Businesses face significant challenges when it comes to security threats, which can result in various negative outcomes like customer data breaches or sensitive data loss. Many companies are now relying on endpoint detection and response (EDR) software to safeguard against these threats.
EXPLORE: Debunking 10 Cybersecurity Myths (TechRepublic Premium)
Among the leading EDR software options in the market are CrowdStrike and Trellix. Both tools excel at identifying and countering threats and vulnerabilities to ensure the security of your network and data. Explore the features offered by each solution and learn how to choose between these two EDR platforms.
Comparing Features of CrowdStrike and Trellix
CrowdStrike functions as a cloud-based EDR solution safeguarding endpoints against critical vulnerabilities like malware, phishing, ransomware, and DDoS attacks.
EXPLORE: McAfee vs Kaspersky: EDR Solutions Comparison (TechRepublic)
On the other hand, Trellix, emerging from the McAfee and FireEye merger in 2022, offers a cloud-based system that reduces alert noise by prioritizing threats to minimize workflow disruptions.
Below is a comparison of the features provided by both EDR tools:
| Malware and ransomware protection | ||
| Cloud-based | ||
| Option for local installation | ||
| Behavioral threat analysis | ||
| Employment of machine learning | ||
| Single-agent model | ||
| Starting price | ||
|
|
Examining Pricing for CrowdStrike and Trellix
Crowdstrike’s EDR solution can be obtained through the Falcon Enterprise and Falcon Elite subscription models. Here’s an overview of the pricing and included features for each CrowdStrike Falcon plan.
- Falcon Enterprise: $184.99 per device; features antivirus, EDR, XDR, and managed threat hunting.
- Falcon Elite: Request a quote from sales; includes EDR, XDR, integrated endpoint, identity protection, and threat-hunting.
Businesses can take advantage of a free trial for Falcon Enterprise before committing to a subscription.
EXPLORE: Carbon Black vs. CrowdStrike: A Comparison of EDR Software (TechRepublic)
As for Trellix, pricing information for its EDR solution is not publicly advertised. To learn more, view the Trellix EDR data sheet or request a product demo.
If you are considering Trellix, it’s recommended to reach out to their sales team to get detailed pricing information.
Comparing Features of CrowdStrike and Trellix
Threat Detection and Mitigation
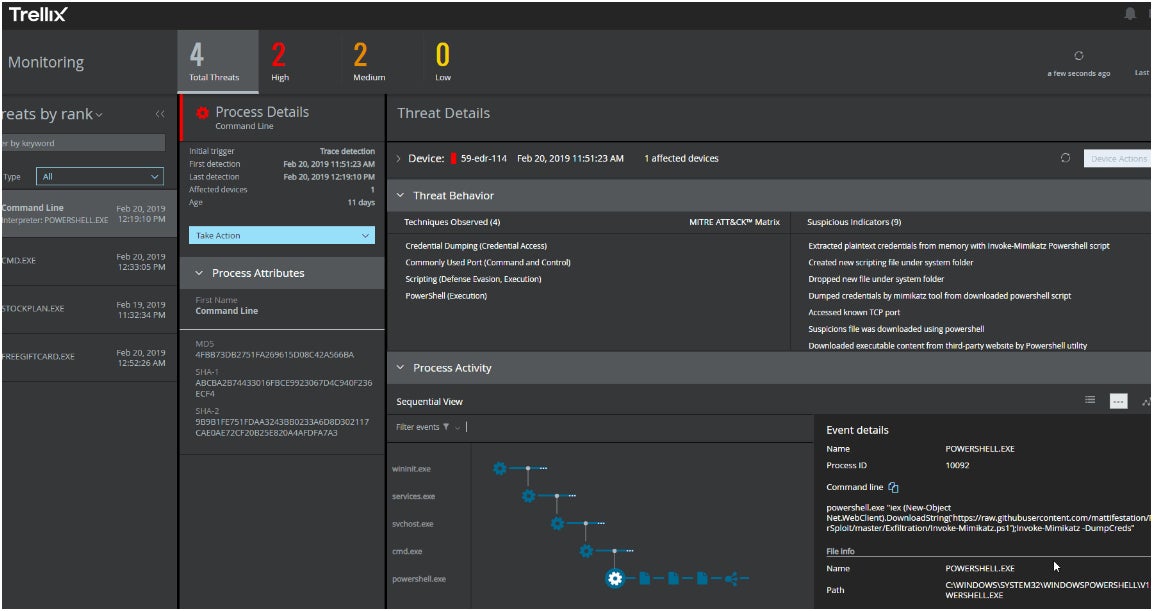
Trellix’s endpoint solution incorporates continuous data collection and various analytical engines during the detection phase to focus only on genuine threats and vulnerabilities, minimizing unnecessary alerts that could waste resources without enhancing security.
