
01 July 2024
During the prior week, an exploration was made on The Current Scenario of Data Breaches, and the input received was quite substantial. It primarily expressed support for the challenges faced in managing HIBP. The former post was a manifestation of frustration: the lack of transparency, uncooperative organizations, downplaying the severity of breaches, and exacerbation by the breach victims themselves by intensifying the situation between them and the corporate entities. Another aspect that has been revolving in my mind is the aspect portrayed by the illustration below:

Administering HIBP has evolved into a continuous juggling act involving a triad comprising hackers, corporate victims, and law enforcement. Let me elaborate:
Cyber Criminals
The origin of most data breaches can be traced to this group, with illegal access to secured systems and unauthorized data retrieval. This is a broad generalization, as the methodologies range from exploiting software vulnerabilities, obtaining exposed database backups, phishing administrative credentials, to obtaining the data. At its core, it involves wrongfully appropriating something that does not belong to them. At times, these cyber criminals initiate contact with me.
Navigating this position is challenging, as it involves weighing the potentially conflicting objectives of informing affected HIBP subscribers while abstaining from fostering the perverse motives of probable offenders. Some instances are straightforward: upon receiving reports regarding exposed data or security vulnerabilities, the advice is to directly notify the concerned organization to avert the situation transforming into a data breach. However, if the data has already been acquired, it constitutes a breach, implicating several of my subscribers. Engaging with the primary party accountable for the breach becomes uncomfortable.
There are myriad circumstances that can heighten this discomfort, such as if the hacker is attempting to extort money from the organization, selling the data on the breach market, or still retaining access to the corporate systems. Conversing with individuals in such a position requires tactfulness, all the while cognizant that they risk being apprehended, and every dialogue shared could potentially be scrutinized by law enforcement. Every word articulated is underpinned by this assumption. Eventually, being apprehended is a plausible prospect; just as defenders are compelled to be precise consistently while hackers only need to succeed once, hackers must ensure meticulous operational security every time as a single oversight could lead to their downfall. A dropped VPN connection, an email address, handle, or password linked to their identity elsewhere, or an erroneous assumption concerning the anonymity of cryptocurrency – a minor slip-up.
Moreover, these discussions necessitate confidentiality. Those reaching out expect confidentiality, established through the trust nurtured over more than a decade of managing this service. Compromising this trust by divulging these conversations without consent could precipitate reputational damage instantaneously. Consequently, often I find myself facilitating dialogues among the three aforementioned parties, exchanging contact information, or relaying messages with mutual agreement.
Such communication can become convoluted: the hacker (often distrustful of large corporations) endeavors to draw attention to an issue while trying to communicate with an entity naturally wary of anonymous individuals accessing their data! Simultaneously, law enforcement, in their inherent role, expresses interest in the hacker, but also acknowledges the function I serve and the reliability characterizing data sharing with me. Furthermore, law enforcement is frequently engaged by the corporate victim, leading to a scenario where all participants are conversing with each other with me in the intermediary position.
I share these insights not to boast about my role but to elucidate the intricate balance required in managing many of these data breaches. This complexity is compounded by the observations from the antecedent post regarding the lack of urgency, among other things.
Business Entities Affected
I opt for this phrase to underscore how easy it is for individuals to point fingers at a company that has undergone a data breach and attribute fault to them. Depending on the circumstances, some fault may be justifiable, but it is crucial to recognize that these companies are typically the victims of deliberate, malicious, criminal actions. When referring to “companies,” it ultimately encompasses individuals who are usually striving to perform to the best of their ability in their roles and, during an incident response phase, often enduring the most arduous period in their careers. I have discerned the agony in their voices and perceived the strain reflected in their expressions on countless occasions, emphasizing the importance of not losing sight of the human aspect amid the uproar of disgruntled customers.
The interaction between corporate victims and hackers demands finesse. They are understandably incensed but are also laboring to glean details about the incident (often unaware of the exact method by which the data was obtained in the initial stages), while navigating through exorbitant demands and maintaining composure. The anonymity-reliant party might opt to vanish altogether, intensifying the challenge. This delicate balancing act is evident in numerous communications released subsequently by hackers, often post-failure in securing the anticipated ransom payment: you encounter exceedingly considerate corporations… who, beneath the facade, harbor intentions of seeing the perpetrator incarcerated!
The involvement of law enforcement, or more broadly speaking, the interactions with governmental bodies in general, presents an intriguing dynamic. Apart from the evident engagement concerning the criminal endeavors of hackers, the corporate victims themselves bear legal responsibilities. This is significantly contingent on the jurisdiction and regulatory frameworks, possibly entailing reporting the breach to the pertinent government body, for instance. It might even necessitate reporting to multiple governmental entities (e.g., state-centric) based on the geographical location. Additionally, the issue of their accountability and the repercussions arising from their actions (or inaction) pre and post-breach could lead to punitive measures. In the previous post, I referenced “covering their arses,” which extends beyond safeguarding against customer or shareholder backlash to encompass shielding against substantial corporate fines.
Based on numerous past encounters, I believe corporations maintain a complex relationship with law enforcement. While they seek assistance in combating criminal elements, they exercise extreme caution in disclosing information, wary of potential implications that could result in punitive actions against them. Picture the intricate balancing act underway when corporate victims suspect that the breach transpired due to significant oversights on their part and approach law enforcement for aid: “How do you think they gained access? Uh…”
As iterated numerous times within this piece: “delicate.”
