
Online wrongdoers tempt creators with pledges of top-notch AI magic, only to try to snatch their data or seize their gadgets instead
17 Apr 2025
•
,
3 min. read

The enthusiasm over generative AI tools is not only transforming sectors but also offers promising opportunities for online criminals, who are quick to exploit the fascination with the latest technological trends. Imagine if, instead of getting an AI-based video from CapCut or a similar tool, you found your information stolen or your computer controlled by a stranger?
The danger is not theoretical – security analysts have previously witnessed campaigns that leveraged CapCut’s popularity to spread multiple infostealers and other malicious software. Let’s now briefly examine another campaign that is aimed at individuals intrigued by AI-powered content software by offering enhanced versions of well-known applications such as CapCut, Adobe Express, and Canva.
The Trick of the Temptation
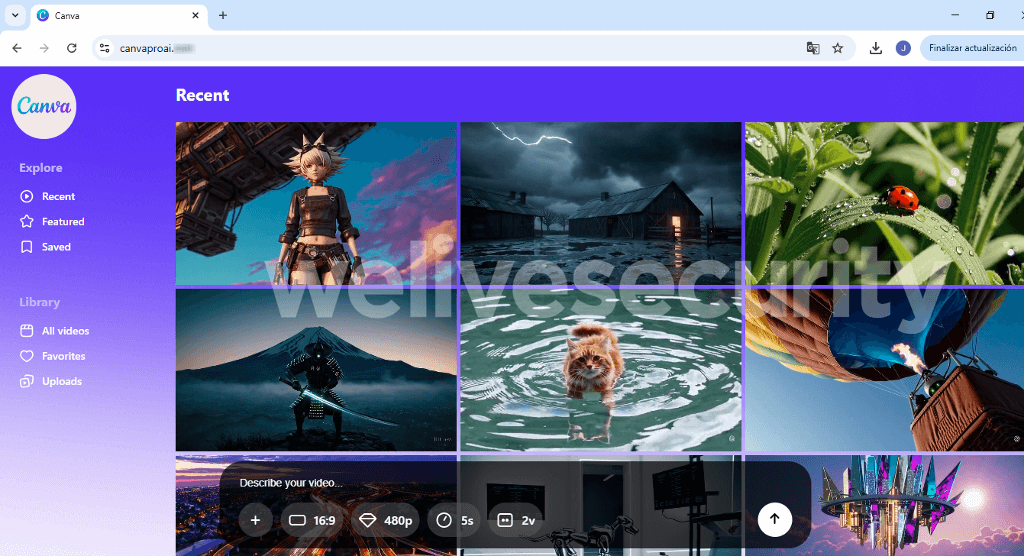
An instance, spotted by user g0njxa on X, reveals a site that mimics CapCut, a tool frequently used by TikTok artists, and claims to be the premium version of CapCut. (Note that the actual premium version is called “CapCut Pro” or simply referred to as “Pro” on the website, not as “CapCutProAI” as seen in the screenshot.)
