Two individuals have been apprehended for reportedly pilfering information and blackmailing numerous organizations that utilized the cloud data storage entity Snowflake. However, a third suspect — a highly skilled computer intruder by the moniker of Kiberphant0m — is still on the loose and persistently extorting victims publicly. Nonetheless, the identity of this individual may not remain concealed for much longer: A meticulous examination of Kiberphant0m’s daily conversations across various online criminal personas implies they are a United States military personnel who either is or was stationed recently in South Korea.
Kiberphant0m’s personalities on online criminal platforms and chat channels like Telegram and Discord have been marketing information stolen from clients of the cloud data storage firm Snowflake. Towards the culmination of 2023, malevolent computer intruders discovered that several companies had uploaded extensive amounts of confidential consumer data to Snowflake accounts that only had username and password protection (sans multi-factor authentication).
Following a search on hidden internet markets for taken Snowflake account login details, the intruders began looting the data repositories of some of the planet’s largest corporations. Among these was AT&T, which made public in July that cybercriminals had illegally obtained personal details, phone records, and text messages of around 110 million individuals. Wired.com reported in July that AT&T compensated a hacker $370,000 to erase stolen call records.
On October 30, authorities in Canada apprehended Alexander Moucka, also known as Connor Riley Moucka hailing from Kitchener, Ontario, under a provisional arrest warrant from the United States, which subsequently indicted him on 20 criminal charges linked to the Snowflake breaches. Another individual suspected in the Snowflake infiltrations, John Erin Binns, is an American currently imprisoned in Turkey.

A photograph from surveillance of Connor Riley Moucka, aka “Judische” and “Waifu,” dated Oct 21, 2024, 9 days before Moucka’s detention. An investigator from the Royal Canadian Mounted Police (RCMP) submitted this image as part of an affidavit.
Investigators claim that Moucka, using the aliases Judische and Waifu, had assigned Kiberphant0m with selling purloined data from Snowflake customers who declined to pay a ransom for their data’s eradication. Immediately subsequent to the dissemination of news on Moucka’s arrest, Kiberphant0m exhibited visible fury and posted on the hacker hub BreachForums what purportedly were AT&T call logs for President-elect Donald J. Trump and Vice President Kamala Harris.
“In case you fail to get in touch with us @ATNT, all governmental officials’ call logs will be revealed,” Kiberphant0m warned, employing numerous “#FREEWAIFU” tags. “Don’t assume we lack contingency plans in the event of an apprehension. Rethink your assumptions.”
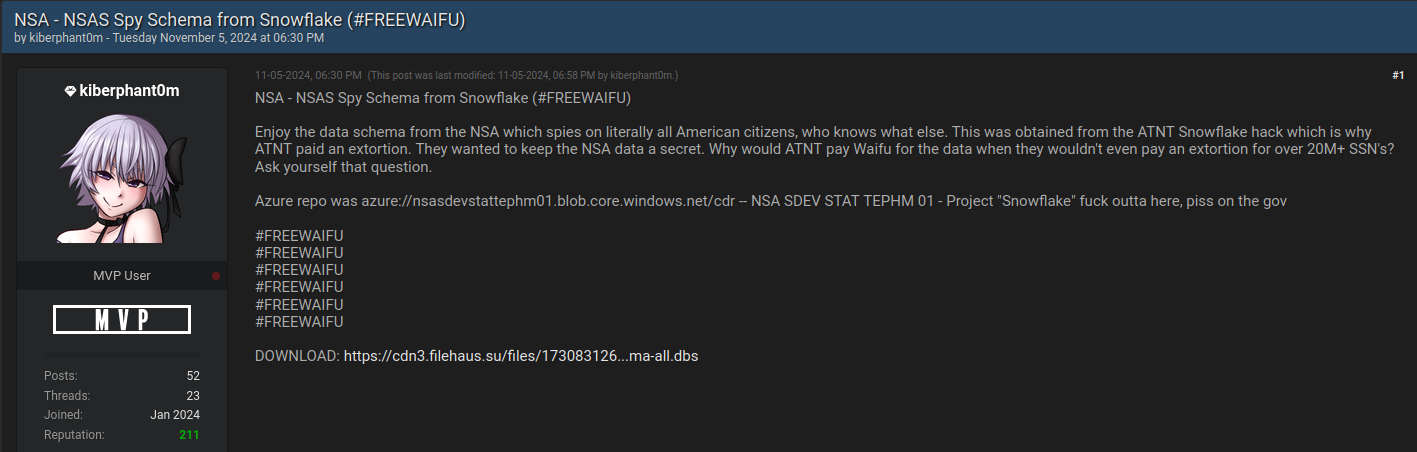
Simultaneously, Kiberphant0m disclosed what they claimed to be the “data schema” from the U.S. National Security Agency.
