
A vital asset that cybersecurity experts across the globe depend on to detect, diminish and repair security flaws in software and hardware faces the risk of collapsing. The publicly funded, non-profit institution MITRE raised an alarm today that its agreement to manage the Common Vulnerabilities and Exposures (CVE) program — which typically receives annual funding from the Department of Homeland Security — will terminate on April 16.

A notice from MITRE vice president Yosry Barsoum regarding the discontinuation of funding for the CVE program on April 16, 2025.
Thousands of security vulnerabilities in software are discovered and reported annually, with these weaknesses eventually being assigned unique CVE tracking numbers (e.g., CVE-2024-43573, identifying a Microsoft Windows bug that was patched by Redmond last year).
There exist numerous organizations — referred to as CVE Numbering Authorities (CNAs) — that are authorized by MITRE to assign these CVE numbers to newly reported vulnerabilities. Many of these CNAs are specific to countries and governments, or linked to individual software vendors or platforms for vulnerability disclosure (also known as bug bounty programs).
In essence, MITRE serves as a crucial and widely-used hub for consolidating and standardizing information on software vulnerabilities. This ensures that the data it provides is integrated into a variety of cybersecurity tools and services that aid organizations in identifying and remediating security weaknesses — ideally before they are exploited by malware or malicious actors.
“The CVE listings offer a standardized approach to describing the seriousness of a flaw, along with a centralized repository detailing which product versions are affected and require updating,” stated Matt Tait, chief operating officer of Corellium, a cyber defense company that offers phone-virtualization software for identifying security vulnerabilities.
In a communication dispatched today to the CVE board, MITRE’s Vice President Yosry Barsoum warned that as of April 16, 2025, “the existing contract for MITRE to develop, manage and upgrade CVE and several related programs will expire.”
“In the event of a service interruption, we foresee multiple repercussions for CVE, including the degradation of national vulnerability databases and alerts, tool providers, incident response operations, and various types of critical infrastructure,” Barsoum expressed.
MITRE informed KrebsOnSecurity that the CVE website, which catalogs vulnerabilities, will remain accessible after the funding ends, but new CVEs will not be added post April 16.
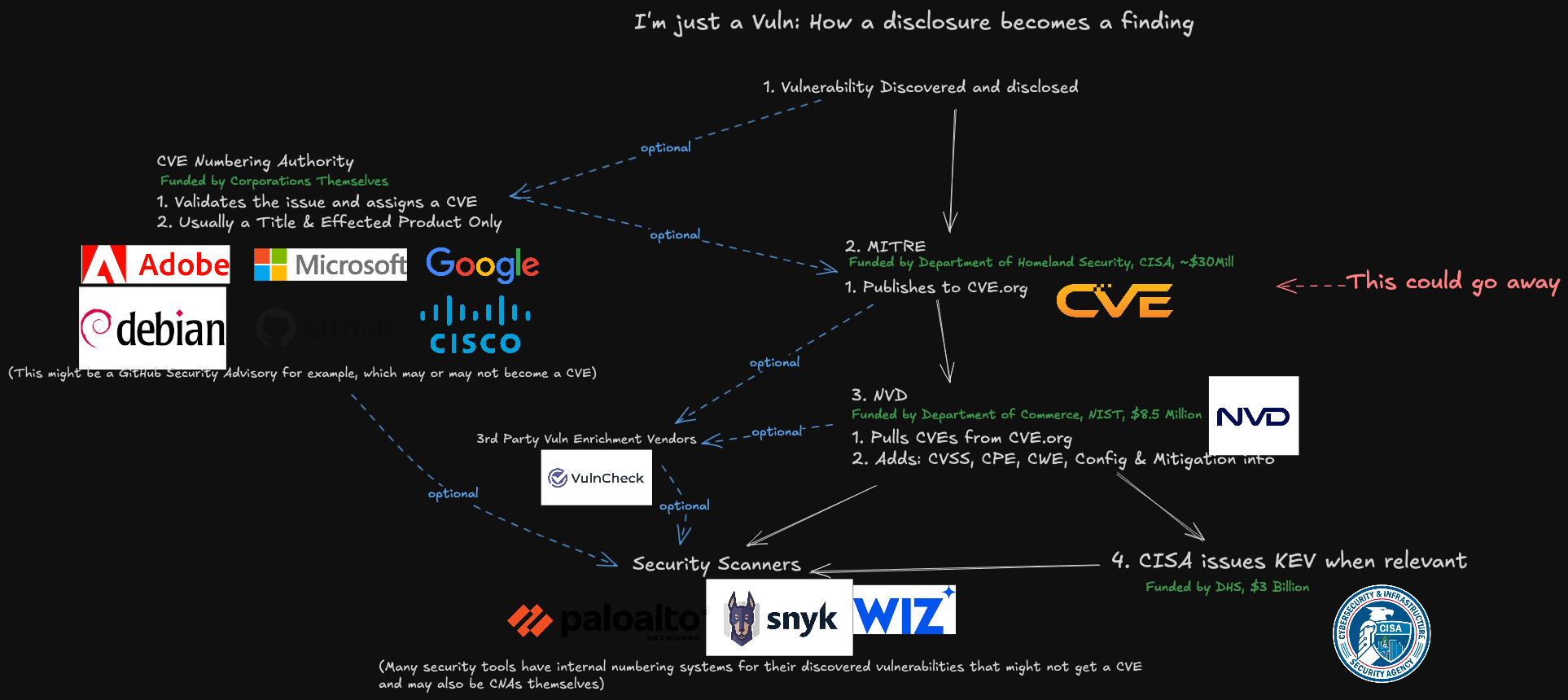
Illustration depicting the process by which a vulnerability is assigned a CVE, and how this information is utilized. Image: James Berthoty, Latio Tech, via LinkedIn.
DHS officials did not respond immediately to a request for comment. The program receives funding from DHS’s Cybersecurity & Infrastructure Security Agency (CISA), which is currently confronting significant budget reductions and staffing shortages under the Trump administration. The CVE contract listed on USAspending.gov indicates that approximately $40 million was allocated to the project last year.
