
Small enterprises are a key focus for cybercrime, as previously emphasized in our prior annual publication. Numerous criminal risks outlined in that study continued to pose significant threats in 2024, with ransomware remaining a critical existential cyber peril for small and midsize establishments.
In 2024, ransomware incidents constituted 70% of Sophos Incident Response cases for small business clients and more than 90% for midsized entities (ranging from 500 to 5000 employees). Ransomware and data breach attempts contributed to almost 30% of all incidents monitored by Sophos Managed Detection and Response (MDR), detecting any form of malicious activity in small and midsized businesses.
Though there was a slight year-over-year decrease in ransomware attacks overall, the financial impact of such attacks rose based on findings from Sophos’ State of Ransomware analysis. Despite the familiar nature of many threats observed in 2024, new data-centric threats are on the rise, alongside emerging tactics and techniques:
- Compromised perimeter network devices such as firewalls, VPN appliances, and other access devices played a role in a quarter of confirmed initial breaches among businesses, likely even higher.
- Software-as-a-service platforms, widely adopted by organizations during the COVID pandemic to aid remote work and enhance overall security, are now being exploited in novel ways for social engineering, initial compromise, and malware distribution.
- Incidents of business email compromise are increasingly prevalent among the initial breaches, utilized for distributing malware, stealing credentials, and employing social engineering for various criminal objectives.
- One contributing factor to business email compromise is the fraudulent acquisition of credentials through adversary-in-the-middle attacks on multifactor authentication (MFA) tokens, a persistent evolving threat.
- Fraudulent applications carrying malware or associated with scams and social engineering via SMS and messaging apps lead to mobile threats for small and midsize enterprises.
- Other non-technical threats exploiting the network’s vulnerabilities continue to be a concern for small businesses, with evolving patterns of scams.
This report delves into the trends concerning cybercriminal attack scenarios encountered by small and midsize entities. Additional information on common malware and abused software identified in endpoint detections and incidents is included in the appendix to this report, accessible here.
Table of Contents
Insights into our data
The insights presented in our Annual Threat Report are derived from the following sources:
- Client reports – consisting of detection data from Sophos endpoint software deployed on client networks, offering extensive insights into encountered threats, which are analyzed within SophosLabs (referred to as endpoint detection data in this report)
- Incident data – encompassing data collected during escalations prompted by the detection of malicious activities on MDR client networks, data obtained through MDR Incident Response regarding client incidents, and data gathered by Sophos Incident Response from incidents on client networks of organizations with up to 500 employees that lacked adequate managed detection and response protection. These datasets are gathered as a unified set of incident data in this report.
- SecureWorks incident and detection data are excluded from this report, as it was based on pre-acquisition telemetry.
- All data pertains to the 2024 calendar year, unless otherwise specified.
Client report data provides a plethora of detections from endpoints, most leading to the prevention of malware. In contrast, incident data includes information collected from any occurrences of malicious activity detected on an MDR client network or uncovered in an Incident Response case, offering a deeper insight into the intent of activities and links to other threat insights in many cases.
This report focuses on data specific to small and midsized entities. For more detailed analyses based on data obtained from Sophos Incident Response and Sophos MDR Operations, including data concerning larger entities, refer to our Active Adversary Report (AAR) series.
Security Weak Spots (and gateways)
Whether due to misconfigurations, weak authentication practices, or vulnerabilities in software or firmware, systems at the network’s perimeter serve as the primary breach point in over a third of all incidents involving intrusions into smaller entities. As highlighted recently by Sophos CEO Joe Levy, obsolete and unpatched hardware and software present a continuously growing source of security flaws, described by him as “digital detritus.”
While zero-day attacks on vulnerabilities targeting small and medium businesses are relatively uncommon, publicly known vulnerabilities can swiftly be exploited by access traders and other cybercriminals. This was evident when the backup software provider Veeam issued a security advisory regarding CVE-2024-40711 in September 2024 – within a month, cybercriminals had weaponized the exploit for the vulnerability, combining it with initial access via VPNs.
