
By Dexter Shin
A lot of official departments render their services online to facilitate their citizens. Moreover, if such services could be availed through a mobile application, it would offer great convenience and accessibility. But what occurs when malicious software masquerades as these services?
The McAfee Mobile Research Team uncovered an InfoStealer Android malware posing as a government agency service in Bahrain. This malware portrays itself as the endorsed app of Bahrain, asserting that users can either renew or submit applications for driver’s licenses, visas, and ID cards via mobile. Users persuaded by these mobile availability claims are handed over their crucial personal data for these services without suspicion. They target users via various channels like Facebook and SMS messages. Unwary users easily fall prey to sharing personal details due to these attacks.
In-depth fake application
In Bahrain, there exists a governmental body known as the Labour Market Regulatory Authority (LMRA). This organization functions with complete financial and administrative autonomy under the direction of a board of directors led by the Minister of Labour. They offer a range of mobile services, with most apps dedicated to a single service. Nevertheless, this fraudulent app asserts to provide multiple services at once.
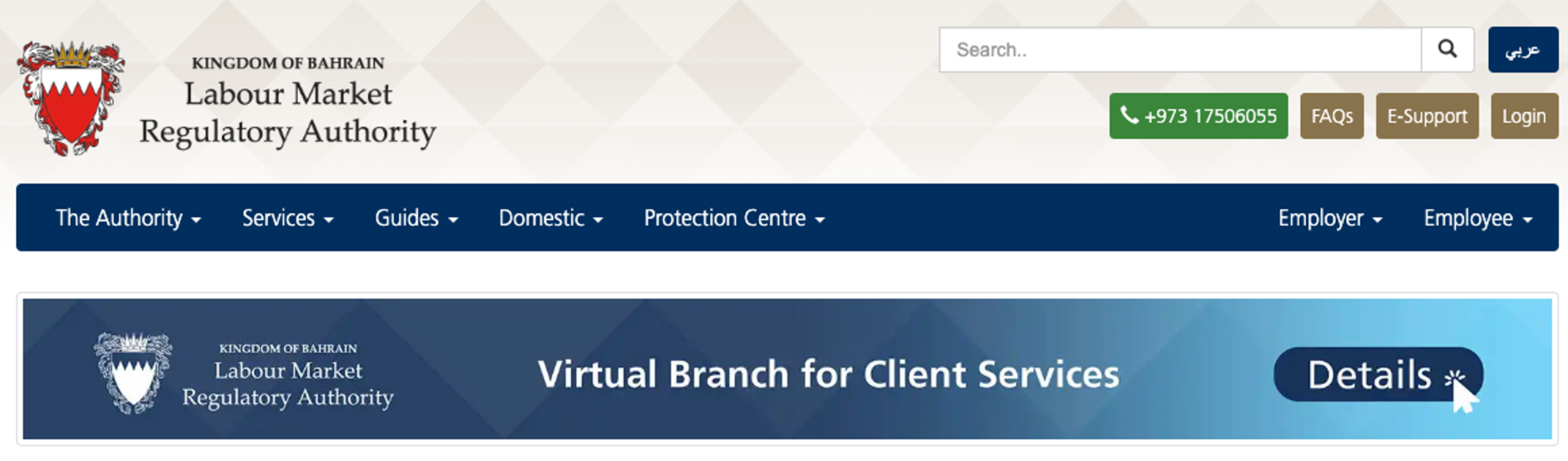
Figure 1. Authentic LMRA website
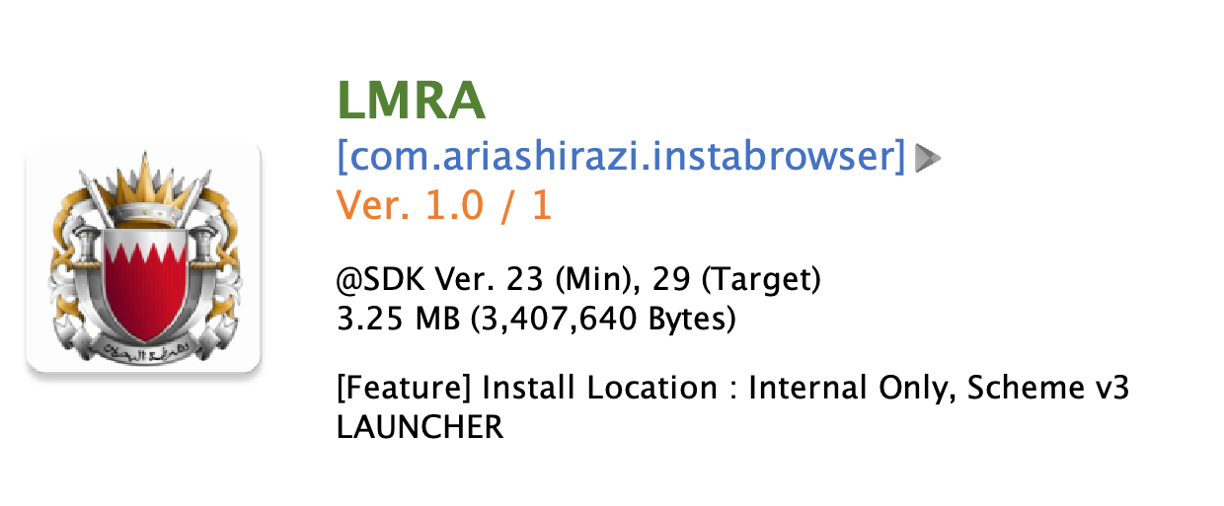
Figure 2. Bogus LMRA application
Excluding the commonly reported fake LMRA apps, other deceptive apps include imitations of Bank of Bahrain and Kuwait (BBK), BenefitPay, a Bahrain-based fintech company, and even apps pretending to be associated with cryptocurrencies or lending services. These apps implement analogous methods as the fake LMRA apps to filch personal information.

Figure 3. Different deceptive apps using similar strategies
Based on the type of app that this malware mimics, it’s likely aimed at financial deception utilizing the purloined personal data. Additionally, an individual has fallen victim to this scheme as depicted in the provided image.
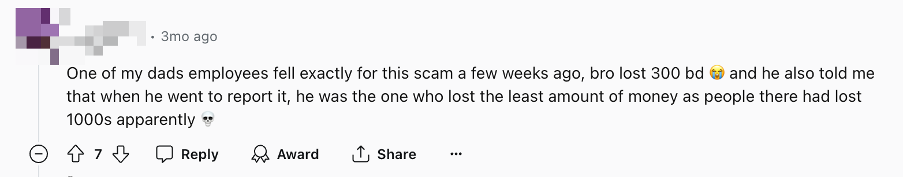
Figure 4. Victims of financial deception (Source: Reddit)
Means of dissemination
They circulate these apps via fake Facebook pages and SMS messages. The Facebook pages are counterfeit, and the malware creator incessantly generates new pages. These pages steer users toward phishing websites, either WordPress blogs or tailored sites devised for app downloads.
