
04 June 2024
An individual specializing in security recently forwarded me 122 gigabytes of information extracted from a multitude of Telegram channels. The data comprised of 1.7 thousand files with 2 billion lines and 361 million exclusive email addresses, out of which 151 million had not been previously identified in HIBP. I have integrated the data into Have I Been Pwned (HIBP) today as there are extensive quantities of previously undiscovered email addresses. From all the validations conducted, it is authenticated data. That’s the overarching outline; now, let’s delve into the specifics:
Telegram is a favored messaging service that enables quick creation of a “channel” for sharing content with interested individuals. Telegram characterizes its offering as straightforward, confidential, and secure, thus making it popular among those looking to anonymously distribute content, including data from breaches. Many of the breaches I’ve previously uploaded onto HIBP have been disseminated through Telegram due to the ease of publishing this category of data on the platform. Here’s how data typically appears on Telegram:
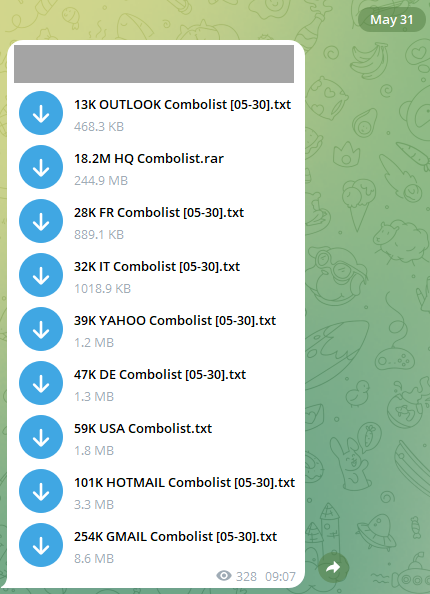
These collections are termed “combolists”, consisting of pairings of email addresses or usernames with passwords. This pairing is what is used for authentication across various services, often exploited by attackers in “credential stuffing” assaults where they endeavor to access accounts in bulk. The sample listed above simply breaks down the pairings according to their respective email service providers. For example, the concluding Gmail illustration encompasses over 250,000 rows similar to this:
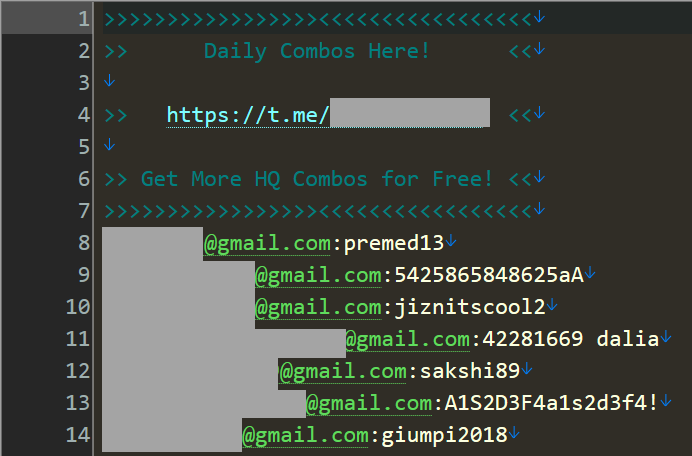
This is just one of numerous files scattered across various Telegram channels. The data provided to me last week originated from 518 diverse channels and tallied up to 1,748 distinct files resembling the one previously mentioned. Some files contain absolutely no data (0kb), while others are quite hefty with tens of millions of rows spanning multiple gigabytes. For instance, the largest file starts off like this:
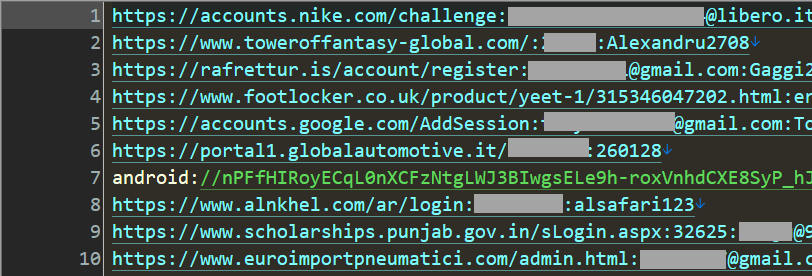
This closely resembles a potential outcome of information-stealing malware that captures credentials as they are entered on compromised machines. For example, the initial record seems to have been captured as someone sought to log into Nike. To gauge the validity of this data, just navigate to the Nike homepage and select the login link which will display the subsequent screen:
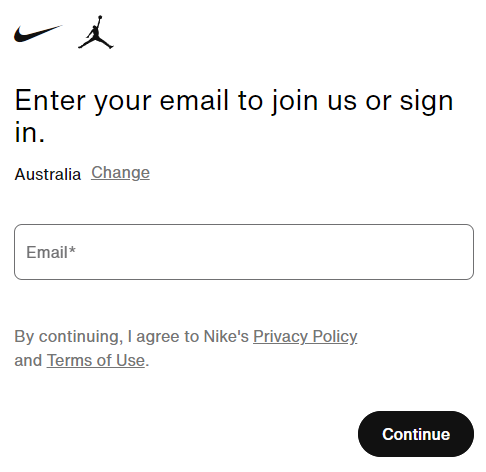