The Veeam vulnerability and similar documented vulnerabilities left unaddressed by clients – some recent, others extending back a year or more – contributed to nearly 15% of the malicious intrusion incidents tracked by Sophos MDR in 2024. In almost all instances, these vulnerabilities had been known and publicized weeks prior to their exploitation by attackers, frequently linked to ransomware attacks. In other scenarios, they were exploited by cybercriminals for initial access to potentially sell to ransomware operators.
Key cited vulnerabilities observed in Sophos MDR / IR intrusion incidents
| CVE | Description | % of intrusions exploited |
Date of CVE publication* |
| CVE-2024-1709 | ConnectWise ScreenConnect authentication bypass | 4.70% | 2024-02-21 |
| CVE-2023-4966 | Citrix NetScaler ADC and NetScaler Gateway buffer overflow vulnerability |
2.78% | 2023-10-10 |
| CVE-2023-27532 | Veeam Backup & Replication Cloud Connect unauthenticated access to encrypted credentials stored in the configuration database |
2.35% | 2023-03-10 |
| CVE-2024-3400 | Palo Alto Networks PAN-OS command injection vulnerability, allows an unauthenticated attacker to execute commands with root privileges on the firewall |
1.28% | 2024-04-12 |
| CVE-2024-37085 | VMware ESXi contains an authentication bypass vulnerability | 0.85% | 2024-06-25 |
execution
unauthenticated attacker to execute commands as SYSTEM
unauthenticated attacker to execute code or commands via HTTP
requests
* Dates of vulnerabilities sourced from cvedetails.com
Figure 1: Top disclosed vulnerabilities observed in Sophos MDR / IR intrusion incidents
In certain instances, despite the deployment of patches for recognized vulnerabilities, devices may remain susceptible due to prior compromise. For instance, web shells or alternative methods of post-exploit access malware could have been deployed before the vulnerability was addressed. Alternatively, the patching process may not have been finalized altogether. In one case handled by Sophos MDR, an attacker utilized a Citrix Netscaler gateway to establish initial access by exploiting sessions that were not reset after deploying the “Citrix Bleed” patch.
Many of the breaches dealt with by Sophos MDR and IR involved diverse vulnerabilities beyond those cataloged by the Common Vulnerabilities and Exposures database: default configurations, misconfigurations, feeble two-factor authentication (username and password), and other vulnerabilities in internet-facing devices that render them exploitable, as well as vulnerabilities that may have been rectified in subsequent updates by vendors but were never assigned CVE identifiers. Some incidents potentially stemmed from much older vulnerabilities in unpatched or end-of-life devices that were left active.
In particular, network edge devices—including virtual private network (VPN) appliances, firewalls with VPN functionalities, and other remote-access appliances—significantly contributed to cybercrime incidents. These devices collectively represented the primary source of initial network compromise in intrusion incidents monitored by Sophos MDR.
