
ESET Research
A discovery by ESET researchers reveals a new zero-day exploit in Telegram for Android that enables the dissemination of harmful files disguised as videos
22 Jul 2024
•
,
6 min. read

An exploit targeting Telegram for Android, named EvilVideo, was uncovered by ESET researchers and was found on a sale post in an underground forum on June 6th, 2024. By abusing this vulnerability, attackers could distribute malicious Android payloads through Telegram channels, groups, and chats, masking them as multimedia files.
An instance of this exploit was identified, allowing for further analysis, and reported to Telegram on June 26th, 2024. Telegram responded by releasing an update on July 11th, 2024 that addresses the vulnerability in versions 10.14.5 and above.
Shown in Figure 1 is a demonstration video elucidating the EvilVideo vulnerability.
Figure 1. Explanation of the EvilVideo vulnerability
Essence of the blogpost:
- An advertisement for a zero-day exploit targeting Telegram for Android was discovered on June 26th, 2024, in an underground forum.
- The vulnerability known as EvilVideo exploited in this case was promptly reported to Telegram, leading to a patch on July 11th, 2024.
- The EvilVideo loophole enables attackers to circulate harmful payloads camouflaged as video files in unpatched versions of Telegram for Android.
- The exploit exclusively functions on Android Telegram versions 10.14.4 and below.
Unveiling
The exploit was found being promoted for sale within an underground forum as depicted in Figure 2.
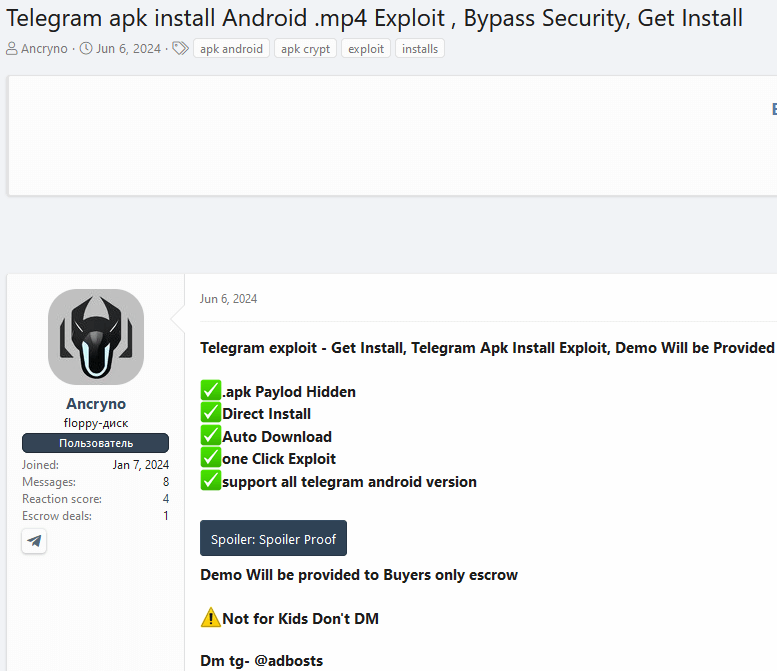
Within the post, the seller showcased screenshots and a video exemplifying the use of the exploit in a public Telegram channel. The identify of this channel was established, with the exploit still accessible. This allowed us to acquire the payload for testing.
Examination
An assessment of the exploit revealed its compatibility with Telegram versions 10.14.4 and earlier. It is presumed that the specific payload was likely engineered using the Telegram API, which enables developers to systematically upload carefully crafted multimedia files to Telegram chats or channels.
The exploit appears to hinge on the capability of threat actors to devise a payload that presents an Android app as a preview of multimedia content rather than a binary attachment. Once shared within a conversation, the malicious payload masquerades as a 30-second video (Shown in Figure 3).