The identical page is shown to both existing and new subscribers, followed by distinct pages based on whether the email address is affiliated with an account (a classic enumeration feature). Randomize the keys to create a bogus email address and you’ll be directed to a registration form; however, input the address from the stolen data and you’ll observe a differential response:
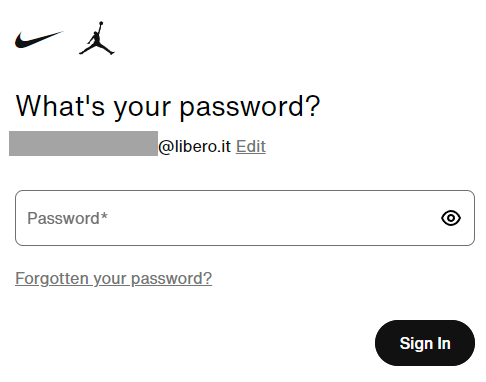
Since the email address is linked to an account, the system prompts for a password. I won’t test the password, as it would constitute unauthorized access. Nonetheless, the objective has already been accomplished: it’s been demonstrated that the address is associated with a Nike account. (Additionally, note that if the password didn’t function, it does not necessarily mean it was invalid at any point in the past; it could simply be inactive now.)
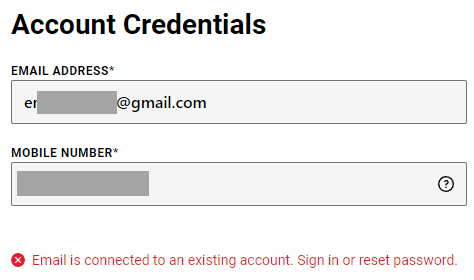
Footlocker attempts to be crafty in circumventing enumeration on password resets, but they will inform you through the registration page if the provided email address already exists:
Even the Italian tire vendor confirms the existence of the tested account:
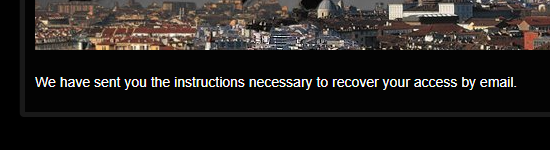
Repetitively, each service I assessed acknowledged the presence of the email address in the stolen data. However, were (or are) the passwords correct? Again, I won’t personally test those, but within HIBP, I have nearly 5 million subscribers who eagerly assist. Hence, I reached out to a few of the most recent ones, inquired if they could verify, and upon confirmation, forwarded their data.
Engaging with existing subscribers, I anticipated witnessing some recurrence in terms of their information being previously disclosed in breaches. For an individual already featured in 13 separate breaches on HIBP, this was their response:
Thank you Troy. This data was disclosed in earlier breaches.
Accurate, yet not novel; moreover, several of the breaches for this individual exhibited a resemblance to the structure of the breach under discussion today, involving combolists utilized in credential-stuffing operations. Likewise, another subscriber with a history in 7 prior breaches mentioned:
Yes, that does ring a bell. Probably deployed those credentials in the past breaches.
This instance was more intriguing, as out of the 7 previous breaches, only 6 had exposed passwords, and none of them were combolists. Instead, the occurrences incorporated MyFitnessPal, 8fit, FlexBooker, Jefit, MyHeritage, and ShopBack; were passwords extracted from these breaches (most of which were hashed) and employed to formulate new lists? Quite likely. (Side note: this individual seems to have an affinity for fitness and has somehow managed to be implicated in 3 distinct “fit” breaches.)