-

Dashboard of Trellix EDR. Image Source: Trellix
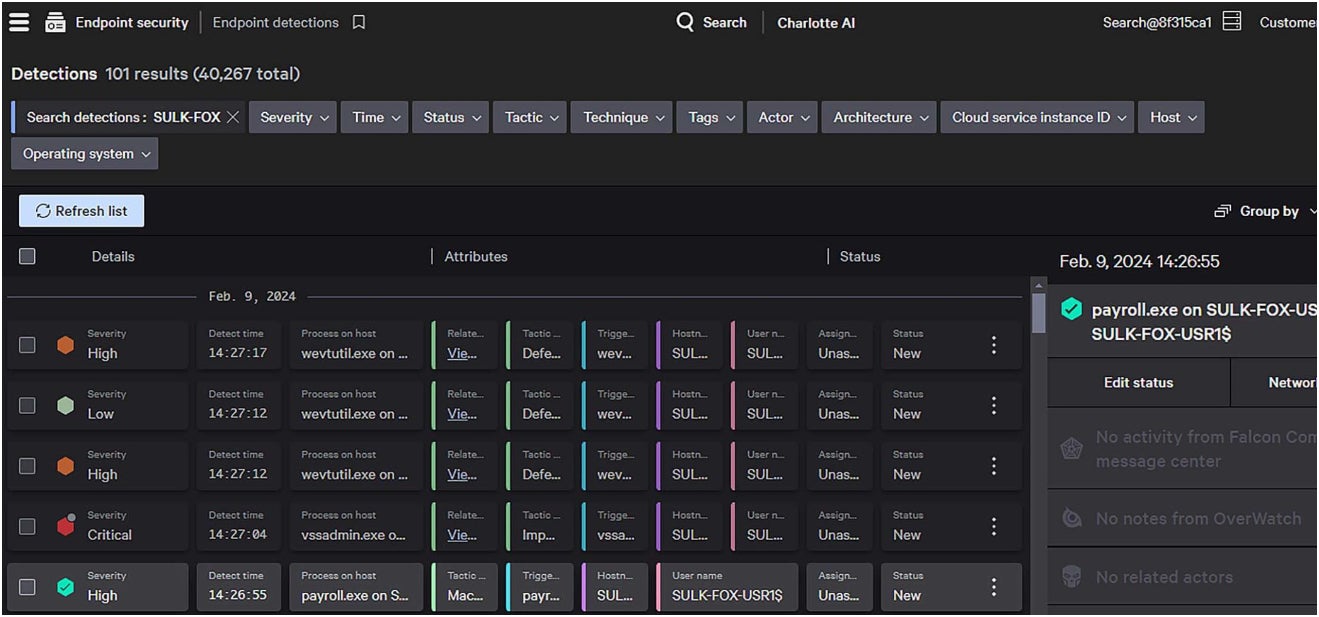
CrowdStrike also provides detection capabilities against known threats, utilizing a machine-learning detection model that is effective in identifying unknown threats and attacks.
Behavioral Learning
Trellix offers behavior-based detection which ensures a consistent procedure for risk assessment of threats, their stage, and prioritized responses. Moreover, Trellix EDR employs AI-guided investigations to generate machine-driven insights into potential exploits.or breaches for analysts in a corporation.
-

CrowdStrike Falcon Enterprise’s EDR and XDR solution. Image: CrowdStrike
Meanwhile, CrowdStrike’s event-driven behavioral detection detects signs of intrusion to thwart advanced fileless and virus-free security breaches. It scrutinizes historical threat data to detect potential irregularities.
Unified-agent design
Trellix EDR adopts a unified-agent structure integrating advanced security features like artificial intelligence and threat confinement.
CrowdStrike also employs a unified-agent setup encompassing all operations. Moreover, it incorporates a single-sensor structure that enhances system efficiency and reduces CPU utilization linked to running CrowdStrike.
Is CrowdStrike or Trellix the right fit for your organization?
Both solutions can safeguard your network and data while fortifying it against diverse threats and assaults. If you prioritize efficiency in vulnerability data gathering, Trellix EDR with its alert noise reduction capabilities can be more beneficial. Its AI-driven insights are also valuable for security experts in smaller entities looking to expand their expertise.
Conversely, CrowdStrike presents a complex system tailored for heavily regulated sectors or high-risk entities susceptible to security breaches. It’s well-suited for large enterprises with intricate security requirements. Organizations in sectors like finance, government, and healthcare often rely on CrowdStrike to fulfill their heightened security needs. CrowdStrike may also be preferable if you have numerous endpoints to secure and seek greater deployment flexibility.
CrowdStrike advantages and disadvantages
Advantages
- Intuitive user interface.
- Seamless and swift investigations.
- Accessible trial version.
Disadvantages
- Complex setup process.
Trellix advantages and disadvantages
Advantages
- AI-driven inquiries.
- Consistent performance.
- Focus on incident response.
Disadvantages
- Lack of transparent pricing.
Approach
My evaluation of CrowdStrike and Trellix’s EDR solutions entailed a thorough comparison of their feature sets, pricing, and overall value.
Specifically, I examined crucial EDR functionalities like threat detection, malware defense, behavioral analysis, incident handling, and investigation capabilities.
Our assessment of both products involved extensive analysis of official product documentation, included features, and potential business use cases. Furthermore, we leveraged third-party evaluations and user feedback from reputable review platforms to complement our insights.