Fraudulent Schemes
Your humble phone number possesses more worth than you might realize. Here is how it could slip into the incorrect hands – and how you can contribute to keeping it out of reach from deceitful individuals.
15 Jul 2024
•
,
7 min. read

What could potentially be among the simplest methods to deceive someone out of their funds – discreetly, naturally?
Could it involve appropriating their credit card details, possibly through digital skimming or following breaching a database of sensitive personal data? Although effective, these approaches might necessitate ample resources and demand some technical expertise.
What about seizing payment information via fraudulent websites? This approach could indeed match the criteria, but imitating legitimate websites (and email addresses to “propagate the information”) may not suit everyone. Furthermore, the likelihood is high that such maneuvers will be detected promptly by the security-aware or hindered by security measures.
Instead, malevolent actors are shifting towards highly scalable activities that depend on sophisticated social manipulation methods and incur minimal costs. By employing voice phishing (also known as vishing) and message fraud (smishing), these undertakings have evolved into a deceptive call-center sector worth billions of dollars.
To begin with, these deceits might not demand a wealth of specialized or technical competencies. Moreover, a solitary individual (often a victim of human trafficking) can, simultaneously, entrap multiple unknowing targets in various types of deceit. These often encompass pig butchering, cryptocurrency schemes, romance deceits, and tech support forgery, each of which fabricates a compelling narrative and exploits certain aspects of our humanity.
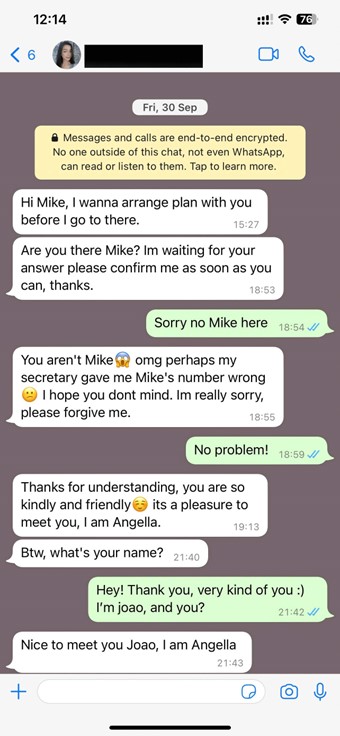
Hey there? Is this device operational?
Picture receiving a call purportedly from your bank informing you that your account has been compromised and to safeguard your funds, you are required to disclose your sensitive details. The urgency in the “employee” of the bank’s voice might be sufficient to convince you to divulge your sensitive information. However, this individual might not be affiliated with your bank – or may not even be real. It might just be a fabricated voice, yet sound completely authentic.
This scenario is not uncommon, and tales of caution from recent times are plentiful. In 2019, a CEO fell victim to a nearly US$250,000 scam orchestrated by a credible voice deepfake impersonating their parent company’s executive. Similarly, a financial professional was deceived via a deepfake video call in 2024, resulting in a loss of US$25 million for their company.
AI, the catalyst
With contemporary AI voice cloning and translation capabilities, vishing and smishing have grown more accessible than ever before. Indeed, ESET’s Global Cybersecurity Advisor Jake Moore showcased how effortlessly anyone can create a convincing deepfake representation of someone else – even someone familiar to you. Seeing and hearing are no longer synonymous with believing.
AI is diminishing the entry barrier for emerging adversaries, functioning as a multifaceted instrument to harvest data, streamline mundane activities, and amplify their global influence. Consequently, phishing employing AI-generated voices and text is likely to become more prevalent.
In line with this, a recent study by Enea pinpointed a 1,265% surge in phishing scams following the introduction of ChatGPT in November 2022 and emphasized the potential of expansive language models in driving such malevolent endeavors.
What moniker do you go by, what’s your contact information?
As revealed by Consumer Reports’ 2022 study, individuals are exhibiting greater privacy awareness compared to previous years. About 75% of the survey participants expressed at least some level of concern regarding the privacy of their online-collected data, which may encompass phone numbers, making them a valuable asset for both identification and promotional endeavors.
Now that we have surpassed the era of the Yellow Pages, how does this correlation between phone numbers and marketing function?
Contemplate this illustrative scenario: a baseball enthusiast initiatedtickets within a dedicated application’s checkout but failed to finalize the transaction. Subsequently, right after shutting down the application, he was contacted via phone with an offer of a reduced price on the tickets. Naturally, he was puzzled as he didn’t recall providing his phone number to the application. How did it acquire his number, then?
The explanation lies in tracking. Certain trackers are capable of gathering specific details from a webpage, so upon inputting their phone number in a form, a tracker could identify and retain it to generate what is commonly known as personalized content and experience. A complete business model exists, referred to as “data brokering”, and the unfortunate news is that a breach isn’t necessary for the data to become public.
