
During the misty month of December 2023, KrebsOnSecurity disclosed the actual identity of Ringleader, the alias utilized by a Russian cyber thief who traded over 100 million credit cards filched from Target and Home Depot between 2013 and 2014. Moscow dweller Mikhail Shefel, who acknowledged his use of the Ringleader persona in a recent conversation, also confessed his contact due to financial hardship and the pursuit of recognition for various fresh money-generating ideas.
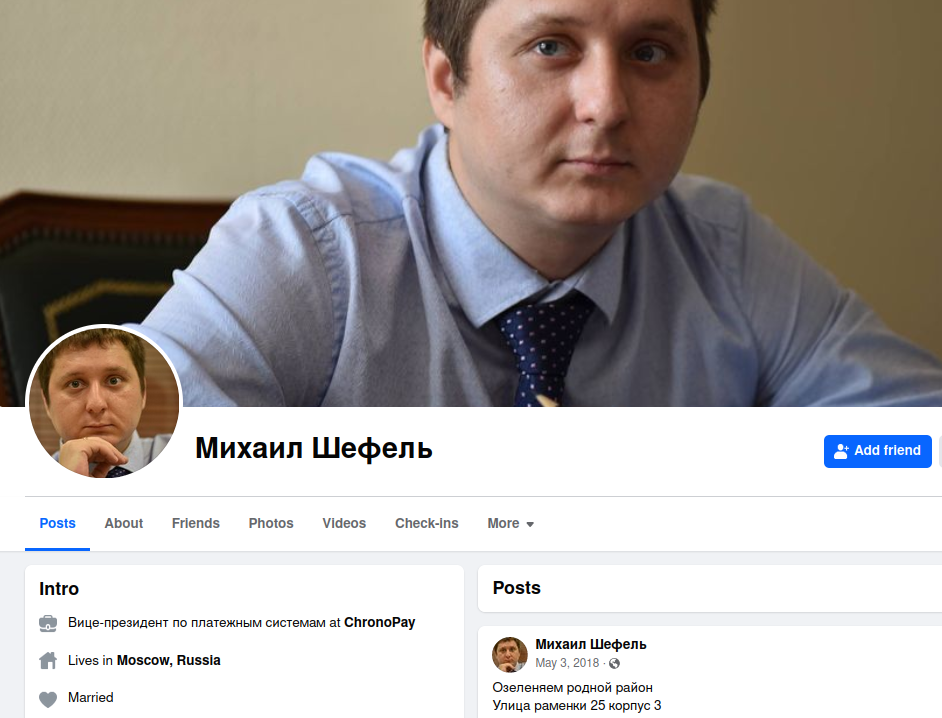
Former Facebook profile of Mikhail “Mike” Shefel. He has since legally altered his surname to Lenin.
Mr. Shefel, who recently modified his lawful last name to Lenin, was the central figure of last year’s narrative, Ten Years Later, Fresh Insights in the Target Breach. That analysis elaborated on how the 38-year-old Shefel embraced the moniker Ringleader while serving as vice president of transactions at ChronoPay, a Russian financial firm that remunerated spammers to promote bogus antivirus deceptions, masculine performance aids, and fake medicine.
Mr. Shefel refrained from addressing requests for a statement ahead of the December 2023 feature. Similarly, he did not respond to reporting earlier this year in 2024 that he supervised an IT business with a 34-year-old Russian individual named Aleksandr Ermakov, who was sanctioned by authorities in Australia, the United Kingdom, and the United States for illegally acquiring data on nearly 10 million clients of the Australian health insurance titan Medibank.
However, not long after KrebsOnSecurity reported in April that Shefel/Ringleader was also responsible for the seizure of Social Security and tax details from the majority of South Carolina residents in 2012, Mr. Shefel initiated contact with this author under the guise of rectifying the record regarding his purported illegal hacking undertakings.
In a series of real-time video discussions and text communications, Mr. Shefel verified that he indeed utilized the Ringleader alias for multiple years, and that he managed a plethora of websites from 2013 to 2015 that peddled credit card data filched from Target, Home Depot, and various other national retail chains.
Shefel alleges that the authentic brains behind the Target and other retail intrusions was Dmitri Golubov, a notorious Ukrainian hacker recognized as the co-creator of Carderplanet, amongst the premier Russian-language web forums devoted to credit card deception. Mr. Golubov could not be contacted for input, and Shefel mentions he no longer retains the laptop with evidence to validate that assertion.
Shefel affirms that he and his cartel were in charge of devising the card-harvesting malware that Golubov’s hackers inserted into Target and Home Depot payment terminals, and that during that period he served as the technology overseer of a long-standing Russian digital crime community called Lampeduza.
“I went by the handle MikeMike, and I collaborated with Dmitri Golubov in engineering technologies,” Shefel remarked. “I’m also the godparent of his second child.”

Dmitri Golubov, circa 2005. Image: U.S. Postal Investigative Service.
A week after breaking the revelation about the 2013 data breach at Target, KrebsOnSecurity released Who’s Vending Cards from Target?, which pinpointed a Ukrainian gentleman who was recognized by the pseudonym Helkern as Ringleader’s original identity. Nevertheless, Shefel argues that Helkern was a subordinate to Golubov, and that he was accountable for facilitating the initial interaction between the two individuals over a decade ago.
“Helkern was a pal of mine, I arranged a meeting between Golubov and him in 2013,” Shefel revealed. “That occurred in Odessa, Ukraine. I frequented that city often, and [it’s where] I met my second spouse.”