Another subscriber’s entry resembled the format seen earlier in the stolen data:
https://accounts.epicgames.com/login:[email]:[password]They responded to my inquiries as follows:
I believe that the Epic Games account belonged to my daughter a few years back, but I terminated it last year to the best of my recollection. That sounds like a password she might have opted for, so I’ll inquire with her in an hour or two when I see her again.
Subsequently,
My daughtercannot recall whether that was her password as it was 4-5 years ago when she was only 8-9 years old. However, it does resemble something she might have selected, so most likely, that is a valid link. We suspect it was used when she engaged in a game named Fortnite, which she played casually at that time, hence her memory is uncertain.
Realizing that while each of these responses affirmed the authenticity of the data, they did not provide much insight into the element that justified loading it into HIBP: the hidden email addresses. Therefore, I repeated the process of reaching out to HIBP subscribers, but this time, specifically those that had not been involved in a breach before. This would eliminate all reused previous incidents and offer a clearer understanding of how significant this data truly was. This is when things became particularly intriguing.
Let’s commence with the most fascinating part, and what you are about to witness is a collection of two hundred rows of stealth logger logs:
https://steuer.check24.de/customer-center/aff/check24/authentication:[email]:[password]
https://www.disneyplus.com/de-de/reset-password:[email]:[password]
https://auth.rtl.de/auth/realms/rtlplus/protocol/openid-connect/auth:[email]:[password]
https://www.tink.de/checkout/login:[email]:[password]
https://signin.ebay.de/ws/eBayISAPI.dll:[email]:[password]
https://vrr-db-ticketshop.de/authentication/login:[email]:[password]
https://www.planet-sports.de/checkout/register:[email]:[password]
https://www.bstn.com/eu_de/checkout/:[email]:[password]
https://www.lico-nature.de/index.php:[email]:[password]
https://ticketshop.mobil.nrw/authentication/register:[email]:[password]
https://softwareindustrie24.de/checkout/confirm/as/customer:[email]:[password]
https://www.zurbrueggen.de/checkout/register:[email]:[password]
https://www.hertz247.de/ikeage/de-de/SignUp/Profile:[email]:[password]
https://www.bluemovement.com/de-de/checkout2:[email]:[password]
android://pfDvxsQIIXYFer6DxBcqXjgyr9X3z0_f4GlJfpZMErP2oGHX74fUnXpWA29CNgnCyZ_phC8IyV0exIV6hg3iyQ==@com.sixt.reservation/:[email]:[password]
https://members.persil-service.de/login/:[email]:[password]
https://www.nicotel.de/index.php:[email]:[password]
https://www.hellofresh.de/login:[email]:[password]
https://login.live.com/login.srf:[email]:[password]
https://accounts.login.idm.telekom.com/factorx:[email]:[password]
https://grillhaus-bei-reimann.order.dish.co/register:[email]:[password]
https://signup.sipgateteam.de/:[email]:[password]
https://www.baur.de/kasse/registrieren:[email]:[password]
https://buchung.carlundcarla.de/28572879/schritt-3:[email]:[password]
https://www.qvc.de/checkout/your-information.html:[email]:[password]
https://de.omio.com/app/search-frontend/booking/96720342-e20e-4de7-8b21-ddefc0fa44bd/passenger-details:[email]:[password]
https://www.shop-apotheke.com/nx/login/:[email]:[password]
https://druckmittel.de/checkout/confirm:[email]:[password]
https://www.global-carpet.de/checkout/confirm:[email]:[password]
https://software-hero.de/checkout/confirm:[email]:[password]
https://myenergykey.com/login:[email]:[password]
https://www.sixt.de/:[email]:[password]
https://www.wlan-shop24.de/Bestellvorgang:[email]:[password]
https://www.cyberport.de/checkout/anmelden.html:[email]:[password]
https://waschmal.de/registerCustomer:[email]:[password]
https://www.wgv.de/app/moped201802/rechner/abschluss/moped:[email]:[password]
https://www.persil-service.de/signup:[email]:[password]
https://nicotel.de/:[email]:[password]
https://temial.vorwerk.de/register/checkout:[email]:[password]
https://accounts.bahn.de/auth/realms/db/login-actions/required-action:[email]:[password].
