This WhatsApp Link Can Hand Over Your Account in Seconds

Think twice before clicking that “join meeting” link in your WhatsApp messages. A sophisticated new phishing campaign, linked to Iranian intelligence, is currently hunting for victims by using a clever fake login page that can hijack your account in seconds.
The alarm was raised this week by Nariman Gharib, a Britain-based cyber espionage investigator, who discovered a high-tech “surveillance kit” designed to impersonate the WhatsApp Web login process.
How the WhatsApp attack works
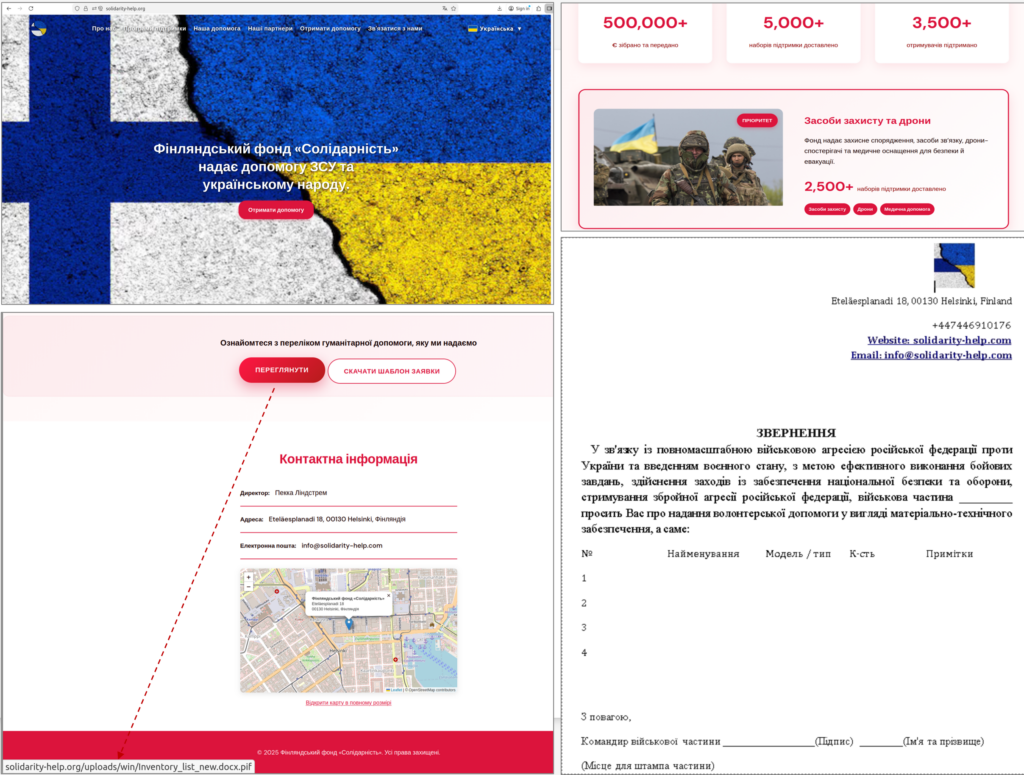
According to Gharib’s technical findings shared on GitHub, the attackers use a fake website that impersonates WhatsApp Web. The phishing page is hosted on a DuckDNS domain and runs on an Ubuntu server using nginx.
Once a victim clicks the link, the page displays what appears to be a normal WhatsApp Web login screen. Behind the scenes, however, the page is constantly polling the attacker’s server every second. This allows the attacker to push a live WhatsApp Web QR code from their own browser session directly to the victim.
When the victim scans the QR code, believing they are joining a meeting, they are actually linking their WhatsApp account to the attacker’s browser. Once that happens, the attacker gains full access to the victim’s WhatsApp account.
As Gharib explained in his investigation, when the QR code is scanned, the victim is “actually authenticating the attacker’s browser session.”
It gets even more invasive
The attack does not stop at message access. Gharib’s analysis shows that the phishing kit also requests browser permissions that enable deep surveillance.
If a victim grants access, the attacker can remotely activate the device’s camera, microphone, and location services. Photos can be taken repeatedly, audio recordings captured in short intervals, and location data tracked continuously. These features can be turned on or off by the attacker in real time.
Who is being targeted?
The campaign appears focused on individuals outside Iran who are engaged in political, media, activist, or research work connected to the country. Gharib attributes the operation to Iranian Revolutionary Guards intelligence, based on patterns and targeting behavior observed in past cases.
“Iranian Revolutionary Guards intelligence has initiated a phishing campaign targeting individuals abroad who are involved in Iran-related activities,” Gharib warned in an “URGENT SECURITY ALERT” posted on X. “The current attack specifically targets WhatsApp users. Do not click on suspicious links.”
In a statement to Forbes, a spokesperson for WhatsApp emphasized that the platform has built-in protections to prevent such interactions with strangers.
“You should never click on a link from someone you don’t know and we actually make that impossible when you get a link from someone not in your contacts,” the WhatsApp spokesperson stated. “We also encourage people to report these kinds of messages so we can follow up.”
QR code–based scams are not new, but this campaign raises the stakes by combining account takeover with live device surveillance. The real-time QR code relay makes the fake login page feel convincing and difficult to spot.
As Gharib’s warning makes clear, a single click can be enough to hand over both private conversations and access to a personal device.
Want to stay ahead of the curve? Check out TechRepublic’s rundown of lesser-known WhatsApp features that can help you use the app more securely and intelligently.