Fox Kitten: Iran Cyber Strike Enables Ransomware in the United States

An up-to-date cybersecurity warning jointly issued by the Federal Bureau of Investigation, the Cybersecurity and Infrastructure Protection Agency, and the Department of Defense Cyber Crime Center has brought to light new revelations about the notorious Iran-based hacker group identified as Fox Kitten.
The organization peddles the corporate entryways they acquire in the shadowy realms of cybercriminal markets and actively teams up with ransomware associates to aid in extorting victims. This malicious group has honed in on infiltrating entities in the U.S. and other foreign domains in the recent past.
The Identity of Fox Kitten
Fox Kitten — also recognized as Pioneer Kitten, UNC757, Parasite, Rubidium, and Lemon Sandworm — represents a perilous cyber threat that has been actively involved in cyberespionage endeavors since at least 2017.
As per the advisory, the FBI has linked this group with the Iranian government, underscoring their assistance in stealing vital technical information from various entities. While the threat actor has primarily targeted establishments in the Middle East like Israel and Azerbaijan, they have also set their sights on organizations in Australia, Finland, Ireland, France, Germany, Algeria, Turkey, the U.S., and potentially more.
The advisory showcases Fox Kitten engaging in a significant number of computer network breach attempts against American institutions since 2017. Their targets encompass educational institutions, municipal bodies, financial establishments, and healthcare facilities based in the U.S., with incidents as recent as August 2024.
Observations from the OT cybersecurity firm Dragos highlight the threat actor’s focus on entities related to Industrial Control Systems by leveraging vulnerabilities in Virtual Private Network appliances.
The advisory also divulges that the group exploits “Danesh Novin Sahand,” an Iranian company, possibly as a front IT entity for the malicious cyber actions of the group.
Beyond Cyberespionage
In 2020, a campaign named “Pay2Key,” orchestrated by Fox Kitten, showcased the group’s ability to pursue objectives beyond cyberespionage.
As reported by the Israeli cybersecurity firm ClearSky Cyber Security, ransomware attacks executed by the group targeted Israeli entities with previously unreported ransomware, although the attack campaign was likely aimed at creating fear and chaos within Israel. Data exfiltrated during the attacks was subsequently made public on a leak site referencing “Pay2Key, Israel cyberspace nightmare!” as detailed in the report.
Another study published by the cybersecurity company CrowdStrike in 2020 unveiled that the threat actor also advertised the sale of compromised network access on an underground forum, suggesting a move towards diversifying revenue sources alongside targeted intrusions in support of the Iranian government.
Partnership with Ransomware Partners
Upon gaining access to victim networks, Fox Kitten collaborates with select ransomware associates from the NoEscape, RansomHouse, and ALPHV/BlackCat factions. They offer comprehensive entry to ransomware affiliates in return for a portion of the ransom proceeds.
Aside from network access, Fox Kitten provides more than just a pathway into compromised networks, according to the FBI. The group actively cooperates with ransomware affiliates to encrypt victim networks and devise strategies for pressuring victims into paying ransoms. Despite this, they maintain secrecy regarding their Iranian origins to their ransomware network contacts.
The joint advisory reveals the group goes by the alias “Br0k3r” and utilized “xplfinder” in their communication channels in 2024.
In-Depth Technical Insights
Fox Kitten leverages the Shodan search engine to pinpoint IP addresses hosting devices susceptible to specific exploits such as Citrix Netscaler, F5 Big-IP, Pulse Secure/Ivanti VPNs, or PanOS firewalls.
Post-exploitation of vulnerabilities, the threat actor undertakes the following actions:
- Deploys webshells and captures login credentials before initiating malicious tasks to insert backdoor malware and further compromise the system.
- Utilizes stolen credentials to establish new accounts on victims’ networks with inconspicuous names like “IIS_Admin” or “sqladmin$.”
- Acquires admin credentials to access domain controllers and other components of the infrastructure, while also disabling existing security tools and antivirus software.
‘Br0k3r’ Continues Operations for Over a Year
The joint advisory supplies various indicators of compromise while listing the TOX identifiers for the alias “Br0k3r.” TOX serves as a peer-to-peer messaging platform designed for secure communication, utilizing unique keys for user identification.
The distinct TOX ID attributed to “Br0k3r” was previously exposed in 2023 by the SANS Institute as an Initial Access Broker peddling access to corporate networks globally, including nations like the U.S., Canada, China, the U.K., France, Italy, Norway, Spain, India, Taiwan, and Switzerland.
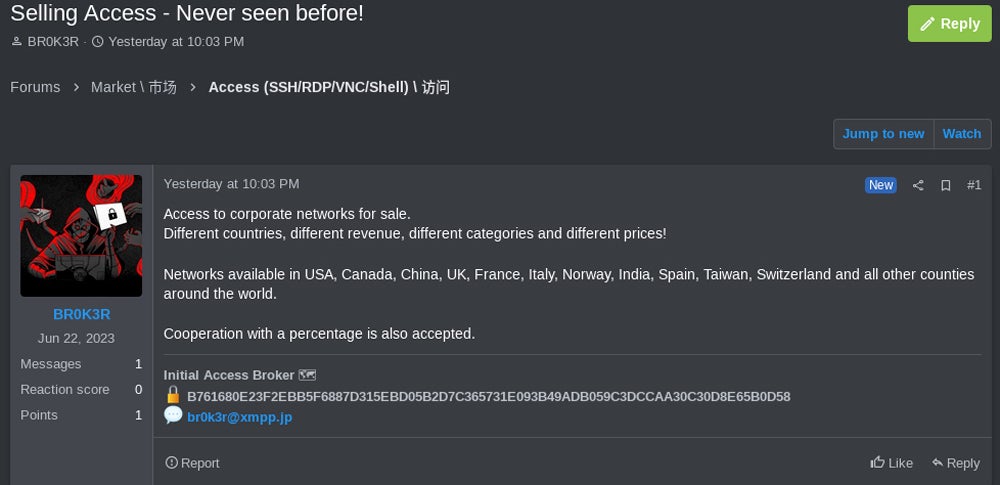
The focus on the United States by the threat actor comes as no surprise, given that it is the most ransomware-affected nation according to cybersecurity firm MalwareBytes.
