
Online wrongdoers entice creators with assurances of state-of-the-art AI magic, only to endeavor to snatch their data or seize their devices instead
17 Apr 2025
•
,
3 min. read

The frenzy encircling generative AI utilities isn’t just reforming sectors – it also presents conducive terrain for online malefactors, who are always swift to ride on the charm of the newest trend in tech. Imagine if, instead of acquiring an AI‑crafted video from CapCut or another akin tool, your data was filched or you unknowingly handed over control of your device to a stranger?
The danger is real – security experts have previously noticed campaigns that leveraged CapCut’s fame to propagate multiple infostealers and other forms of malware. Let’s now delve briefly into another campaign that’s aiming at individuals intrigued by AI-enhanced content by pledging premium variations of renowned software such as CapCut, Adobe Express, and Canva.
The strategy of the enticement
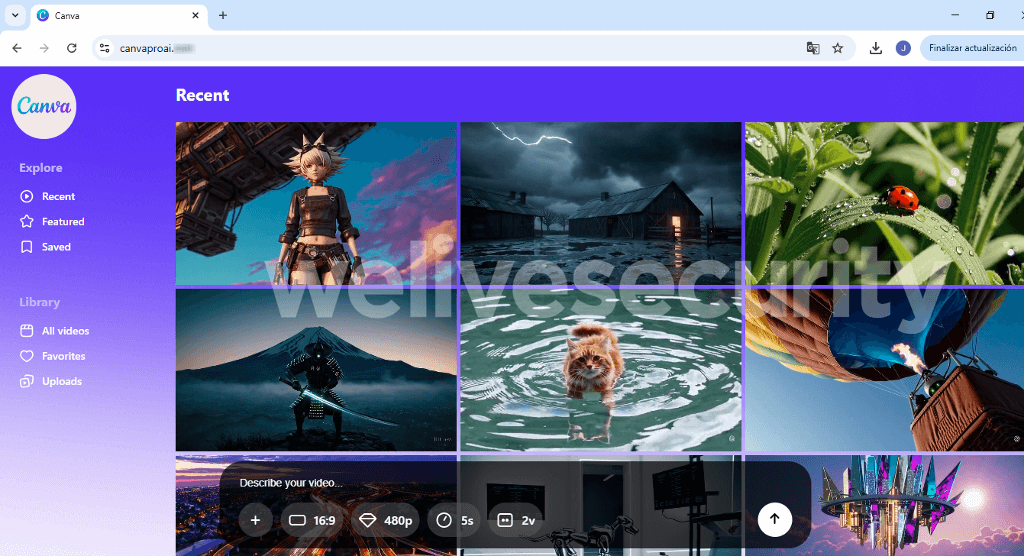
The instance below, spotted by X user g0njxa, exhibits a website that mimics CapCut, a tool frequently utilized by TikTok artists, and purports to be CapCut’s deluxe edition. (Note that the authentic deluxe edition is dubbed “CapCut Pro” or simply described as “Pro” on the website, not “CapCutProAI” as shown in the snapshot.)