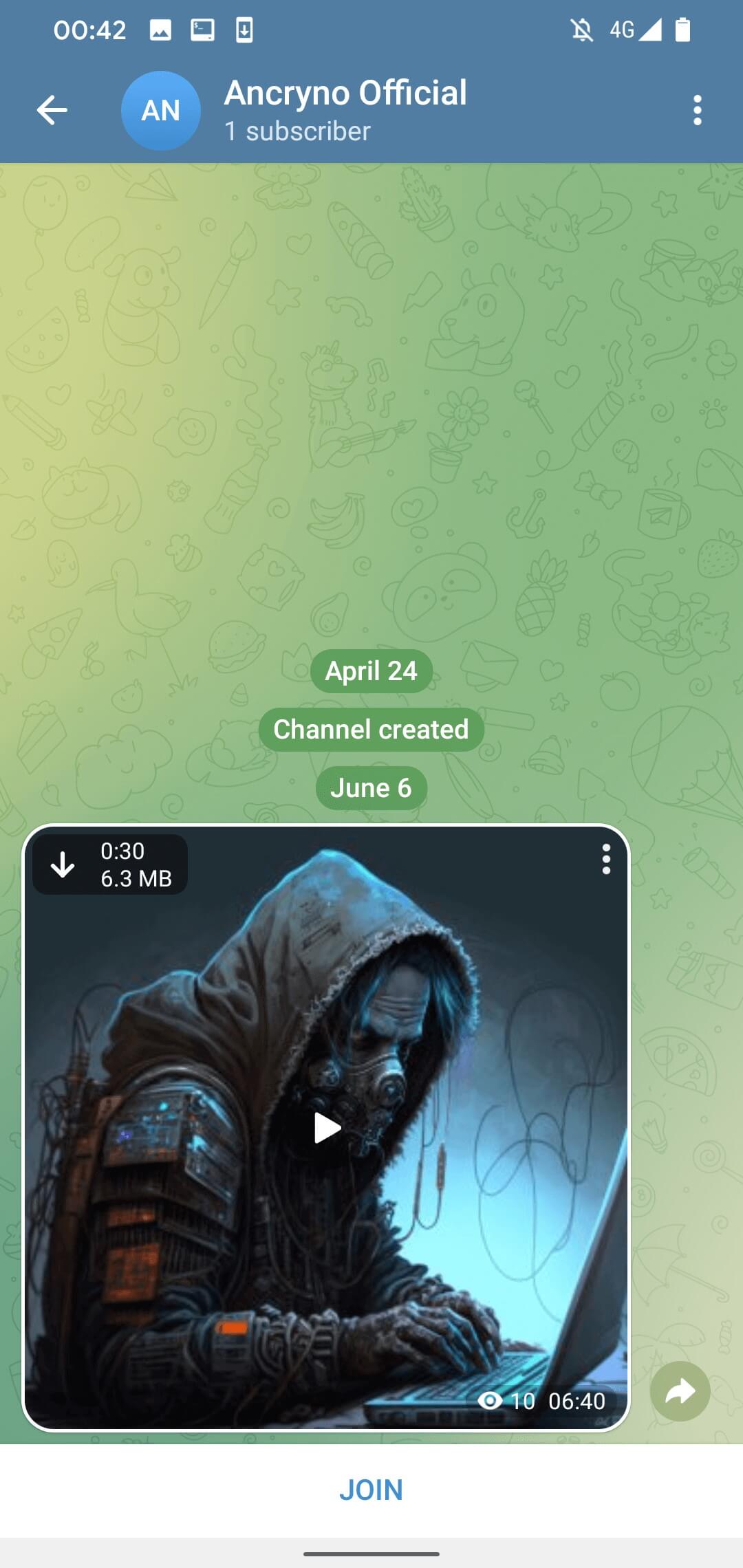
By default, media files received via Telegram initiate automatic downloads. This implies that users with this setting enabled will automatically receive the harmful payload when accessing the conversation where it was shared. However, manual download of the payload is still achievable by tapping the download button in the top-left corner of the apparent video as demonstrated in Figure 3.
