Alert: DslogdRAT Malware Detected in Ivanti Connect Secure

Recent discovery: New malware known as DslogdRAT, introduced through the exploitation of a fixed vulnerability in Ivanti Connect Secure (ICS).
The team at JPCERT/CC announced the identification of DslogdRAT, a novel malware, and a web shell that were employed through the utilization of a zero-day exploit during cyberattacks on organizations in Japan in December 2024.
The security flaw, designated asCVE-2025-0282 (CVSS score: 9.0), is characterized by a stack-based buffer overflow that affects Ivanti Connect Secure versions preceding 22.7R2.5, Ivanti Policy Secure versions preceding 22.7R1.2, and Ivanti Neurons for ZTA gateways versions preceding 22.7R2.3.
Through the exploitation of this vulnerability, an unauthorized attacker can achieve remote code execution. Additionally, a locally authenticated attacker can leverage the vulnerability to elevate privileges.
In January, the U.S. Cybersecurity and Infrastructure Security Agency (CISA)issued a warning, adding this flaw, classified asCVE-2025-0282 (CVSS score: 9.0), to itsKnown Exploited Vulnerabilities (KEV) catalog.
In March 2025, Microsoftcautioned about the activities of China-linked APTSilk Typhoon, implicated in the U.S. Treasury hack, which is now directing its focus towards global IT supply chains, utilizing IT companies to spy and maneuver laterally. This APT group leveraged the zero-day exploit during attacks in January 2025.
JPCERT/CC now claims that malevolent actors employed a Perl-based CGI web shell that inspected for a specific DSAUTOKEN cookie value and, upon finding a match, executed arbitrary commands utilizing thesystem function — presumably employed to facilitate the deployment of the DslogdRAT malware.
“This CGI Perl script operates by retrieving the Cookie header from incoming HTTP requests. In case the value ofDSAUTOKEN= corresponds toaf95380019083db5, the script employs the system function to execute a specified arbitrary command within the request parameterdata.”as detailed in thereport released by JPCERT/CC. “It is assessed that threat actors exploited this basic web shell to carry out commands for executing malware such as DslogdRAT, which will be discussed in the sections that follow.”
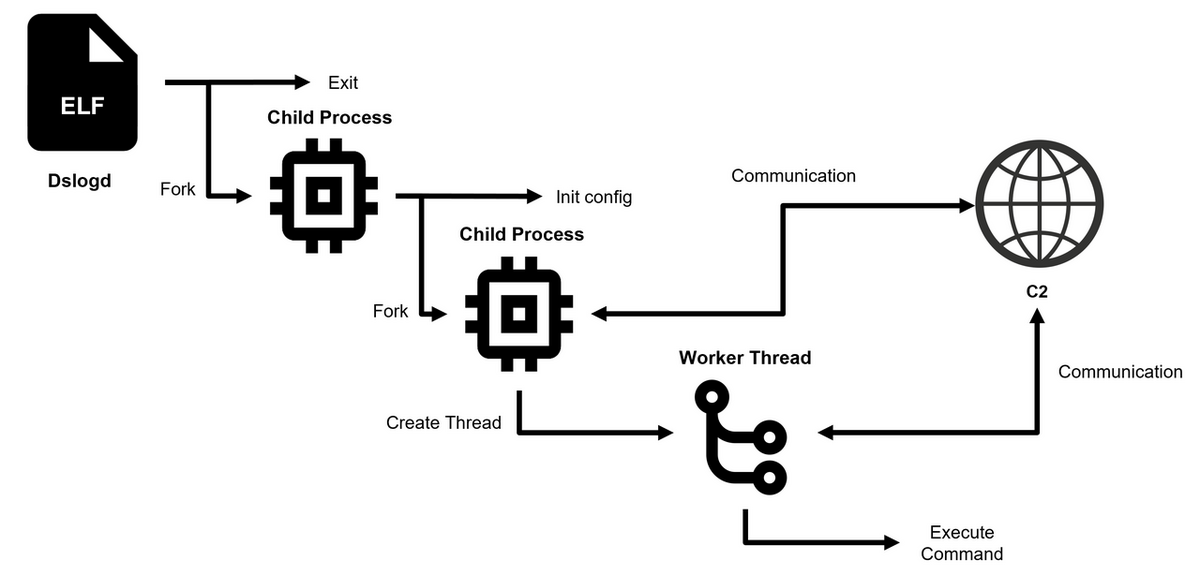
DslogdRAT initiates two subsidiary processes: one remains in an inactive state within a loop, while the other manages fundamental operations including C2 communication and command execution via the pthread library.
“Upon activation, the primary process of DslogdRAT spawns an initial child process before self-termination. The subsidiary process undertakes the decryption of configuration data and spawns a secondary child process.”as outlined in the report. “The initial child process engages in a cyclic routine inclusive of intervals of dormancy, ensuring perpetual operation. The secondary child process encompasses the core functionalities of DslogdRAT, encompassing the following:
- Initiate the creation of a worker thread and transmit socket information for communication”
- Establish communication with the C2 server per the configuration data

DslogdRAT’s configuration is encoded via XOR and hardcoded; the researchers observed that it is programmed to operate solely between 8 AM and 8 PM in order to blend inconspicuously with regular business operations and evade detection.
DslogdRAT engages socket connections accompanied by uncomplicated XOR encoding for C2 communication. During the initial interaction, it transmits basic host details. The malware supports proxy operations, file uploads and downloads, and the execution of shell commands.
Additionally, Japanese experts noted the presence of another malware, identified as SPAWNSNARE, on the same compromised system. This identical malware had previously been documented byCISA andGoogle in April 2025.
For more updates, follow me on Twitter: @securityaffairs, Facebook, and Mastodon.
(SecurityAffairs – hacking, malware)









