
The illicit activity known as carding, which involves the theft, sale, and use of stolen payment card data, has historically been dominated by hackers based in Russia. Fortunately, the widespread adoption of more secure chip-based payment cards in the United States has weakened the carding market. However, a surge of innovative approaches from cybercriminal networks in China is injecting new vitality into the carding sector, by transforming phished card data into mobile wallets that enable online and in-store transactions.
Displayed on a Chinese phishing group’s Telegram channel are different toll road phishing kits available.
If you possess a smartphone, it is highly likely that you have encountered a phishing message within the past couple of years. These messages typically mimic official entities such as the U.S. Postal Service or pose as local toll road operators claiming unpaid toll fees.
Advanced phishing kits offered by various cybercriminals in mainland China are behind these messages, which diverge from conventional SMS phishing or “smishing” tactics by evading direct communication through mobile networks. Instead, these messages are channeled via the Apple iMessage service and the RCS technology, akin to Google phones.
Individuals prompted to input their card details on these fraudulent sites are informed that their bank must validate a small transaction by sending a one-time passcode to their mobile device. In reality, this code, once provided by the victim, is used by the fraudsters’ financial institution to authenticate the user’s intent to associate their card details with a mobile wallet.
Upon the victim furnishing the one-time code, the scammers will connect the card details to a new mobile wallet from Apple or Google, integrating the wallet into a smartphone under their control.
A REVAMPED APPROACH TO CARDING
Ford Merrill, an individual engaged in security research at SecAlliance, a branch of the CSIS Security Group, has scrutinized the development of several smishing syndicates in China. He observed that many of these groups utilize instructive video tutorials within their sales profiles on Telegram. These videos demonstrate the process of loading numerous stolen digital wallets onto a single device, which is subsequently retailed in bulk for substantial sums.
Reflecting on his discoveries at the M3AAWG security conference in Lisbon, Merrill remarked, “Who claims carding is obsolete? This is the ultimate mag stripe duplication device. This threat actor stipulates the purchase of at least 10 phones, which they will promptly dispatch to the buyer.”
One promotional video exhibits stacks of milk crates brimming with phones available for sale. Upon closer scrutiny, each phone bears a handwritten note detailing the date of wallet installation, the quantity of wallets present, and the seller’s initials.
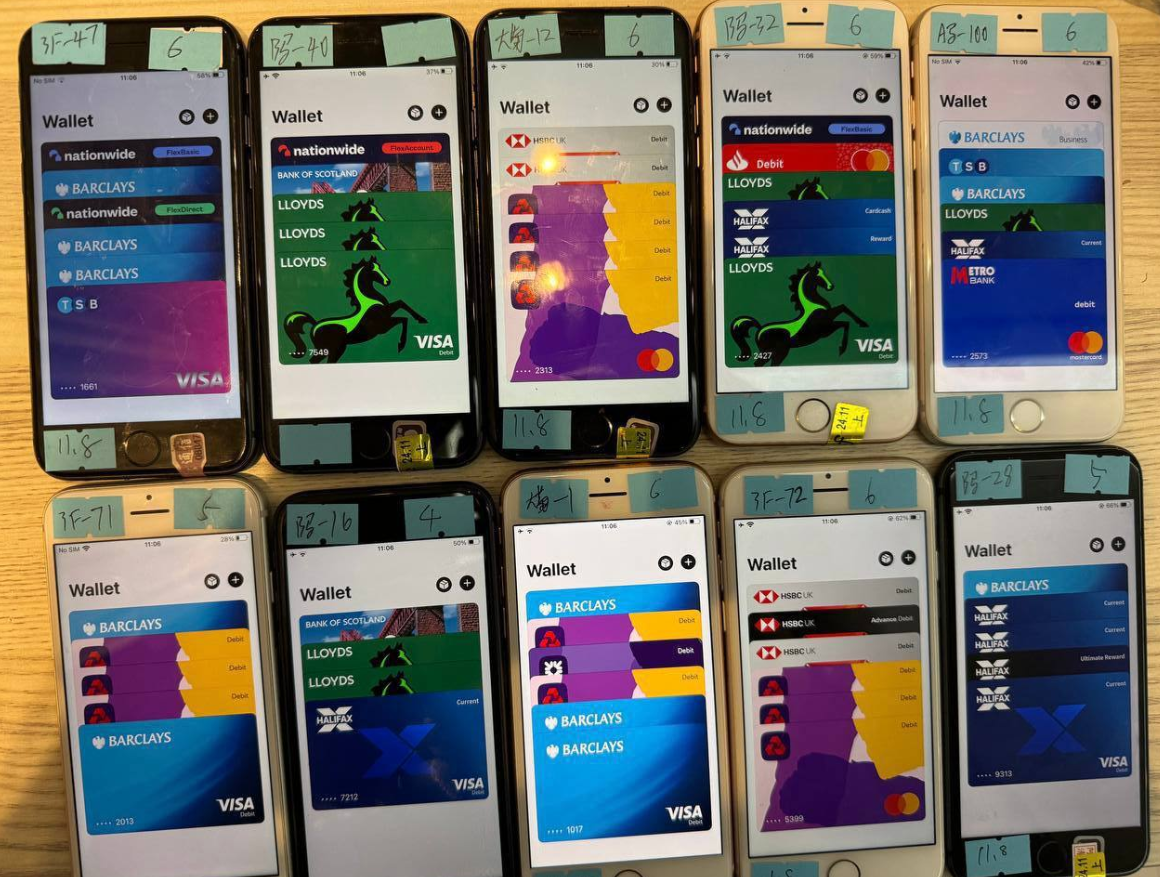
Observed on the Telegram channel of a prominent Chinese smishing kit vendor are 10 mobile phones for sale, each loaded with 4-6 digital wallets from diverse UK financial institutions.
