
ESET Investigation
A recent discovery by ESET researchers uncovers a zero-day exploit in Telegram for Android allowing the circulation of disguised malicious files as videos
22 Jul 2024
•
,
6 minutes read

ESET analysts unearthed a zero-day exploit targeting Telegram for Android, which emerged for purchase at an unspecified rate in an underground discussion on June 6th, 2024. By utilizing this exploit to manipulate a vulnerability termed as EvilVideo, cyber attackers could distribute harmful Android packages through Telegram channels, groups, and chats, camouflaging them as multimedia files.
An example of the exploit was located, enabling further examination and prompt reporting to Telegram on June 26th, 2024. Consequently, on July 11th, Telegram released an update rectifying the vulnerability in versions 10.14.5 and above.
Illustration 1 showcases a video to elucidate the EvilVideo vulnerability.
Illustration 1. Clarification of EvilVideo vulnerability
Main points from the blogpost:
- An advertisement for a zero-day exploit on Telegram for Android surfaced in an underground discussion on June 26th, 2024.
- EvilVideo, the exploit’s target, was promptly reported to Telegram, resulting in its resolution on July 11th, 2024.
- EvilVideo empowers threat actors to disseminate harmful packages disguised as videos on unpatched Telegram for Android versions.
- The exploit is solely effective on Android Telegram versions 10.14.4 and earlier.
Unveiling
We encountered the exploit being advertised for sale within an underground discussion: refer to Illustration 2.
