
An up-to-date study from Palo Alto Networks’s Unit 42 reveals the consistent and developing risk of DNS interception, a covert strategy malevolent actors employ to divert internet traffic. By utilizing passive DNS examination, the cybersecurity firm also showcased real-life instances of recent DNS interception assaults — emphasizing the necessity of combating this concealed peril.
Understanding DNS interception
DNS interception entails altering the replies from targeted DNS servers, steering users towards attacker-corralled servers rather than the genuine ones they aim to visit.
Various methods can be utilized for DNS interception:
- Seizing authority of the domain owner’s account, granting access to DNS server configurations: In this circumstance, the assailant holds valid user credentials with the power to directly modify the DNS server setup. The attacker might also possess legitimate credentials for the domain registrar or DNS service provider, enabling them to alter the configuration.
- DNS cache pollution: The offender impersonates a DNS nameserver and produces a falsified response, causing users to encounter attacker-controlled material instead of the authentic one.
- Man-in-the-Middle attack: The malevolent actor intercepts the user’s DNS queries and furnishes results that steer the victim towards the attacker’s content. This scheme only functions if the attacker is in command of a system implicated in the DNS query/answer process.
- Altering DNS-linked system files, like the host file in Microsoft Windows systems. If the attacker can access that local file, they can redirect the user towards attacker-controlled content.
Offenders typically exercise DNS interception to redirect users to phishing websites that resemble the intended sites or to infect users with malicious software.
Spotting DNS interception through passive DNS
The Unit 42 report delineated a technique to identify DNS interception using passive DNS scrutiny.
What is passive DNS?
Passive DNS denotes petabytes of historical DNS queries. Besides the domain name and DNS record type, passive DNS logs typically include a “first seen” and “last seen” timestamp. These logs enable users to track the IP addresses a domain has directed users to over time.
For an entry to materialize in passive DNS, it must be queried by a system whose DNS inquiries are chronicled by passive DNS systems. Hence, the most comprehensive passive DNS data usually emerges from providers with significant query volumes, such as ISPs or enterprises with extensive customer bases. Subscribing to a passive DNS provider is frequently recommended, as they amass more DNS queries than the average company, providing a more extensive perspective than local DNS queries alone.
SEE: All You Need to Grasp about the Malvertising Cybersecurity Menace (TechRepublic Premium)
Discerning DNS interception
Palo Alto Network’s system for uncovering DNS interception initiates by identifying never-before-seen DNS records, as perpetrators commonly produce new records to steer users. Domain names that have never been seen before are excluded from detection due to insufficient historical data. Bogus records are also eradicated at this stage.
The DNS records are subsequently scrutinized using passive DNS alongside geolocation information founded on 74 attributes. As per the report, “certain attributes contrast the historical utilization of the new IP address to the old IP address of the domain name in the new record.” The purpose is to uncover irregularities that could indicate a DNS interception operation. A machine-learning model subsequently supplies a likelihood score based on the evaluation.
WHOIS records are examined as well to deter a domain from being re-registered, as that generally results in a total IP address alteration that might be identified as DNS interception.
Lastly, active navigations are executed on the domains’ IP addresses and HTTPS certificates. Identical outcomes denote false positives and can thus be omitted from DNS interception operations.
DNS interception data
Between March 27 to Sept. 21, 2024, analysts evaluated 29 billion new records, with 6,729 marked as DNS interception. This led to an average of 38 DNS interception records daily.