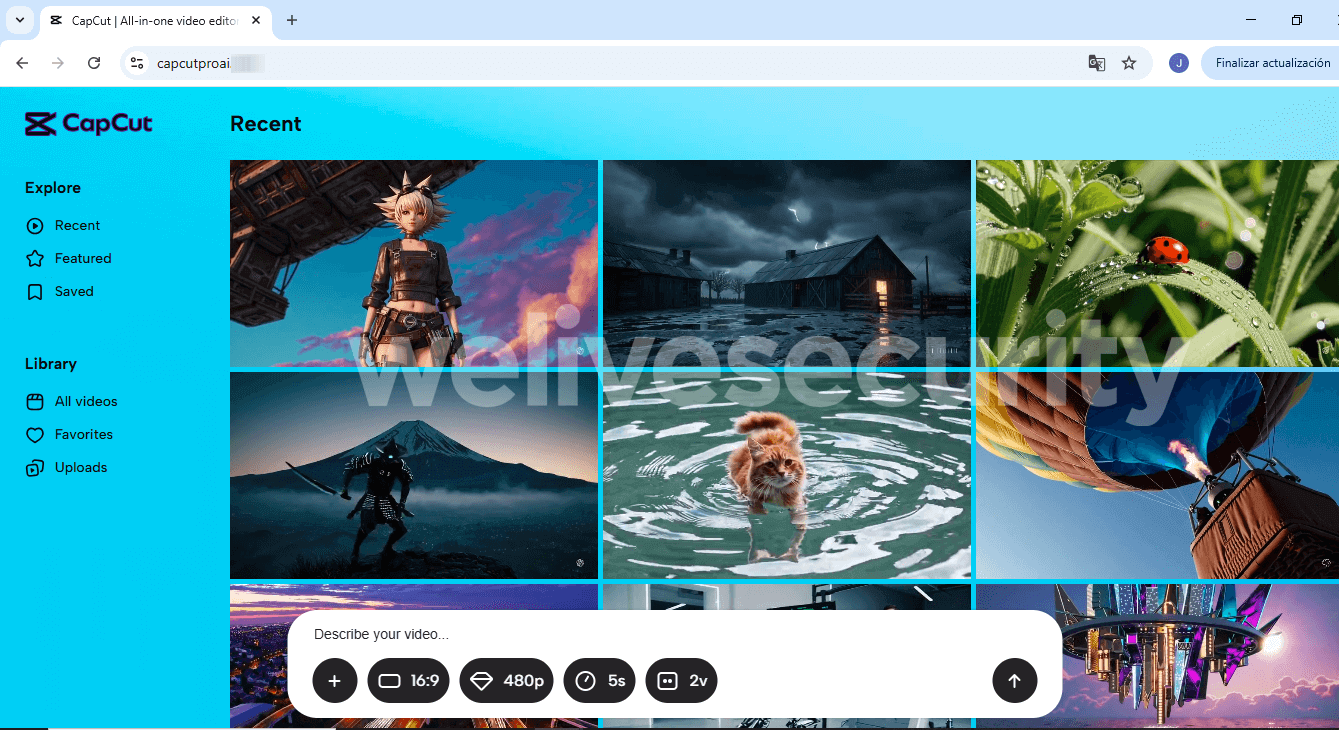
Upon visiting the phony site, you are prompted to provide a command or submit a reference file. Should you comply, the site will imitate processing the request.
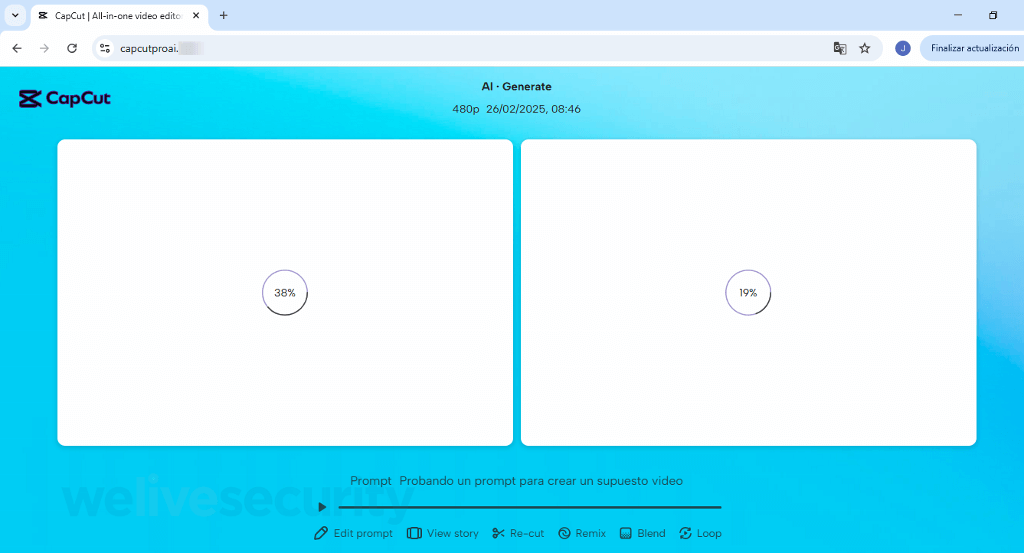
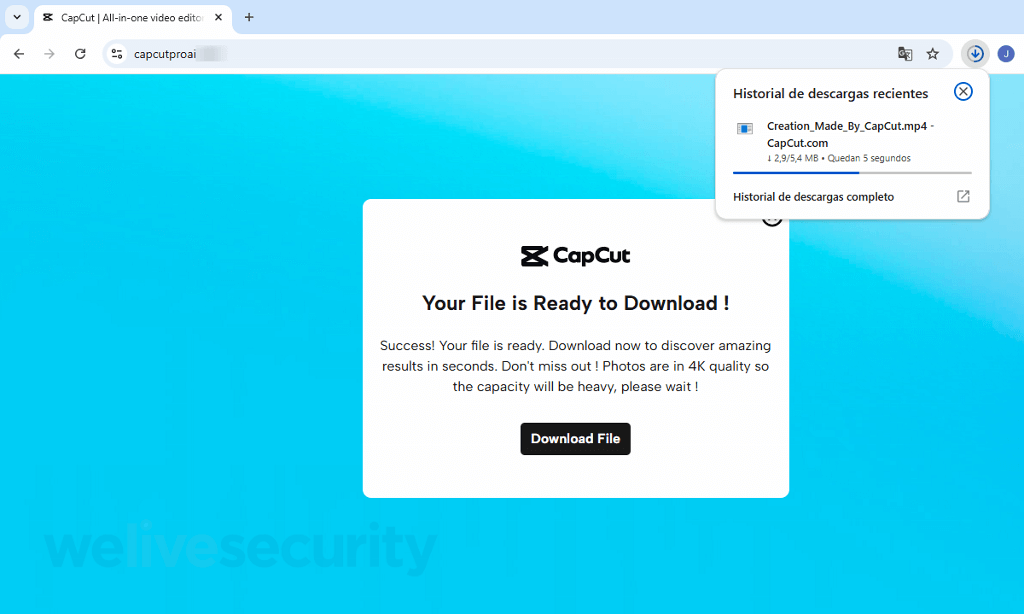
After building the anticipation and setting the trap, you are asked to download your new “creation”. However, the file, labeled Creation_Made_By_CapCut.mp4 – CapCut.com, is far from legitimate. In actuality, it is an executable for remote access software. With a few clicks, unless other defenses intervene, you may unwittingly hand over control of your device to criminals.
Here are two more websites that pretend to be genuine and are part of the same scheme:
Distant yet Near
In perspective, while authentic remote access tools like ConnectWise ScreenConnect, TeamViewer, and AnyDesk are essential for IT professionals offering technical support, in the wrong hands they can be abused to seize control of your system for malicious purposes. This includes stealing data, installing ransomware or other malware, and utilizing the compromised device to launch attacks on other systems.
These kinds of risks also pose a significant threat to business networks, as threat actors can, for example, distribute portable, self-contained executables for legitimate remote monitoring and management (RMM) tools that bypass admin privileges and eliminate the necessity for full software installation.
