BlastRADIUS Vulnerability Discovered in RADIUS Protocol Utilized in Corporate Networks and Cloud Environments

A weakness in the RADIUS protocol has been brought to light by cybersecurity experts, known as BlastRADIUS. Despite no active exploitation by malicious actors, a call has been made by the team to update every RADIUS server as a precautionary measure.
Understanding the RADIUS protocol
RADIUS, which stands for Remote Authentication Dial-In User Service, is a networking standard that delivers centralized authentication, authorization, and accounting for users connecting to a network service. It sees widespread usage among internet service providers and businesses for various network devices such as switches, routers, access servers, firewalls, and VPN products.
Exploring a BlastRADIUS incident
In a BlastRADIUS exploit, the malefactor intercepts network communications between a client (e.g., a router) and the RADIUS server. By altering the MD5 hashing algorithm, the attacker can manipulate an Access-Denied network message to appear as Access-Accept, granting unauthorized access to the client device without proper credentials.
Although MD5 is recognized for its weaknesses which allow for collisions or hash reversal, researchers claim that the BlastRADIUS incident is a more intricate process compared to a conventional MD5 collision attack and is notable for its speed and scale. This marks the first successful demonstration of an MD5 exploit against the RADIUS protocol.
Discovery of the BlastFLARE vulnerability
A collaborative team comprising researchers from Boston University, Cloudflare, BastionZero, Microsoft Research, Centrum Wiskunde & Informatica, and the University of California, San Diego uncovered the BlastRADIUS weakness in February. The team promptly informed Alan DeKok, the CEO of InkBridge Networks and an expert in RADIUS technology.
Now known as CVE-2024-3596 and VU#456537, the BlastRADIUS flaw originates from a fundamental design defect in the RADIUS protocol, as stated in a security update by FreeRADIUS, a RADIUS server managed by DeKok. Consequently, this vulnerability extends beyond individual products or suppliers.
EXPLORE: Implementing FreeRADIUS for SSH authentication
DeKok mentioned in a press statement that network personnel will need to install firmware updates and reconfigure a vast array of devices like switches, routers, GGSN, BNG, and VPN concentrators worldwide. There is a predicted surge in RADIUS security-related discussions and actions in the following weeks.
Impact of the BlastRADIUS weakness
Research indicates that RADIUS implementations using PAP, CHAP, MS-CHAP, and RADIUS/UDP over the internet are susceptible to the BlastRADIUS flaw. This poses a threat to ISPs, cloud identity vendors, telecommunications providers, and businesses with internal networks, particularly those utilizing RADIUS for administrative logins.
While individual users operating from home are not directly at risk, they depend on their ISPs addressing the BlastRADIUS issue to prevent their traffic from being diverted to a compromised system.
Organizations employing PSEC, TLS, or 802.1X protocols, as well as services like eduroam or OpenRoaming, are considered secure.
