Scams
Your humble contact number holds more value than you might realize. Below is how it could end up in the hands of wrongdoers – and ways to safeguard it from falling into the grasp of scammers.
15 Jul 2024
•
,
7 min. read

What would be among the simplest methods to defraud an individual – without revealing one’s identity?
Could it entail acquiring their credit card data, potentially through digital skimming or hacking into a database containing sensitive personal information? Although effective, these tactics might demand significant resources and technical expertise.
What about unlawfully obtaining payment information through counterfeit websites? This could be a possibility, but impersonating authentic websites (along with email addresses to “spread the word”) may not be feasible for everyone. The likelihood is high that such strategies will be detected promptly by the security-conscious or impeded by security measures.
Instead, malicious entities are opting for scalable operations that lean on advanced social engineering techniques and involve minimal costs. By utilizing voice phishing (referred to as vishing) and message scams (smishing), these operations have evolved into a fraudulent call-center industry valued at billions of dollars.
Initially, these schemes may not necessitate specialized or technical skills. Furthermore, an individual (often a victim of human trafficking) can ensnare numerous unsuspecting targets concurrently in various types of fraud. These frequently include pig butchering, cryptocurrency schemes, romance scams, and tech support fraud, each weaving a captivating narrative and exploiting fundamental aspects of human nature.
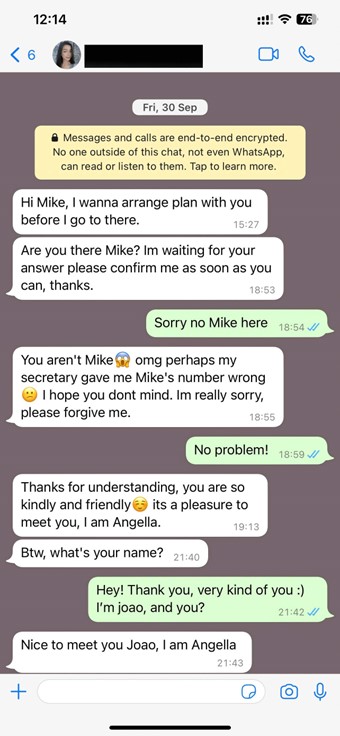
Hey there! Is anyone listening?
Picture receiving a call from what seems to be your bank informing you that your account has been compromised. To safeguard your funds, they insist that you disclose sensitive information. The urgency in the voice of the supposed bank “representative” could tempt you to reveal your confidential data. However, this individual might not be affiliated with your bank – or may not even exist at all. It could just be a fabricated voice that sounds entirely natural.
This scenario is not uncommon, and cautionary anecdotes from recent times are abundant. In 2019, a CEO fell victim to a nearly US$250,000 scam using a convincing voice deepfake of their parent company’s leader. Likewise, a finance professional was deceived through a deepfake video call in 2024, resulting in a US$25 million loss for their company.
Artificial Intelligence, the catalyst
With modern AI capabilities in voice cloning and translation, vishing and smishing have become increasingly uncomplicated. In fact, ESET Global Cybersecurity Advisor Jake Moore showcased how effortlessly anyone can craft a convincing deepfake representation of another person – even someone familiar to you. Seeing and hearing no longer guarantee authenticity.
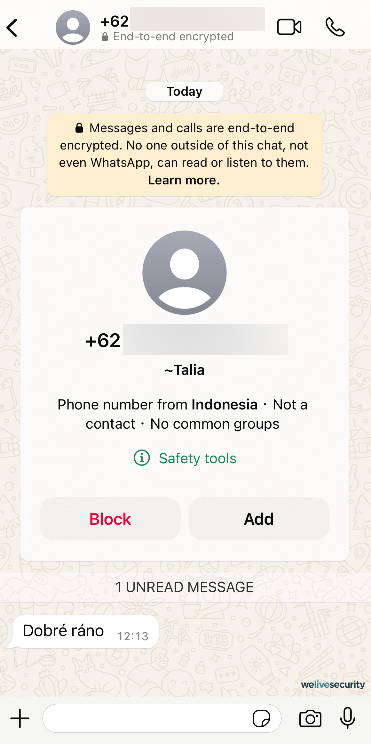
AI is diminishing the entry barrier for emerging adversaries, serving as a versatile instrument for data collection, task automation, and global outreach. Consequently, the utilization of AI-generated voices and text in phishing attempts will likely grow more prevalent.