Tracking, data intermediaries, and breaches
Data intermediaries extract your personal details from publicly accessible sources (such as government licenses/registrations), commercial sources (business partners like credit card providers or stores), as well as by monitoring your online activities (engagements on social media, ad clicks, etc.), before vending your information to others.
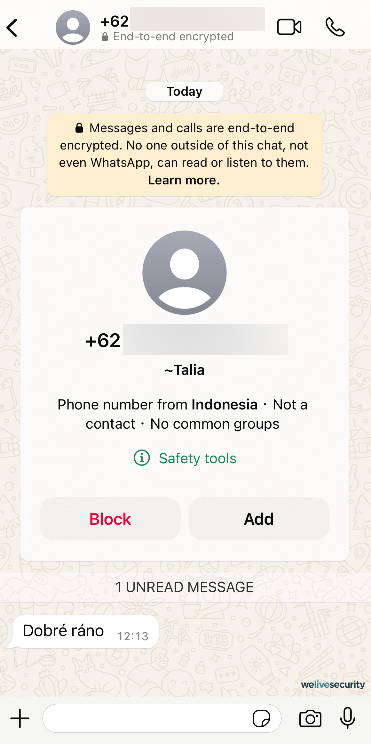
Nevertheless, you might be wondering: how can fraudsters come into possession of other individuals’ phone numbers?
The more companies, websites, and applications you disclose your personal information to, the more thorough your personal “marketing profile” becomes. This, in turn, heightens your vulnerability to data breaches, since data intermediaries themselves can encounter security incidents. A data intermediary might also vend your details to others, potentially including nefarious entities.
However, data intermediaries, or breaches that impact them, are not the lone source of phone numbers for scammers. Here are some additional ways in which criminals can obtain your phone number:
- Public sources: Social media platforms or online job markets could display your phone number for networking purposes. If your privacy settings are inadequately configured or you are unaware of the ramifications of disclosing your phone number on your social media profile, your number might be visible to anyone, even an AI web scraper.
- Compromised accounts: Various online services mandate your phone number, whether to verify your identity, place an order, or serve as an authentication factor. If your accounts are compromised due to weak passwords or if one of your online providers suffers a data breach, your number could easily be leaked.
- Robocallers: Automated dialers contact random numbers, and upon answering the call, you may be targeted by a scam. At times, these robocallers call merely to confirm the number’s activity, enabling its addition to a list of targets.
- Correspondence: Inspect any recent deliveries – these typically showcase your address on the package, but occasionally, they may also reveal your email or phone number. What if someone pilfered one of your packages or perused through your recycling pile? Given that data breaches commonly encompass identical details, this can pose severe risks and serve as a basis for further exploitation.
AT&T recently disclosed a massive data breach revealing that call and text message records of millions of customers from mid-to-late 2022 were exposed. Nearly all customers of the company and individuals utilizing the cell network had their numbers, call durations, and call interactions count divulged. Although call and text contents purportedly did not form part of the breached data, customer names and numbers are easily linkable, as noted by CNN.
Reportedly, the fault lies with a third-party cloud platform that was infiltrated by a malicious actor. Interestingly, this same platform has experienced several instances of substantial leaks associated with it in recent years.
Securing your phone number
Hence, how can you safeguard yourself and your number? Here are a few recommendations:
- Stay alert to phishing attempts. Refrain from responding to unsolicited messages/calls from foreign numbers, avoid clicking on random links in your emails/messages, and bear in mind to stay composed and deliberate before reacting to what appears to be an urgent situation, as that’s how they ensnare you.
- Inquire with your service provider about their SIM security protocols. They might offer card locks to thwart SIM swapping, for instance, or supplementary account security layers to combat scams like call forwarding.
- Fortify your accounts with two-factor authentication, preferably utilizing specialized security keys, applications, or biometrics rather than SMS-based verification. The latter can be intercepted by malicious actors quite easily. Extend this practice to your service provider accounts as well.
- Exercise caution before furnishing your phone number to a website. While having it as an extra recovery option for your diverse apps may be handy, alternative methods like secondary emails/authenticators could present a more secure substitute.
- For online transactions, contemplate utilizing a pre-paid SIM card or a VoIP service instead of your regular phone number.
- Deploy a mobile security solution with call screening capabilities, and also ensure that third-party cookies in your web browser are obstructed, while exploring other privacy-enhancing tools and technologies.
In a domain increasingly reliant on digital record-keeping, it is improbable that your number won’t be retained by a third party somewhere. And as evidenced by the AT&T mishap, relying on the security measures of your own carrier proves to be somewhat problematic. Nevertheless, this doesn’t signify that you should live in a perpetual state of paranoia.
Conversely, it underscores the necessity of adhering to proper cyber hygiene and having an awareness of your online data. Vigilance remains paramount, particularly when contemplating the repercussions of this novel, AI-fortified (under)world.








