfered accounts: Various online services necessitate your phone number, whether to authenticate your identity, to finalize an order, or to serve as an authentication element. When your accounts are improperly accessed due to feeble passwords or when one of your digital service providers suffers a data breach your number could effortlessly be exposed as well.
- Automated dialers: Automated dialers contact random numbers, and upon answering the call, you might be singled out for a potential scam. At times, these automated dialers place calls merely to verify the activity on the number so that it can be included in a roster of targets.
- Correspondence: Inspect any of your recent shipments – typically, these bear your address visible on the parcel, but occasionall, they may also exhibit your email or phone number. What if someone pilfered one of your shipments or searched through your discarded items? Given that data breaches commonly encompass the same details, this could be very perilous and provide grounds for further exploitation.
As an illustration of a large-scale data breach affecting phone numbers, AT&T recently disclosed that millions of customers’ call and text message logs from the mid-to-late 2022 period were laid bare in a substantial data leak. Nearly all patrons of the company and cellular network users have had their numbers, call durations, and quantity of call engagements exposed. While call and text contents are purportedly not part of the disclosed data, customer identities and numbers can still be readily connected, as highlighted by CNN.
Sources suggest that a third-party cloud platform can be held accountable for the incident, as it was accessed by a malicious actor. Coincidentally, the same platform has encountered several instances of substantial data leaks associated with it in recent times.
Strategies to safeguard your phone number
Hence, how can you shield yourself and your number? Here are a handful of recommendations:
- Remain cautious of phishing. Refrain from responding to unsolicited messages/calls from unfamiliar numbers, abstain from clicking random links in your emails/messages, and bear in mind to keep composed and deliberate before reacting to ostensibly pressing situations, as that’s how they lure you in.
- Inquire with your service provider about their SIM protection protocols. They might offer card locks to counteract SIM swap scams, for instance, or supplementary account security layers to thwart scams like call forwarding.
- Secure your accounts with two-step verification, preferably deploying dedicated security keys, applications, or biometrics instead of SMS-based authentication. The latter can be intercepted by malefactors with relatively little effort. Extend this practice to service provider accounts as well.
- Contemplate before furnishing your phone number to a website. While having it as an extra recovery option for your diverse applications could prove beneficial, other alternatives like secondary emails/authenticators could present a more secure substitute.
- For online transactions, contemplate utilizing a prepaid SIM card or a Voice over Internet Protocol (VoIP) service instead of your standard phone number.
- Adopt a mobile security software with call filtering, alongside ensuring that third-party cookies in your web browser are disabled, and explore additional privacy-enhancing tools and technologies.
In a world that depends increasingly on digital archival practices, it is improbable that your number will not be preserved by a third party somewhere. As indicated by the AT&T incident, relying solely on the security measures of your carrier poses its own set of challenges. Nonetheless, this should not compel you to maintain a perpetual state of paranoia.
Conversely, it underscores the significance of adhering to sound cyber hygiene and being mindful of your online data. Vigilance remains crucial, especially when contemplating the repercussions of this burgeoning, AI-driven underworld.








