
ESET Study
ESET researchers stumbled upon a new Telegram for Android exploit that permits sending deceptive files disguised as videos
22 Jul 2024
•
,
6 minutes read

ESET researchers uncovered a zero-day exploit targeting Telegram for Android, which surfaced for sale at an undisclosed cost in an underground blog post dated June 6th, 2024. By leveraging the exploit to manipulate a vulnerability dubbed MalevolentFilm, attackers could distribute harmful Android payloads via Telegram channels, groups, and chats, disguising them as multimedia files.
An instance of the exploit was tracked down, enabling further analysis and prompt reporting to Telegram on June 26th, 2024. Telegram released a fix for the vulnerability in versions 10.14.5 and higher on July 11th, 2024.
Figure 1 provides a visual presentation and elucidation of the MalevolentFilm vulnerability.
Figure 1. Elucidation of the MalevolentFilm vulnerability
Main points from the blog:
- On June 26th, 2024, an underground forum exhibited an advertisement for a zero-day exploit targeting Telegram for Android.
- We designated the exploited vulnerability as MalevolentFilm and reported it to Telegram; their team addressed it on July 11th, 2024.
- MalevolentFilm enables attackers to dispatch harmful payloads cloaked as video files in unpatched versions of Telegram for Android.
- The exploit exclusively functions on Android Telegram editions 10.14.4 and earlier.
Uncovering
We stumbled upon the exploit being marketed for sale on an underground forum: check out Figure 2.
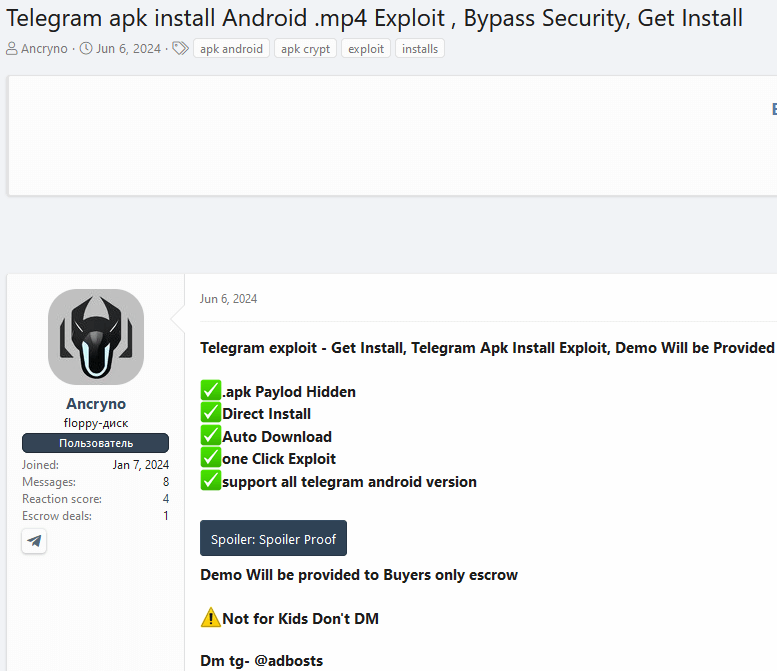
In the post, the vendor showcased screenshots and a video demonstrating the exploit in a public Telegram channel. We managed to identify the specific channel and access the exploit, facilitating our evaluation and testing.
Examination
Our evaluation of the exploit unveiled its compatibility with Telegram versions 10.14.4 and earlier. We speculate that the bespoke payload is likely fabricated leveraging the Telegram API, given its ability to systematically upload tailor-made multimedia files to Telegram conversations or channels.
The exploit appears to hinge on the threat actor fabricating a payload that showcases an Android application as a multimedia preview rather than a binary attachment. Post-sharing in a chat, the malevolent payload masquerades as a 30-second video (Figure 3).
