
With the progression of technology, ensuring the protection of computer systems, networks, and applications is becoming increasingly crucial. One method that security experts can utilize to evaluate the security stance of an entire digital environment is through performing penetration testing, or pen testing for short.
Penetration testing is the sanctioned replication of a genuine cyber assault. This enables organizations to assess the strength of their security systems and pinpoint any existing weaknesses or vulnerabilities.
As indicated by studies by SNS Insider, the penetration testing market is predicted to achieve a value of $6.98 billion by 2032, mainly due to the continuous evolution of cybersecurity threats. As a core practice for evaluating an organization’s security stance, pentests require both the proficiency of seasoned security professionals and the utilization of robust penetration testing utilities.
Given the abundance of these utilities, I have compiled a list of the best penetration assessment tools currently available along with their characteristics, advantages, and drawbacks.
Comparison table of Penetration Assessment Software
Here is a feature overview of our chosen pen assessment tools and how they compare with each other.
| Compliance verifications | Quantity of tests included | Open-source / cloud-based | Documentation and reporting | Initial cost | |
|---|---|---|---|---|---|
| Astra | Yes | 8,000+ | Cloud-based | Yes | $1,999 per year, one target |
| Acunetix | No | 7,000+ | Cloud-based | Yes | Contact for quote. |
| Intruder | Yes | Not specified | Cloud-based | Yes | $157 per month, one application |
| Metasploit | Yes | 1,500+ | Both | No | Contact for quote. |
| Core Impact | Yes | Not specified | Cloud-based | Yes | $9,450 per user, user per year. |
| Kali Linux | Yes | Not specified | Open-source | Yes | Completely free |
| Wire Shark | No | Not specified | Open-source | Yes | Completely free |
| SQL Map | No | Not specified | Open-source | Yes | Completely free |
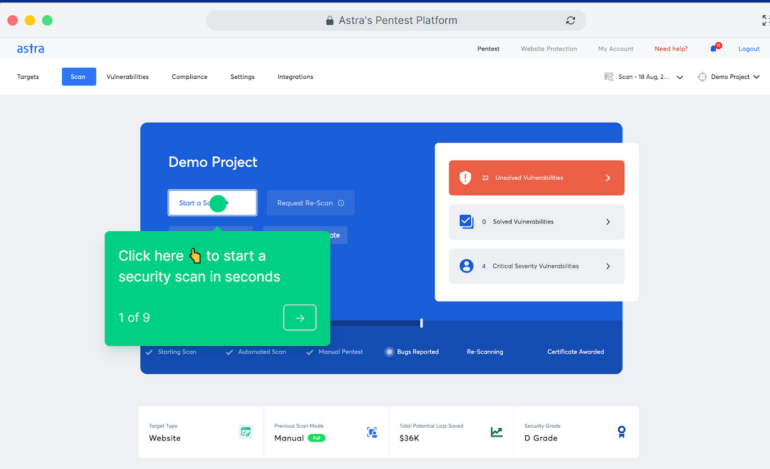
Astra: Ideal for diverse infrastructure

Astra serves as a tool for conducting penetration tests, offering a blend of manual and automated testing functionality for applications, networks, API, and blockchain. With support for over 8,000 tests, this tool aids security professionals in identifying vulnerabilities within systems. Astra covers various penetration testing types, including web application pentesting, cloud security pentesting, and mobile application pentesting.
Functioning as a thorough penetration testing solution, Astra encompasses numerous tests that support organizations in meeting compliance standards. It can verify compliance with standards such as SOC2, GDPR, and ISO 27001. Moreover, the Astra tool seamlessly integrates with GitLab, Jira, and Slack, embedding security into continuous integration/continuous deployment (CI/CD) pipelines.
My Reasoning for Choosing Astra
I opted for Astra due to its Enterprise Web App subscription, which caters to diverse infrastructural needs. It is versatile, supporting web, mobile, cloud, and network infrastructures and providing multiple targets across various asset categories. Astra’s offering of over 8,000 tests and its extensive integration capabilities with other popular software were additional reasons for my choice.
