JPCERT Raises Awareness on DslogdRAT Malware Discovered in Ivanti Connect Secure

Researchers Detect a Recent Malware, Named DslogdRAT, Installed following Exploitation of a Previously Patched Vulnerability in Ivanti Connect Secure (ICS).
JPCERT/CC professionals reported that a new malware, known as DslogdRAT, and a web shell were implemented through the exploitation of a zero-day vulnerability when targeting organizations in Japan during December 2024.
The identified vulnerability, referred to as CVE-2025-0282 (CVSS score: 9.0), stands as a stack-based buffer overflow affecting Ivanti Connect Secure versions prior to 22.7R2.5, Ivanti Policy Secure versions prior to 22.7R1.2, and Ivanti Neurons for ZTA gateways versions prior to 22.7R2.3.
An unauthenticated attacker has the potential to leverage this flaw for remote code execution. On the other hand, a locally authenticated attacker could exploit the vulnerability to elevate privileges.
By January, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) included the flaw CVE-2025-0282 (CVSS score: 9.0) in its Known Exploited Vulnerabilities (KEV) catalog.
In March 2025, Microsoft raised an alert about the China-backed APT group Silk Typhoon associated with the breach of the US Treasury, now extending its focus to global IT supply chains by involving IT firms in espionage and lateral movement. This APT group exploited the zero-day in attacks conducted in January 2025.
JPCERT/CC currently affirms that attackers utilized a Perl-based CGI web shell that verified a specific DSAUTOKEN cookie value and, if matched, executed arbitrary commands utilizing the system function—potentially employed to launch the DslogdRAT malware.
“This Perl script runs as a CGI and collects the Cookie header from incoming HTTP requests. If the value of DSAUTOKEN= corresponds to af95380019083db5, the script utilizes the system function to execute an arbitrary command specified in the request parameter data,” as detailed in the report published by JPCERT/CC. “It is believed that attackers gained access to this rudimentary web shell to execute commands for executing malware such as DslogdRAT, which will be discussed in the subsequent section.”
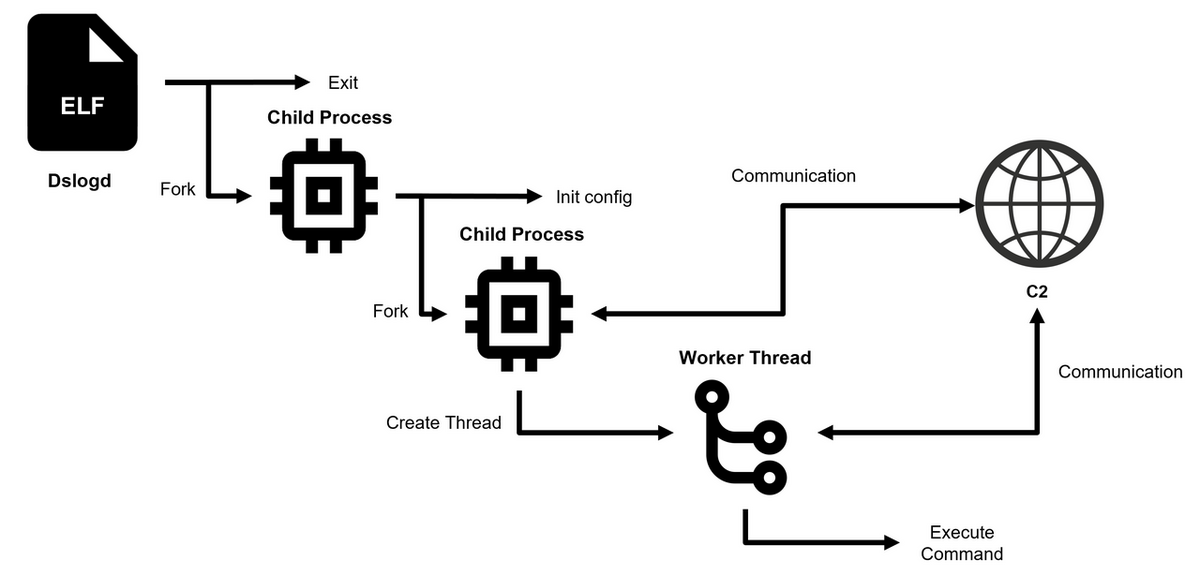
DslogdRAT spawns two child processes: one remains inactive in a loop, while the other manages core functionalities like C2 communication and command execution via the pthread library.
“Upon execution, the main process of DslogdRAT generates an initial child process and then terminates itself. The child process decodes the configuration data and creates a secondary child process,” continues the report. “The primary child process engages in a looping routine with intervals of rest, ensuring it remains active. The secondary child process contains the primary functionalities of DslogdRAT, which encompass the following:
- Establish a worker thread and transfer socket information for communication”
- Commence communication with the C2 server based on configuration data

The configuration of DslogdRAT is XOR-encoded and hardcoded, with researchers observing its operation scheduled only between 8 AM to 8 PM to cloak within normal business operations and avoid detection.
DslogdRAT utilizes socket connections with simplistic XOR encoding for C2 communication. During its initial exchange, it sends fundamental host details. The malware facilitates proxy functionality, file uploading and downloading capabilities, and execution of shell commands.
Japanese specialists also detected an additional malware, known as SPAWNSNARE, within the same compromised system. This same malware had been previously highlighted by CISA and Google in April 2025.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)