In the advertisement, the seller showcased screenshots and a video of the exploit testing within a public Telegram channel. We successfully identified the concerned channel where the exploit was still active, allowing us to acquire the payload for verification purposes.
Critical Examination
An in-depth review of the exploit disclosed its compatibility with Telegram versions 10.14.4 and preceding releases. It is apparent that the unique payload is likely formulated utilizing the Telegram API, granting developers the ability to upload meticulously crafted multimedia files to Telegram chats or channels programmatically.
The exploit’s effectiveness leans on the threat actor’s adeptness in creating a payload presenting an Android application as a multimedia preview, rather than a binary attachment. Once distributed in the chat, the malicious payload masquerades as a 30-second video (Illustration 3).
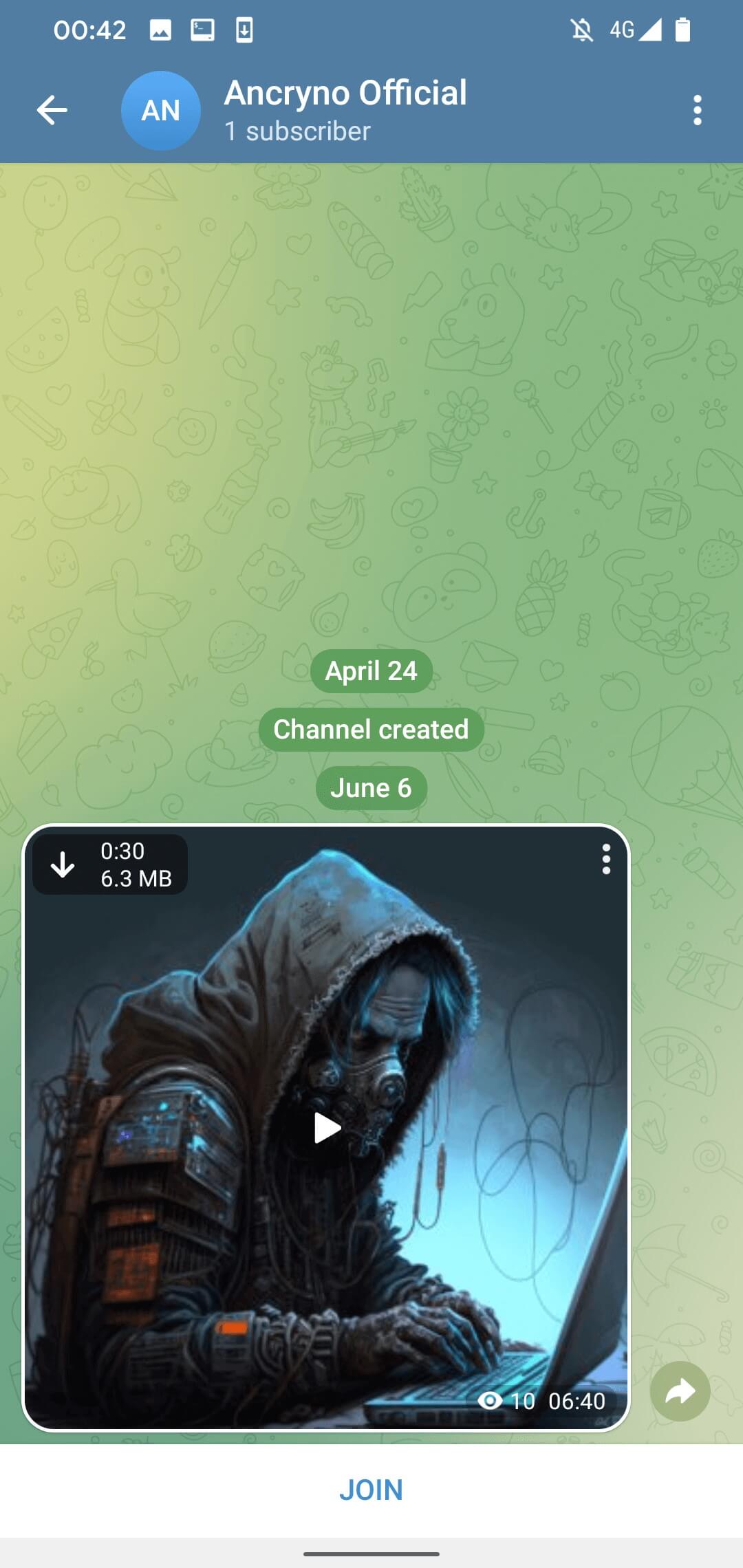
As a default setting, media files transmitted via Telegram prompt automatic downloads. Consequently, users who have this option enabled will automatically download the malicious payload upon opening the relevant conversation. For manual downloading, the payload can still be retrieved by tapping the download button located at the top left of the disguised video, as visible in Illustration 3.
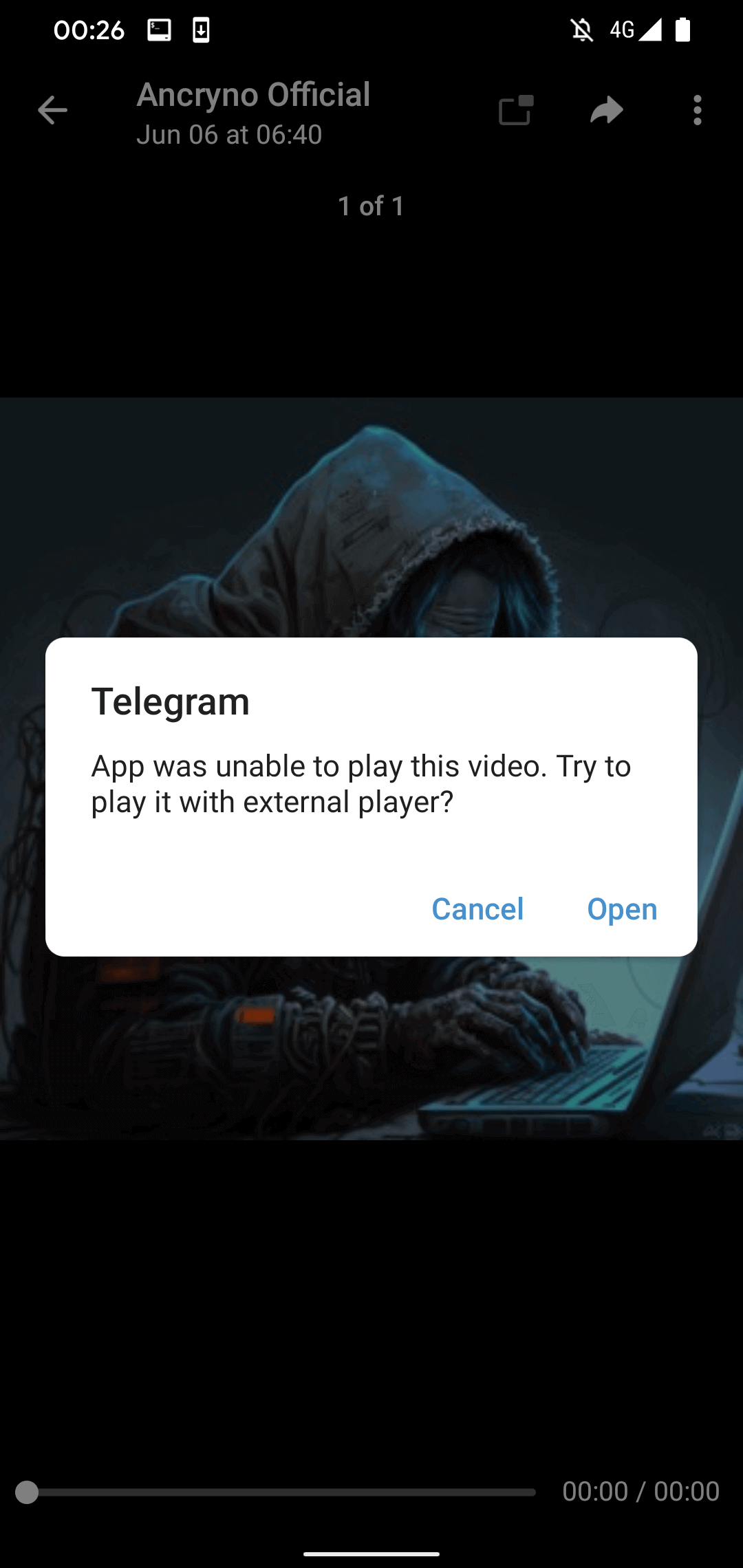
If the user endeavors to play the “video,” Telegram issues a notification stating its inability to play it and proposes utilizing an external player (refer to Illustration 4). This authentic warning by Telegram was identified within the source code of the legitimate Telegram for Android application; it is not a contrived message propelled by the malicious payload.