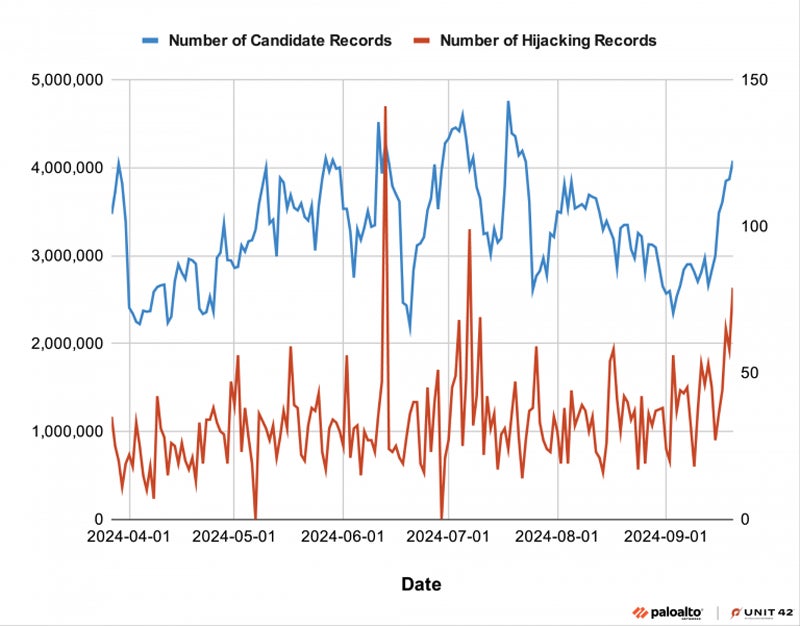
Unit 42 has indicated that crooks have hijacked domains to host phishing material, vandalize websites, or distribute unauthorized content.
DNS interception: Real-world instances
Unit 42 has documented numerous instances of DNS interception in the wild, primarily for illicit activities. Nonetheless, DNS interception could also be utilized for cyber espionage.
Hungarian political party links to phishing
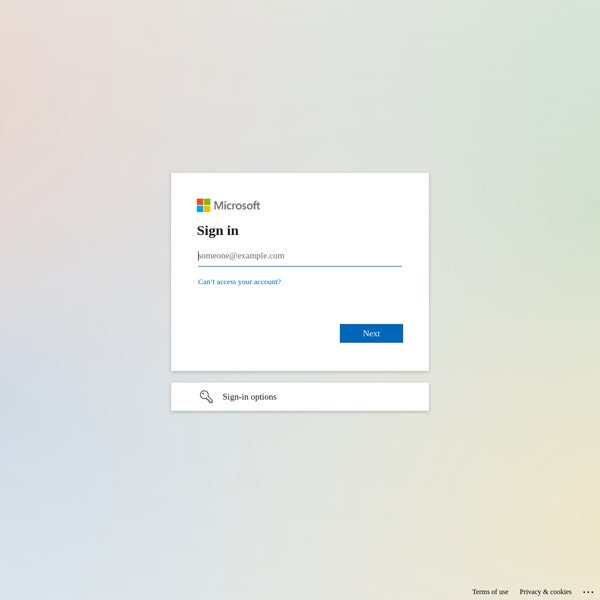
One of the most renowned political opposition factions to the Hungarian government, the Democratic Coalition (DK), has been accommodated on the same network of IP addresses in Slovakia since 2017. In January 2024, researchers identified a modification in the DK’s website, which abruptly resolved to a new German IP address, directing users to a Microsoft login page instead of the party’s conventional news page.
Leading US corporation targeted
During May of 2024, two domains belonging to a prominent U.S. utility administration corporation were compromised. The FTP facility, which has been linked to the same IP address since 2014, underwent an abrupt alteration. The DNS nameserver was infiltrated through the use of the adversary-controlled ns1.csit-host.com.
It was found that the attackers previously used the same nameservers to seize control of other websites in the years 2017 and 2023. The core objective of the operation was to display a defaced page affiliated with an activist organization.
How to shield corporations from this danger
To fortify against these dangers, the report proposed that enterprises should:
- Implement dual-factor authentication for entry into their DNS registrar accounts. Formulating a whitelist of authorized IP addresses for accessing DNS configurations is also recommended.
- Utilize a DNS registrar that endorses DNSSEC. This mechanism enhances security by digitally signing DNS communications, making it harder for malevolent actors to intercept and falsify data.
- Deploy networking utilities that cross-check DNS query findings from third-party DNS servers — such as those offered by ISPs — with the DNS query findings acquired through the company’s habitual DNS server. Any inconsistency could imply a modification in DNS configurations, which may signify a DNS hijacking maneuver.
Furthermore, all devices, including routers, need to have the latest firmware, and all applications should be updated and patched to prevent exploitation through common vulnerabilities.
Declaration: I am employed by Trend Micro, yet the opinions expressed in this piece are solely mine.