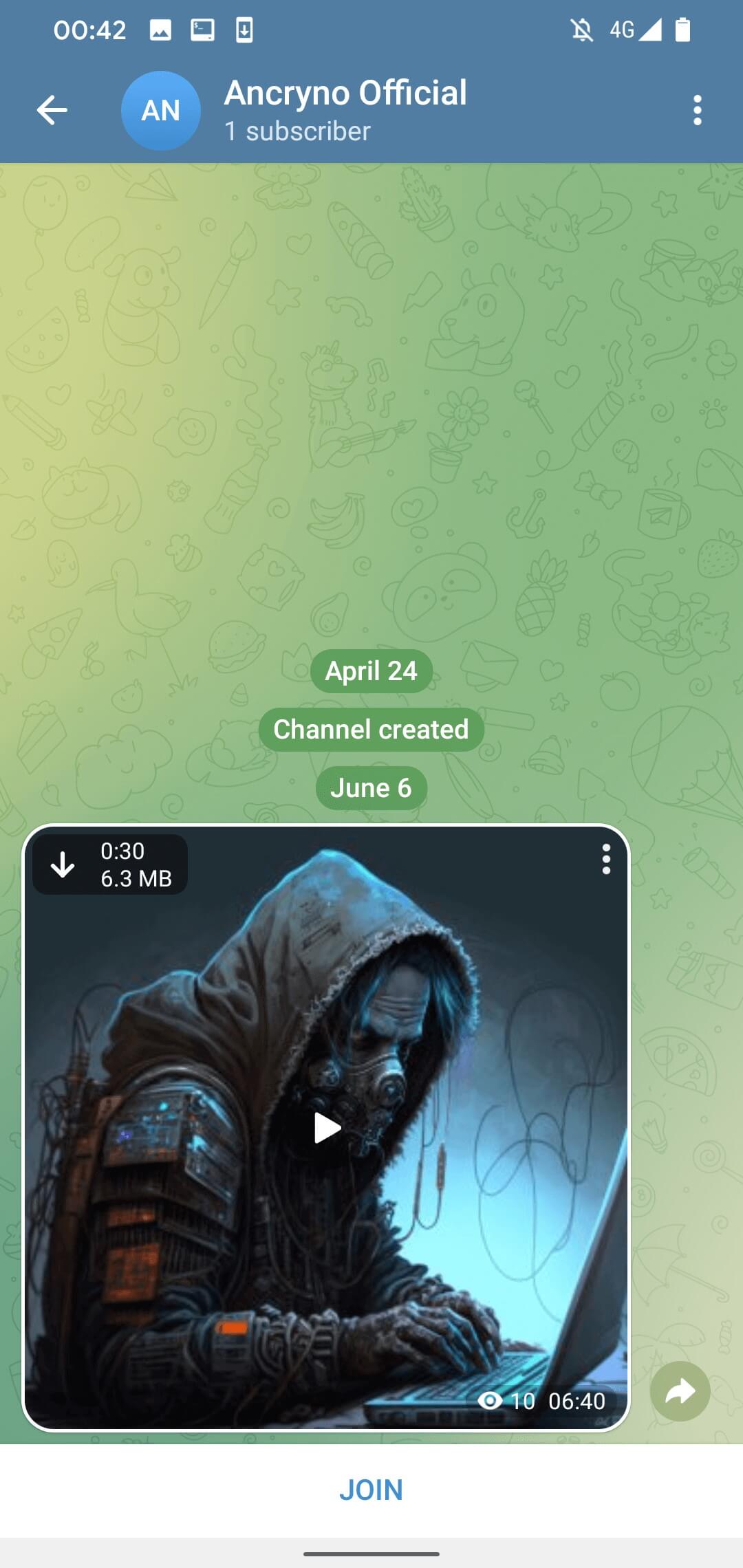
As standard, media files received over Telegram are configured to auto-download. Consequently, users with this setting active will automatically download the harmful payload upon accessing the conversation where it was shared. Manual deactivation is an option – in such instances, the payload remains downloadable upon tapping the download icon in the top-left corner of the ostensibly shared video, as depicted in Figure 3.
