
Fraudsters based in China who specialize in SMS scams are experiencing remarkable success converting stolen payment card information into digital wallets through renowned brands like Apple and Google. Previously, the group known as the “Smishing Triad” primarily masqueraded as toll road companies and delivery services. However, industry experts reveal that these criminal organizations are now directly aiming at clients of global banks while significantly expanding their cybercrime operations and support teams.

A photo depicting an iPhone device farm shared on Telegram by a member of the Smishing Triad. Image: Prodaft.
If you possess a mobile gadget, there’s a high likelihood that at some point in the past couple of years, you’ve received a message alerting you about an outstanding toll charge or a lost parcel supposedly from the United States Postal Service (USPS). Those who fall for the scam and click the link provided are redirected to a counterfeit USPS or toll road operator’s website that requests their payment card details.
The site then asserts that the user’s bank requires a “verification” of the transaction by sending a unique code via SMS. In actuality, the bank sends this code to the mobile number linked to the victim’s account as the scammers have tried to register that person’s card details to a digital wallet.
If the victim provides the one-time code, their card information is added to a new digital wallet set up on an Apple or Google device operated by the fraudsters. These phishing syndicates usually upload multiple stolen cards to digital wallets on a single Apple or Android device before selling these devices in bulk to scammers who utilize them for illicit online shopping and tap-to-pay transactions.
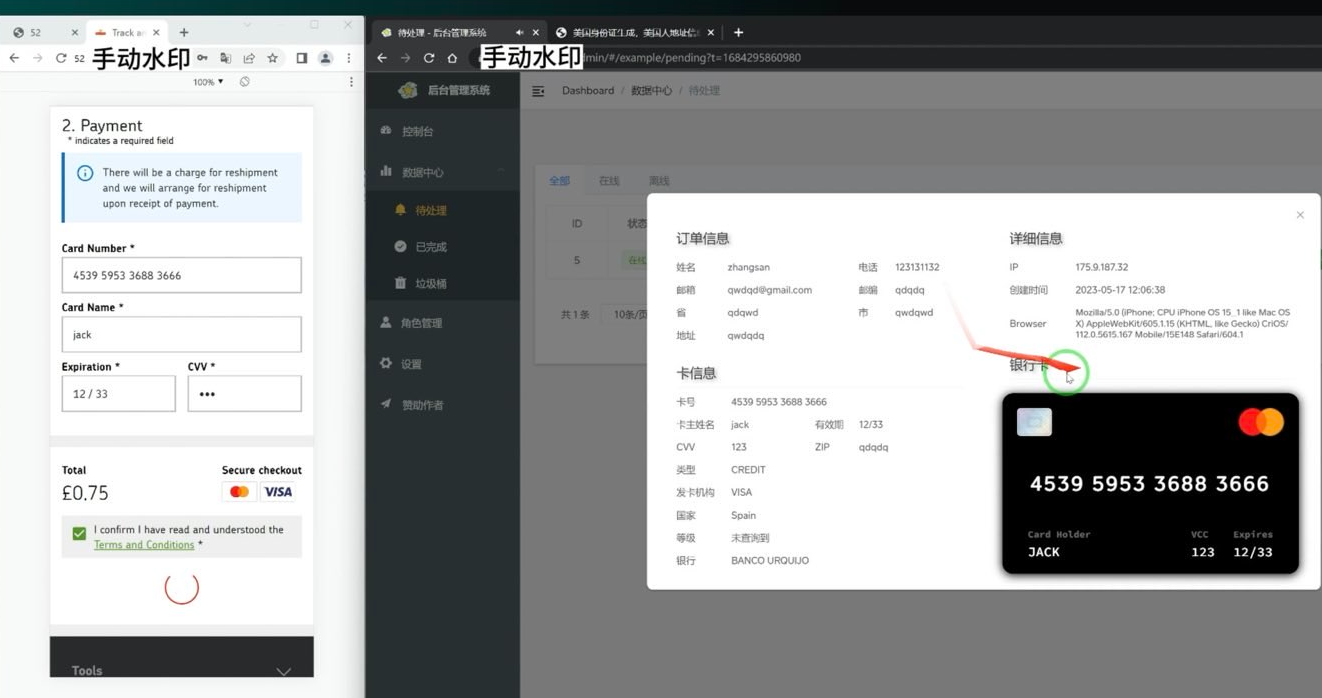
An overview of the administrative dashboard for a smishing toolkit. The left panel displays the (test) data entered on the phishing platform, whereas the right panel shows how the kit overlays the provided card number onto a payment card image. When this falsified card image is scanned into Apple or Google Pay by the phishing kit, it triggers the bank to deliver a one-time code. Image: Ford Merrill.