“This was secured from the ATNT Snowflake breach, which explains why ATNT made a payoff for the information,” Kiberphant0m inscribed in a discussion on BreachForums. “For what reason would ATNT remunerate Waifu for the information when they refused to pay extortion for more than 20 million+ SSNs?”
On Nov. 5, Kiberphant0m put up for sale call logs obtained from Verizon’s push-to-talk (PTT) customers — predominantly agencies of the U.S. government and first responders in emergencies. By Nov. 9, Kiberphant0m promoted a sales exhibit on BreachForums advertising a “SIM-swapping” assistance aimed at Verizon PTT clients. In a SIM-swap, criminals leverage credentials acquired illicitly or stolen from mobile network company employees to redirect a target’s calls and messages to a gadget under their command.
GET ACQUAINTED WITH ‘BUTTHOLIO’
Kiberphant0m accessed BreachForums in January 2024, although their public statements on Discord and Telegram channels date back to at least the beginning of 2022. In their initial post on BreachForums, Kiberphant0m disclosed that they could be reached via the Telegram handle @cyb3rph4nt0m.
An appraisal of @cyb3rph4nt0m shows that this user has made more than 4,200 posts since January 2024. Many of these posts functioned as attempts to enlist individuals who could be engaged to distribute a software that surreptitiously controlled host devices in an Internet of Things (IoT) botnet.
On BreachForums, Kiberphant0m has circulated the source code for “Shi-Bot,” a personalized Linux DDoS botnet patterned after the Mirai malware. Prior to the public revelation of the Snowflake assaults in May, Kiberphant0m had few trading threads on BreachForums, a significant portion of which comprised databases pilfered from firms in South Korea.
On June 5, 2024, a user on Telegram under the alias “Buttholio” joined the fraud-centric Telegram channel “Comgirl” and asserted they were Kiberphant0m. Buttholio made this declaration subsequent to being taunted as being insignificant by another contributor of Comgirl, alluding to their @cyb3rph4nt0m account on Telegram and the Kiberphant0m alias on cybercrime platforms.
“Type ‘kiberphant0m’ on google with the quotes,” Buttholio instructed another individual. “I’ll wait. Go ahead. Over 50 articles. 15+ telecommunications breached. I have acquired the IMSI number of every individual ever registered with Verizon, Tmobile, ATNT, and Verifone.”
On September 17, 2023, Buttholio messaged in a Discord chatroom dedicated to players of the video game Escape from Tarkov. “Head to Korea, the servers there hardly have extract campers or cheaters,” Buttholio suggested.
In another message on that same day within the gaming Discord, Buttholio informed others that they purchased the game in the United States but were playing it in Asia.
“The game was bought in the USA, but the server’s location is the actual in-game servers you play on. I am a United States fighter so”I purchased it in the United States but had to switch to using servers in Asia due to rotation,” they disclosed.
‘REVERSESHELL’
The account @Kiberphant0m was allocated the Telegram ID number 6953392511. An examination of this ID on the cyber intelligence platform Flashpoint indicates that on January 4, 2024, Kibertphant0m posted on the Telegram channel named “Dstat,” which is frequented by cybercriminals engaged in initiating distributed denial-of-service (DDoS) assaults and offering DDoS-for-hire services [Disclosure: At present, Flashpoint advertises on this website].