Upon attempting to play the “video,” Telegram presents an error message indicating its inability to play it, along with a suggestion to employ an external player (see Figure 4). This warning is authentic and sourced from the legitimate Telegram for Android application’s codebase, as opposed to being contrived and propagated by the malevolent payload.
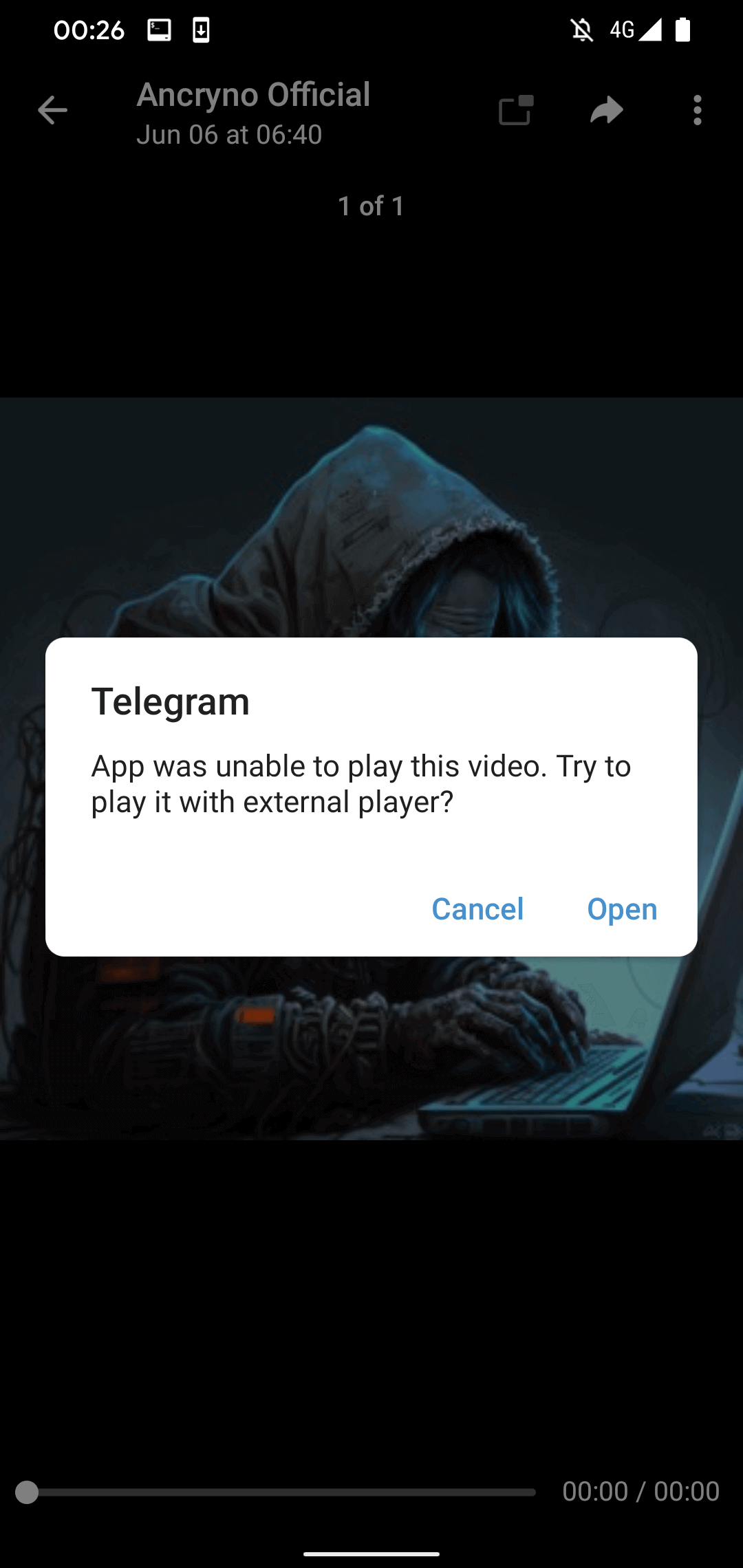
Nevertheless, if the user opts to tap the “Open” prompt in the displayed message, they will be prompted to install a malevolent application masked as the earlier mentioned external player. As seen in Figure 5, prior to installation, Telegram will solicit the user’s approval to install untrusted applications.
