Blog
More_Eggs Malware Disguised as CVs Targets Talent Scouts in Email Scam
June 10, 2024PressEmail Scam / Cybercrime Cyber experts have identified a mail scam propagating the More_Eggs malware by presenting it...
Comparison of Crowdstrike and Trellix (2024): Notable Contrasts
Businesses face significant concerns regarding security threats, which can lead to various negative outcomes such as breaches in customer data...
The AI Lab at Lander & Rogers tackles “three or four” prototypes daily
Inside the law firm Lander & Rogers, an AI Lab is actively developing and testing "three or four" prototypes each...
Apple AI: M1 Mac or iPad Essential
It is likely due to the significant computational demands of genAI requests that users will need cutting-edge M1 Mac or...
Cisco Expands on the CNAPP Movement to Safeguard and Defend the Cloud Native Application Estate
With the aim of enhancing flexibility, scalability, and rate of innovation, contemporary enterprises are constructing and embracing cloud native applications...
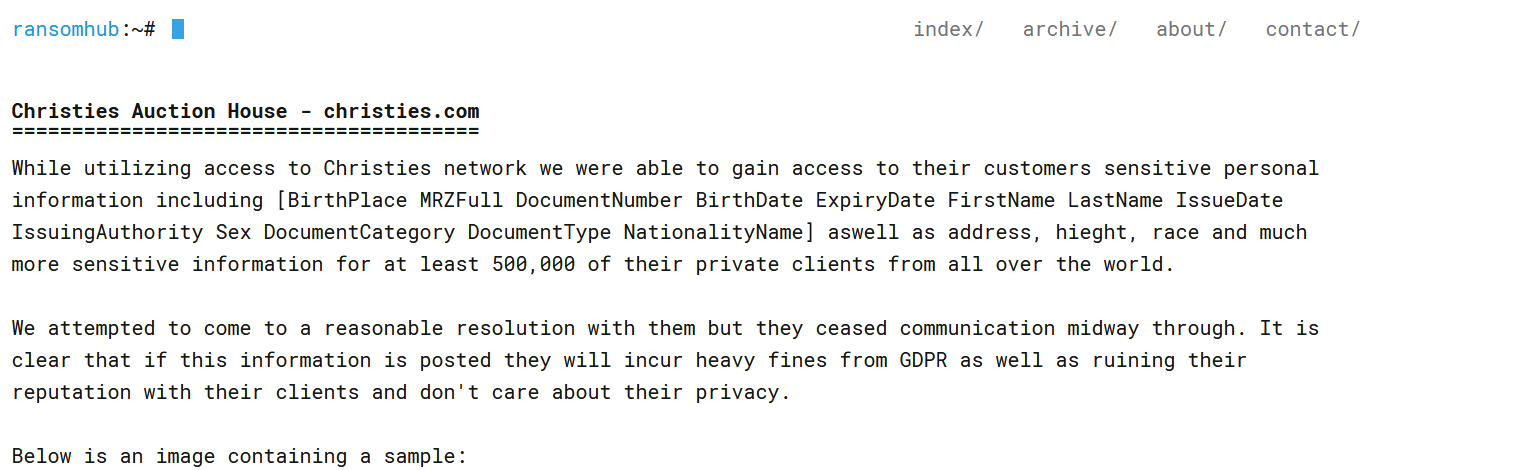
Christie’s data breach affected 45,798 people
Christie’s data breach impacted 45,798 individuals Pierluigi Paganini June 10, 2024 Auction house Christie’s disclosed that the data breach caused...