“Most remote control applications offer the option to create a preconfigured executable to connect to a specific IP address or user. This can assist with remote assistance but is also a tool for attackers. The victim simply needs to open the file, and with a few clicks, they may unknowingly surrender control of their computer to a cybercriminal,” explains Martina López, a security analyst with ESET’s Latin America laboratory.
Advice for the Wise
A few straightforward measures can greatly enhance your safety:
- When obtaining new software, ensure it is from the official source, typically the publisher’s legitimate website
- Avoid clicking on unsolicited links in emails or social media posts that often lead to dubious websites – these messages may be deceptive
- Apply the same caution with advertisements – it’s safer to visit the website directly by typing the URL or searching for it (with a critical eye, of course) in your preferred search engine
- Check the URL of the website – legitimate software providers do not have odd extensions in their URLs or tricky “alternate” versions (like “CapCutProAI”)
- Ensure your OS, browser, and other software are up to date to defend against known vulnerabilities
- Utilize multi-layered security tools and follow basic cyber hygiene practices, such as creating strong, unique passwords and activating two-factor authentication on all your online accounts
Naturally, this is not the first nor the last instance where CapCut users have been targeted by cybercriminals, and these instances demonstrate that scammers are always ready to exploit trust and the newest trends in technology.
The positive news is that while these schemes may be sophisticated, they are not unbeatable. Your attentiveness is your strongest shield against the strategies of scammers.