Pricing Details
Astra’s pricing is segmented into web application, mobile application, and AWS cloud security, each with distinct pricing structures.
- Web application: Scanner – $1,999/year, Pentest – $5,999/year, Enterprise – $9,999/year.
- Mobile application: Pentest – $2,499/year and Enterprise – $3,999/year.
- AWS cloud security: Offers Basic and Elite plans, each requiring users to engage with the sales team for a custom quote.
Notable Features
- Encompasses over 8,000 scanning tests.
- Covers all necessary tests for ISO 27001, HIPAA, SOC2, and GDPR compliance.
- Seamless integration with GitLab, GitHub, Slack, and Jira.
- Supports scanning for PWA/SPAs applications.
- Accessible support via Slack and Microsoft Teams.
Integration Points
- Capable of integrating with Slack workspaces.
- Integration compatibility with Jira.
- Integration capabilities with GitHub.
- Compatibility with GitLab.
- Integrates with Azure.
- Supports integration with CircleCI.
Pros and Cons of Astra
| Benefits | Drawbacks |
|---|---|
| Facilitates the provision of publicly verifiable pentest certificates, which can be shared with users. | The purported free trial incurs a cost of $1 per day. |
| Boasts extensive testing coverage (over 8,000 tests). | Support via Slack and MS Teams is only accessible under the Enterprise plan. |
| Employs AI/ML for automated testing. | |
| Supports assistance via Slack or Microsoft Teams. |
Acunetix: Optimal for Automating Penetration Tests

Invicti’s Acunetix stands out as a robust web application penetration testing tool. Offering an array of scanning tools, this solution enables penetration testing teams to swiftly identify over 7,000 web application vulnerabilities and
Supply an in-depth overview of the vulnerability range.
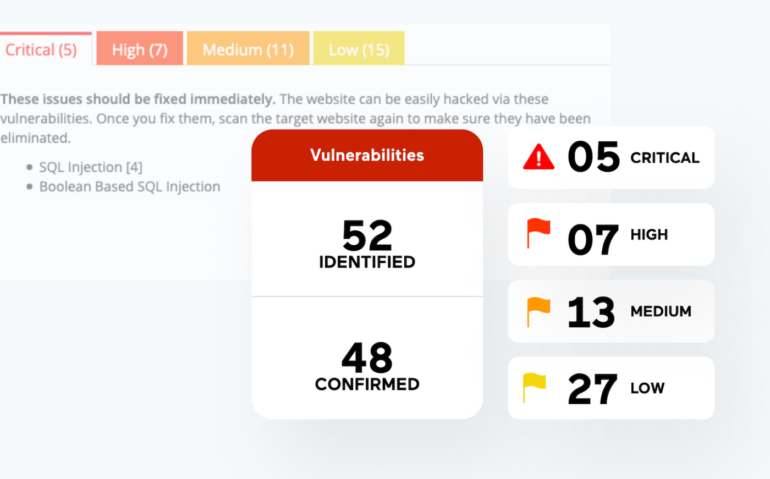
Some of the prominent vulnerabilities that Acunetix can identify encompass Cross-Site Scripting (XSS), SQL injections, publicly available databases, off-band vulnerabilities, and configuration errors.
There is a dashboard within Acunetix that can categorize vulnerabilities into various levels such as critical, high, medium, and low. This software is coded in C++ and is compatible with Microsoft Windows, Linux, macOS, and cloud platforms.
The Reason for Selecting Acunetix
I prefer Acunetix for enterprises seeking automated penetration testing. It facilitates scheduled or routine application scans, incorporates over 7,000 vulnerability assessments, and yields valuable insights even before completing a scan. It seems like an ideal solution for businesses desiring an uncomplicated penetration testing tool that saves time while maintaining robust security measures.
Pricing Information
Kindly reach out to Acunetix for a price estimate.
Characteristics
- Arrangement of vulnerabilities based on severity.
