
Last week, law enforcement in at least two American states separately reported the apprehension of Chinese citizens accused of executing an innovative type of tap-to-pay fraud using portable devices. Initial disclosures from authorities reveal that the scammers were utilizing mobile wallets obtained through online phishing operations and were depending on a tailor-made Android application to facilitate tap-to-pay transactions from devices situated in China.

Image: WLVT-8.
The authorities in Knoxville, Tennessee informed last week that they have apprehended 11 Chinese individuals who stand accused of purchasing substantial amounts of gift cards at local stores with mobile wallets obtained through devious online practices. The Knox County Sheriff’s office labeled these arrests as the pioneering ones in the country related to this unique tap-to-pay fraud paradigm.
When questioned about the distinguishing features of this fraudulent tactic, Knox County responded by highlighting that although it may seem like the individuals are simply acquiring gift cards, they are, in reality, engaging in numerous transactions to procure assorted gift cards and conducting their criminal activity across multiple states.
Chief Deputy Bernie Lyon from Knox County stated, “These perpetrators have been touring the country, employing purloined credit card details to buy gift cards and cleanse ill-gotten funds. In the operation on Monday, we uncovered gift cards exceeding $23,000 in value, all purchased using information from unsuspecting victims.”
Inquiries about the mobile devices seized from the suspects were met with Lyon’s explanation that “tap-to-pay fraud involves a crew using Android devices to execute Apple Pay transactions utilizing stolen or compromised debit/credit card data,” [emphasis added].
Lyon opted not to provide further details about the operational mechanics of the fraud, citing an ongoing investigation.
Ford Merrill, who specializes in security research at SecAlliance, a CSIS Security Group subsidiary, pointed out that there are limited legitimate scenarios where Android devices can execute Apple Pay transactions, unless they are utilizing a specialized Android application that was previously discussed in an article by KrebsOnSecurity as part of an in-depth exploration of the operations of Chinese-based phishing syndicates that are rejuvenating the payment card fraud sector (also known as “carding”).
How are these Chinese phishing organizations acquiring pilfered payment card details and integrating them into Google and Apple phones? It all commences with phishing.
If you possess a mobile handset, it’s highly probable that at some juncture in the last couple of years, the device has received at least one fraudulent message posing as the U.S. Postal Service to claim an outstanding delivery fee or an SMS masquerading as a local toll road authority declaring an overdue toll fee.
These messages are propagated through sophisticated phishing toolkits vended by numerous cybercriminals situated in mainland China. These aren’t traditional SMS phishing or “smishing” messages as they circumvent the mobile networks entirely. Instead, the messages are disseminated via the Apple iMessage platform and through RCS, the functionally equivalent service on Google devices.
Individuals who input their payment card information on one of these websites are informed that their financial institution necessitates confirming the minor transaction by dispatching a single-use passcode to the customer’s mobile device. Essentially, this code is sent by the victim’s financial institution in response to a request from the fraudsters to bind the phished card details to a mobile wallet.
In case the victim furnishes that unique code, the fraudsters will intertwine the card data with a new mobile wallet from Apple or Google, loading the wallet onto a mobile phone under the scammers’ control. These phones are subsequently prepped with multiple compromised wallets (often 5-10 per device) and distributed in bulk to scammers on Telegram.