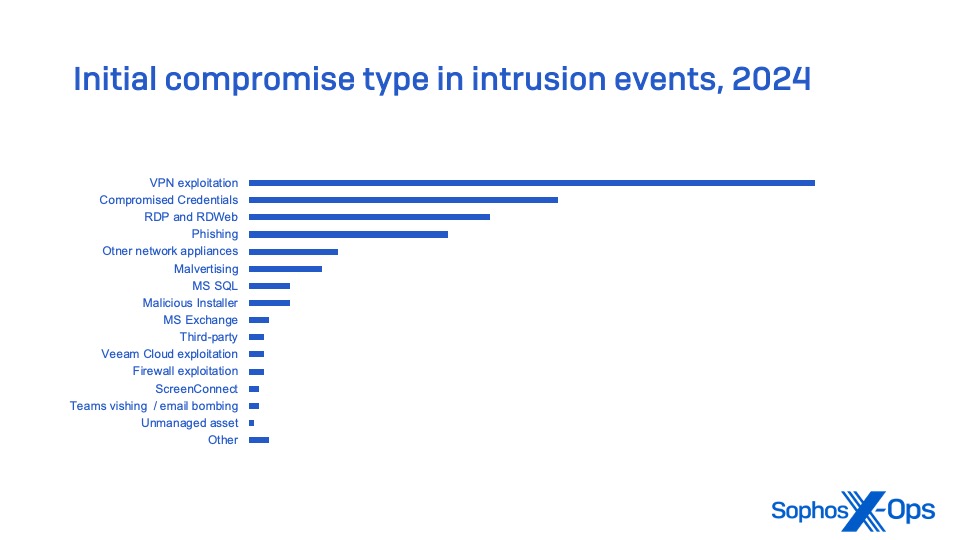
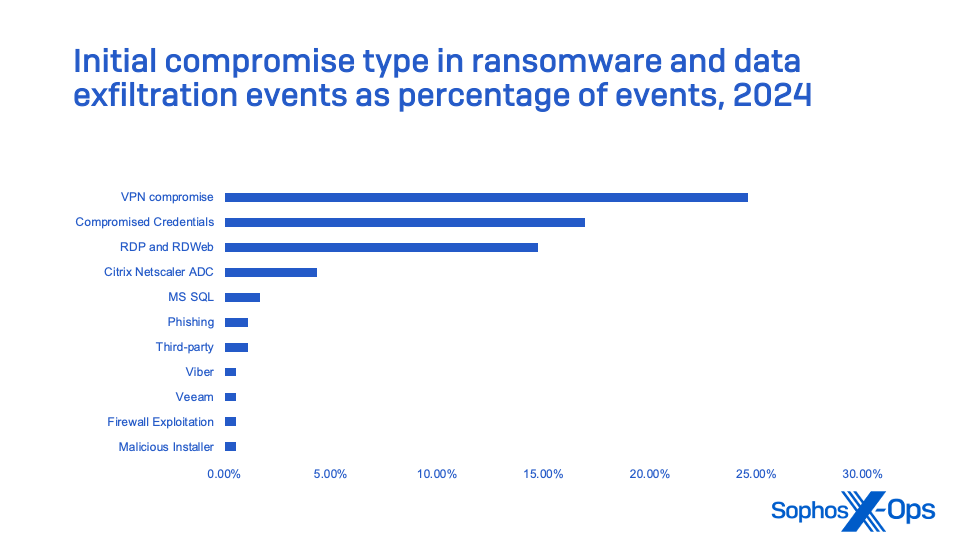
These figures do not encompass incidents where ransomware execution or data exfiltration did not transpire due to the blocking of C2 and other post-exploitation tools.
These statistics emphasize the importance for even small organizations to implement MFA for all user accounts, particularly those with remote access privileges via VPN or other methods. They also underscore the necessity of auditing devices utilized for remote network connection and regularly updating their software or firmware—and replacing software and operating systems no longer receiving regular security update support.
STACs: Bundled playbooks, strategies, tools, and protocols
Instead of monitoring “threat groups,” Sophos MDR concentrates on recognizing distinct behavior patterns to trace a group of actors across multiple incidents. These encompass tools, strategies, and protocols (TTPs), support infrastructure, and other attributes reflecting the application of a shared playbook or set of scripted tools. They are denoted as Security Threat Activity Clusters (STACs) and their activities are tracked as campaigns.
STACs characterize not just a single group of actors, but a common playbook—including tactics, tools, and protocols (TTPs), such as attack scripts and comparable mechanisms for targeting victims. These playbooks may have been compiled for use by multiple affiliates of a ransomware organization, vended on clandestine platforms, or outright pilfered by individuals transitioning from one criminal endeavor to another.