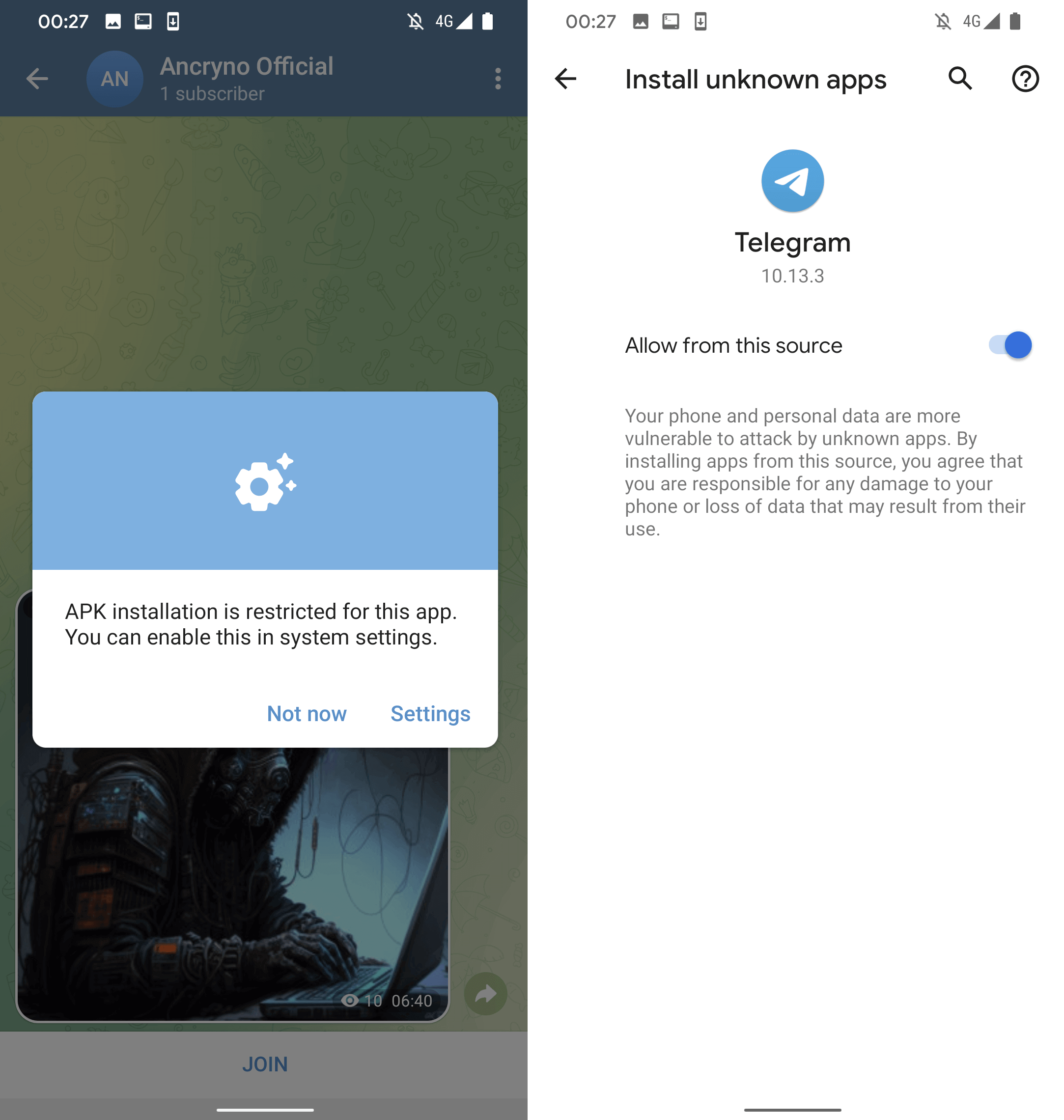
At this juncture, the malevolent application has already been downloaded under the guise of a video file, yet bearing the .apk extension. Interestingly, the anomaly of the flaw causes the shared file to mimic a video – the actual malevolent application remains unaltered to appear as a multimedia file, hinting at the potential exploitation of the upload process. The appeal for installation of the illicit application can be observed in Figure 6.