- Support for over 7,000 vulnerabilities in web applications.
- Adherence to the OWASP Top 10 standards for web developers and application security.
- Capability to schedule scans.
- Integration compatibility with issue-tracking platforms like Jira and GitLab.
Interconnections
- Jira.
- Azure DevOps.
- GitHub.
- GitLab.
- Bugzilla.
- Mantis.
Merits and Drawbacks of Acunetix
| Merits | Drawbacks |
|---|---|
| Vulnerabilities detected are organized by level of severity. | Lacks transparent pricing details for users. |
| Enables reporting and documentation. | Does not offer a free trial option. |
| Extensive coverage with over 7,000 vulnerability tests. | |
| Users can schedule single or recurrent scans. | |
| Capability to concurrently scan multiple environments. |
Attributes
- Cloud-based vulnerability scanning.
- Web-focused vulnerability scanning.
- API-specific vulnerability scanning.
- Features for compliance and reporting.
- Internal and external vulnerability scanning functionalities.
Connectivity
- Amazon Web Services (AWS).
- Drata.
- Jira.
- GitHub.
- GitLab.
- Google Cloud.
Merits and Drawbacks of Intruder
| Merits | Drawbacks |
|---|---|
| Offers a complimentary 14-day trial period. | Does not specify the extent of test coverage. |
| New users can easily start with the tool due to the availability of a demo. | The 14-day free trial is exclusive to the Pro plan. |
| Automatically creates compliance reports. |
Attributes
- Remote API integrations.
- Automated brute forcing of credentials.
- Capability for automated report generation.
- Sequencing of tasks for custom automated workflows.
Functionality connections
- InsightVM.
- Python.
- Core Impact.
- Burp Suite.
- Project Sonar.
- Nexpose.
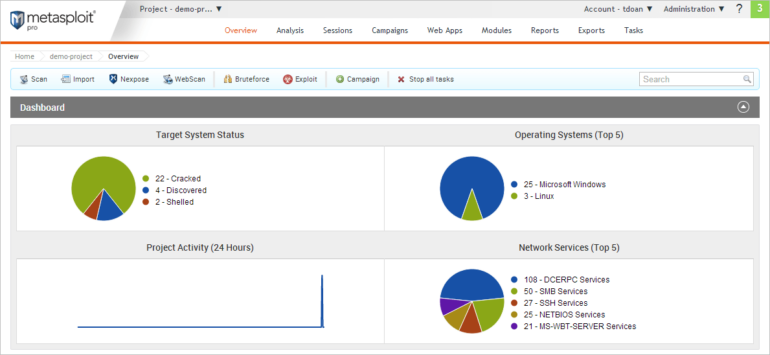
Metasploit advantages and disadvantages
| Benefits | Drawbacks |
|---|---|
| Provides a complimentary 30-day trial period. | The Framework version is restricted in operation. |
| Employs an easy-to-use web interface. | The Github download and setup process might be challenging for inexperienced users. |
| Features a costless edition for developers and scholars. | |
| Accessible as open-source and commercial software. |
Core Impact: Most suitable for teamwork

Core Impact, now integrated into Fortra, stands as one of the eldest tools for penetration testing that have developed in line with the current necessities of a testing scenario. The application can aid in replicating attacks over endpoints, network structures, the web, and apps to reveal exploited weaknesses and offer recommendations for resolution.
Core Impact diminishes the necessity for manual configuration during setup and testing. Users can smoothly define the test range and adjust test parameters, leaving the rest to Core Impact. Furthermore, this tool can produce an attack visualization, providing users with a live update of attack actions during testing.
The reason for selecting Core Impact
I chose Core Impact for its noteworthy emphasis on communal testing. It allows several security analysts to interact with each other in the same session. This enables testing crews to effortlessly exchange discoveries and data, as well as distribute testing responsibilities more effectively. By promoting collaborative workspaces, Core Impact makes testing more effective and comprehensive.
Pricing structure
Core Impact provides three pricing options:
- Basic: Commences at $9,450/user annually.