Utilizing cybercriminal forums
An exclusive Tor-hosted website was presented by the threat actor for advertising their access on various cybercriminal forums.
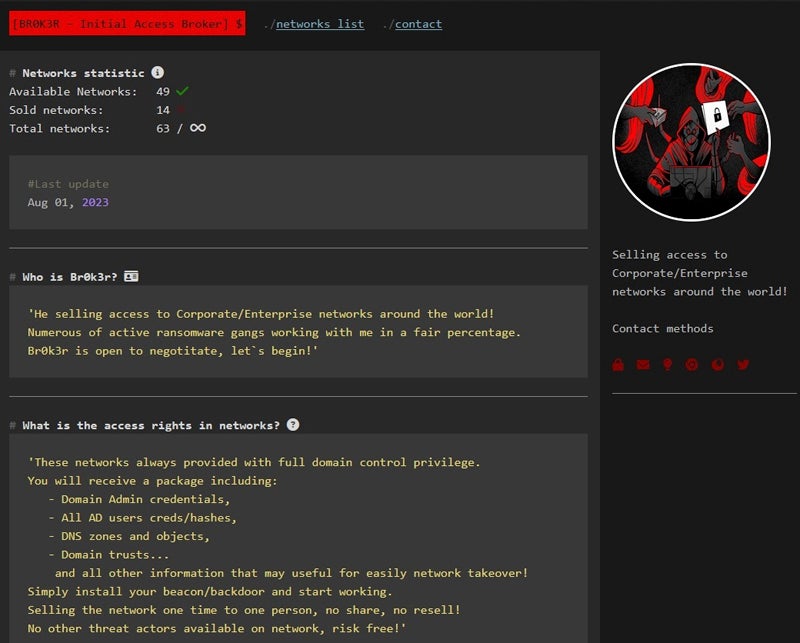
The initial iteration of Br0k3r’s website reveals that every purchase includes complete domain control, which comprises domain administrator credentials, Active Directory user credentials, DNS zones and objects, and Windows Domain trusts.
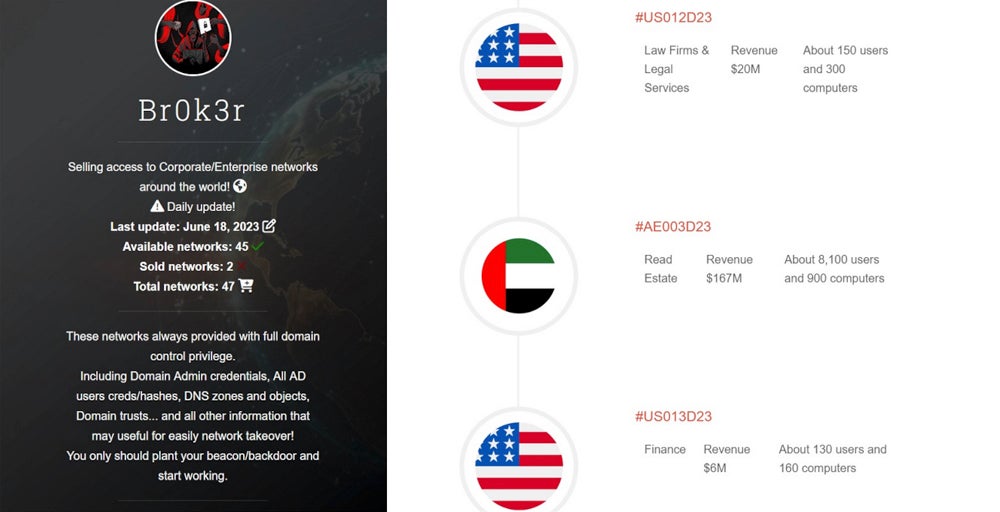
The subsequent version of the site introduced in August 2023 asserts, “Multiple active ransomware gangs collaborating with me at a fair rate.”
Safeguarding your enterprise from this risk
The initial attack method employed by Fox Kitten involves leveraging known vulnerabilities in various Internet-exposed devices, specifically corporate VPNs or firewall devices. To shield against this online menace, organizations should:
- Maintain and update VPN and firewall devices to prevent falling prey to such vulnerabilities.
- Keep all operating systems updated and patched, and ensure software is current and patched.
- Supervise VPN access to identify any suspicious connections or connection attempts. Moreover, implement filters on the VPN devices so that employees can only connect from their regular internet connection as needed.
- Review and scrutinize log entries. Any detection of a compromise indicator outlined in the collaborative report must trigger an immediate probe.
- Install security solutions on all endpoints and servers to identify unusual behavior.
Lastly, the FBI and the CISA discourage payment of ransom as it does not guarantee file recovery, and such payments may finance additional criminal activities.
Disclaimer: I am associated with Trend Micro, but the opinions expressed in this post are personal.





