01 July 2024
In my previous article on The Status of Data Breaches, I received an abundance of responses. The feedback was largely empathetic towards the challenges faced while managing HIBP. The post primarily expressed frustration: the lack of transparency, uncooperative organizations, downplaying of breaches, and the exacerbation caused by breach victims targeting the affected companies. However, another perspective has been circling my mind, depicted in the image below:

Overseeing HIBP has evolved into a continuous juggling act involving three main entities: cybercriminals, afflicted corporations, and law enforcement. Let me elaborate:
Cybercriminals
The majority of data breaches originate with cybercriminals illicitly infiltrating protected systems and pilfering data. This is a broad characterization, encompassing activities such as exploiting software vulnerabilities, downloading exposed database backups, phishing administrator credentials, and acquiring data. Occasionally, these cybercriminals reach out to me.
Navigating this situation is challenging as I must weigh the potentially conflicting objectives of notifying impacted HIBP subscribers while refraining from encouraging the unethical incentives of probable criminals. There are instances where the course of action is clear: if an individual reports exposed data or a security vulnerability, the recommendation is to inform the involved company rather than escalate it into a data breach. However, if the data has already been compromised, it unequivocally constitutes a breach, which inevitably impacts a portion of my subscribers. Initiating conversations with the individuals responsible for the breach can be awkward.
Various circumstances can further complicate matters, such as if the cybercriminal attempts to extort money from the company, trades the data on the breach market, or maintains access to the corporate system. Engaging in discussions with someone in such a position requires tact, all the while considering the possibility of their eventual arrest. Every word I convey is underpinned by this assumption. Moreover, these dialogues must be treated with confidentiality as individuals reaching out expect discretion, built on the trust I have cultivated over more than ten years of operating this service. Consequently, I often find myself facilitating discussions between the aforementioned parties, exchanging contact details or relaying messages with mutual consent.
Interactions of this nature can become convoluted: the cybercriminal (often distrusting of large corporations) strives to highlight an issue, but is communicating with a party naturally wary of unidentified individuals who accessed their data! Simultaneously, law enforcement focuses on the cybercriminal due to their obligations, while respecting the role I fulfill and the confidential nature of data sharing with me. Law enforcement is also frequently engaged by the afflicted corporation, leading to a scenario where all entities communicate with each other while I navigate the middle ground.
I share this not to aggrandize my role but to underscore the delicate equilibrium required when managing many data breaches. These intricacies are further compounded by the observations from the preceding article concerning the lack of urgency, among other issues.
Affected Organizations
I opt for this term as it is effortless for individuals to castigate companies experiencing data breaches. Depending on the circumstances, some culpability may be justified, but it is crucial to recognize that breached companies are often the targets of deliberate, malevolent criminal operations. When I mention “companies,” I refer to individuals striving to fulfill their roles to the best of their ability and who, during an incident response phase, endure challenging times in their careers. I have sensed the distress in their voices and seen the pressure etched on their faces during prior occasions, as I endeavor to ensure the human aspect is not overlooked amidst the clamor of displeased customers.
The interaction between afflicted corporations and cybercriminals is notably delicate. While rightfully aggrieved, these companies tread carefully, aiming to glean insights into the breach (the method through which the data was obtained is often unknown initially), while contending with exorbitant demands and maintaining composure. It is remarkably easy for individuals accustomed to anonymity to abruptly vanish, leaving the company in a quandary. This balancing act is evident in numerous communications later disclosed by cybercriminals, typically after failing to secure the expected ransom; the corporations appear exceedingly polite… masking a fervent desire to see the perpetrator prosecuted!
The involvement of law enforcement, or more broadly, the engagement with governmental authorities, introduces an intriguing dynamic. Beyond addressing the illicit activities of cybercriminals, the affected corporations have legal obligations. This responsibility varies significantly based on jurisdiction and regulatory frameworks, potentially necessitating reporting the breach to the relevant government body. There may be a need to report to multiple governmental entities at the state level, contingent on their location. Furthermore, questions regarding their culpability arise, particularly whether their actions (or inaction) pre-and post-breach could lead to punitive measures. In the preceding article, I included a reference to “covering their bases,” which not only pertains to shielding against customer or shareholder backlash but increasingly shields against substantial corporate fines.
From past encounters, I gather that corporations share a complex relationship with law enforcement. While desiring support in combatting criminals, they tread cautiously about revelations that could potentially contribute to subsequent penalties. Consider the delicate balancing act when an affected corporation suspects that oversights on their part led to the breach and approaches law enforcement for assistance: “How do you think the breach occurred? Um…”
As reiterated throughout this discussion: “delicate”.
Law Enforcement
Among the trio, law enforcement emerges as the most multifaceted participant, engaging reciprocally with each entity in diverse ways.