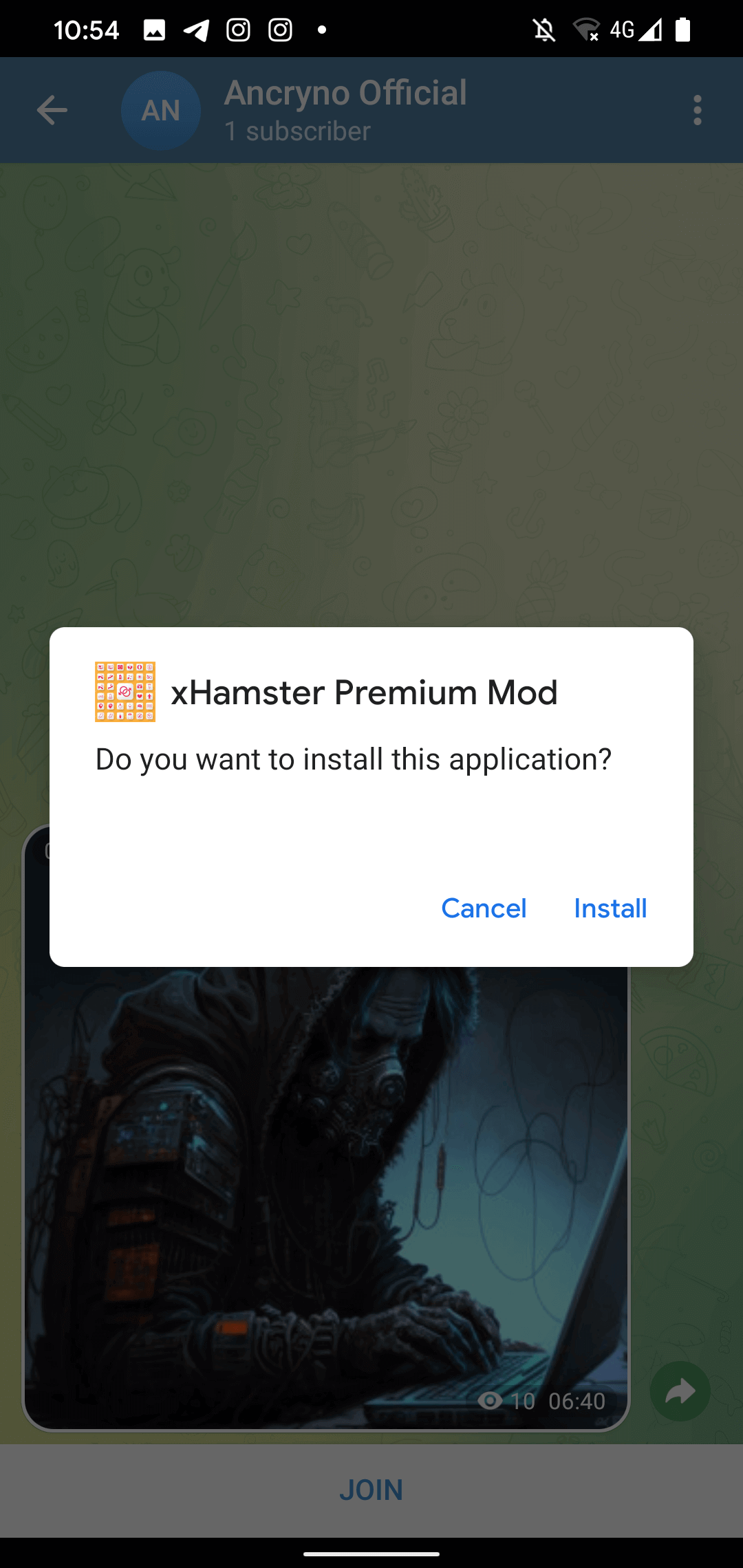
Regrettably, we were unable to recreate the exploit, solely able to scrutinize and authenticate the specimen shared by the vendor.