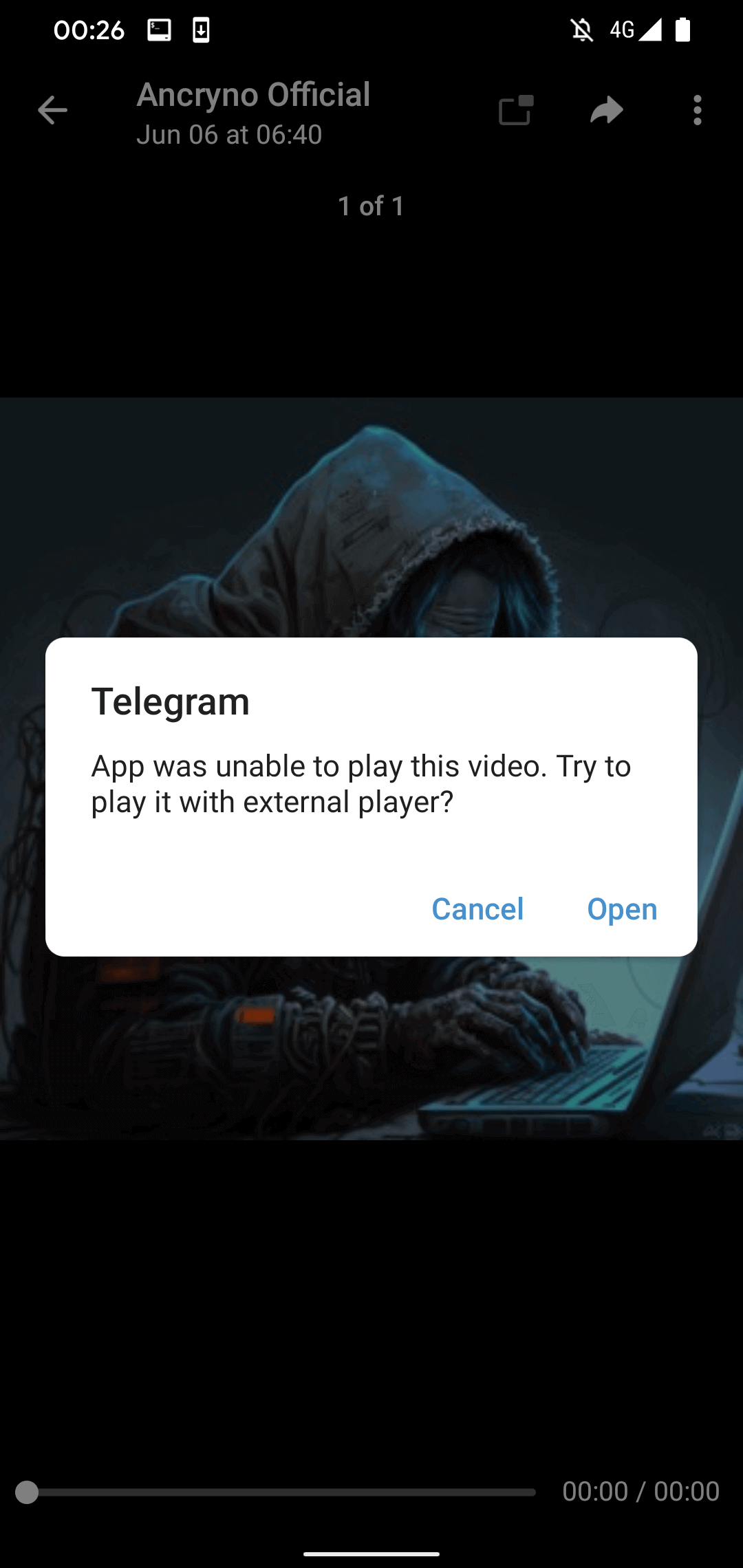
Upon attempting to play the “video”, Telegram will display an error message indicating its incapacity to play the content and advising usage of an external player (refer to Figure 4). This warning, originating from the legitimate Telegram for Android app’s source code, is not an output of the malicious payload but a standard Telegram communication.