- Pro: Commences at $12,600/user annually.
- Enterprise: Price estimate available upon request.
Characteristics
- Automated Rapid Penetration Tests (RPTs).
- Multi-vector testing capability encompassing network, client, and web.
- Validation of vulnerabilities from third-party scanning outcomes.
- Centralizes penetration testing, from data collection to reporting.
- Penetration testing covers network security, web application, IoT security, and cloud security.
Functionality connections
- Metasploit.
- Cobalt Strike.
- PowerShell.
- Empire.
- PlexTrac.
Core Impact advantages and disadvantages
| Benefits | Drawbacks |
|---|---|
| Utilizes automated wizards for discovery, testing, and reporting. | Pricing is exceedingly high. |
| Offer of a trial free of charge. | The trial does not specify the duration of the free trial period. |
| Provides a wider range of cybersecurity services. | |
| Fresh users have the option to experience the tool through a demonstration. |
Kali Linux: Ideal for technical individuals

An open-source penetration testing solution, Kali Linux operates on the Debian-based Linux distribution. The tool boasts advanced cross-platform capabilities supporting mobile, desktop, Docker, subsystems, virtual machines, and bare metal testing.
Professionals can easily tailor Kali to suit their testing scenarios due to its open-source nature. Extensive guidance is available on utilizing Kali’s metapackages to generate software editions for specific testing needs. Kali streamlines the tool setup process by incorporating an automated configuration system that fine-tunes the tool based on varying usage scenarios.
Why Kali Linux was Chosen
Kali Linux is the top choice for technical and seasoned penetration testers seeking a robust testing solution. It was purposely crafted for professional pentesters, providing a highly adaptable framework enabling them to construct custom software versions tailored to their requirements.
The upfront stance of Kali Linux, stating its alignment with veteran pentesters and adept Linux users as opposed to everyday consumers, is particularly commendable. This orientation allows their tool to be optimized for their chosen user base, rather than diluting the quality by catering to all users.
Pricing
It is freely available.
Specialties
- Metapackages for specialized tasks.
- Live USB Boot feature for convenient booting from a USB device.
- Support for over 600 penetration testing utilities.
- The open-source development model is accessible on GitHub.

Interconnections
- Amazon Web Services (AWS).
- Microsoft Azure.
- Digital Ocean.
- Linode.
Kali Linux pros and cons
| Merits | Drawbacks |
|---|---|
| Covers a broad range of versions. | Primarily suitable for proficient Linux users. |
| Accessible at no cost. | |
| Guides and resources are provided for beginners. | |
| Supports multiple languages. |
Wireshark: Optimal for Unix Operating System Users

Wireshark is proficient in analyzing an organization’s network protocol for potential threats. This versatile penetration testing utility offers live capture, offline capabilities, and VoIP analysis.
Operating as an open-source tool, Wireshark extends substantial support to users via documentation, webinars, and video tutorials. Users also benefit from decryption functionalities for various protocols like Kerberos, SSL/TLS, and WEP.
Reasons for Selecting Wireshark
I opted for Wireshark as the ideal choice for Unix OS users. Being free and open-source, Wireshark empowers users to examine network protocols in both broad and granular detail. Despite its technical complexity, the detailed documentation provided is beneficial for users looking to utilize Wireshark for their specific testing requirements.
Pricing
It can be used at no cost.
Characteristics
- Compatible with UNIX and Windows systems.
- Live packet data capture from network interfaces.
- Sorting and analyzing traffic streams using display filters.
- Supports offline operations and VoIP analysis.
Connections
- AirPcap.
- YR20 network capture hardware.
- Inside Products.
- C5 SIGMA.
Wireshark advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Freely available and open source. | Installation may require advanced technical knowledge. |
| Includes an object export feature for sharing test results. | Limited automation capabilities. |
| Allows decryption for various protocols. | |
| Comprehensive documentation for beginners. |
SQLMap: Ideal for identifying SQL injection breaches

SQLMap is a great penetration testing tool favored by enthusiasts of open-source software for identifying and exploiting SQL injections within applications. Penetration testers rely on this tool to breach databases and evaluate vulnerability levels.