The nickname “Smishing Triad” was coined by Resecurity, which was one of the first to highlight in August 2023 about three distinct mobile phishing factions based in China that seemed to share infrastructure and unconventional phishing tactics. However, it’s somewhat misleading as the phishing baits distributed by these organizations are not conventional SMS or text messages.
Instead, they are dispatched via iMessage to Apple user devices and through RCS on Google Android devices. Consequently, these messages bypass traditional cellular networks entirely, ensuring nearly a 100 percent delivery rate (at least until Apple and Google bar the suspicious accounts).
In a publication issued on March 24, the Swiss cybersecurity intelligence firm Prodaft outlined the rapid technological advancements originating from the Smishing Triad. Prodaft described the group as a loosely connected consortium of Chinese phishing service providers with aliases like Darcula, Lighthouse, and the Xinxin Group.
Prodaft mentioned observing a notable transformation in the underground economy, particularly among Chinese-speaking cyber threats actors who have traditionally operated more discreetly compared to their Russian-speaking counterparts.
“Chinese-speaking actors are introducing inventive and cost-efficient systems that enable them to target larger audiences with sophisticated services,” Prodaft elaborated. “Their strategic approach signifies a new era in underground commercial practices, emphasizing scalability and efficiency in cybercrime activities.”
A recent analysis from experts at the cybersecurity company SilentPush reveals that members of the Smishing Triad have branched out to offering phishing kits aimed at clients of globally recognized financial institutions like CitiGroup, MasterCard, PayPal, Stripe, and Visa, as well as banks across Canada, Latin America, Australia, and the wider Asia-Pacific region.

Phishing traps from the Smishing Triad impersonating PayPal. Image: SilentPush.
SilentPush uncovered that the Smishing Triad now imitates renowned brands in various industries from at least 121 countries and a multitude of sectors, including postal services, logistics, telecommunications, transport, finance, retail, and public services.
According to SilentPush, the domains utilized by the Smishing Triad are frequently swapped, with around 25,000 phishing domains operational during any 8-day period, most of which are hosted by two Chinese service providers: Tencent (AS132203) and Alibaba (AS45102).
“Considering that [the] Smishing Triad targets almost two-thirds of all nations globally, it’s plausible to state that they are essentially aiming at every country with modern infrastructure except for Iran, North Korea, and Russia,” as stated by SilentPush. “While we have observed potential targeting in Russia (such as domains incorporating their country codes), there’s no compelling evidence to suggest that Russia is a primary focus. Interestingly, although these are Chinese threat actors, we have
We have observed instances of targeting aimed at Macau and Hong Kong, both special administrative territories of China.”
Zach Edwards from SilentPush mentioned that his team discovered a vulnerability that exposed data from one of the Smishing Triad’s phishing pages. This revealed the number of daily visits to each site across numerous active phishing domains at that time. Using this data, SilentPush estimates that these phishing pages received significantly more than a million visits over a period of 20 days.
The report points out that the Smishing Triad claims to have “300+ front desk staff worldwide” engaged in one of their popular phishing kits called Lighthouse. This staff is mainly utilized to support various aspects of the group’s fraudulent activities and cash-out schemes.