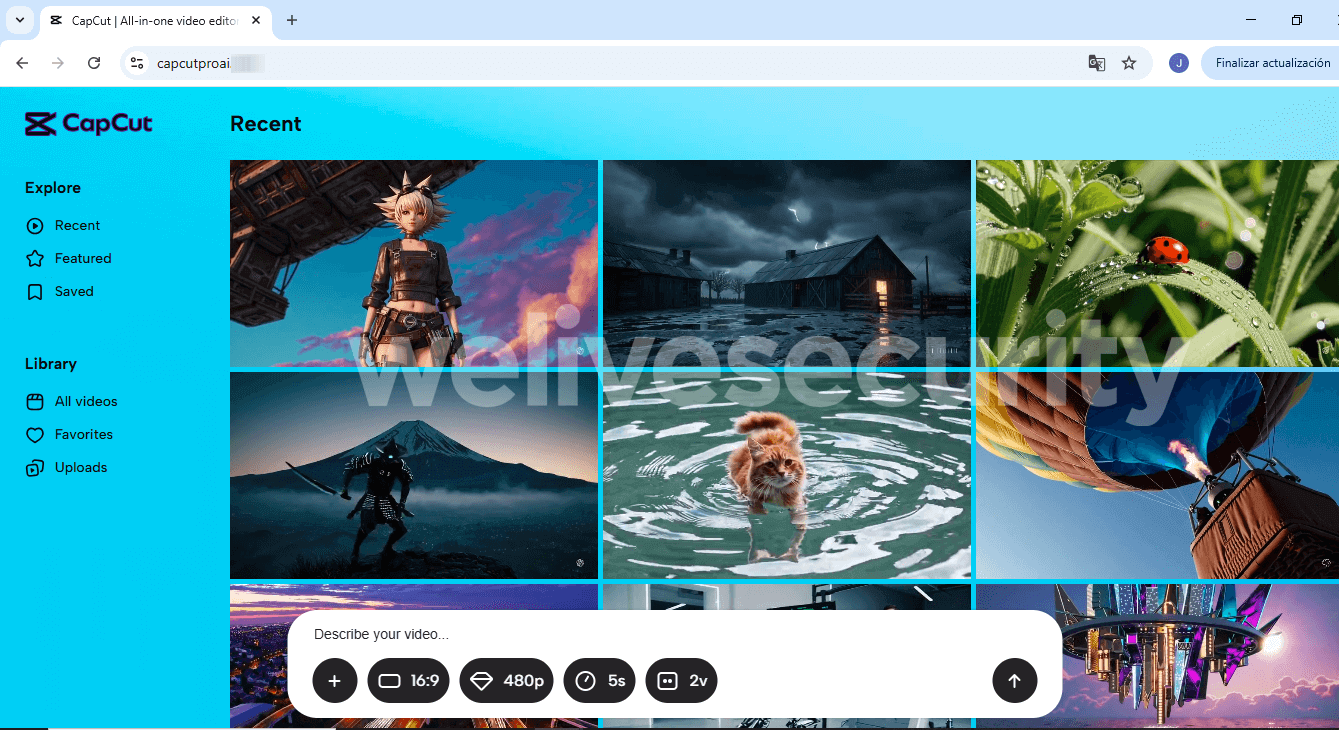
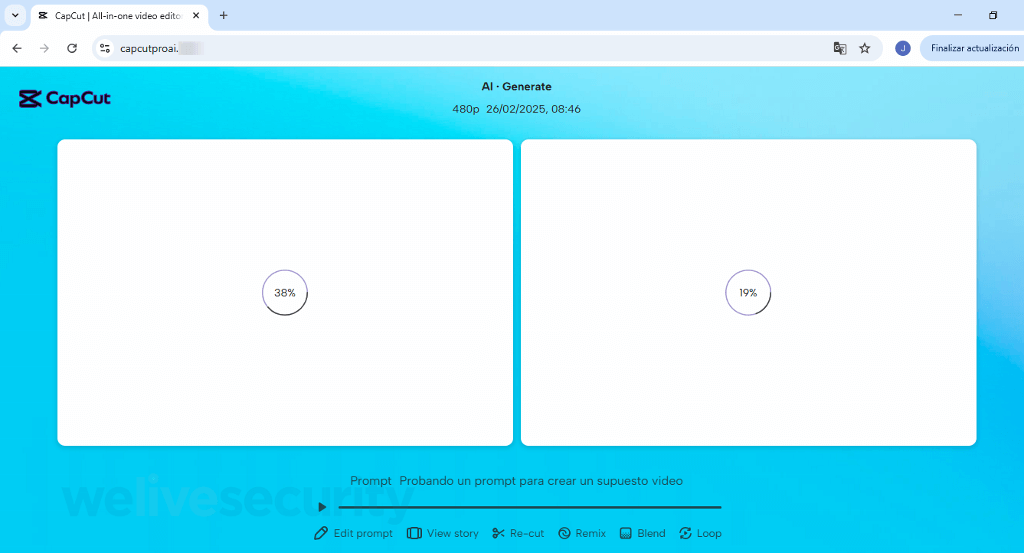
Upon arriving on the fake site, you are prompted to input a command or upload a reference file. Should you comply, the website will feign processing the request.