Moreover, SQLMap features a testing engine that can conduct multiple SQL injection assaults concurrently, saving time during testing. Notable servers supported include Microsoft Access, IBM DB2, SQLite, and MySQL.
It is compatible with macOS, Linux, and Windows platforms.
Reasons to choose SQLMap
For enterprises seeking protection against SQL injection threats, I highly suggest considering SQLMap. This top-tier penetration testing solution automates the detection of SQL injections in diverse applications. It covers numerous injection methods and attacks, offering extensive support for various database management systems. SQLMap is free and boasts abundant online documentation.
Pricing
Free of charge
Characteristics
- Supports multiple SQL injection techniques.
- Automatically identifies password hash types.
- Enables password cracking via dictionary-based attacks.
- Capable of executing arbitrary commands and retrieving their outputs.
Connections
- Burp Suite.
- Metasploit.
- Nmap.
SQLMap advantages and disadvantages
| Advantages | Disadvantages |
|---|---|
| Covers various SQL injection techniques. | Suited for users comfortable with command-line interfaces. |
| Compatible with various database management systems like MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, and more. | |
| Offered at no cost. | |
| Comes with comprehensive documentation. |
Important characteristics to consider in penetration testing tools
Penetration testing solutions provide numerous features and applications depending on the user’s goals. Here are the key attributes of penetration testing tools.
Detection of Vulnerabilities
Identifying vulnerabilities and flaws in software applications, networks, and systems is known as vulnerability scanning. It is a common technique used in penetration testing to uncover potential weaknesses like outdated software versions, misconfigurations, and known security issues.
Mapping and Reconnaissance of Networks
Network mapping and reconnaissance involve gathering information and visually representing a network’s infrastructure and connected devices. Before launching attacks, hackers typically gather information about their targets.
In a similar fashion, penetration testing tools help with reconnaissance by mapping networks, identifying active hosts, and collecting information about the target infrastructure. This capability assists security professionals in comprehending the organization’s digital footprint and potential entry points for attackers.
Analysis of Traffic and Packet Capture
Some penetration testing tools can analyze network traffic and capture packets. This feature enables security professionals to monitor and inspect network communications, identify potential vulnerabilities, and detect any suspicious or malicious activities. By analyzing network traffic, organizations can gain valuable insights into the security posture of their systems.
Generation of Reports and Documentation
Effective communication of vulnerabilities and recommended mitigation strategies is crucial in the penetration testing process. Penetration testing tools include features for reporting and documentation to produce comprehensive reports detailing identified vulnerabilities, testing procedures, and recommendations for remedial actions. These reports aid in prioritizing security measures and validating compliance processes.
Customization Capabilities
Organizations have unique security requirements. These tools often provide customization options and extensibility features that allow security professionals to tailor the testing process to their specific needs. Customization empowers organizations to focus on their most critical assets and assess vulnerabilities specific to their environment.
Common inquiries about penetration testing
How does vulnerability scanning differ from penetration testing?
Vulnerability scanning identifies weaknesses or gaps in an organization’s computer network and reports them. On the other hand, penetration testing exposes system vulnerabilities and attempts to exploit them, evaluating the reaction of an organization’s security measures during an attack.
Conducted by ethical hackers and DevOps engineers, pen tests simulate real cyber attacks against an organization’s security posture. In contrast, IT departments typically conduct vulnerability scanning to pinpoint security weaknesses and offer actionable insights afterward.
While these two concepts overlap and diverge in various aspects, considerations such as scope, objectives, and costs must be taken into account. However, the brief overview above provides a comparison of these two cybersecurity strategies.
For a more detailed comparison, refer to our Vulnerability Scanning vs Penetration Testing feature.
How can penetration testing tools assist in evaluating network security?