Merrill disclosed that a prevalent method employed by criminal factions in China to liquidate stolen mobile wallets is through the establishment of fictitious e-commerce entities on platforms like Stripe or Zelle, executing transactions, typically ranging from $100 to $500, through these channels.
Initially, these phishing groups would wait approximately 60 to 90 days before vending the phones or engaging in fraudulent activities since commencing operations in earnest two years ago. Presently, this waiting period has notably dwindled to merely seven to ten days.
“At the outset of this deployment, the actors exemplified immense patience,” Merrill emphasized. “However, nowadays, only a brief window of 10 days transpires before high-intensity exploitation of the wallets commences.”
TECHNOLOGICAL INNOVATION: GHOST TAP
Criminals have devised methods to exploit mobile wallets by acquiring legitimate point-of-sale terminals, enabling tap-to-pay functionality across multiple devices. Another cutting-edge approach to mobile fraud identified by Merrill involves the sale of an Android application by one of the Chinese phishing groups, termed “ZNFC.” This app enables the relay of a valid NFC transaction from any location globally. Users merely wave their device at a compatible payment terminal accepting Apple or Google Pay, while the app transmits the NFC transaction remotely from a Chinese phone.
“This software boasts universal functionality,” Merrill underlined. “The developers offer the software at a rate of $500 monthly, facilitating both NFC-enabled tap-to-pay and digital wallet transactions, supported by round-the-clock assistance.”
The emergence of the “ghost tap” mobile software was initially documented in November 2024 by security analysts at ThreatFabric. Notably, Andy Chandler, the company’s chief commercial officer, highlighted the proliferation of criminal groups from diverse regions worldwide adopting this illicit means.
These encompass organized crime syndicates in Europe leveraging analogous mobile wallet and NFC tactics to siphon funds from ATMs compatible with smartphones.
Chandler emphasized, “A multitude of methodologies underpins the same modus operandi, with over ten unique approaches surfacing, each with distinct operational nuances. This phenomenon transcends the limited disclosures made by financial institutions thus far.”
An article published by Singapore’s The Straits Times in November 2024 reported the arrest of three foreign individuals recruited through social messaging platforms in their home countries. Equipped with ghost tap applications, these individuals perpetrated e-commerce scams, illicitly purchasing high-value items from retailers like mobile phones, jewelry, and gold bars.
Since November 4, a minimum of ten individuals deceived by e-commerce fraud schemes reported unauthorized transactions exceeding $100,000 on their credit cards, funding purchases from…
such as digital goods, such as iPhones and adapters, and ornaments in Singapore,” The Straits Times expressed, highlighting a separate incident where authorities apprehended a man and woman from Malaysia on Nov 8.

Three individuals accused of utilizing ghost tap software at an electronics establishment in Singapore. Image: The Straits Times.
INNOVATIVE PHISHING TACTICS
As per Merrill, the fake pages designed to imitate the USPS and various toll agencies are enhanced with several advancements to optimize the retrieval of target data.
For instance, a potential smishing target may input their personal and financial details but then realize it’s a hoax before submitting the data. In such cases, any information entered into the phishing page is collected in real time, irrespective of whether the user clicks the “submit” button or not.
Merrill mentioned that individuals providing credit card data on these phishing sites are often informed that their card cannot be processed and are encouraged to try a different one. This tactic, he explained, sometimes enables the scammers to pilfer more than one digital wallet per victim.
Unlike many phishing sites that retain stolen data on the phishing domain, these Chinese phishing kits forward all victim data to a backend database maintained by the kit vendors, as per Merrill. This strategy ensures that even if the smishing sites are shut down for deception, the stolen data remains intact and secure.
Another notable development is the utilization of mass-generated Apple and Google accounts through which these scammers send out their mass messages. One of the Chinese phishing groups showcased images on their Telegram sales channels illustrating how these automated Apple and Google accounts are loaded onto Apple and Google devices and arranged neatly next to each other in a vast, multi-tiered rack situated directly in front of the phishing service operator.

The ashtray says: You’ve been phishing all night.
Put differently, the smishing websites rely on real human operators as long as new messages are being dispatched. Merrill pointed out that the fraudsters typically send only a limited number of messages at once, likely because the scam necessitates manual effort from the human operators in China. After all, most one-time codes utilized for digital wallet setup expire within a few minutes.