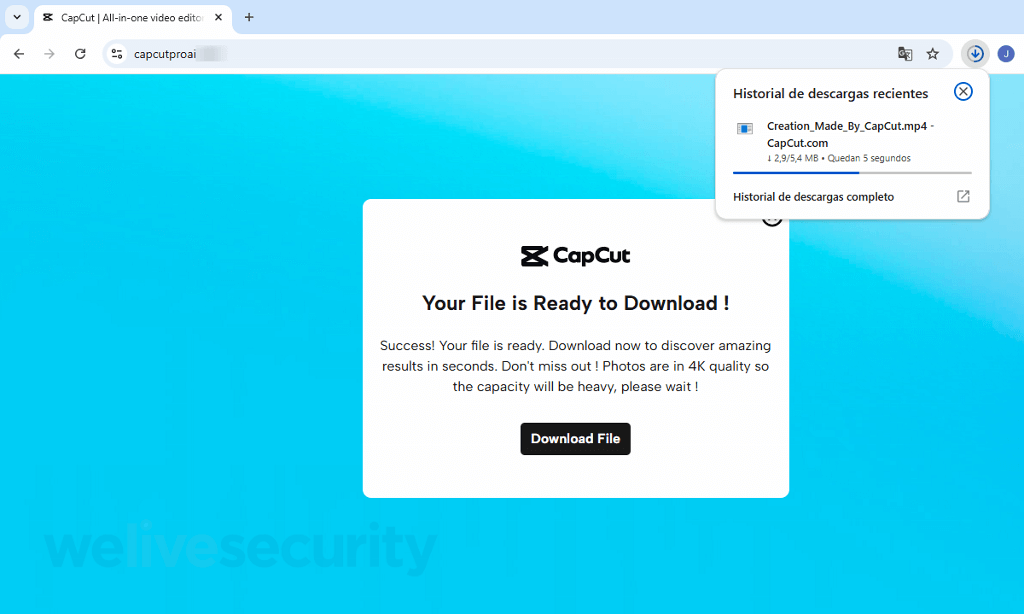
After the suspense builds up and the trap is set, you are coerced to download your gleaming new “creation”. Needless to say, the file, labeled Creation_Made_By_CapCut.mp4 – CapCut.com, is far from what it claims to be. In truth, it’s an executable for remote access software. Proceed a few clicks ahead and, unless other protections kick in, you may be relinquishing control of your device to malevolent individuals.
Here are two more sites that pose as the legitimate deal and are part of the same campaign:
Distant, yet near
For perspective, while legitimate remote access tools, such as ConnectWise ScreenConnect, TeamViewer, and AnyDesk, are invaluable for IT professionals offering technical support, in the wrong hands they can be abused to seize control of your computer for malicious motives. These encompass data thievery, installation of ransomware or other forms of malware, and utilizing the compromised device as a launch pad for incursions on other machines.
These types of hazards also loom large on corporate networks, as malevolent actors can, for instance, dispense portable, self-contained executables for legitimate remote monitoring and management (RMM) software that bypass admin privileges and bypass the necessity for full software installation.
“Most remote control applications come with the option to generate a preconfigured executable to connect to a specific IP address or user. This is useful for remote assistance, but also for attackers. The victim simply has to open the file, and in a couple of clicks, they may unwittingly give control of their computer to a cybercriminal,” says Martina López, a security researcher with ESET’s lab in Latin America.
Advice worth noting
A few uncomplicated measures will significantly contribute toward ensuring your safety:
- When downloading new software, ensure to retrieve it from the authorized source, usually the developer’s official website
- Avoid clicking on unsolicited links in email or social messages that often claim to route to such sites – the messages may be deceitful
- The same applies to advertisements – it’s safer to directly navigate to the website by typing it in your browser or searching for it (judiciously, though) in your preferred search engine
- Inspect the URL of the website – software developers typically don’t wield various quirky extensions in URLs or dubious “alternative” versions (think “CapCutProAI”)
- Ensure your operating system, browser, and other software are up to date to guard against known vulnerabilities
- Employ multi-layered security software, and adhere to other fundamental cybersecurity practices, like robust and unique passwords and activating two-factor authentication on all your online accounts
Needless to say, this isn’t the premier nor the final instance of CapCut users falling prey to online crooks, and these instances merely demonstrate that malefactors are always ready to exploit confidence and the latest trend in tech.
The promising aspect is that whereas these schemes are frequently sophisticated, they are not impregnable. Your alertness is your optimum defense against the stratagems of fraudsters.