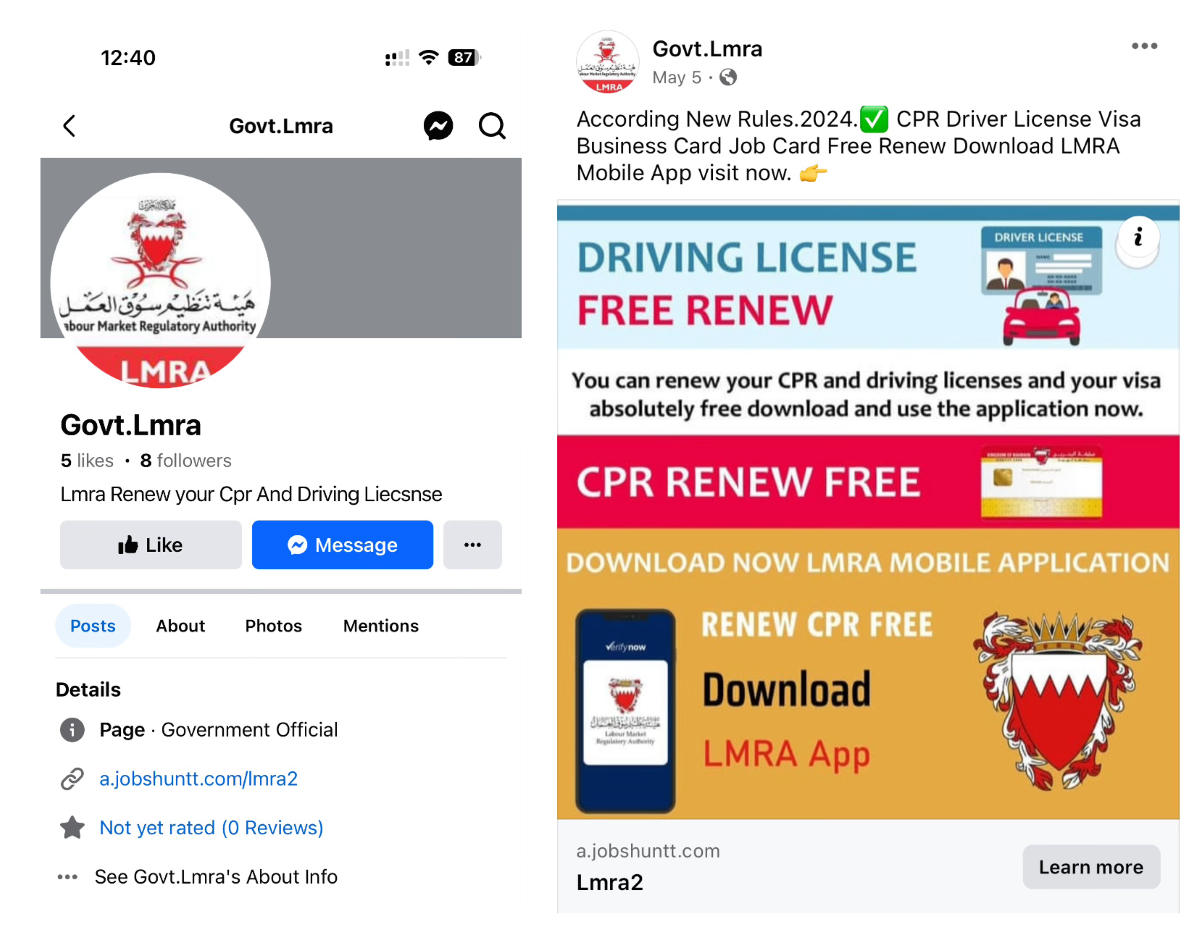
Figure 5. Facebook profile and page containing a phishing site link

Figure 6. One of the app-download phishing sites
Regarding SMS, users are duped through social engineering messages to induce them into immediately confirming by clicking a link.
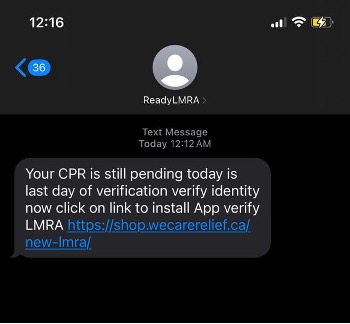
Here we can see Reddit as the source of the Phishing message displayed in Figure 7.
Intent behind their actions
The application initiates with a deceptive approach by presenting a seemingly legitimate icon, urging users to input their CPR and contact number. CPR, which stands for Central Population Register, is a distinct 9-digit code assigned to each Bahrain resident. Despite having a “Verify” option, it simply sends the data to the C2 server upon clicking. Once users provide their information, they are swiftly forwarded to the subsequent stage without any form of authentication. This action solely stores the entered details for the next phase.