Interestingly, none of the phishing sites imitating the toll agencies or postal services will load on a standard web browser; they activate only if they detect that the visitor is accessing from a mobile device.
“They want you to use a mobile device so that you receive the one-time code on the same device,” Merrill elaborated. “Moreover, they aim to minimize the chances of you exiting. To capture that mobile tokenization and acquire your one-time code, they require a live operator.”
Merrill discovered that the Chinese phishing kits feature another advancement facilitating customers to convert stolen card details into a digital wallet effortlessly: They automatically transform the card data provided by the phishing victim into a digital depiction of a legitimate payment card corresponding to the victim’s financial institution. Hence, attempting to register a stolen card on platforms like Apple Pay becomes as straightforward as scanning the counterfeit card image using an iPhone.
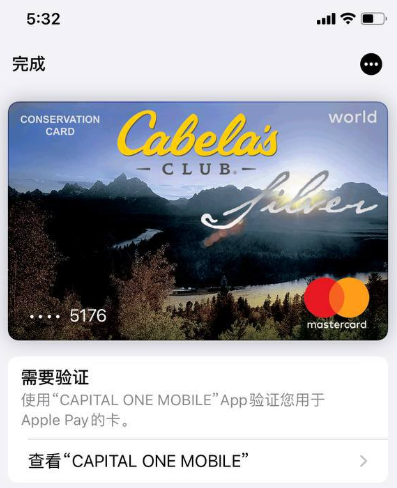
An advertisement from a Chinese SMS phishing group’s Telegram channel illustrating how the service transforms stolen card data into an image of the pilfered card.
“The phone cannot differentiate between a real card and an image,” pointed out Merrill. “Hence, it scans the card into Apple Pay, which then requests verification of card ownership by dispatching a one-time code.”
REVENUES
How lucrative are these mobile phishing kits? The most informed estimate till date emerges from data collated by other security analysts who have been monitoring these sophisticated Chinese phishing vendors.
In August 2023, the security company Resecurity uncovered a vulnerability in a prominent Chinese phish kit vendor’s system that exposed the personal and financial information of phishing victims. Referred to as the Smishing Triad by Resecurity, the group was found to have harvested 108,044 payment cards from 31 phishing domains (3,485 cards per domain).
In August 2024, security researcher Grant Smith delivered a presentation at the DEFCON security conference detailing his pursuit of the Smishing Triad following incidents where scammers impersonating the U.S. Postal Service fooled his spouse. By identifying an alternate weakness in the group’s phishing kit, Smith disclosed that individuals enrolled 438,669 distinct credit cards across 1,133 phishing domains (387 cards per domain).
Based on his study, Merrill suggested that each card turned into a digital wallet could result in losses ranging from $100 to $500. Merrill remarked they identified close to 33,000 distinct domains associated with these Chinese smishing collectives in the year between Resecurity’s report and Smith’s DEFCON presentation.
By assuming a median of 1,935 cards per domain and a conservative loss of $250 per card, the potential fraudulent charges could exceed $15 billion over a year.
Merrill refrained from divulging whether he had unearthed additional security vulnerabilities in any of the phishing kits distributed by the Chinese groups, pointing out that the fraudsters promptly rectified vulnerabilities highlighted publicly by Resecurity and Smith.
COMBATING THE THREAT
The popularity of contactless payments surged in the United States post the onset of the COVID-19 pandemic, prompting many American financial institutions to facilitate the linking of payment cards to mobile wallets. Consequently, the standard authentication process for this connection defaulted to dispatching a one-time code via SMS.
Experts believe that this persistent reliance on one-time codes for mobile wallet activation has fostered this recent surge in fraudulent card activity. KrebsOnSecurity conversed with a security professional from a major European financial entity who requested anonymity due to lack of authorization to engage with the media.
The expert pointed out that the delay between the phishing of card information and its eventual misuse for fraudulent activities has left several financial institutions struggling to identify the underlying causes of their financial losses.
“That’s partly why the industry has been caught off guard,” the expert remarked. “Many are questioning how this could occur when we’ve transitioned from a plaintext process. The volume of responses to these phishers is unprecedented.”
To enhance the security of the digital wallet setup process, some banks in Europe and Asia mandate customers to log into the bank’s mobile application before linking a digital wallet to their device.
Alleviating the ghost tap menace might necessitate updates to contactless payment terminals to better discern NFC transactions relayed from other devices. However, specialists indicate that expecting retailers to replace their existing payment terminals before they reach the end of their estimated lifespan is unrealistic.
In addition, both Apple and Google have a heightened responsibility, given that their accounts are being generated in bulk and utilized to broadcast these smishing messages. Both corporations could easily track which of their devices suddenly have numerous mobile wallets from various individuals across the globe. They could also suggest that financial institutions adopt more secure authentication methods for digital wallet activation.
Neither Apple nor Google responded to requests for comments on this matter.