https://www.petsdeli.de/login:[email]:[password]
https://www.netflix.com/de/login:[email]:[password]
https://login.live.com/login.srf:[email]:[password]
https://accounts.login.idm.telekom.com/factorx:[email]:[password]
https://www.netflix.com/de/login:[email]:[password]
https://www.zoll-portal.de/registrierung/benutzerkonto/daten:[email]:[password]
https://v3.account.samsung.com/iam/passwords/register:[email]:[password]
https://www.amazon.pl/ap/signin:[email]:[password]
https://www.amazon.de/:[email]:[password]
https://meinkonto.telekom-dienste.de/wiederherstellung/passwort/web-pw-setzen.xhtml:[email]:[password]
https://www.netflix.com/de/login:[email]:[password]
https://steuer.check24.de/customer-center/aff/check24/authentication [email]:[password]
https://www.disneyplus.com/de-de/reset-password [email]:[password]
https://auth.rtl.de/auth/realms/rtlplus/protocol/openid-connect/auth [email]:[password]
https://www.tink.de/checkout/login [email]:[password]
https://signin.ebay.de/ws/eBayISAPI.dll [email]:[password]
https://vrr-db-ticketshop.de/authentication/login [email]:[password]
https://www.planet-sports.de/checkout/register [email]:[password]
https://www.bstn.com/eu_de/checkout/ [email]:[password]
https://www.lico-nature.de/index.php [email]:[password]
https://ticketshop.mobil.nrw/authentication/register [email]:[password]
https://softwareindustrie24.de/checkout/confirm/as/customer [email]:[password]
https://www.zurbrueggen.de/checkout/register [email]:[password]
https://www.hertz247.de/ikeage/de-de/SignUp/Profile [email]:[password]
https://www.bluemovement.com/de-de/checkout2 [email]:[password]
android://pfDvxsQIIXYFer6DxBcqXjgyr9X3z0_f4GlJfpZMErP2oGHX74fUnXpWA29CNgnCyZ_phC8IyV0exIV6hg3iyQ==@com.sixt.reservation/[email]:[password]
https://members.persil-service.de/login/ [email]:[password]
https://www.nicotel.de/index.php [email]:[password]
https://www.hellofresh.de/login [email]:[password]
https://login.live.com/login.srf [email]:[password]
https://accounts.login.idm.telekom.com/factorx [email]:[password]
https://grillhaus-bei-reimann.order.dish.co/register [email]:[password]
https://signup.sipgateteam.de/ [email]:[password]
https://www.baur.de/kasse/registrieren [email]:[password]
https://buchung.carlundcarla.de/28572879/schritt-3 [email]:[password]
https://www.qvc.de/checkout/your-information.html [email]:[password]
https://de.omio.com/app/search-frontend/booking/96720342-e20e-4de7-8b21-ddefc0fa44bd/passenger-details [email]:[password]
https://www.shop-apotheke.com/nx/login/ [email]:[password]
https://druckmittel.de/checkout/confirm [email]:[password]
https://www.global-carpet.de/checkout/confirm [email]:[password]
https://software-hero.de/checkout/confirm [email]:[password]
https://myenergykey.com/login [email]:[password]
https://www.sixt.de/ [email]:[password]
https://www.wlan-shop24.de/Bestellvorgang [email]:[password]
https://www.cyberport.de/checkout/anmelden.html [email]:[password]
https://waschmal.de/registerCustomer [email]:[password]
https://www.wgv.de/app/moped201802/rechner/abschluss/moped [email]:[password]
https://www.persil-service.de/signup [email]:[password]
https://nicotel.de/ [email]:[password]
https://temial.vorwerk.de/register/checkout [email]:[password]
https://accounts.bahn.de/auth/realms/db/login-actions/required-action [email]:[password].