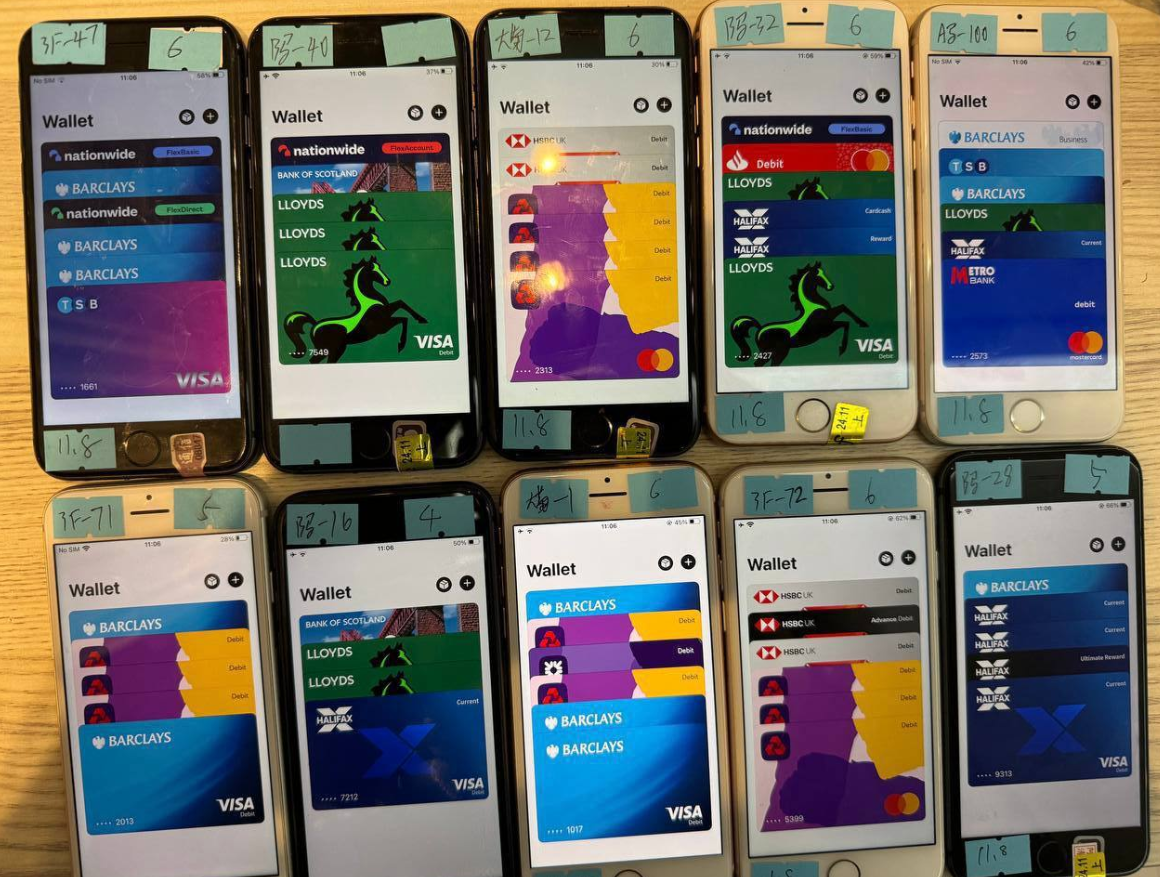
An image from the Telegram channel for a popular Chinese smishing kit vendor shows 10 mobile phones for sale, each loaded with 5-7 digital wallets from different financial institutions.
Merrill identified that at least one of the Chinese phishing factions markets an Android app named “Z-NFC” that can relay a legitimate NFC transaction to any location globally. All the user has to do is wave their phone at a nearby payment terminal accepting Apple or Google Pay, and the app forwards an NFC transaction online from a phone in China.
“It would be surprising if this wasn’t the NFC relay app,” Merrill expressed concerning the recently detained suspects in Tennessee.
Merrill mentioned that the Z-NFC application is functional from any part of the world and that one phishing syndicate offers the software for $500 monthly.
“It can facilitate both NFC capable tap-to-pay transactions and any digital wallet,” Merrill highlighted. “They even offer round-the-clock support.”
On the 16th of March, the Sacramento-based ABC affiliate, ABC10, in California broadcasted a segment detailing the arrest of two Chinese citizens who were caught employing an app to execute illicit transactions using stolen credit cards at a local Target store. The investigative report stated that the individuals endeavored to purchase gift cards using a mobile application that cycled through more than 80 pilfered payment cards.
ABC10 reported that although a majority of those transactions were declined, the suspects still managed to get away with $1,400 worth of gift cards. Following their apprehension, both individuals purportedly confessed to receiving $250 a day for carrying out the fraudulent activities.
Merrill mentioned that it’s commonplace for fraud rings to promote such activities on social media platforms, including TikTok.
A CBS News report about the arrests in Sacramento revealed that one of the suspects attempted to utilize 42 distinct bank cards, with 32 being rejected. Nonetheless, the individual was reportedly able to spend $855 during the transactions.
Similarly, the alleged accomplice of the suspect tried 48 transactions using different cards, succeeding 11 times and spending $633, according to CBS.
“It’s intriguing that a substantial number of cards were declined,” Merrill remarked. “One explanation could be that financial institutions are becoming more adept at identifying this type of fraudulent activity. Another reason might be that the cards were already utilized and flagged for fraud even prior to these individuals trying to use them. Therefore, there might be an element of sending these individuals out to stores to experiment, and if unsuccessful, they are left to fend for themselves.”
Merrill’s investigation into the Telegram sales channels of these Chinese-based phishing syndicates indicates that their deceptive websites are actively operated by fraudsters stationed in front of extensive arrays of Apple and Google devices employed to dispatch spam messages and immediately address responses.
In essence, the phishing websites are sustained by live human operatives as long as they are disseminating new messages. Merrill noted that the criminals usually dispatch only a few dozen messages at once, likely due to the manual efforts required by the human operators in China to complete the scam. After all, the one-time codes used for mobile wallet setup typically remain viable for just a few minutes before expiring.
For detailed insights into the operational methodologies of these China-based mobile phishing syndicates, refer to How Phished Data Turns Into Apple and Google Wallets.

The ashtray says: You’ve been phishing all night.