Former CISA Director Jen Easterly likened the CVE program to the Dewey Decimal System, but for cybersecurity.
“It’s the worldwide index that helps everyone—security teams, software providers, researchers, governments—organize and discuss vulnerabilities using a common system of reference,” Easterly remarked in a post on LinkedIn. “Without it, individuals would be using diverse references or no reference at all, making it unclear if they are discussing the same issue, wasting time to identify problems, and enabling threat actors to exploit the confusion.”
John Hammond, chief security researcher at the managed security company Huntress, shared with Reuters that he uttered an expletive upon learning about the jeopardy to CVE’s funding, and losing the CVE program would equate to losing “the language and terminology we rely on to address cybersecurity issues.”
“I believe this is only going to create problems,” stated Hammond, who uploaded a video on Youtube to express concerns and alert others.
Multiple sources close to the situation informed KrebsOnSecurity that the CVE program’s budget has been left hanging until the final moments on previous occasions. Barsoum’s leaked letter carried a positive tone, expressing hope that the government is exerting “substantial efforts to uphold MITRE’s role in supporting the program.”
Tait highlighted that without the CVE program, risk managers within companies would need to vigilantly monitor numerous other sources for information on new vulnerabilities that could endanger the security of their IT systems. Consequently, there is a higher likelihood that software updates might be given incorrect priority, resulting in companies deploying vulnerable software for longer durations than they should, he noted.
“Hopefully a resolution will be reached, otherwise the list will swiftly become outdated and lose its utility,” he concluded.
Update, April 16, 11:00 a.m. ET: The CVE board disclosed the establishment of a non-profit organization named The CVE Foundation that will continue the program’s operations via a new, undisclosed funding mechanism and organizational structure.
“Since its establishment, the CVE Program has been operated as a U.S. government-funded initiative, managed and overseen through a contract,” stated the press release. “While this setup has facilitated the program’s expansion, it has also provoked longstanding concerns among CVE Board members about the sustainability and impartiality of a globally relied-upon resource being reliant on a single government sponsor.”
The foundation’s website, thecvefoundation.org, is less than a day old and currently only hosts the press release announcing its establishment. The announcement mentioned that the foundation would provide additional details regarding its structure and transition planning in the coming days.
Update, April 16, 4:26 p.m. ET: MITRE issued a statement today revealing that it “secured additional funding to maintain the programs’ functionality. We are grateful for the immense backing shown by the global cybersecurity community, industry, and government in the past 24 hours. The government is investing significant efforts to support MITRE’s role in the program, and MITRE remains dedicated to CVE and CWE as globally essential resources.”