For instance, during the investigation of threats leveraging the Veeam vulnerability CVE-2024-40711, Sophos MDR Threat Intelligence pinpointed a particular threat activity cluster utilizing it in conjunction with VPN exploitation and nearly identical TTPs. The cluster, labeled STAC5881, is monitored in this campaign. The Veeam vulnerability was exploited to create administrator accounts with identical names (labeled “point”). However, the ransomware deployed varied in these instances: Akira, Fog, and a newly discovered ransomware named Frag.

Frag seems to be described as a “junk gun” ransomware—roughly programmed, economical ransomware created as a substitute for ransomware-as-a-service, and either originated by the cybercriminals themselves or acquired from an underground marketplace at an average cost of $375.
The most active STAC campaigns monitored by Sophos MDR in 2024 were predominantly ransomware-related, with only one exception—which was the enduring malware-as-a-service platform DanaBot, a potential precursor to ransomware assaults.
Primary security threat activities were concentrated in clusters during 2024
| STAC4265 | DanaBot campaign employing Facebook social manipulation, featuring links to sites offering “unclaimed money” that redirect to distribute malware aimed at stealing browser data and sending it through the Tor anonymizing network |
| STAC4529 | Exploitation of an authorization loophole using RCE in ConnectWise Screen Connect versions before 23.9.8 |
| STAC4556 | Execution of Crytox ransomware, dropping uTox messenger application, usage of a vulnerable kernel driver for disabling EDR software. The group in this cluster also employed legitimate “dual-use” utilities: Advanced Port Scanner for network reconnaissance, and Mimikatz and Lazagne utilities for finding and retrieving credentials |
| STAC6451 | Affiliates of Mimic ransomware, employing Cloudflare to conceal command and control domains, exploiting Microsoft SQL Server for unauthorized entry, and deploying Impacket for creating backdoors using common credentials. They also demonstrated skill in bypassing network detection by diverting probing domains to valid websites and sending data through recognizable file transfer services. |
| STAC5881 | A cluster utilizing Akira, Fog, and Frag ransomware attacks, exploiting VPNs and CVE-2024-4071 (mentioned earlier) |
| STAC5464 | A cluster related to ransomware linked to Hunters International, sharing the same SFTP exfiltration server for multiple incidents, performing NTDS credential dumping, and utilizing network proxying through Plink, SystemBC malware, and other tools |
| STAC5397 | Actor or group linked to Akira and Fog ransomware. Establishes hidden access with a standard password. This cluster has been identified deploying legitimate “dual-use” tools: AnyDesk for execution and lateral movement, and Rclone and FileZilla for data extraction. |
| STAC4663 | A ransomware-oriented cluster that employs custom, obscured malware for intrusions. The group frequently utilizes CVE-2023-3519 to exploit Citrix NetScaler appliances for initial access and utilizes the legitimate OpenSSH library for tunneling network traffic in targeted environments. |
| STAC5304 | A RansomHub ransomware associate first identified in summer 2024 who has reused exfiltration IP addresses across different incidents, leveraging legitimate tools (Atera Agent remote machine management software, FileZilla for data exfiltration) and a script named HideAtera.bat to evade defenses |
Figure 5: Primary security threat activity clusters in 2024 ranked by incident count
Trends in cybercrime methodologies, strategies, and practices
Remote ransomware perpetuates its growth
Despite a slight decline in the overall number of incidents in 2024 due to improved defenses and the disruption of major ransomware-as-a-service operators, ransomware-linked criminal activities are not diminishing. If anything, the strategies of ransomware perpetrators are adapting to be more rapid in their attacks and more willing to extort the victim over extracted data when encryption of victim’s files fails. Some attackers even forego attempting to encrypt the files.
When ransomware is executed, it is frequently initiated from beyond the detection reach of endpoint protection software—either from an unmanaged device remotely or directly linked to the targeted network. Such “remote” ransomware assaults employ network file-sharing links to reach and encrypt files on other devices, ensuring that the ransomware itself is not directly activated on those devices. This approach can obscure the encryption process from malware scans, behavioral detection methods, and other defenses.