The Mechanics of a BlastRADIUS assault
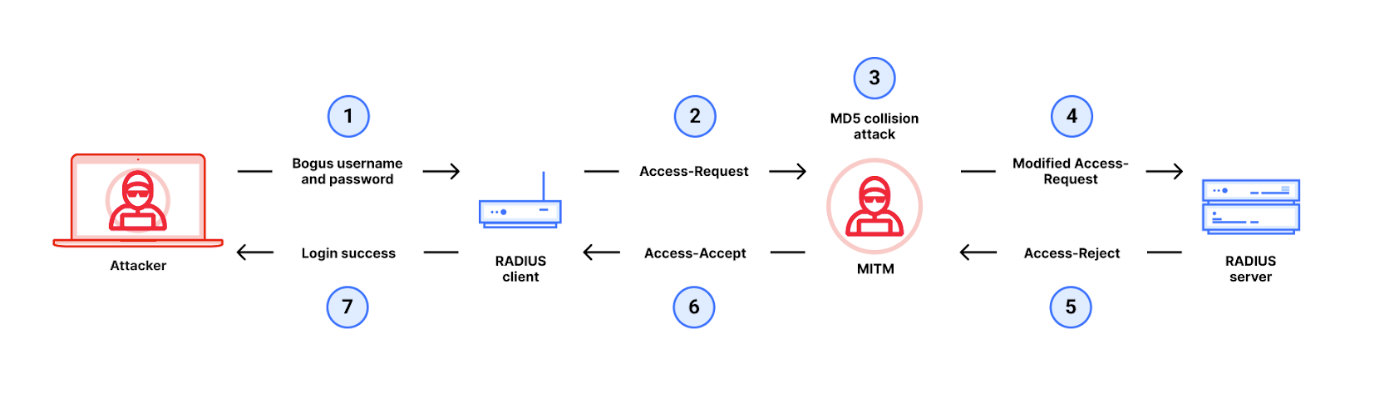
Exploitation of this vulnerability involves executing a man-in-the-middle attack during the RADIUS authentication procedure. This hinges on a crucial aspect of the RADIUS protocol where some Access-Request packets lack authentication and integrity validation.
An attacker initiates the assault by trying to log in with wrong credentials, generating an Access-Request message sent to the server. This message includes a Request Authenticator, a 16-byte value created through MD5 hashing.
The Request Authenticator is designed for the server to calculate its response along with a shared secret known only to the client and server. Upon receiving the response, the client deciphers the message using the Request Authenticator and shared secret, verifying its legitimacy from the trusted server.
In a BlastRADIUS attack, the intruder alters the Access-Request message pre-server arrival using an MD5 collision tactic. By embedding extraneous data into the Access-Request message, the Access-Denied response from the server includes this data. The attacker further manipulates the response to appear valid to the client as an Access-Accept message, effectively gaining unauthorized entry.
Cloudflare researchers, in their study, executed the attack on RADIUS equipment within a five-minute timeout window. Nevertheless, advanced attackers with robust computational capabilities might reduce this time frame significantly, possibly between 30 and 60 seconds,
The default timeout period for numerous RADIUS devices is as follows.
“The core of the assault lies in the fact that in numerous instances, Access-Request packets lack any verification or integrity validations,” a report by InkBridge Networks states. “This allows an attacker to execute a chosen prefix attack, permitting them to alter the Access-Request to substitute a legitimate response with a response of their choice.”
You can access a comprehensive technical explanation and demonstration of a BlastRADIUS attack in this PDF.
How simple is it for a hacker to exploit the BlastRADIUS vulnerability?
Though the BlastRADIUS weakness is wide-reaching, exploiting it is not straightforward; the attacker must possess the ability to intercept, modify, block, and analyze incoming and outgoing network packets, with no accessible exploit tool. Moreover, the attacker must already have network access, which might be gained by leveraging a scenario where RADIUS/UDP is transmitted over the public internet or by breaching a section of the corporate network.
Furthermore, the attacker should possess substantial financial backing, given the substantial cloud computing resources needed to carry out each BlastRADIUS assault. InkBridge Networks notes in its BlastRADIUS FAQs that such expenditures would be insignificant for nation-states interested in targeting specific users.
How organizations can defend themselves from a BlastRADIUS attack
The security experts have outlined the following suggestions for organizations utilizing the RADIUS protocol:
- Implement the most recent updates provided by the vendor for all RADIUS servers and clients. Updates have been rolled out to ensure that Message-Authenticator attributes are always dispatched and necessary for requests and responses. An updated version of FreeRADIUS can be found here.
- Avoid attempting to update all RADIUS devices simultaneously to prevent errors. It is preferable to focus on upgrading the RADIUS servers first.
- Deliberate on utilizing InkBridge Networks’ validation tools that evaluate a system’s vulnerability to BlastRADIUS and other network infrastructure concerns.
More comprehensive guidance for system administrators is accessible on the FreeRADIUS website.