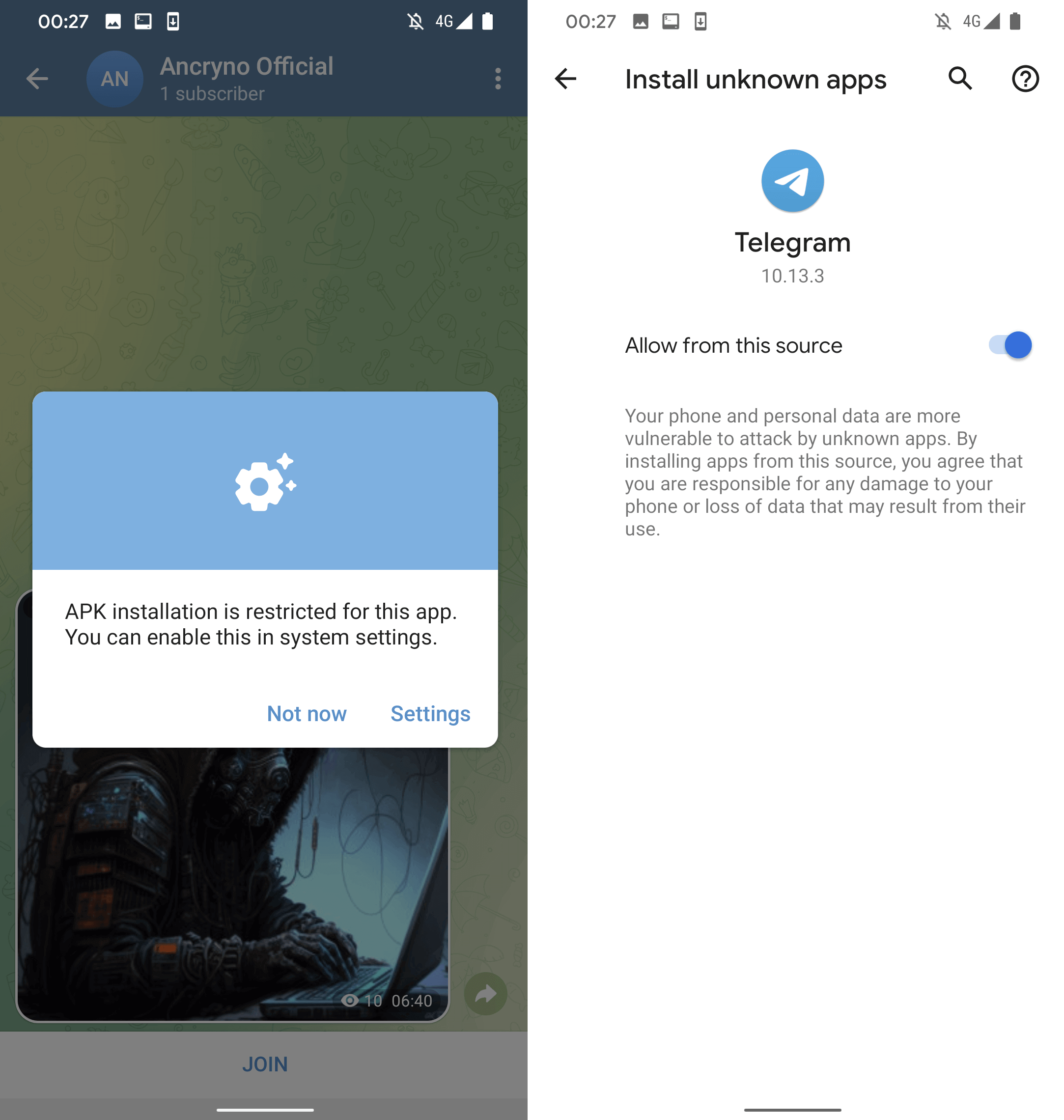
Should a user opt to tap the “Open” button within the prompt, they will be prompted to install a malicious app disguised as the previously suggested external player. Visible in Figure 5, Telegram would request permission from the user to install unverified apps before installation.
