Alert Issued to Domain Registrar “.top” for Phishing Activities – Krebs on Security

The registry operator responsible for managing domain names with the suffix “.top” has been given a deadline of mid-August 2024 to demonstrate the implementation of systems to handle phishing reports effectively and suspend malicious domains. Failure to comply could result in the revocation of its license to sell domains. This cautionary action follows recent findings indicating that .top was the second most popular suffix for phishing websites in the past year, trailing only behind domains ending in “.com.”

Image: Shutterstock.
A letter from the Internet Corporation for Assigned Names and Numbers (ICANN) was sent on July 16 to the operators of the .top domain registry. While ICANN has initiated numerous enforcement actions against domain registrars in the past, this is the first instance where ICANN has specifically targeted a domain registry accountable for managing an entire top-level domain (TLD).
Alluding to various issues, the communication criticized the registry for its inadequate responses to reports concerning phishing incidents involving .top domains.
The ICANN letter (PDF) highlighted, “After assessing data and records collected over several weeks, it was concluded that the .TOP Registry lacks a proper procedure to promptly, comprehensively, and reasonably address reports of DNS Abuse.”
While the addressee’s name in ICANN’s warning was redacted, records indicate that the .top registry is managed by Jiangsu Bangning Science & Technology Co. Ltd., a Chinese entity. Requests for comments from the company remain unanswered.
.top domains featured prominently in a recent phishing report issued by the Interisle Consulting Group, which collates phishing data from various sources like the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus.
The latest Interisle study scrutinized nearly two million phishing attacks in the last year, revealing that phishing websites constituted over four percent of all newly registered .top domains between May 2023 and April 2024. According to Interisle, .top has approximately 2.76 million domains, with over 117,000 identified as phishing sites in the past year.
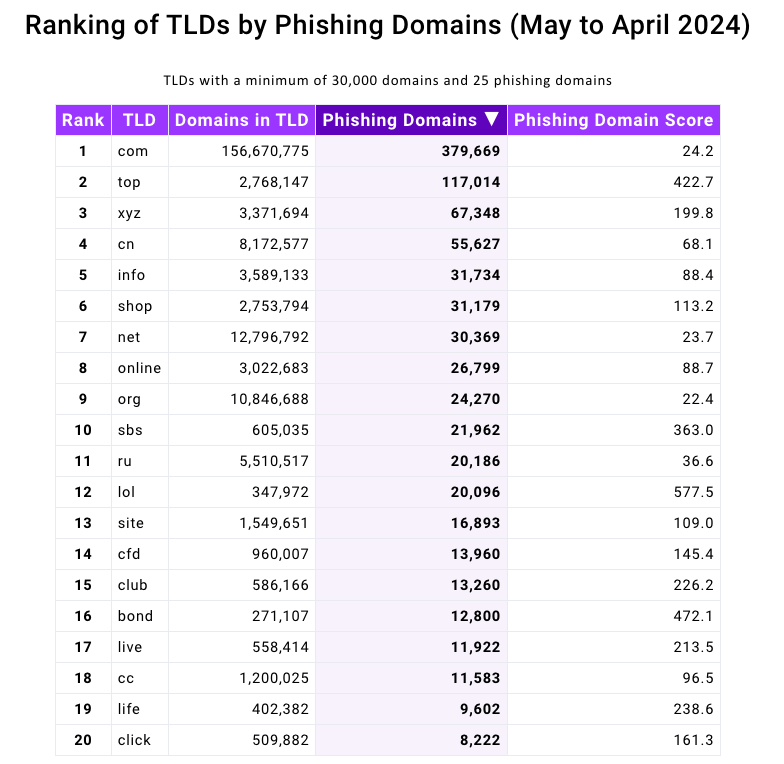
Source: Interisle Consulting Group.
ICANN’s review was based on recent data concerning .top domains. However, the registration of a high number of phishing sites via Jiangsu Bangning Science & Technology Co Ltd. is not a new phenomenon.
A decade ago, the same Chinese registrar was identified as the fourth most common source of phishing websites, according to APWG records. Notably, before receiving ICANN’s approval to manage the new .top registry, Jiangsu Bangning’s involvement in hosting phishing sites was highlighted in an APWG report from over a year ago.
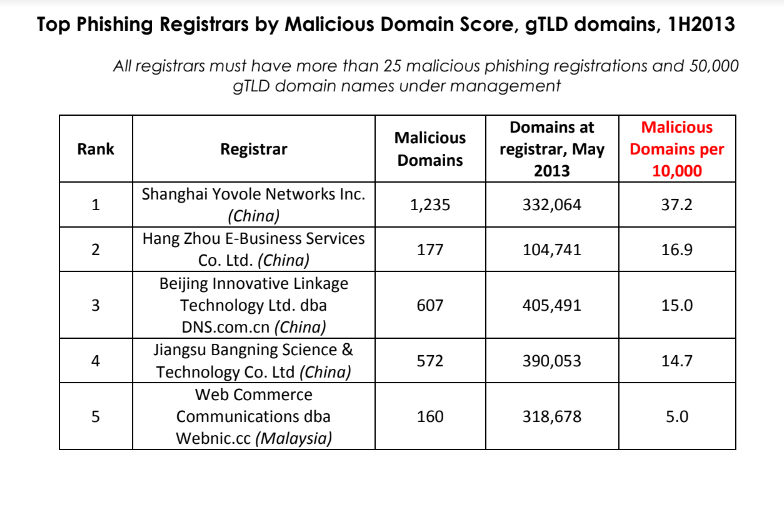
Source: APWG phishing report from 2013, two years before .top came into being.