Telegram Web and Desktop
Despite the exploitation targeted at Telegram for Android solely, we decided to inspect how it behaves on alternative Telegram clients. Both the Telegram Web client and the Telegram Desktop client for Windows were tested – unsurprisingly, the exploit failed on both platforms.
With regards to Telegram Web, upon initiating play on the “video,” the client exhibited an error directive advising the utilization of the desktop application instead (refer to Figure 7). Upon manual download of the attached file, we determined its title and extension to be Teating.mp4. Although the file was essentially an Android executable binary (APK), Telegram’s interpretation as an MP4 file prevented the exploitation: for it to materialize, the attachment should have held the .apk extension.
A similar scenario unfolded on the Telegram Desktop client for Windows: the downloaded file was dubbed Teating.apk.mp4, indicating it was again an APK binary with an appended .mp4 extension. This implies that even if a perpetrator engineered aA Windows application should be used instead of the Android APK, treating it as a multimedia file to prevent exploitation.

Adversary
The threat actor’s identity remains elusive; however, we did uncover another dubious service they offer through the Telegram handle disclosed in their forum post. Apart from the exploit, they are also promoting an Android cryptor-as-a-service on the same underground forum since January 11th, 2024. Refer to Figure 8 for the forum post details.
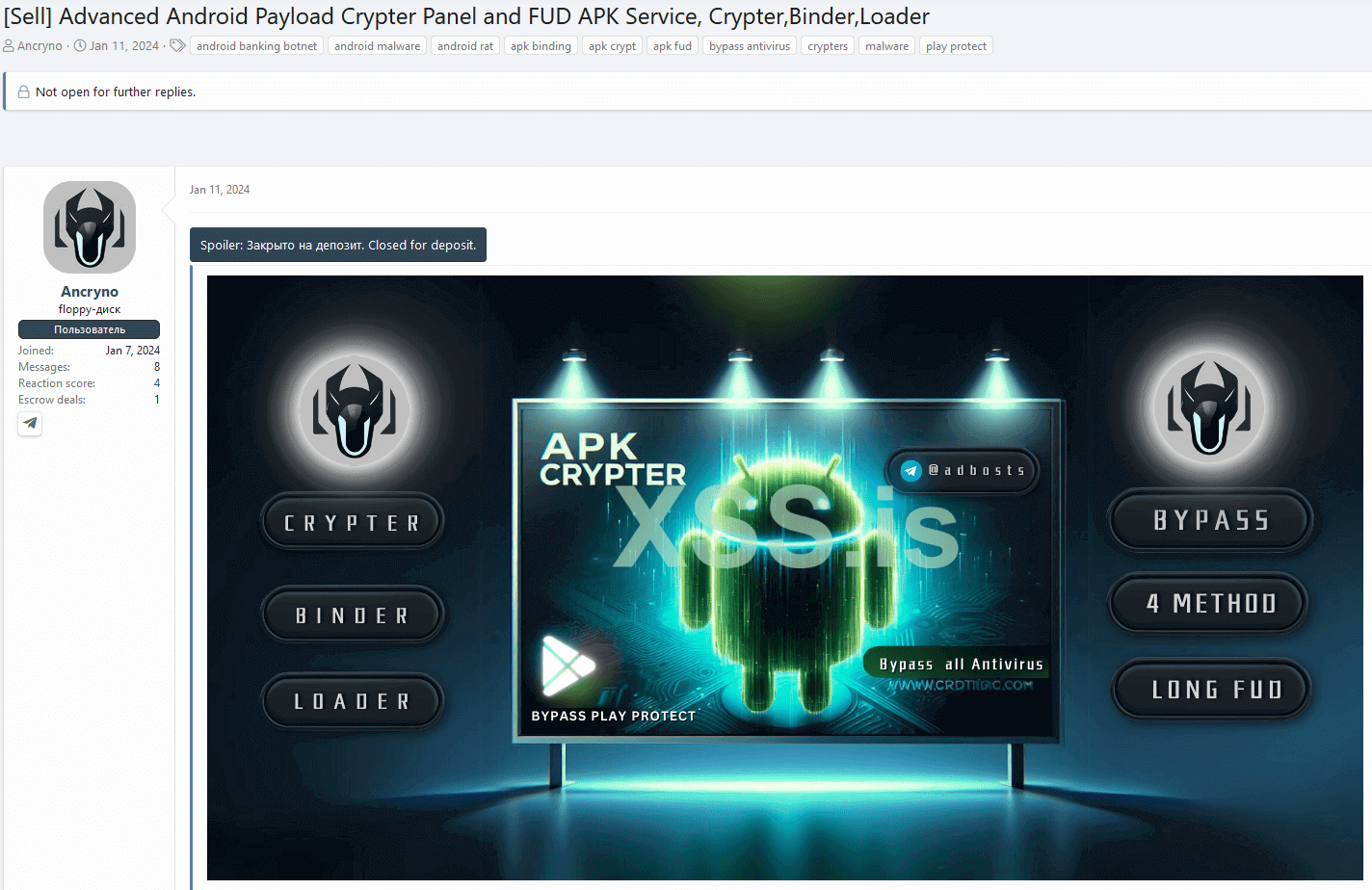
Report on Vulnerability
Unveiled on June 26th, 2024, the EvilVideo vulnerability led to Telegram being informed as per our coordinated disclosure policy. Despite no initial response, Telegram acknowledged the issue on July 4th and promptly initiated an investigation. They rectified the vulnerability by releasing version 10.14.5 on July 11th, followed by an email notification to us.