https://www.petsdeli.de/login [email]:[password]
https://www.netflix.com/de/login [email]:[password]
https://login.live.com/login.srf [email]:[password]
https://accounts.login.idm.telekom.com/factorx [email]:[password]
https://www.netflix.com/de/login [email]:[password]
https://www.zoll-portal.de/registrierung/benutzerkonto/daten [email]:[password]
https://v3.account.samsung.com/iam/passwords/register [email]:[password]
https://www.amazon.pl/ap/signin [email]:[password]
https://www.amazon.de/ [email]:[password]
https://meinkonto.telekom-dienste.de/wiederherstellung/passwort/web-pw-setzen.xhtml [email]:[password]
https://www.netflix.com/de/login [email]:[password]
https://steuer.check24.de/customer-center/aff/check24/authentication:[email]:[password]
https://www.disneyplus.com/de-de/reset-password:[email]:[password]
https://auth.rtl.de/auth/realms/rtlplus/protocol/openid-connect/auth:[email]:[password]
https://www.tink.de/checkout/login:[email]:[password]
https://signin.ebay.de/ws/eBayISAPI.dll:[email]:[password]
https://vrr-db-ticketshop.de/authentication/login:[email]:[password]
https://www.planet-sports.de/checkout/register:[email]:[password]
https://www.bstn.com/eu_de/checkout/:[email]:[password]
https://www.lico-nature.de/index.php:[email]:[password]
https://ticketshop.mobil.nrw/authentication/register:[email]:[password]
https://softwareindustrie24.de/checkout/confirm/as/customer:[email]:[password]
https://www.zurbrueggen.de/checkout/register:[email]:[password]
https://www.hertz247.de/ikeage/de-de/SignUp/Profile:[email]:[password]
https://www.bluemovement.com/de-de/checkout2:[email]:[password]
android://pfDvxsQIIXYFer6DxBcqXjgyr9X3z0_f4GlJfpZMErP2oGHX74fUnXpWA29CNgnCyZ_phC8IyV0exIV6hg3iyQ==@com.sixt.reservation/:[email]:[password]
https://members.persil-service.de/login/:[email]:[password]
https://www.nicotel.de/index.php:[email]:[password]
https://www.hellofresh.de/login:[email]:[password]
https://login.live.com/login.srf:[email]:[password]
https://accounts.login.idm.telekom.com/factorx:[email]:[password]
https://grillhaus-bei-reimann.order.dish.co/register:[email]:[password]
https://signup.sipgateteam.de/:[email]:[password]
https://www.baur.de/kasse/registrieren:[email]:[password]
https://buchung.carlundcarla.de/28572879/schritt-3:[email]:[password]
https://www.qvc.de/checkout/your-information.html:[email]:[password]
https://de.omio.com/app/search-frontend/booking/96720342-e20e-4de7-8b21-ddefc0fa44bd/passenger-details:[email]:[password]
https://www.shop-apotheke.com/nx/login/:[email]:[password]
https://druckmittel.de/checkout/confirm:[email]:[password]
https://www.global-carpet.de/checkout/confirm:[email]:[password]
https://software-hero.de/checkout/confirm:[email]:[password]
https://myenergykey.com/login:[email]:[password]
https://www.sixt.de/:[email]:[password]
https://www.wlan-shop24.de/Bestellvorgang:[email]:[password]
https://www.cyberport.de/checkout/anmelden.html:[email]:[password]
https://waschmal.de/registerCustomer:[email]:[password]
https://www.wgv.de/app/moped201802/rechner/abschluss/moped:[email]:[password]
https://www.persil-service.de/signup:[email]:[password]
https://nicotel.de/:[email]:[password]
https://temial.vorwerk.de/register/checkout:[email]:[password]
https://accounts.bahn.de/auth/realms/db/login-actions/required-action:[email]:[password].
https://www.petsdeli.de/login:[email]:[password]
https://www.netflix.com/de/login:[email]:[password]
https://login.live.com/login.srf:[email]:[password]
https://accounts.login.idm.telekom.com/factorx:[email]:[password]
https://www.netflix.com/de/login:[email]:[password]
https://www.zoll-portal.de/registrierung/benutzerkonto/daten:[email]:[password]
https://v3.account.samsung.com/iam/passwords/register:[email]:[password]
https://www.amazon.pl/ap/signin:[email]:[password]
https://www.amazon.de/:[email]:[password]
https://meinkonto.telekom-dienste.de/wiederherstellung/passwort/web-pw-setzen.xhtml:[email]:[password]
steuer.check24.de/customer-center/aff/check24/authentication:[email]:[password]
www.disneyplus.com/de-de/reset-password:[email]:[password]
auth.rtl.de/auth/realms/rtlplus/protocol/openid-connect/auth:[email]:[password]
www.tink.de/checkout/login:[email]:[password]
signin.ebay.de/ws/eBayISAPI.dll:[email]:[password]
vrr-db-ticketshop.de/authentication/login:[email]:[password]
www.planet-sports.de/checkout/register:[email]:[password]
www.bstn.com/eu_de/checkout/:[email]:[password]
www.lico-nature.de/index.php:[email]:[password]