Sophos X-Ops discovered through telemetry analysis that the use of remote ransomware surged by 50 percent in 2024 compared to the previous year, and by 141 percent since 2022.

Social engineering through Teams vishing
In the latter half of 2024, particularly in the final quarter, we witnessed the adoption of a mix of technical and social engineering attacks by threat actors to target Microsoft 365 organizations (previously Office 365). One of these campaigns successfully extracted data but failed to progress to ransomware deployment. Multiple other attempts were thwarted while gathering credentials and attempting to infiltrate further into the targeted organizations’ networks (potentially reaching their software-as-a-service instance and its data).
These campaigns by two distinct threat groups employed “email bombing”—the bombardment of a large number of emails to specific individuals within the attacked organizations—followed by a deceptive technical assistance call via Microsoft Teams to those individuals, using their own 365 accounts to send Teamscommunications and engage Teams audio and video calls with the marked organizations.
Multifactor authentication (MFA) scam
Bad actors have also adapted their misleading methods to gather user credentials. MFA has raised the complexity of converting usernames and passwords into entry. The cybercrime marketplace has reacted with fresh approaches to seizing both credentials and multifactor tokens instantly to surpass that hindrance.
MFA scam relies on an “adversary-in-the-middle” strategy, where the scamming platform operates as an intermediary to the real authentication procedure for the multifactor-secured service. The platform then transfers captured credentials and the session cookie received from the login to the cybercriminal via a distinct channel, allowing them to then transmit the credentials and token to the victim’s legitimate service portal and gain entry.
A multifactor authentication scam platform known as Dadsec emerged in the autumn of 2023, and later got tied to operations in 2024 by a phishing-for-hire platform called Tycoon. However, Tycoon was not the sole phishing circle utilizing tools derived from Dadsec. Rockstar 2FA and FlowerStorm both seem to be grounded on upgraded versions of the Dadsec platform, employing Telegram as a command-and-control network. Rockstar 2FA was extensively operational in the mid of 2024 and faced technical malfunctions in November, later quickly being replaced by FlowerStorm.

Opponent AI utilization
social manipulation tasks: fabricating images, videos, and text for fabricated profiles, and for communication with targets to mask language proficiency issues and identity. They also employ it to enhance the appearance of their tools—similar to what RaccoonStealer developers did for a graphic on their portal login interface.
showcased the potential to create an entire campaign of targeted emails through AI-guided procedures derived from data extracted from the social media profiles of targeted individuals, employing existing resources.
an initial probe in late 2023, followed by an update in early 2025), there remains substantial skepticism among certain threat actor factions. Some are trialing and employing AI for mundane duties, but malevolent applications still linger mostly as theories—though our most recent update noted a few threat actors starting to merge generative AI into spamming facilities and analogous utilities.
QRishing


Sponsored Content and Search Engine Poisoning
Malvertising refers to the utilization of malicious internet advertisements, including sponsored listings within search results. It remains a popular strategy for spreading malware. While traditionally linked to droppers like ChromeLoader, malvertising has now become the preferred method for disseminating data-stealing malware, with Sophos MDR noting additional malware injection techniques leveraging malvertising.
A malvertisement may connect to a malicious website or directly launch a malicious script, leading the victim to download and run malware or other tools, granting the attacker persistence on the victim’s machine. For instance, in the latter part of 2024, Sophos X-Ops identified a browser hijack scheme related to Google search malvertising, targeting users searching for a PDF tool download through specific keywords. These adverts resulted in the download of malicious Microsoft installer (.MSI) files that appeared to be genuine PDF tools but, in reality, implanted a system task, a startup component, and registry entries to ensure the persistence of browser-hijacking malware, redirecting users’ search queries to sites controlled by the malware operators.
Sophos MDR has linked malvertising with some of the most active malware campaigns of 2024, such as DanaBot, Lumma Stealer, and GootLoader. Other attack vectors observed utilizing malvertising include backdoors, remote administration trojans like SectopRat, the Cobalt Strike attack toolkit, and the misuse of legitimate remote access software like AnyDesk.