In this context, a recent study by Enea highlighted a 1,265% surge in phishing incidents post the ChatGPT launch in November 2022 and emphasized the potential role of extensive language models in fueling such malicious endeavors.
Can we have your name and number?
As indicated by research conducted by Consumer Reports in 2022, individuals are increasingly cautious about their privacy. Around 75% of survey participants expressed some degree of concern regarding the privacy of their online-collected data, which may encompass contact details, seen as a valuable asset for identification and marketing purposes.
Now that we’re well beyond the era of the Yellow Pages, how exactly does the association between contact details and marketing operate?
Consider this illustrative scenario: a baseball enthusiast placedtickets within a designated application’s shopping cart but failed to finalize the transaction. Following the closure of the application, he promptly received a telephone call extending a discount offer on the tickets. Naturally, he was bewildered as he could not recall furnishing his telephone number to the application. How did the application acquire his number then?
The explanation lies in tracking. Certain trackers have the capability to gather specific details from a webpage. Therefore, when you input your phone number into a form, a tracker can identify and retain it to generate what is commonly referred to as tailored content and user experience. There exists a complete business framework known as “data brokering,” and the unfortunate revelation is that a breach is not a requisite for the data to be made public.
Surveillance, data dealers, and breaches
Data dealers hoover up your personal particulars from publicly accessible sources (such as government licenses/registrations), commercial sources (like business associates such as credit card companies or retailers), and also by monitoring your online behaviors (interactions on social media, ad clicks, etc.), prior to vending your information to others.
Nevertheless, you may be pondering: how do scammers acquire the phone numbers of other individuals?
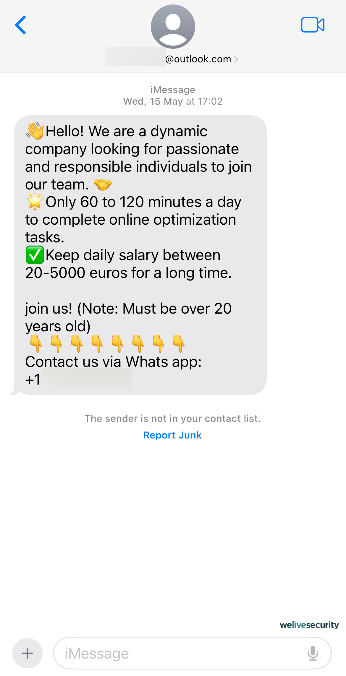
The greater the number of companies, websites, and applications with which you share your personal data, the more intricate your personal “marketing profile” becomes. Consequently, this augments your susceptibility to data breaches, since data brokers themselves might encounter security occurrences. A data broker could potentially vend your details to others, possibly encompassing nefarious entities.
However, data brokers, or breaches impacting them, are not the singular sources of phone numbers for scammers. Here are several alternate methods by which malefactors may obtain your telephone number:
- Public sources: Social media platforms or virtual job markets might showcase your phone number as a mode of connection. In the event that your privacy configurations are not set up correctly or you are uninformed of the consequences of disclosing your phone number in your social media profile, your number could potentially be accessed by anyone, including an AI web scraper.
- Pilfered accounts: Various online services necessitate your phone number, either to authenticate your identity, place an order, or serve as an authentication element. If your accounts are compromised due to feeble passwords or if one of your online service providers undergoes a data breach, your number could easily be exposed as well.
- Robocallers: Automated calling systems dial random numbers, and upon answering the call, you could potentially be singled out by a scam operation. Occasionally, these robocallers call solely to ascertain that the number is active for inclusion in a list of targets.
- Correspondence: Inspect any recent deliveries – typically, these display your address visibly on the package or letter, but occasionally, they may also feature your email or phone number. Suppose someone pilfered from one of your deliveries or combed through your discarded items? Given that data breaches typically entail similar information, this can be perilous and grounds for further exploitation.