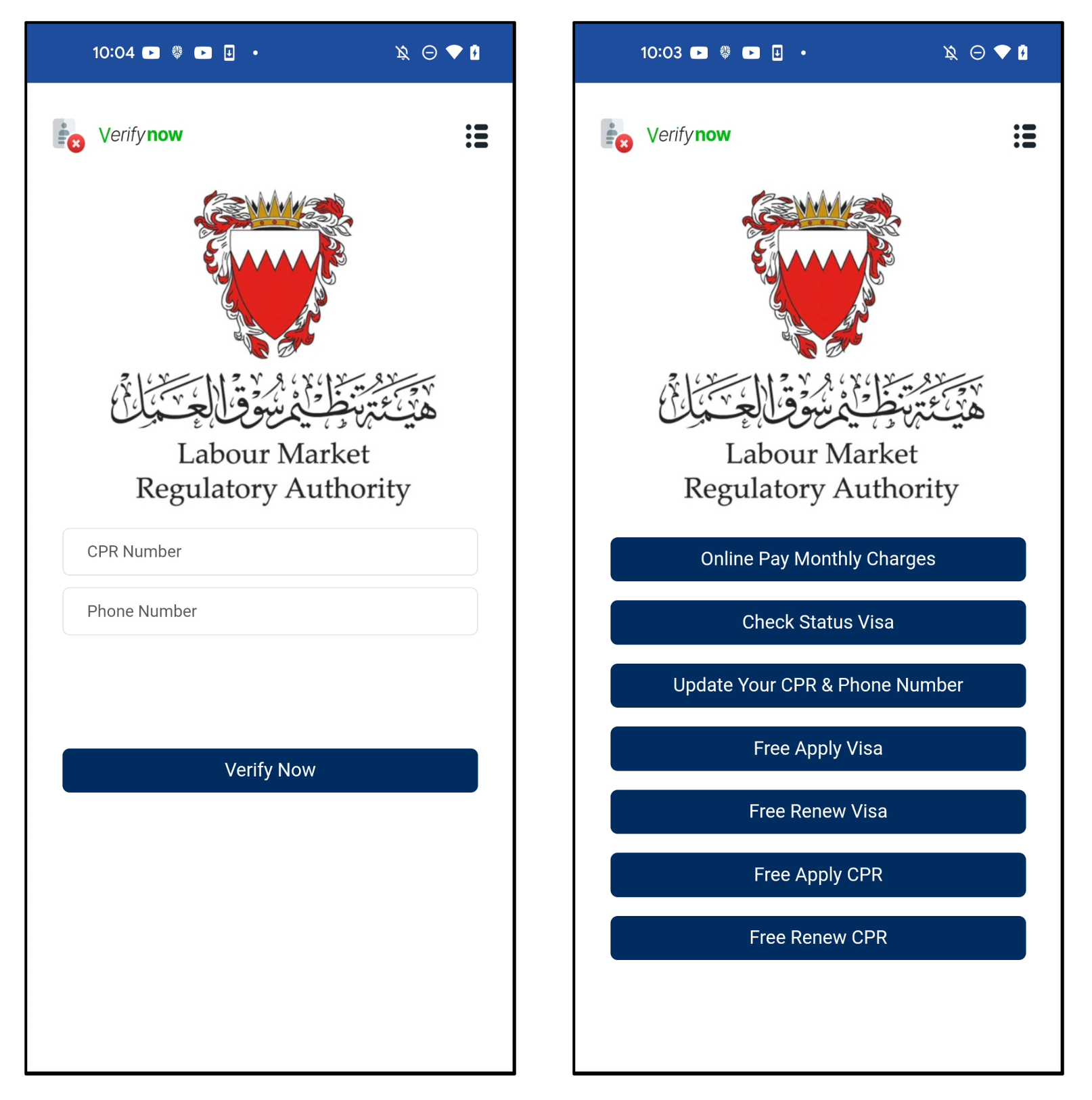
Figure 8 illustrates the initial and subsequent screens of this deceptive application.