EDR Termination Tools
Sophos X-Ops has identified various malicious tools developed for the criminal underground in the last couple of years commonly referred to as “EDR terminators.” These tools are designed to leverage kernel drivers to gain privileged access to the operating system, terminating targeted protected processes—especially endpoint security software—allowing for the unhindered deployment of ransomware or other malware. Notably, the developers of these tools now increasingly rely on a set of legitimate yet vulnerable drivers to power them, known as “bring your own vulnerable driver” (BYOVD) attacks.
In 2024, Sophos X-Ops encountered several potential EDR terminators used by ransomware actors. EDRSandBlast was among the most frequently identified, employed by multiple threat actors. Variants of EDRSandBlast were detected in numerous ransomware attempts throughout the year, particularly spiking around the US Thanksgiving holiday in November, as revealed in incidents handled by MDR and Incident Response teams.
Figure 12: Top 10 Malware Terminators affecting Sophos EDR solutions
Sophos employs tamper protection, behavioral monitoring, and specific detections to combat the malicious use of kernel drivers in defending against such tools. Nevertheless, the evolving nature of these malicious programs places additional strain on defenders to identify and thwart attackers before they successfully execute their strategies.
Conclusion
The dynamic threat landscape for small and medium-sized enterprises witnesses continuous adaptations by cybercriminals to counter new defense mechanisms and exploit both new and long-standing vulnerabilities as they surface. Addressing these challenges often exceeds the capabilities of most small organizations without external assistance and strains even dedicated IT teams within larger enterprises.
Effective lifecycle management of all systems, spanning from Internet routers to firewall appliances, VPN devices, and public-facing applications and servers, constitutes a crucial aspect of deterring a considerable portion of cyber attacks. Neglecting patch updates or running devices beyond their vendor-endorsed support timeframe can inadvertently attract access brokers and ransomware operators who actively scour the Internet for unprotected systems to target.
This year’s statistics indicate a shift towards criminal infiltration in less-monitored areas:
- Sophos MDR has noted an uptick in the exploitation of vulnerabilities and misconfigurations in network perimeter devices, employed to gain and mask illicit network access.
- When there’s a risk of detection by endpoint security systems, attackers resort to “remote ransomware” tactics from less-guarded assets.
- Given the opportunity to elevate privileges, cybercriminals introduce a vulnerable device driver to evade security countermeasures.
Whether through MFA code theft, the deceptive use of QR codes to lure users into visiting malicious login pages via mobile devices, or through social engineering tactics like email bombing and vishing attacks, threat actors consistently adapt and refine their strategies to circumvent defenses.
When viewed holistically, the trends and data underscore the necessity of adopting a layered security approach for safeguarding organizations of all sizes. Many of these strategies do not require increased security investments but rather a shift in mindset to align with the evolving threat landscape. Small and medium-sized enterprises can decrease their risk exposure with the following measures:
- Transition from password-based credentials to device-specific passkeys. Passkeys are encrypted digital keys unique to each device and are resistant to interception by phishing kits.
- Implement multifactor authentication for accounts where passkeys cannot be adopted and prioritize passkey implementation where feasible.
- For accounts unsuitable for passkeys or multifactor authentication, closely monitor them via an identity threat detection and response strategy, either internally or through external managed services.
- Give due attention to patching edge devices such as firewalls and VPN appliances and ensure complete adherence to patching protocols, including device resets when necessary.
- Deploy endpoint security solutions across all devices to prevent exploitation of unmanaged assets by attackers.
- Routinely engage external audits to monitor and secure external attack surfaces, identifying and rectifying exploitable entry points that could attract threat actors scanning for vulnerable targets.
Contributions
Sophos X-Ops extends gratitude to Anna Szalay, Colin Cowie, and Morgan Demboski of Sophos MDR Threat Intelligence, as well as Chester Wisniewski, Director, Global Field CISO, for their contributions to this report.