The members of the Smishing Triad operate their own sales channels in Chinese on Telegram, regularly sharing videos and photos of their staff working diligently. Some of these images show vast arrays of phones used to send phishing messages, with human operators positioned right in front of them, ready to receive any time-critical one-time codes.
As mentioned in a story from February How Phished Data Turns Into Apple and Google Wallets, one of their cash-out schemes involves an Android app named Z-NFC. This app can transmit a valid NFC transaction from a compromised digital wallet to anywhere globally. For a monthly subscription fee of $500, customers can utilize their phone at any payment terminal accepting Apple or Google Pay, with the app sending an NFC transaction over the Internet from a stolen wallet on a phone based in China.
Chinese citizens were recently apprehended while attempting to use these NFC apps to buy high-end electronic devices in Singapore. Furthermore, in the United States, law enforcement in California and Tennessee arrested Chinese nationals who were accused of using NFC apps to fraudulently obtain gift cards from retail stores.
The researchers at Prodaft mentioned that they came across an undocumented backend management panel for Lucid, a smishing-as-a-service operation linked to the XinXin Group. This panel contained victim data indicating that the smishing campaigns maintain an average success rate of around five percent, with certain domains receiving more than 500 visits a week.
“In one specific case, a single phishing website harvested 30 credit card records from 550 victim interactions over a span of 7 days,” Prodaft stated.
Prodaft’s report elaborates on how the Smishing Triad has achieved such success in sending their fraudulent messages. For instance, one phishing vendor seems to be sending messages using multiple Android device emulators operating simultaneously on a single machine.
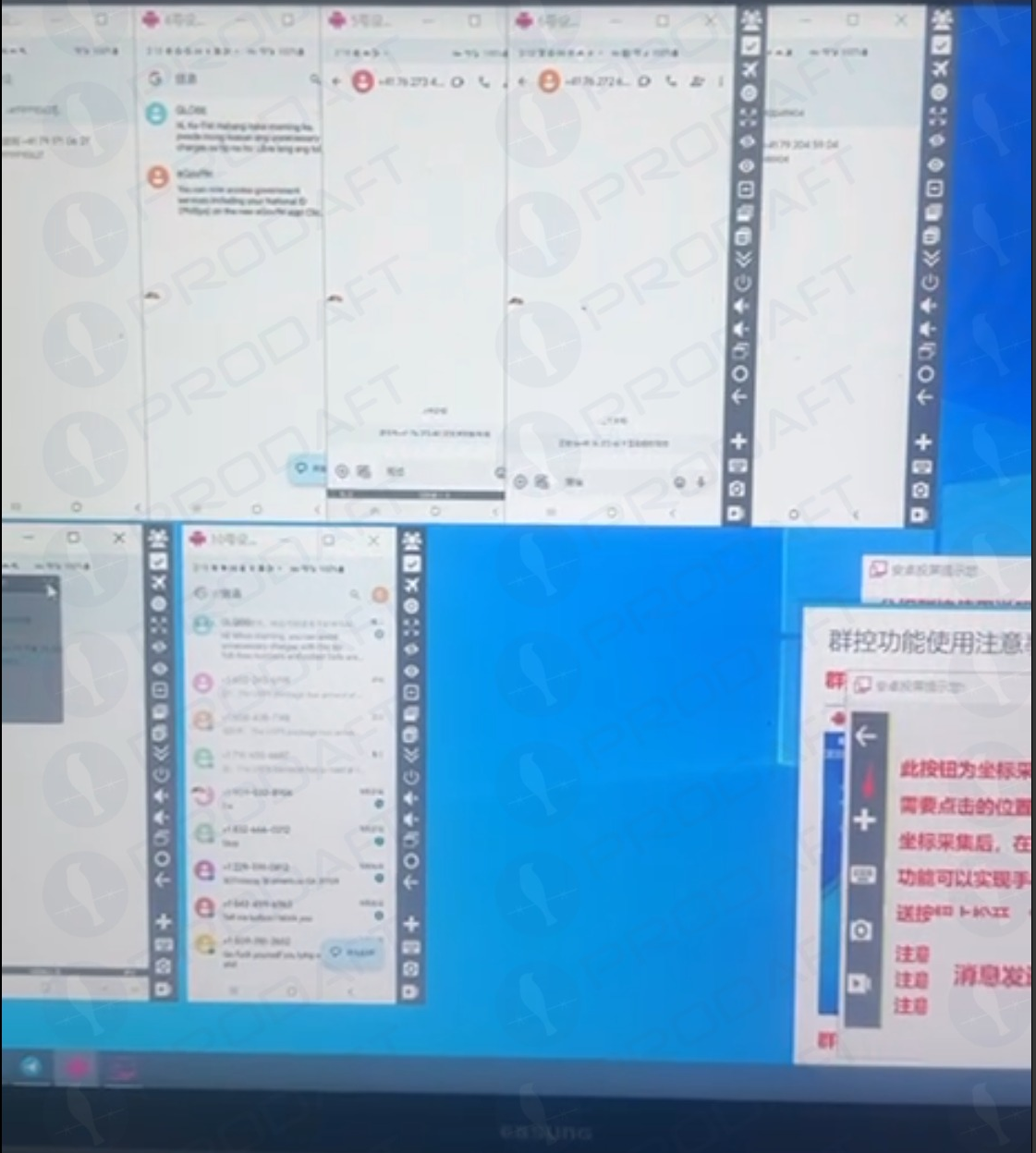
Phishers using multiple virtualized Android devices to orchestrate and distribute RCS-based scam campaigns. Image: Prodaft.
According to Prodaft, the threat actors initially obtain phone numbers through various methods such as data breaches, open-source intelligence, or buying lists from underground markets. They then exploit weaknesses in sender ID validation within messaging platforms.