Legal Authorities
This component epitomizes the most multifaceted player in the triad, maintaining bilateral communications with each party involved in variousmethods. It is evident that their primary purpose is to ensure that criminals face legal consequences, placing hackers well within their jurisdiction. I have frequently mentioned “the FBI and allies” or similar terms to demonstrate the collaborative nature of international law enforcement efforts, as seen in the action taken against cybercrime initiatives:
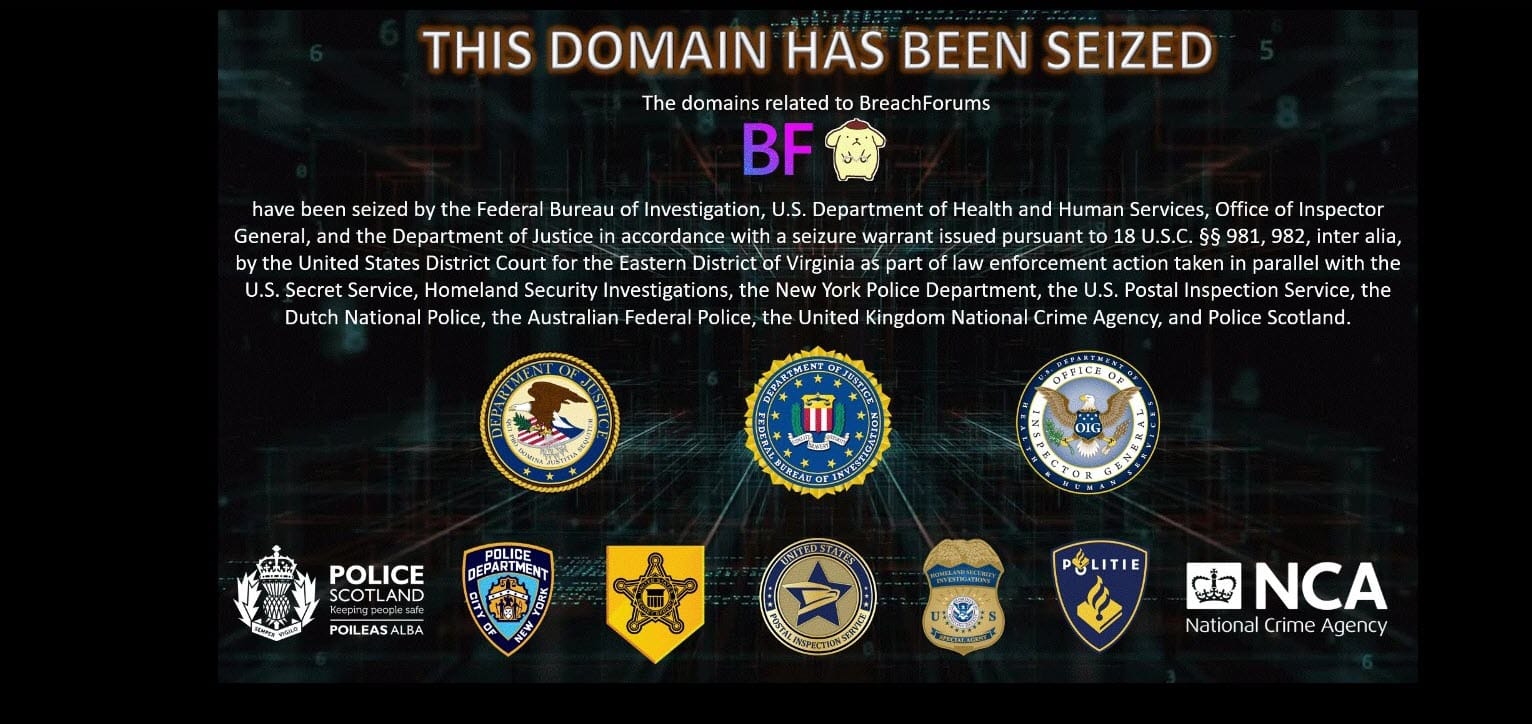
Hackers themselves often willingly interact with law enforcement. Sometimes to provoke, other times to directly target, often at a very personal level by identifying specific agents. It should be noted that “hacker” is a broad term that, at its worst, encompasses criminal activities intended for personal financial gain. On the other end of the spectrum is a more nuanced area where individuals labeled as such may not have malicious intentions but, to put it differently: “I stumbled upon something, can you assist me in reporting it to the authorities”.
The collaboration between law enforcement and corporate victims typically commences with the latter reporting an incident. This is commonly observed in disclosure statements such as “we have informed the authorities,” which is a natural course of action following a criminal act. It extends beyond hacking itself, often involving a ransom demand, adding another layer of criminal activity that necessitates authorities’ involvement. Conversely, law enforcement frequently detects early signs of compromise before the corporate victim, enabling direct communication. Increasingly, formal government entities are issuing broader cybersecurity guidance, as exemplified by the Australian Signals Directorate’s regular releases.
I often find myself assuming various roles with law enforcement agencies. For instance, establishing a channel for the FBI to integrate breached passwords, assisting the Estonian Central Criminal Police in making data concerning their citizens searchable, spending time with the Dutch police on victim notification, and providing testimony before US Congress. Additionally, supporting thirty-six national CERTs across the globe with unrestricted access to details of their government domains in HIBP. Many of these agencies exhibit a natural interest in individuals who contact me, particularly from the aforementioned first category. Nonetheless, I have always found law enforcement to treat with respect the information shared by hackers with me; they acknowledge the importance of the trust I previously mentioned, recognizing its significance in enabling me to fulfill my role.
Summary
A decade later, I still find this position of navigating between these three entities both peculiar and engaging. It is an environment characterized by unpredictability, fascination, excitement, and stress. I hope you found this insightful and enjoyable to read 🙂










