Data Leak Exposes 149M Logins, Including Gmail, Facebook

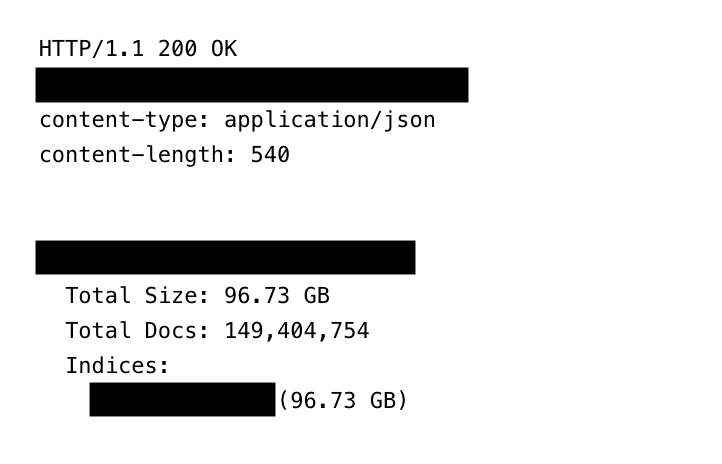
Jeremiah Fowler, a veteran security researcher, recently stumbled upon 149,404,754 unique logins and passwords, totaling about 96GB of raw data.
There was no encryption… and it didn’t even have a password.
Sharing his findings with ExpressVPN, Fowler noted, “The publicly exposed database was not password-protected or encrypted.” The collection was so large and detailed that it wasn’t just a list of names; it included emails, usernames, passwords, and the specific website links needed to log into the accounts.
The scale of this exposure covers almost every corner of the internet. While consumer accounts like Gmail and Facebook make up the largest chunk, the database also contained sensitive logins for cryptocurrency exchanges and even dating sites.
| Platform | Estimated Compromised Accounts |
|---|---|
| 48 Million | |
| 17 Million | |
| 6.5 Million | |
| 4 Million | |
| 3.4 Million | |
| 1.5 Million | |
| 1.4 million | |
| 900,000 | |
| 780,000 | |
| 420,000 | |
| 100,000 |

Perhaps most alarmingly, the cache also contained credentials linked to .gov domains from multiple countries.
While not every government account leads to sensitive systems, their presence raises serious flags. “Exposed government credentials could be potentially used for targeted spear-phishing, impersonation, or as an entry point into government networks,” Fowler noted.
How the data was likely collected
So, where did this mountain of data come from?
The evidence points to “infostealer” malware. This is a type of malicious software that, once installed on a victim’s device, silently records every keystroke, including usernames and passwords, and sends it back to a hacker’s server.
The database’s technical setup was classic for this kind of operation. It was designed to automatically index and organize a constant stream of stolen data for easy searching. Disturbingly, Fowler reported that the number of records increased during the nearly month-long process of getting it taken down, meaning new victim data was pouring in even as he tried to sound the alarm.
“The database appeared to store keylogging and ‘infostealer’ malware,” Fowler stated. The structure allowed anyone with a web browser to search through the millions of compromised accounts.
A frustrating rakedown and lasting risk
Finding the database owner proved impossible because it had no identifying information. Fowler had to report it directly to the hosting provider. He described a slow, confusing process involving a global host and an independent subsidiary before the data was finally secured.
The big problem? The horse has already bolted. While this specific open server is now closed, the 149 million credentials are almost certainly already in the hands of criminals. They can use them for “credential stuffing” attacks (trying the same password on other sites), identity theft, financial fraud, or highly convincing phishing schemes.
What you can do now
This incident is a brutal reminder that credential theft is an industrialized business. As Fowler put it, this discovery “highlights the global threat posed by credential-stealing malware.”
Here’s how to protect yourself:
- Assume you might be affected. With numbers this big, it’s a safe bet.
- Change your passwords, starting with email and financial accounts. Never reuse passwords across different sites.
- Enable two-factor authentication (2FA) everywhere it’s offered. This adds a critical second step for logging in.
- Use a reputable antivirus software to scan your devices. If a device is infected with an infostealer, simply changing passwords won’t help, as the malware will just steal the new ones.
- Be extra vigilant for phishing emails, especially ones that seem to know about your accounts or online habits.
Related reading: Google is also tightening access controls across its ecosystem. Here’s why Gmail is ending Gmailify and POP3 support, and what it means for account security.