The application features multiple menus, all linked to an identical URL. The parameter values consist of the CPR and contact numbers entered by the users on the initial screen.
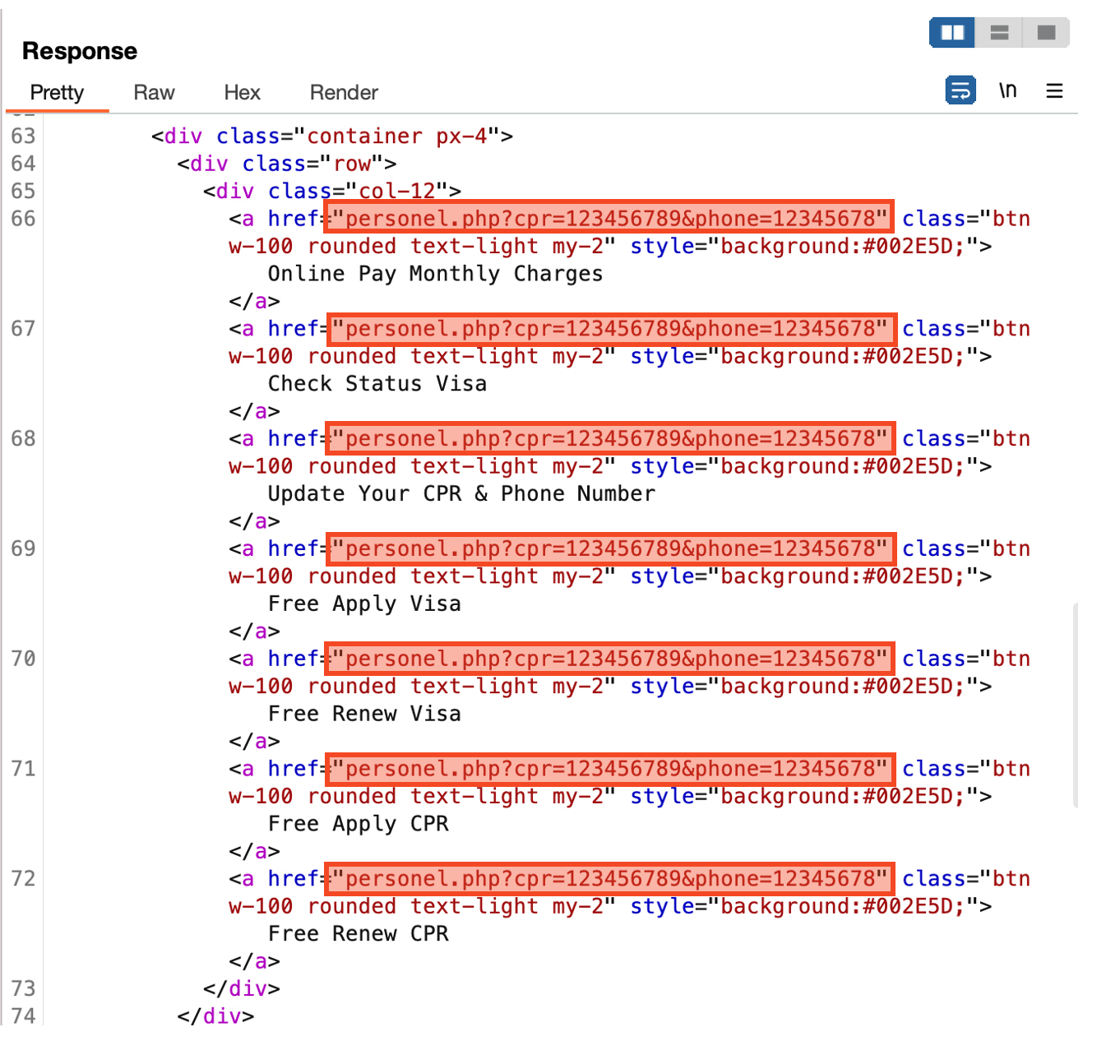
Figure 9 presents the interconnected menus directing to a single URL.