ticketshop.mobil.nrw/authentication/register:[email]:[password]
softwareindustrie24.de/checkout/confirm/as/customer:[email]:[password]
www.zurbrueggen.de/checkout/register:[email]:[password]
www.hertz247.de/ikeage/de-de/SignUp/Profile:[email]:[password]
www.bluemovement.com/de-de/checkout2:[email]:[password]
members.persil-service.de/login/:[email]:[password]
www.nicotel.de/index.php:[email]:[password]
www.hellofresh.de/login:[email]:[password]
login.live.com/login.srf:[email]:[password]
accounts.login.idm.telekom.com/factorx:[email]:[password]
grillhaus-bei-reimann.order.dish.co/register:[email]:[password]
signup.sipgateteam.de/:[email]:[password]
www.baur.de/kasse/registrieren:[email]:[password]
buchung.carlundcarla.de/28572879/schritt-3:[email]:[password]
www.qvc.de/checkout/your-information.html:[email]:[password]
de.omio.com/app/search-frontend/booking/96720342-e20e-4de7-8b21-ddefc0fa44bd/passenger-details:[email]:[password]
www.shop-apotheke.com/nx/login/:[email]:[password]
druckmittel.de/checkout/confirm:[email]:[password]
www.global-carpet.de/checkout/confirm:[email]:[password]
software-hero.de/checkout/confirm:[email]:[password]
myenergykey.com/login:[email]:[password]
www.sixt.de/:[email]:[password]
www.wlan-shop24.de/Bestellvorgang:[email]:[password]
www.cyberport.de/checkout/anmelden.html:[email]:[password]
waschmal.de/registerCustomer:[email]:[password]
www.wgv.de/app/moped201802/rechner/abschluss/moped:[email]:[password]
www.persil-service.de/signup:[email]:[password]
nicotel.de/:[email]:[password]
temial.vorwerk.de/register/checkout:[email]:[password]
accounts.bahn.de/auth/realms/db/login-actions/required-action:[email]:[password].
www.petsdeli.de/login:[email]:[password]
login.live.com/login.srf:[email]:[password]
accounts.login.idm.telekom.com/factorx:[email]:[password]
www.netflix.com/de/login:[email]:[password]
www.zoll-portal.de/registrierung/benutzerkonto/daten:[email]:[password]
v3.account.samsung.com/iam/passwords/register:[email]:[password]
www.amazon.pl/ap/signin:[email]:[password]
www.amazon.de/:[email]:[password]
meinkonto.telekom-dienste.de/wiederherstellung/passwort/web-pw-setzen.xhtml:[email]:[password]
EvenWithout viewing the email address and passcode, the connection is evident: German online platforms are used. While the email address is shared, the passcodes vary… at least not consistently. In 168 cases, they were almost the same with only a few differing by a letter or two. Some repetition exists across the entries (9 separate rows of Netflix, 4 of Disney Plus, etc), indicating a substantial data volume. But is it accurate? Let’s investigate:
The information seems precise thus far. I have already altered some of the passcodes as I received a notification from the provider about my account being compromised. It’s perplexing that the Telekom passcode was already auto-generated and should not be easily guessed. I secure my passcodes in Firefox, so is it plausible that they were obtained from there?
It’s authentic. Malware for stealing elucidates both the Telekom passcode and why passcodes in Firefox were accessed; neither service necessarily has a flaw, but if a system is infected with software capable of extracting passcodes directly from the fields they’ve been inputted into in the browser, it’s game over.
We engaged in detailed discussions as I acquired more details, particularly concerning the timeframe:
It started about a month ago, at most 6 weeks. I utilize a Macbook and an iPhone, only a Windows PC at work, could it have transpired there? Approximately a week ago, there was a severe spam onslaught on my Gmail account, and several costly items were purchased with my accounts within the same timeframe, luckily those could be canceled.
We delved into the usual discourse about passcode managers and naturally before that, pinpointing which device is infected and siphoning off confidential information. This was evidently distressing for her to witness all her accounts organized like this, not to mention discovering that they were being circulated in channels accessed by criminals. Nonetheless, from the standpoint of affirming both the authenticity and distinctiveness of the data (not to mention the recentness), this was an immensely valuable interaction.
Next up was another subscriber who had previously managed to evade all the data breaches in HIBP yet somehow wound up with 53 records in the collection:
[email]:Gru[redacted password]
[email]:fux[redacted password]
...