Right after Kiberphant0m joined the Dstat channel, another user greeted with “hello buttholio,” to which Kiberphant0m responded positively with an acknowledgment of “wsg,” standing for “what’s good.” On Nov. 1, Dstat’s site dstat[.]cc was confiscated as part of “Operation PowerOFF,” a multinational law enforcement operation against DDoS services.
The data from Flashpoint displays that @kiberphant0m informed a fellow member of Dstat on April 10, 2024, that their alternate Telegram username was “@reverseshell,” and did the same two weeks later in The Jacuzzi Telegram chat. The Telegram ID for this account is 5408575119.
Back on Nov. 15, 2022, @reverseshell informed another member of a Telegram channel named Cecilio Chat that they were a soldier in the U.S. Army. This user also posted the following image of an individual dressed in military fatigues, with a camouflaged backpack nearby:

Kiberphant0m’s assumed alias ReverseShell published this image on the Telegram channel Cecilio Chat, on Nov. 15, 2022. Image: Flashpoint.
In September 2022, Reverseshell was caught up in an altercation with another member who had threatened to unleash a DDoS attack against Reverseshell’s Internet address. Following the attack as promised, Reverseshell retorted, “You all just struck military base contracted wifi.”
In a conversation from October 2022, Reverseshell was boasting about the rapidity of the servers they were utilizing and in response to a question from another member, mentioned that they were connecting to the Internet through South Korea Telecom.
Telegram chat logs preserved by Flashpoint reveal that on Aug. 23, 2022, Reverseshell bragged about using automated tools to discover valid logins for Internet servers that they resold to others.
“I’ve accessed US gov servers with default credentials,” Reverseshell remarked, alluding to systems with easily guessable usernames and/or passwords. “Telecom control servers, machinery shops, Russian ISP servers, etc. I traded a few prominent companies for about $2-3k each. You can sell the access when you get a major SSH into a corporation.”
On July 29, 2023, Reverseshell shared a screenshot of a login page for a significant U.S. defense contractor, asserting that they had the credentials of an aerospace company to offer.
PROMAN AND VARS_SECC
Flashpoint detects that the Telegram ID 5408575119 has utilized various aliases since 2022, including Reverseshell and Proman557.
A search on the alias Proman557 on the cyber intelligence platform Intel 471 reveals that a hacker under the alias “Proman554” registered on Hackforums in September 2022, and in communications with other users Proman554 mentioned they could be reached at the Telegram account Buttholio.
Intel 471 also discovers that the moniker Proman557 is one of many aliases used by an individual on the Russian-language hacking forum Exploit in 2022 who peddled various Linux-based botnet malware.
Proman557 was eventually banned — supposedly for defrauding a fellow member out of $350 — and the Exploit moderator cautioned forum participants that Proman557 had previously registered under several other pseudonyms, including an account named “Vars_Secc.”
Thousands of comments made by Vars_Secc on Telegram over a span of two years indicate that this user divided their attention among online gaming, managing a DDoS botnet, and endorsing the sale or rental of their botnets to other users.
“I deploy ddos for multiple purposes not just to be a skid,” Vars_Secc declared. “Why do you assume I haven’t marketed my network?” They then proceeded to enumerate the most valuable attributes of their botnet:
-I deploy it to disrupt servers that ban me or irritate me
-I used to ddos particular games to retrieve my items since the data resets to when you joined
-I utilize it for server-side desync RCE (Remote Code Execution) vulnerabilities
-I use it at times for ransom
-I leverage it when bored as a form of amusement
Flashpoint reveals that in June 2023, Vars_Secc reacted to provocation from a fellow member in the Telegram channel SecHub who had threatened to expose their personal information to the federal government for a reward.
“Man I’ve been engaged in this activity for 4 years,” Vars_Secc responded casually. “I seriously doubt the government would shell out millions for data pertaining to some random individual managing a pointless ddos botnet and discovering a few vulnerabilities here and there.”
For several months in 2023, Vars_Secc was also an active participant in the Russian-language criminal forum XSS, where they marketed access to a U.S. government server for $2,000. However, Vars_Secc would be expelled from XSS after attempting to offer access to the Russian telecom giant Rostelecom. [In this instance, Vars_Secc violated the top rule for operating on a Russia-based criminal forum: Never proposition to hack or vend data pilfered from Russian entities or citizens].
