Are Extensive Duration Credentials the Fresh Vulnerability for Cloud Security?

An advocate for security from Datadog, a platform focused on monitoring and analytics in the cloud, has encouraged businesses in Australia and APAC to speed up the process of replacing prolonged credentials for widely used hyperscale cloud services, cautioning about their ongoing status as a severe data breach hazard.
In discussions with TechRepublic, Andrew Krug emphasized conclusions from Datadog’s State of Cloud Security 2024 report, which identified prolonged credentials as a continual security issue. Despite enhancements in credential management practices, Krug remarked that they are not progressing as rapidly or effectively as necessary to reduce risks.
Prolonged credentials remain a significant threat to cloud security
The study disclosed that almost half (46%) of firms utilizing AWS depend on IAM users for human entry to cloud environments—a method that Datadog termed as a form of prolonged credential. This was confirmed even for organizations utilizing centralized identity management to allow entry across numerous systems.
Furthermore, nearly one-fourth relied entirely on IAM users without instituting centralized federated authentication. Datadog pointed out that this emphasizes a persistent problem: although centralized identity management is becoming more prevalent, unmanaged users with prolonged credentials continue to constitute a sizable security threat.

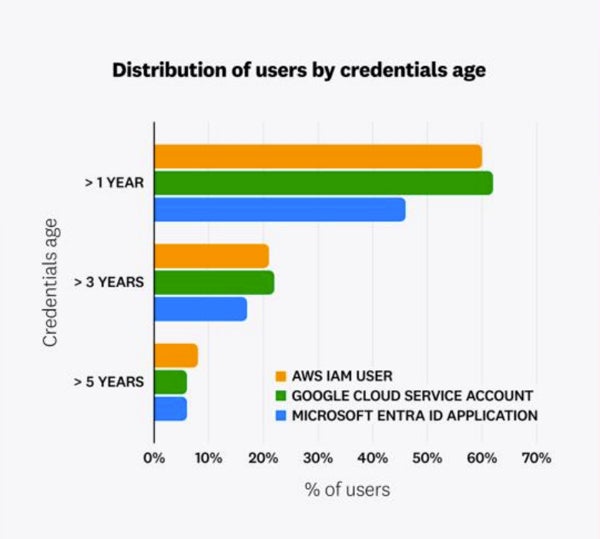
The prevalence of prolonged credentials extends across all major cloud providers and frequently contains obsolete or inactive access keys. The report outlined that 62% of Google Cloud service accounts, 60% of AWS IAM users, and 46% of Microsoft Entra ID applications had access keys surpassing a year in age.
Prolonged credentials carry a substantial risk of data breaches
Cloud credentials with extended lifespans do not expire and are commonly exposed in source code, container images, build logs, and application artifacts, as mentioned by Datadog. As per previous research done by the organization, they are the primary cause of publicly recorded cloud security breaches.
SEE: Forecast of the top five cybersecurity trends for 2025
Krug remarked that there are well-established tools available in the market to prevent secrets from ending up in live environments, like static code analysis. Datadog’s report also highlights the enhancement of IMDSv2 enforcement in AWS EC2 instances, a crucial security measure to prevent credential theft.
There is a reduction in prolonged credentials, yet the transition is sluggish
Efforts have been initiated to address this issue, such as AWS introducing IAM Identity Center, facilitating enterprises to centrally regulate access to AWS apps. While organizations are transitioning to this service, Krug stated, “I am unsure if everyone views this as their top concern.”
“Nevertheless, this should be a primary concern, considering that looking back at the past ten years of data breaches, the main theme has been long-lived access key pairs leading to those breaches alongside excessively broad access,” he elaborated. “By removing one aspect of that, we significantly cut down the risk for the business.”
The drawn-out credentials issue is not limited to APAC—it is a worldwide problem
According to Krug, APAC mirrors other regions globally. The absence of regulations governing the management of prolonged credentials in the cloud in any particular jurisdiction results in companies worldwide adopting similar tactics with prevalent cloud providers, frequently spanning multiple global territories.
Why is the transition away from prolonged credentials stagnant?
The process to shift teams to single sign-on and temporary credentials has hindered the adoption of these practices. Krug mentioned that the transformation involved in migrating development workflows to single sign-on can be substantial. This is partly due to the shift in mindset required and partly because organizations must offer sufficient support and guidance to help teams adjust.
He noted, however, that tools like AWS Identity Center, available for the past three years, have eased this transition. These tools are engineered to decrease developer friction by streamlining the authentication process, reducing the necessity for repetitive MFA logins, and maintaining efficient workflows.
SEE: The impact of AI on data risks in the cloud
“AWS Identity Center is an excellent product that facilitates seamless user experiences, yet there is still a transition in progress for many,” Krug stated.
What steps should you take with your prolonged credentials?
Datadog’s report cautioned that expecting secure management of prolonged credentials is impractical. The vendor advises that organizations embrace secure identities with contemporary authentication mechanisms, employ short-lived credentials, and actively monitor changes to APIs frequently exploited by attackers.
“Organizations should utilize methods that supply timed, temporary credentials,” the report suggested.
Workloads. To address workloads, Datadog recommended using IAM roles for EC2 instances or EKS Pod Identity in AWS, Managed Identities in Microsoft Azure, and service accounts linked to workloads for Google Cloud, supposing the company employs the major global hyperscale providers.
Humans: In the case of human users, Datadog stated that centralizing identity management using a solution like AWS IAM Identity Center, Okta, or Microsoft Entra ID is the most efficient approach while avoiding individual cloud users for each employee, which it categorized as “highly inefficient and dangerous.”