The flaw impacted all versions of Telegram for Android up to 10.14.4 but has been remedied in version 10.14.5. As verified, the multimedia preview in chats now accurately identifies the shared file as an application (Refer Figure 9) instead of a video.

Summary
We happened upon a zero-day exploit for Telegram’s Android version on a clandestine forum. This vulnerability facilitated the transmission of deceptive payloads disguised as multimedia files across Telegram chats. Should a user attempt to playback the supposed video, they were prompted to install an external app, actually installing the malevolent payload. Fortunately, following our disclosure to Telegram, this vulnerability was rectified by July 11th, 2024.
Any queries concerning our publications on WeLiveSecurity can be directed to threatintel@eset.comESET Research also offers exclusive APT intelligence reports and data feeds. For inquiries on this service, access the ESET Threat Intelligence page.
Indicators of Compromise (IoCs)
To view a detailed list of Indicators of Compromise (IoCs) and samples, please visit our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinityhackscharan. |
Administrator Beam Cable System |
2024‑07‑16 |
C&C server of EvilVideo payload. |
MITRE ATT&CK Tactics
The MITRE ATT&CK mobile techniques table has been generated using version 15 of the framework.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Exploitation for Initial Access |
The malevolent EvilVideo vulnerability can be adopted by Android malware for initial device access. |
|
|
Execution |
Exploitation for Client Execution |
The EvilVideo vulnerability deceives users into installing a malicious app that masquerades as a multimedia file. |