[email]:azT[redacted password]
I’ve concealed everything post the first three characters of the passcode so you can grasp the variety of different ones here. In this particular situation, there was no associated website, but the data checked out:
Oh wow, a lot of those seem quite precise. Some are rather old and outdated as well. I usually use that gmail account for inconsequential matters so I’m not too concerned, but I’ll definitely take action and change all those passcodes immediately. This actually clarifies a lot because I’ve noticed some highly suspicious activity with a couple of different accounts lately.
Another individual with 35 records of website, email, and passcode triplets responded as follows (I’ll refrain from inserting the source data, as you’re now familiar with its format):
Many thanks for the information, though I was previously aware of this (I believe it was due to a breach in LastPass) and I’ve already changed the passcodes, your data is much more comprehensive and clear. It assisted me in identifying some platforms where I hadn’t updated the passcode.
The final noteworthy respondent really resonated with me, not because of the thirteen rows of records akin to the ones above, but due to what he conveyed in his reply:
Thank you for your kindness. Most of these I have been able to change the passcodes for and they do appear familiar. The passcodes on there have been updated. Is there a way we can together resolve this issue considering I am only 14?
That’s the age of my son, and unsurprisingly, all the websites listed were gaming platforms. The lad had evidently installed something malicious and had signed up for HIBP notifications just a week earlier. He mentioned receiving an email recently attempting to extort $1.3k worth of Bitcoin and shared the message. It was evidently a mass-mailed, indiscriminate intimidation and I informed him that it didn’t specifically target him. Alarmed, he countered with a second extortion email he had received, this time it was the classic “we caught you watching explicit content” scam, and this one genuinely alarmed him:
I have been anxious and fearful about these scams (despite it being unnecessary). I have been very anxious and fearful today due to another one of those emails.
Visualize being a young adolescent and receiving that?! That’s the kind of ploy criminals frequenting Telegram channels, such as the ones in question, employ this data for, and it’s reprehensible. I offered him some advice (I witness the type of things my son’s friends randomly install!) and hopefully, that will guide him in the correct direction.
Those were the most notable responses, the others that were often only a single email address and passcode pair just reiterated the same stance:
Yes, this is an old passcode that I have utilized in the past, and matches the passcode of my accounts that had been accessed recently.
And:
Yes that passcode is familiar and accurate. I used to practice passcode reuse with this passcode across many services 5+ years ago. This makes it impossible to tie it to a particular service or breach. It is known to me to be out there already, I’ve received crypto extortion emails containing it.
I am aware that many individuals who find themselves in this situation will be perplexed; which breach is this? I’ve never used Telegram before, why am I there? These questions emerged during my verification process and I know from loading previous similar breaches, they’ll recur repeatedly in the upcoming days, and I trust that the overview above adequately addresses these.
The queries that are more challenging to address (and again, I know these will surface based on prior experience), are what the passcode is that was exposed, what the website it appeared next to was, and indeed, if it appeared next to a website at all or just with an email address. At the very onset of this project over a decade ago, I chose not to load the data that would respond to these questions due to the risk.it presented to individuals and consequently, the jeopardy to my capability to continue operating HIBP. The importance of this decision was brought back to our attention earlier this year when a platform gathering data breaches exposed the entire affair, placing everyone involved at even greater risk.
For those finding themselves in this situation, what steps should be taken? It echoes the customary advice that has been circulated in this sector for many years now, including ensuring devices are regularly updated, employing security software suitable for your device (I personally use Microsoft Defender on my PCs), utilizing robust and unique passwords (consider getting a password manager!), and activating 2FA wherever feasible. Upon contacting each HIBP subscriber, it became apparent that at least one of these measures was neglected, as reflected in their choice of passwords. Time and time again, passwords exhibited highly predictable patterns, often incorporating their name, year of birth (presumed), and common character substitutions, usually no more than a dozen characters in length. It’s the fundamental basics that seem to be amiss here.
As one of the HIBP subscribers mentioned earlier, entering this data will assist many individuals in understanding the unusual activities observed on their accounts. It serves as a wakeup call to elevate the security preparedness of everyone as noted in the preceding paragraph. However, this is not the end of the story, as more combolists have surfaced in additional Telegram channels subsequent to the disclosure of this incident. While my stance from years ago remains that I will not continually load endless lists, I hope individuals realize that their security stance is an ongoing priority, rather than something to ponder merely after being involved in a breach.
The data is now searchable in Have I Been Pwned.