Upon reaching the final page, the user is prompted to provide their complete name, email address, and date of birth. Once all details are submitted and the “Send” button is clicked, all previously entered information is dispatched to the c2 server controlled by the malware’s author.
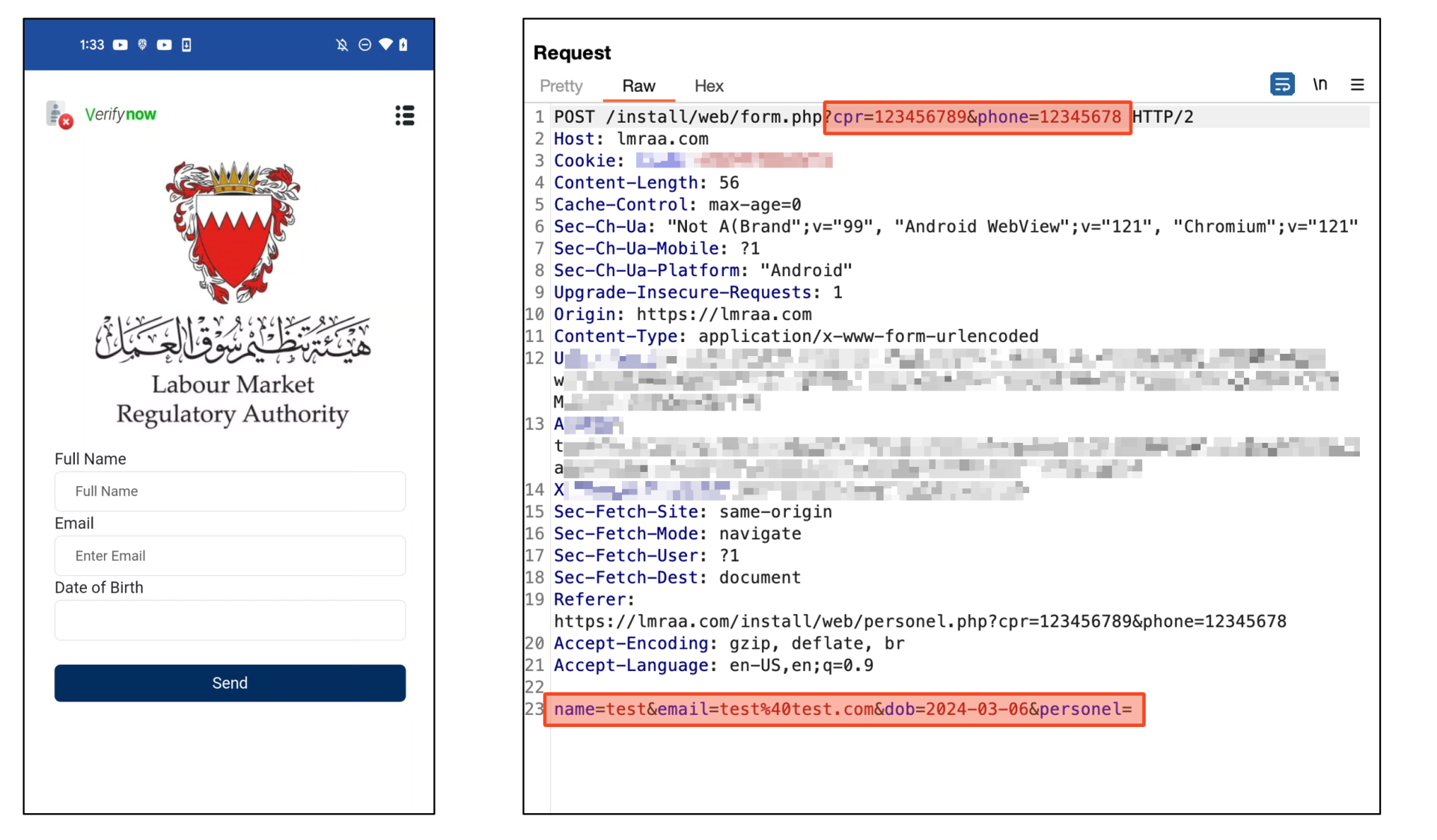
Figure 10 showcases the transmission of all data to the c2 server.