“To tackle iMessage, this involves generating temporary Apple IDs with fake display names, while RCS abuse leverages inconsistencies in sender verification by carriers,” Prodaft explained. “Message delivery is automated through platforms using VoIP numbers or compromised credentials, often implemented in precisely timed multi-wave campaigns to maximize effectiveness.
Furthermore, the phishing links included in these messages use time-restricted single-use URLs that expire or redirect based on device fingerprinting to avoid security scrutiny, they discovered.
“The attackers are favored economically, as neither RCS nor iMessage messages incur costs per message like traditional SMS, allowing high-volume campaigns at minimal operating expenses,” Prodaft added. “The convergence in templates, target groups, and strategies among these platforms highlights a unified threat environment, with Chinese-speaking actors leading innovation in the underground economy. Their ability to expand operations globally and their evasion techniques present significant obstacles to cybersecurity defenses.”
Ford Merrill is involved in security research at SecAlliance, a CSIS Security Group company. Merrill noted that he has seen at least one video showcasing a Windows binary that wraps a Chrome executable, capable of loading target phone numbers and broadcasting messages via RCS, iMessage, Amazon, Instagram, Facebook, and WhatsApp.
“The indications we have suggest that a single device can dispatch around 100 messages per second,” Merrill mentioned. “We also believe that there is a potential to obtain SIM cards specific to certain countries in bulk, which allows them to register various online accounts needing validation with specific country codes, and make these SIM cards accessible to the devices for extended periods, hindering services dependent on phone number validation or SIM card presence on a mobile network.”
Experts argue that this growing trend of card fraud persists because many financial institutions still rely on sending one-time codes via SMS for confirming card enrollment in mobile wallets by Apple or Google. KrebsOnSecurity interviewed several security officials at non-U.S. financial institutions who preferred not to be named as they were unauthorized to speak to the media. These banks have now moved away from SMS-based one-time codes and now require customers to log in to the bank’s mobile app before they can connect their card to a digital wallet.