Ethical hackers can perform a “network pen test,” a form of penetration testing that specifically targets an organization’s network infrastructure. By using pen test tools, organizations can witness firsthand how their network security systems defend against potential attacks by malicious actors.
Pen test tools can also highlight deficiencies or vulnerabilities within the network, such as firewall misconfigurations, outdated or buggy software, and unauthorized access, among others.
What are the constraints of penetration testing?
Although penetration tests can provide valuable insights into an organization’s security posture, they have certain limitations. Here are a few:
- Test results are limited by the scope of the pen test, which may exclude certain areas from evaluation.
- Unlike real attackers, pen tests are time-constrained.
- Pen tests can be costly and resource-intensive, serving as significant obstacles for smaller organizations with limited resources.
- Due to human involvement, pen testers may overlook vulnerabilities or make errors, resulting in incomplete findings.
Selecting the ideal penetration testing software for your business
Amidst the plethora of pen-testing tools available to security professionals, choosing the right software can be challenging. To aid in your selection, here are key factors to consider when choosing the best penetration testing software for your business’s unique requirements.
Define your pen testing objectives
Prior to the selection process, clearly outline your goals for conducting penetration testing. Establish what you aim to accomplish through the testing process, whether it is identifying vulnerabilities, evaluating the efficacy of security controls, or meeting regulatory compliance requirements.
Defining your goals will help narrow down software options that align with your specific needs. Our comparison table illustrates that certain tools are better suited for different scenarios.
Establish test scope and budget
While testing your entire system environment may seem ideal, the cost of testing the entire software ecosystem may suggest otherwise. Every organization has areas of high and low vulnerability, where high-risk points are susceptible to exploitation by malicious actors. These areas can include the application code base, configuration files, and operating systems.
Knowing the scope of the test in advance is crucial for planning a penetration testing budget and determining which pen test software to utilize.
Consider testing methodologies
Penetration testing can be conducted using various methodologies, such as black box, white box, or gray box testing. Evaluate the software’s ability to support the desired testing methodology. Some tools may specialize in specific testing types, so ensure that the software aligns with your preferred approach. Flexibility in supporting various testing strategies is essential. Stay tuned for more exciting updates. Thank you!
Different methodologies can bring advantages when diverse approaches are needed for various systems or situations.
Reflect on the simplicity and design of the user interface
One should evaluate the user-friendliness of the software and how intuitive its user interface is. Penetration testing comprises intricate procedures, hence opting for a tool that is easy to navigate and comprehend is crucial. A finely crafted user interface along with clear documentation can greatly enhance the user experience and boost productivity. While some of the shortlisted penetration testing tools provide both graphical and command-line interfaces, there are those that only cater to the command-line interface. Although both interfaces yield similar outcomes, advanced users might find the command-line interface more suitable compared to regular users.
Assess compatibility and integration possibilities
Evaluate the software’s compatibility with your existing IT setup. Ensure that the tool can seamlessly blend in with your systems, networks, and applications without causing any disruptions. Additionally, consider other compatibility factors like supported operating systems, databases, and programming languages of the software.
Furthermore, confirm if the tool can harmonize with your prevailing security solutions such as vulnerability management platforms or security information and event management systems.
SEE: SMB Security Pack (TechRepublic Premium)
Include testing of remote resources
Make sure that your organization’s penetration testing strategies incorporate remote resources and staff members. Companies with remote job roles often grant remote access to critical resources, which might act as a potential entryway for hackers due to inadequate security monitoring. It is essential to include remote resources lacking robust security monitoring systems in any penetration tests carried out. Excluding remote staff and resources from your pentests defeats the purpose of evaluating the overall security status of your IT infrastructure.
Methodology
In compiling our roster of top-notch penetration testing tools, extensive research was conducted by extracting data from official websites, product documentation, case studies, and user reviews on trustworthy third-party review platforms. The selection criteria considered comprised the core features and functionalities offered by the pen testing solution, the software’s community, its user base/popularity, user-friendliness, and the quality of documentation provided. These criteria played a pivotal role in our selection process for this review.
Luis Millares revised this article.