At this stage, the malicious app has already been downloaded under the guise of a video file, albeit bearing the .apk extension. It is interesting to note that the shared file’s video appearance is a side effect of the vulnerability — the harmful app itself was not altered to masquerade as a multimedia file, hinting towards an exploitation during the upload process. The solicitation for the installation of the malicious app is evident in Figure 6.
Regrettably, we were unable to replicate the exploit ourselves; we could only scrutinize and validate the sample furnished by the seller.
Telegram Web and Desktop
Despite the intended focus of the payload on Telegram for Android, we endeavored to evaluate its functionality across other Telegram platforms. Testing on both the Telegram Web client and the Telegram Desktop client for Windows demonstrated the exploit’s ineffectiveness on either of these clients.
Following an attempt to play the “video” on Telegram Web, an error message appeared instructing the user to utilize the desktop app for viewing, as seen in Figure 7. Manual downloading of the attached file unveiled its name and extension as Teating.mp4. Although the content was an Android executable binary (APK), the misidentification as an MP4 file by Telegram thwarted the exploit since the attachment needed to be identified with the .apk extension for it to function.
A parallel occurrence took place on the Telegram Desktop client for Windows whereby the downloaded file was labeled Teating.apk.mp4, reaffirming that it was an APK binary file posing as an MP4. This implies that even if an attacker meticulously crafted a malicious app, Telegram’s interpretation of it as an MP4 file impeded the exploit, requiring an extension of .apk for execution.
A Windows executable could replace the Android APK, treating it still as a multimedia file, making the exploit ineffective.

Threat actor
Limited information is available about the threat actor. However, we were able to discover another sketchy service they offer using the Telegram handle provided in their forum post. Apart from the exploit, they are promoting an Android cryptor-as-a-service on the same underground forum, claiming it to be completely undetectable (FUD) since January 11th, 2024. You can view the forum post in Figure 8.
Vulnerability report
Upon identifying the EvilVideo vulnerability on June 26th, 2024, we adhered to our coordinated disclosure policy by reporting it to Telegram. Initially, we received no response. Subsequently, we re-reported the vulnerability on July 4th, prompting Telegram to acknowledge and investigate the issue on the same day. They rectified the problem with version 10.14.5 released on July 11th and confirmed the fix via email.
The vulnerability impacted all versions of Telegram for Android up to 10.14.4 but has been addressed in version 10.14.5. We confirmed that the chat multimedia preview now accurately identifies the shared file as an application (Figure 9) rather than a video.

Conclusion
We came across a zero-day Telegram for Android exploit available for purchase on an underground forum. This exploit leveraged a vulnerability enabling the transmission of malicious payloads camouflaged as multimedia files via Telegram chat. Should a user attempt to play the purported video, a request to install an external app would pop up, which in reality deploys the malicious payload. Fortunately, Telegram addressed this vulnerability on July 11th, 2024, post our disclosure to them.
For queries regarding our research featured on WeLiveSecurity, feel free to reach us at threatintel@eset.comESET Research offers confidential APT intelligence reports and data feeds. To know more about this service, check out the ESET Threat Intelligence page.
IoCs
An extensive list of Indicators of Compromise (IoCs) and samples is available in our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinityhackscharan. |
Administrator Beam Cable System |
2024‑07‑16 |
C&C server of EvilVideo payload. |
MITRE ATT&CK techniques
This table was constructed using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Exploitation for Initial Access |
The EvilVideo vulnerability can be abused by Android malware to achieve initial device access. |
|
|
Execution |
Exploitation for Client Execution |
The EvilVideo vulnerability tricks the victim into installing a malicious app that impersonates a multimedia file. |