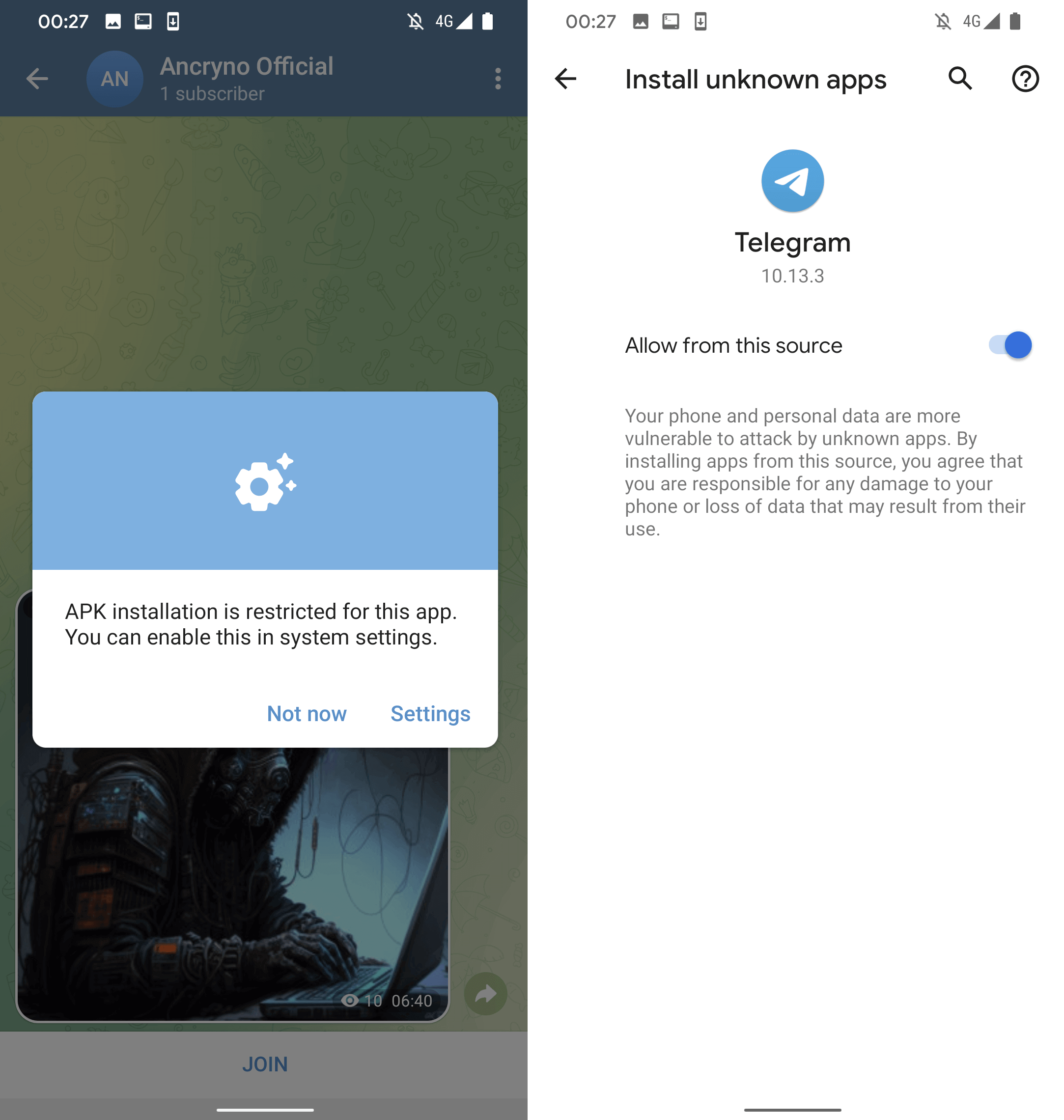
Nonetheless, upon tapping the Open button in the notification, the user is solicited to install a malicious application disguised as the aforementioned external player. Before installation, Telegram necessitates the user to sanction the installation of unknown applications, as depicted in Illustration 5.
At this juncture, the malevolent application, previously downloaded as a feigned video file, emerges with the .apk extension. Interestingly, the vulnerability’s exploit makes the shared file mimic a video – the actual malicious application was not modified to impersonate a multimedia file, suggesting that the upload process was likely the point of exploitation. The appeal for the installation of the malevolent application can be witnessed in Illustration 6.
Regrettably, replication of the exploit evaded us, but we were able to scrutinize and authenticate the sample shared by the seller.
Telegram Web and Desktop
Despite the payload’s targeting of Telegram for Android, we ventured to assess its behavior on other Telegram platforms. Both the Telegram Web client and the Telegram Desktop client for Windows were scrutinized – the resultant revelation being the exploit’s inefficacy on either of these platforms.