Utilization of Firebase for Dynamic Phishing Site Loading
It has been verified that there exist two variants of these applications. The first type establishes a personalized C2 server to directly retrieve data via web API, while the second type incorporates Firebase services. Firebase, a backend platform by Google, encompasses Firestore, a database for data storage. This malicious software exploits Firestore due to its association with a reputable service like Google, making it arduous to discern as a malevolent link.
Applications leveraging Firebase dynamically load phishing URLs stored within Firestore. Consequently, even if a phishing site is thwarted, immediate adjustments can be made by altering the URL saved in Firestore to sustain the existing victim base.

Illustration 13. Phishing site loaded dynamically in a webview
Inference
Based on our monitoring data, there have been 62 users who have utilized this application in Bahrain. Nevertheless, as this data is current at the time of composing, this count is foreseen to rise continually, given the ongoing generation of new Facebook pages.
New types of malicious software are seeking out specific countries or users instead of launching broad-scale assaults. These threats can be challenging for everyday users to spot since the malware adeptly tailors itself to the requirements of individuals situated in certain regions. Therefore, we urge users to equip their devices with reliable security solutions. Furthermore, users are advised to obtain and employ applications exclusively from authorized stores like Google Play Store or Apple AppStore. If an application cannot be found in these outlets, it is essential to download it from the official website.
The Android/InfoStealer threat has already been recognized by McAfee Mobile Security. For further details, please visit McAfee Mobile Security.
Signs of Intrusion (SOIs)
Instances:
| SHA256 | Package Title | Application Title |
| 6f6d86e60814ad7c86949b7b5c212b83ab0c4da65f0a105693c48d9b5798136c | com.ariashirazi.instabrowser | LMRA |
| 5574c98c9df202ec7799c3feb87c374310fa49a99838e68eb43f5c08ca08392d | com.npra.bahrain.five | LMRA Bahrain |
| b7424354c356561811e6af9d8f4f4e5b0bf6dfe8ad9d57f4c4e13b6c4eaccafb | com.npra.bahrain.five | LMRA Bahrain |
| f9bdeca0e2057b0e334c849ff918bdbe49abd1056a285fed1239c9948040496a | com.lmra.nine.lmranine | LMRA |
| bf22b5dfc369758b655dda8ae5d642c205bb192bbcc3a03ce654e6977e6df730 | com.stich.inches | Visa Update |
| 8c8ffc01e6466a3e02a4842053aa872119adf8d48fd9acd686213e158a8377ba | com.ariashirazi.instabrowser | EasyLoan |
| 164fafa8a48575973eee3a33ee9434ea07bd48e18aa360a979cc7fb16a0da819 | com.ariashirazi.instabrowser | BTC Flasher |
| 94959b8c811fdcfae7c40778811a2fcc4c84fbdb8cde483abd1af9431fc84b44 | com.ariashirazi.instabrowser | BenefitPay |
| d4d0b7660e90be081979bfbc27bbf70d182ff1accd829300255cae0cb10fe546 | com.lymors.lulumoney | BBK Loan App |
Domains:
- https[://]lmraa.com
- https[://]lmjbfv.site
- https[://]dbjiud.site
- https[://]a.jobshuntt.com
- https[://]shop.wecarerelief.ca
Firebase(for C2):
- https[://]npra-5.firebaseio.com
- https[://]lmra9-38b17.firebaseio.com
- https[://]practice-8e048.firebaseio.com
The article Counterfeit Android Application from Bahrain Government Extracts Personal Information for Financial Deception initially surfaced on McAfee Blog.