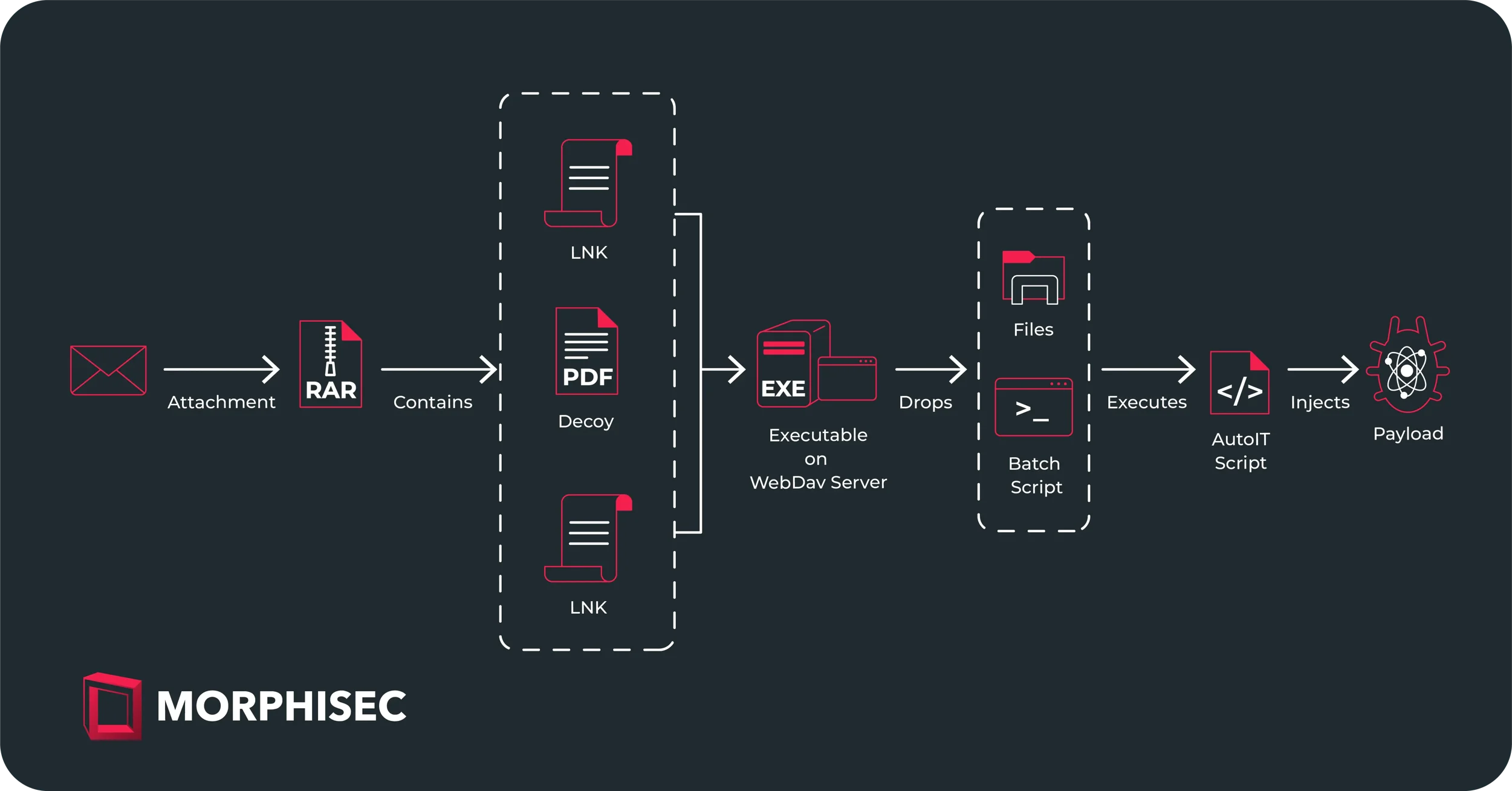
Adhesive Werewolf targets the aeronautics sector in Russia and Belarus
Adhesive Werewolf goes after the aviation field in Russia and Belarus Pierluigi Paganini June 10, 2024 Morphisec experts witnessed a...
Using Mistyped Web Addresses – Schneier on Security
Exploiting Mistyped URLs Engaging study: “Hyperlink Hijacking: Exploiting Incorrect URL Links to Fake Domains“: Summary: Internet users often rush when...
Microsoft introduces opt-in for Windows Recall after negative feedback on privacy and security
Furthermore, users will be required to provide a "proof of presence" to search in Recall or view a timeline. Moreover,...
Cybersecurity Continuing Professional Education: Unravelling the What, Why & How
Jun 10, 2024The Hacker NewsCybersecurity / Exposure Management Remaining Sharp: Demystifying Cybersecurity CPEs Perhaps more than other professional areas, cybersecurity...
Warning: Microsoft Alerts Potential Exploitation of Azure Service Tags by Hackers
Jun 10, 2024NewsroomCloud Security / Vulnerability Microsoft cautions regarding the potential exploitation of Azure Service Tags by unauthorized users to...
Google Censor Influence Efforts Linked to China, Indonesia, and Russia
Google disclosed the removal of 1,320 YouTube channels and 1,177 Blogger blogs in an effort to combat coordinated influence activities...
Differences Between Crowdstrike and Trellix (2024)
Businesses face significant challenges when it comes to security threats, which can result in various negative outcomes like customer data...
Advantages of Implementing a Network Security Protocol in Your Business
Given the escalating intricacy of cybersecurity threats and data breaches, firms need to establish strong measures to safeguard their networks....









.jpeg)