On June 20, 2023, Vars_Secc initiated a sales post on the cybercrime forum Ramp 2.0 titled, “Selling US Gov Financial Access.”
“Server within the network, potential to pivot,” read Vars_Secc’s succinct sales pitch. “Has 3-5 subroutes connected to it. Price $1,250. Telegram: Vars_Secc.”
Vars_Secc also leveraged Ramp in June 2023 to market access to a “Vietnam government Internet Network Information Center.”
”Selling access server allocated within the network,” wrote Vars_Secc. “Contains some data. $500.”
BUG BOUNTIES
The Vars_Secc persona claimed on Telegram in May 2023 that they generated income by reporting software faults to HackerOne, a company that assists tech firms in managing reports about security vulnerabilities in their products and services. Particularly, Vars_Secc stated that they had received financial remuneration or “bug bounties” from reddit.com, the United States Department of Defense, and Coinbase, among 30 others.
“I earn through bug bounties, it’s quite straightforward,” Vars_Secc mentioned when queried about their profession. “That’s why I have submitted over 30 bug bounty reports on HackerOne.”
A month before that, Vars_Secc mentioned they had identified a vulnerability in reddit.com.
“I contaminated Reddit’s cache,” they elaborated. “I’m intending to exploit it further, then report it to reddit.”
KrebsOnSecurity reached out to HackerOne, which expressed its intent to investigate the claims. This article will be updated if they provide a response.
The Vars_Secc telegram handle also purported ownership of the BreachForums member “Boxfan,” and Intel 471 indicates that Boxfan’s initial posts on the forum included the Vars_Secc Telegram account in their signature. In the mostIn a recent post on BreachForums in January 2024, Boxfan revealed a security flaw they discovered in Naver, the top-rated search engine in South Korea (as per statista.com). Boxfan’s remarks hint at their strong disdain for the South Korean culture.
Boxfan expressed on BreachForums, “Enjoy exploiting this vulnerability,” along with sharing a lengthy piece of code to exhibit the flaw. “Curse you South Korea and your biased perspectives. No one appreciates your trashy kpop, you malevolent individuals. Congratulations to anyone who can extract this DB [database]. I’m not in the mood to do it, so I’ll share it here instead.”
The many personas linked to Kiberphant0m strongly indicate they are or were recently a soldier in the U.S. Army deployed in South Korea. Kiberphant0m’s alternative identities never made any mention of their military status, unit, or area of expertise.
However, it seems likely that the Army recognized Kiberphant0m’s proficiency in computers and networks. According to the U.S. Army’s official website, most of its troops in South Korea are positioned within the Eighth Army, which contains a specialized cyber operations division dedicated to thwarting cyber threats.
On April 1, 2023, Vars_Secc shared a screenshot of the National Security Agency’s website in a public Telegram chat channel. The screenshot indicated that the visitor had recently submitted an application for some position at the NSA.

A screenshot shared by Vars_Secc on Telegram on April 1, 2023, hinting at a job application at the National Security Agency.
Requests for comment from the NSA are yet to receive a response.
When contacted via Telegram, Kiberphant0m admitted that KrebsOnSecurity had managed to uncover their previous aliases.
“I noticed you traced back the IP, unbelievable,” replied Kiberphant0m. “You actually dug up my old pseudonyms LOL.”
Kiberphant0m refuted any ties to the U.S. Army or past presence in South Korea, alleging that it was all part of an elaborate scheme to create a fictional identity. They called it an “incredible opsec maneuver.”
When questioned about the risk of being apprehended, Kiberphant0m dismissed the possibility.
“There’s no way I can be caught,” declared Kiberphant0m, declining to provide further explanations. “I don’t even reside in the USA, Mr. Krebs.”
Below is a conceptual map aimed at illustrating the connections between Kiberphant0m’s apparent aliases.