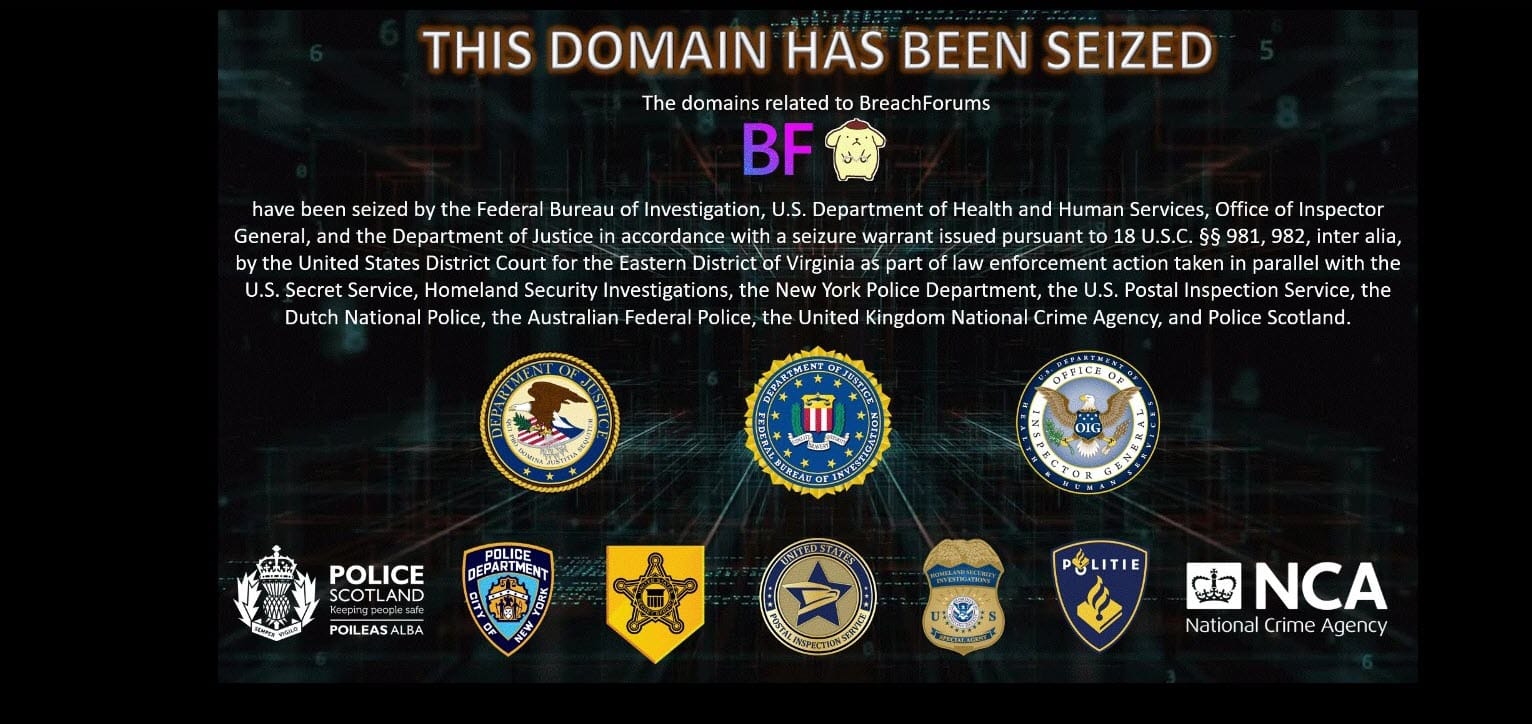
Ways to operate. It is evident that they are present in order to apprehend wrongdoers, which clearly includes hackers in their scope. I have frequently made mention of “the FBI and their associates” or similar phrases that highlight the collaborative nature of international law enforcement endeavors, as often seen through the issuance of takedown notices related to cybercrime initiatives:
The hackers themselves are often more than willing to interact with law enforcement as well. Sometimes for purposes of provocation, and at other times to directly target, frequently at a highly personalized level by calling out specific agents. It must be noted that the term “hacker” covers a wide spectrum, with its extreme end involving outright criminal activities aimed at causing harm for personal financial gain. At the opposite end of this spectrum lies a realm of much more nuanced nature, where individuals labeled with this term may not have malicious intentions, but rather express sentiments like: “I stumbled upon something, could you assist me in reporting it to the authorities”.
The interaction between law enforcement and businesses that are victims usually commences when the latter reports an incident. This is a common occurrence, often reflected in statements of disclosure like “we have informed the authorities,” which is a natural sequence following a criminal act. It’s not just about the hacking incident itself; it often involves additional criminal elements such as ransom demands, which requires further referrals to the authorities. Conversely, law enforcement frequently detects signs of compromise early on, even before the business victim becomes aware, enabling direct communication. Increasingly, we witness governmental organizations issuing broader cybersecurity recommendations, such as the consistent alerts provided by the Australian Signals Directorate.
I frequently find myself taking on various roles with law enforcement agencies. For instance, establishing a conduit for the FBI to integrate breached passwords, aiding the Estonian Central Criminal Police by enabling searchability of data impacting their citizens, spending time assisting the Dutch police with victim notifications, and even providing testimony before US Congress. Moreover, supporting thirty-six national CERTs worldwide with unrestricted access to their federal domain exposures in HIBP. Many of these agencies also naturally take an interest in individuals who reach out to me, particularly from the first category mentioned earlier. Despite that, I have always found law enforcement to be respectful of the trust with which hackers share information with me; they recognize the significance of the trust I previously mentioned and its role in my activities.
Summary
A decade later, I continue to find this realm intriguing, as I navigate through the interactions of these three entities, sometimes positioned on the periphery and occasionally right in the center. It is an environment that is both unpredictable and captivating, filled with excitement and stress, and I trust you found this exploration engaging 🙂