In the context of Telegram Web, post attempting to initiate the “video,” the client displayed an error message advising to utilize the desktop application instead (refer to Illustration 7). Upon manually downloading the attached file, its name and extension were revealed to be Teating.mp4. Although the file itself was an Android executable binary (APK), Telegram’s recognition of it as an MP4 file thwarted the exploit: for successful execution, the attachment was mandated to carry the .apk extension.
A similar scenario unfurled with the Telegram Desktop client for Windows: the downloaded file was labeled Teating.apk.mp4, underscoring the nature of an APK binary file with an appended .mp4 extension. This observation signifies that even if an assailant contrived aReplace “executable” with “program”, “treated” with “regarded”, and “seller” with “vendor”:
Program to be used instead of the Android APK, it would still be regarded as a multimedia file and the exploit would not work.

Threat actor
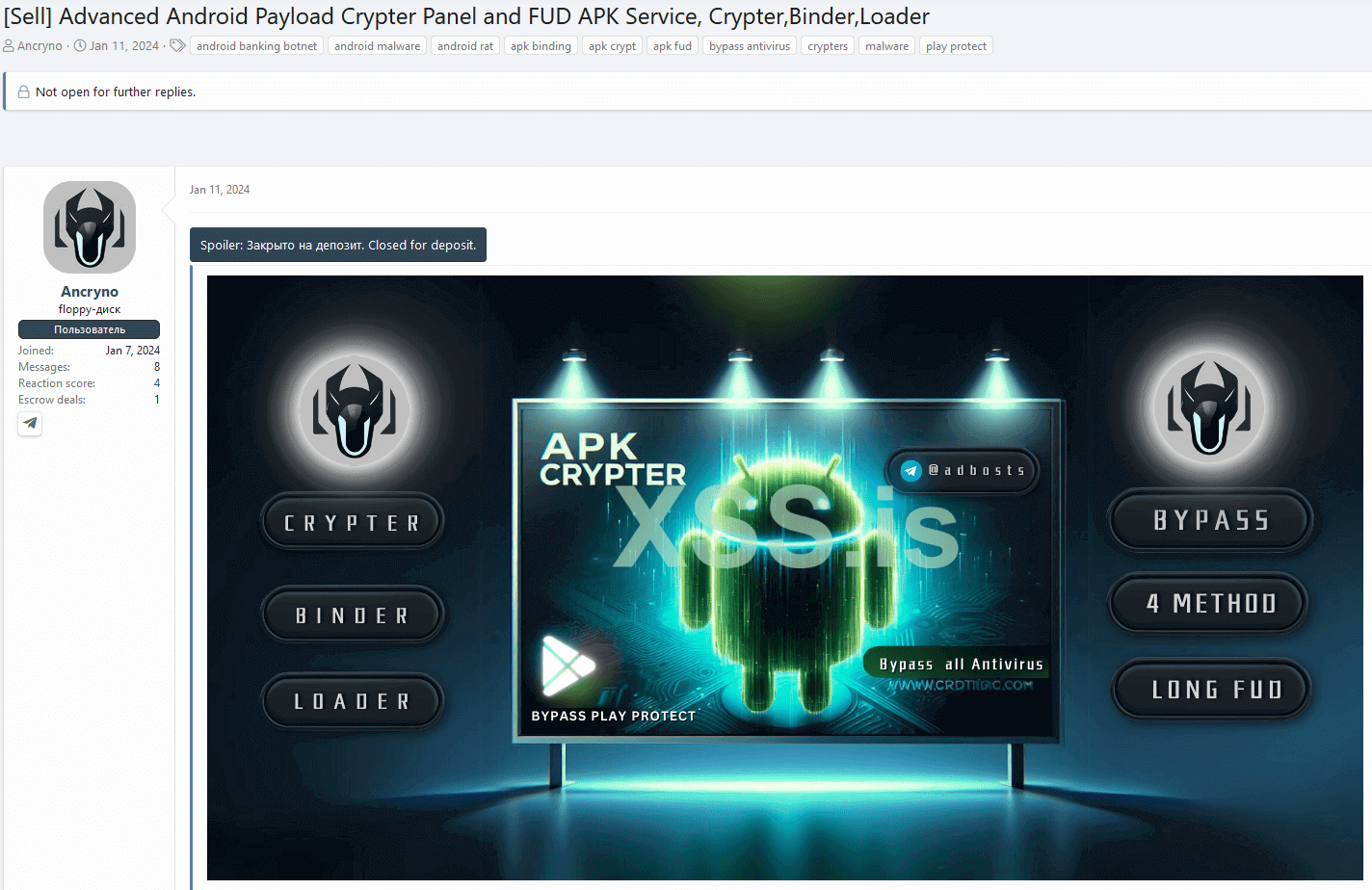
While we do not know much about the threat actor, we managed to find another shady service they are providing based on the Telegram handle the vendor shared in their forum post. In addition to the exploit, they have been using the same underground forum to advertise an Android cryptor-as-a-service that they claim is fully undetectable (FUD) since January 11th, 2024. The forum post can be seen in Figure 8.
Vulnerability report
After discovering the EvilVideo vulnerability on June 26th, 2024, we followed our coordinated disclosure policy and reported it to Telegram, but received no response at the time. We reported the vulnerability again on July 4th, and that time, Telegram reached out to us the same day to confirm its team was investigating EvilVideo. They fixed the issue, shipping version 10.14.5 on July 11th, and informed us via email.
The vulnerability affected all versions of Telegram for Android up to 10.14.4, but has been patched as of version 10.14.5. As we verified, the chat multimedia preview now correctly displays that the shared file is an application (Figure 9) and not a video.

Conclusion
We discovered a zero-day Telegram for Android exploit for sale on an underground forum. The vulnerability it exploits allows sending malicious payloads that look like multimedia files via Telegram chat. If a user tries to play the apparent video, they will receive a request to install an external app, which actually installs the malicious payload. Luckily, the vulnerability has been fixed as of July 11th, 2024, after we reported it to Telegram.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.comESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
A comprehensive list of Indicators of Compromise (IoCs) and samples can be found in our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinityhackscharan. |
Administrator Beam Cable System |
2024‑07‑16 |
C&C server of EvilVideo payload. |
MITRE ATT&CK techniques
This table was built using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Exploitation for Initial Access |
The EvilVideo vulnerability can be abused by Android malware to achieve initial device access. |
|
|
Execution |
Exploitation for Client Execution |
The EvilVideo vulnerability tricks the victim into installing a malicious app that impersonates a multimedia file. |








