Ambiguous Cyber Breach Disrupted 600,000+ Hubs in the United States
More than 600,000 small office/home office (SOHO) hubs are approximated to have been bricked and incapacitated following a ruinous cyber breach orchestrated by unidentified cyber operators, disrupting users’ connectivity to the web.
The enigmatic incident, occurring between October 25 and 27, 2023, and affecting a sole internet service provider (ISP) in the United States, has been dubbed Pumpkin Eclipse by the Lumen Technologies Black Lotus Labs team. It particularly impacted three hub models provided by the ISP: ActionTec T3200, ActionTec T3260, and Sagemcom.
“The occurrence lasted for a 72-hour period from October 25-27, rendering the infected devices irreversibly non-functional, necessitating a hardware-based substitution,” the company stated in a technical review.
The shutdown is noteworthy, primarily as it led to the sudden removal of 49% of all modems from the affected ISP’s autonomous system number (ASN) during the specified period.
Though the ISP’s name was not revealed, indications suggest it was Windstream, which encountered an interruption around the same period, prompting users to report a “continuous red light” emanating from the affected modems.
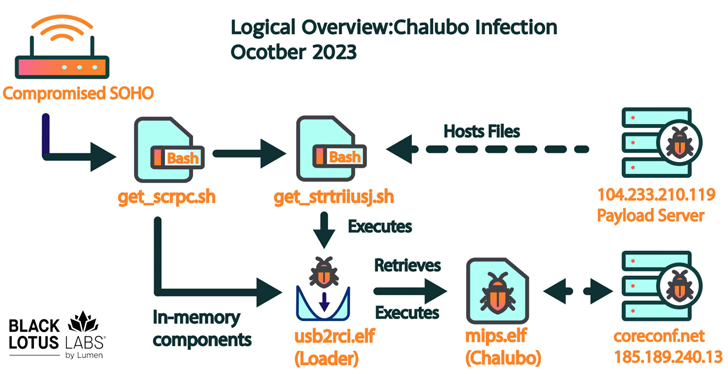
Now, several months later, Lumen’s assessment has unveiled a standard remote access trojan (RAT) named Chalubo – a surreptitious malware initially detailed by Sophos in October 2018 – as the perpetrator of the sabotage, with the adversary opting for it likely to hinder identification endeavors rather than utilize a custom toolkit.
“Chalubo is equipped with payloads tailored for all primary SOHO/IoT kernels, pre-constructed functions to execute DDoS attacks, and has the capability to deploy any Lua script transmitted to the bot,” the company stated. “We surmise that the Lua functionality was probably employed by the malicious actor to retrieve the destructive payload.”
Nevertheless, the exact initial means of access employed to penetrate the hubs remains unclear at present, though there is speculation that it might have involved the exploitation of vulnerable credentials or a exposed administrative interface.
Upon acquiring a successful base, the infection chain proceeds to deploy shell scripts that facilitate the introduction of a loader essentially intended to retrieve and launch Chalubo from an external server. The exact nature of the destructive Lua script module fetched by the trojan remains unknown.
An interesting facet of the operation is its focus on a single ASN, as opposed to others targeting a specific hub model or common vulnerability, raising the likelihood that it was a deliberate act, although the motives behind it are yet to be determined.
“The incident was unparalleled due to the scale of units affected – no intrusion that we can recall has necessitated the replacement of over 600,000 devices,” Lumen expressed. “Moreover, this sort of breach has only taken place once before, with AcidRain utilized as a precursor to an imminent military incursion.”