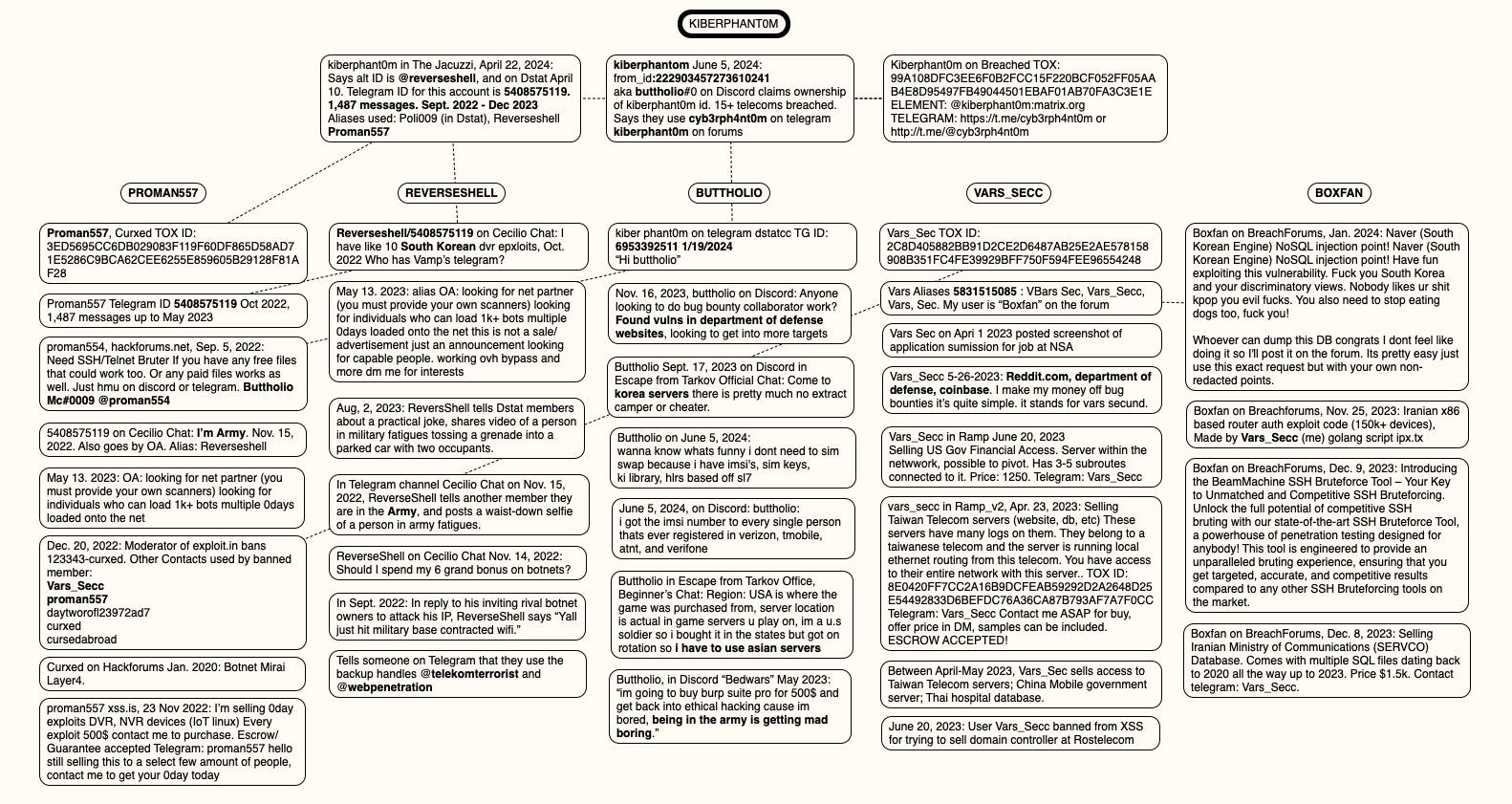
A conceptual map showing the links between the identities apparently used by Kiberphant0m. Click to expand.
KrebsOnSecurity wishes to express special gratitude to the security intelligence firm Unit 221B based in New York City for their assistance in assembling key elements of Kiberphant0m’s various identities.