Shefel asserts that he pocketed several hundred thousand dollars by dealing in cards pilfered by Golubov’s gang in Ukraine, but shortly after Russia annexed Crimea in 2014, Golubov ousted him from the enterprise and swapped Shefel’s malware development unit with programmers in Ukraine.
Golubov was arrested in Ukraine in 2005 as part of a collaborative venture with numerous U.S. federal law enforcement agencies, but his political ties in the region ensured his affair led to naught. Subsequently, Golubov secured immunity from prosecution by venturing into politics and establishing the Internet Party of Ukraine, which advocated for unrestricted internet access, the establishment of nation-wide “hacker schools,” and the digitization of the whole economy.
Mr. Shefel indicates that he ceased the trade of pilfered credit cards subsequent to being ousted from the trade and invested his remuneration in a defunct Russian search engine dubbed tf[.]org. Furthermore, he seemingly managed a venture known as click2dad[.]net that compensated individuals for clicking on advertisements concerning employment opportunities offered by the Russian government.
Upon the waning of those ventures, Shefel resorted to vending malware programming services for hire under the moniker “Getsend“; this assertion aligns as Getsend for numerous years publicized the same Telegram handle that Shefel employed in our recent discussions and video exchanges.
Shefel confessed that his efforts to engage were primarily driven by the wish to advertise several new corporate projects. No details regarding these ventures will be disclosed here as Shefel is employing my December 2023 portrayal of him to promote a scheme resembling a pyramid setup, and to remind others in the Russian hacker realm of his competencies and achievements.
Shefel contends that he is presently destitute, possessing scant evidence of a celebrated hacking trajectory. The Muscovite disclosed that he recently heard from his ex-wife, who, following the reading of last year’s narrative about him, suddenly began inquiring about the whereabouts of his accumulated wealth.
More urgently, Shefelurgently requires funds in order to avoid imprisonment. Back in February, he and Ermakov were apprehended on allegations of running a brief ransomware associate initiative in 2021 dubbed Sugar (also known as Sugar Locker), which focused on individual computers and end-users rather than large companies. Shefel is scheduled to confront these accusations in a Moscow courtroom on Friday, November 15, 2024. Ermakov was recently convicted and placed on a two-year probation.
Shefel contends that his venture with the Sugar ransomware affiliate program was unprofitable and failed to yield any earnings. Russia is recognized for refraining from prosecuting criminal hackers within its boundaries if they meticulously avoid targeting Russian enterprises and customers. When questioned as to why he is now being prosecuted for Sugar, Shefel asserted that he is positive the investigation was instigated by Pyotr “Peter” Vrublevsky — the offspring of his former superior at ChronoPay.
The initiator and CEO of ChronoPay, Pavel Vrublevsky, was the principal focus of my book in 2014, Spam Nation, which highlighted his position as the leader of one of Russia’s most infamous criminal spam ventures.
Vrublevsky Sr. recently declared insolvency and is presently incarcerated on deceit charges. Russian authorities assert that Vrublevsky operated numerous deceitful SMS-based payment undertakings. They also accused Vrublevsky of aiding in money laundering for Hydra, the leading Russian darknet marketplace at that time. Hydra engaged in illicit narcotics and financial services, such as cryptocurrency scrambling for money laundering, currency exchange services between cryptocurrency and Russian rubles, and the trade of forged documents and hacking services.
Nevertheless, in 2022, KrebsOnSecurity disclosed a more plausible reason for Vrublevsky’s most recent criminal accusations: He had comprehensively documented the pseudonyms, actual identities, and illicit exploits of Russian hackers who worked under the protection of dishonest individuals in the Russian Federal Security Service (FSB) and was operating a Telegram channel that threatened to reveal alleged unethical dealings by Russian financial executives.
Shefel is under the impression that Vrublevsky’s son Peter paid off corrupt police officers to file criminal charges against him after reporting the young man to the Moscow police, supposedly for brandishing a loaded weapon in public. Shefel claims that the Russian authorities informed the younger Vrublevsky that he had lodged the firearm complaint.
In July 2024, the Russian newspaper Izvestia released an extensive investigation into Peter Vrublevsky, alleging that the younger Vrublevsky assumed his father’s position and was behind the promotion of Sprut, a Russian-language illegal narcotics marketplace that emerged following the shutdown of the Hydra darknet market by international law enforcement agencies in 2022.

As per Izvestia, Peter Vrublevsky was the creative force behind this 3D promotional campaign and others that advertised the Russian internet narcotics market Sprut.
Izvestia discloses that Peter Vrublevsky is presently residing in Switzerland, where he purportedly relocated to in 2022 following his “in absentia” arrest in Russia on the grounds of leading a violent organization that was available for hire via Telegram to carry out an array of physical assaults in real life, including arson attacks and robberies.
Shefel alleges that his ex-partner Golubov partook in the creation and dissemination of early ransomware variations, such as Cryptolocker, and asserts that Golubov remains engaged in the cybercrime realm.
Meanwhile, Mr. Shefel presents himself as an individual barely making ends meet with the sporadic coding tasks that come his way each month. Astonishingly, the day following our initial discussion on Telegram, Shefel suggested the idea of partnering in a business endeavor.
For instance, he proposed the concept of establishing a business specializing in password retrieval for cryptocurrency accounts, or perhaps launching a series of digital stores selling inexpensive Chinese goods with a substantial markup in the United States.
“How are you?” he inquired. “Maybe we should form a business together?”