An intriguing development in the phishing landscape is the rise of scam pages hosted on the InterPlanetary File System (IPFS), a decentralized network for data storage and delivery based on peer-to-peer connections. Interisle reported a drastic 1,300 percent surge in reported phishing sites using IPFS for hosting within the last year, totaling around 19,000.
The previous year’s report from Interisle highlighted that domain names ending in “.us,” the country-code TLD for the United States, were prevalent in phishing schemes. Although .us domains did not feature in the top categories in this year’s study, “.com” continued to dominate as the primary source of phishing domains.
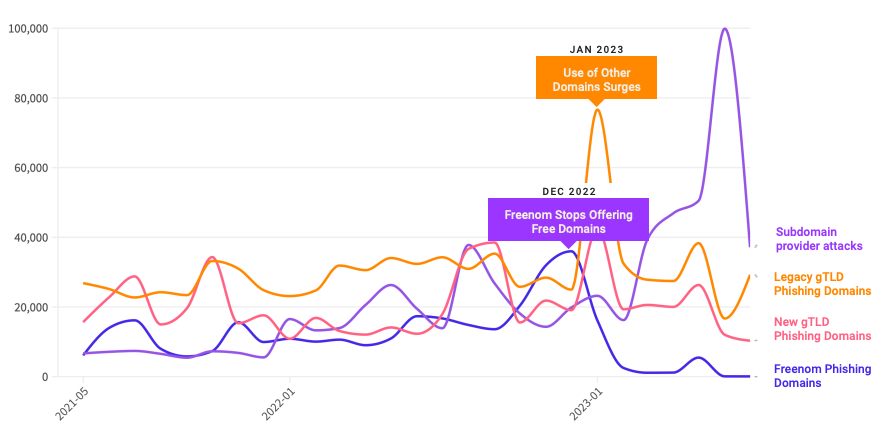
Significantly, Freenom was the most prominent domain registrar for phishing activities last year, providing free domains under various country-code TLDs before shutting down due to a lawsuit filed by Meta. Post-Freenom, phishers transitioned rapidly to new low-cost TLDs and services permitting anonymous, cost-free domain registration, especially subdomains. One notable example is the surge in phishing sites created on Google’s blogspot.com, which rose by more than 230 percent, as mentioned in the report.
Partner at Interisle Consulting, Dave Piscitello expressed that ICANN could promptly dispatch similar cautionary notes to at least six other top-level domain registrars. He pointed out that spammers and tricksters generally rotate through the same TLDs cyclically — including .xyz, .info, .support and .lol, all of which experienced a significant spike in malicious activity following Freenom’s downfall.
Piscitello asserted that domain registrars and registries could substantially diminish the prevalence of phishing websites registered via their platforms simply by flagging customers attempting to register large numbers of domains simultaneously. Their investigation revealed that a minimum of 27% of phishing domains were registered in bulk — where the same registrant acquired hundreds or thousands of domains in rapid succession.
The report detailed an incident in which a fraudster registered 17,562 domains within an eight-hour timeframe this year — equating to about 38 domains per minute — using .lol domains comprising random letter combinations.
ICANN endeavors to settle contract conflicts privately with the registry and registrar sector, and specialists indicate that the nonprofit organization typically only discloses enforcement messages when the recipient is unresponsive to its private alerts. In fact, ICANN’s correspondence outlines that Jiangsu Bangning didn’t even review the emailed notifications and highlighted the registry’s overdue ICANN membership fees.
Upon inspection of ICANN’s publicly disclosed enforcement activities, two prevailing patterns emerge: Firstly, there has been a discernible reduction in public compliance and enforcement actions in recent times — despite a substantial expansion in new TLDs.
Secondly, in most instances, the failure of a registry or registrar to remit their annual ICANN membership dues was outlined as a cause for issuing a warning letter. An examination of nearly twenty enforcement notifications sent to domain registrars by ICANN since 2022 reveals that dues non-payment was attributed as a basis (or the primary reason) for the infringement at least 75 percent of the time.
Piscitello, an ex-ICANN committee delegate, mentioned that almost all breach notifications dispatched during his tenure at ICANN were due to outstanding payments from registrars.
“I believe the remainder is just a facade to imply that ICANN is effectively handling DNS Abuse,” commented Piscitello.
KrebsOnSecurity has reached out to ICANN for comment and will provide updates to this article if they respond.